1.相关知识--对象存储
说明:ceph兼容S3: 提供了对象存储接口,兼容 亚马逊S3 RESTful 接口的一个大子集。
创建网关用户
docker exec ceph-rgw radosgw-admin user create --uid=$USER --display-name=$USER --access-key=$ACCESS_KEY --secret-key=$SECRET_KEY docker exec ceph-rgw radosgw-admin role create --role-name=$ROLE_NAME --path=/ --assume-role-policy-doc=$ROLE_DOC
查看创建的role:
radosgw-admin role list docker exec ceph-rgw radosgw-admin role-policy put --role-name=$ROLE_NAME --policy-name=$ROLE_POLICY_NAME --policy-doc=$ROLE_POLICY_DOC
查看role-policy:
radosgw-admin role-policy list --role-name S3Access1
radosgw-admin role-policy get --role-name S3Access1 --policy-name Policy2
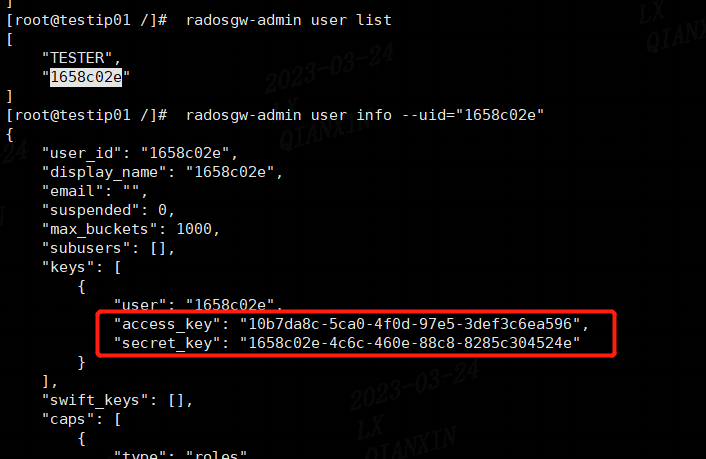
#查看用户信息 radosgw-admin user info --uid="test"
2.python脚本实现

import boto3 #创建用户:docker exec ceph-rgw radosgw-admin user create --uid=TESTER --display-name=TESTER --access-key=9876456313 --secret-key=123456789 #获取s3临时token 去访问ceph # iam_client = boto3.client('iam', # aws_access_key_id="10b7da8c-5ca0-4f0d-97e5-3def3c6ea596", # aws_secret_access_key="1658c02e-4c6c-460e-88c8-8285c304524e", # endpoint_url="https://lxtest.t.lanxin.cn:11443", # region_name='default' # ) # # print("iam here",iam_client) # # # policy_document = '''{"Version":"2012-10-17","Statement":[{"Effect":"Allow","Principal":{"AWS":["arn:aws:iam:::user/TESTER"]},"Action":["sts:AssumeRole"]}]}''' # # role_response = iam_client.create_role( # AssumeRolePolicyDocument=policy_document, # Path='/', # RoleName='S3Access6', # ) # print("role here",role_response) # role_policy = '''{"Version":"2012-10-17","Statement":{"Effect":"Allow","Action":"s3:*","Resource":"arn:aws:s3:::*"}}''' # # response = iam_client.put_role_policy( # RoleName='S3Access6', # PolicyName='Policy6', # PolicyDocument=role_policy # ) # print("res here",print(response)) #上面步骤创建的网关用户 sts_client = boto3.client('sts', aws_access_key_id="9876456313", aws_secret_access_key="123456789", endpoint_url="https://lxtest.t.lanxin.cn:11443", region_name='', ) print("sts here") response = sts_client.assume_role( RoleArn="arn:aws:iam:::role/S3Access6", #role_response['Role']['Arn'], RoleSessionName='Bob', DurationSeconds=3600, ) print("sts res heres",response) #获取token信息 print(response['Credentials']['SessionToken']) #通过临时token操作对象存储 s3client = boto3.client('s3', aws_access_key_id = response['Credentials']['AccessKeyId'], aws_secret_access_key = response['Credentials']['SecretAccessKey'], aws_session_token = response['Credentials']['SessionToken'], endpoint_url="https://lxtest.t.lanxin.cn:11443", region_name='default',) bucket_name = 'my-bucket' s3bucket = s3client.create_bucket(Bucket=bucket_name) resp = s3client.list_buckets() print(resp)
我的环境,创建网关用户已经操作过了, 只需通过网关用户获取临时token信息
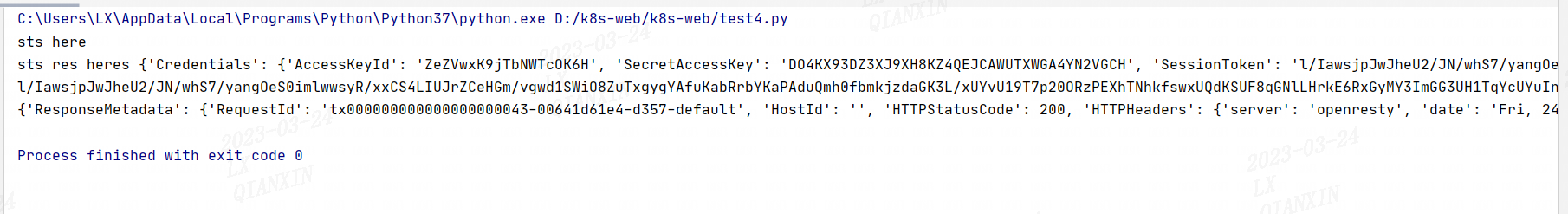
import boto3 sts_client = boto3.client('sts', aws_access_key_id="10b7da8c-5ca0-4f0d-97e5-3def3c6ea596", aws_secret_access_key="1658c02e-4c6c-460e-88c8-8285c304524e", endpoint_url="https://lxtest.t.lanxin.cn:11443", region_name='', ) print("sts here") response = sts_client.assume_role( RoleArn="arn:aws:iam:::role/1658c02e-sts", #role_response['Role']['Arn'], RoleSessionName='Bob', DurationSeconds=3600, ) print("sts res heres",response) #获取token信息 print(response['Credentials']['SessionToken']) #通过临时token操作对象存储 s3client = boto3.client('s3', aws_access_key_id = response['Credentials']['AccessKeyId'], aws_secret_access_key = response['Credentials']['SecretAccessKey'], aws_session_token = response['Credentials']['SessionToken'], endpoint_url="https://lxtest.t.lanxin.cn:11443", region_name='default',) bucket_name = 'my-bucket' # s3bucket = s3client.create_bucket(Bucket=bucket_name) resp = s3client.list_buckets() print(resp)
user、access、secret获取:
arn获取: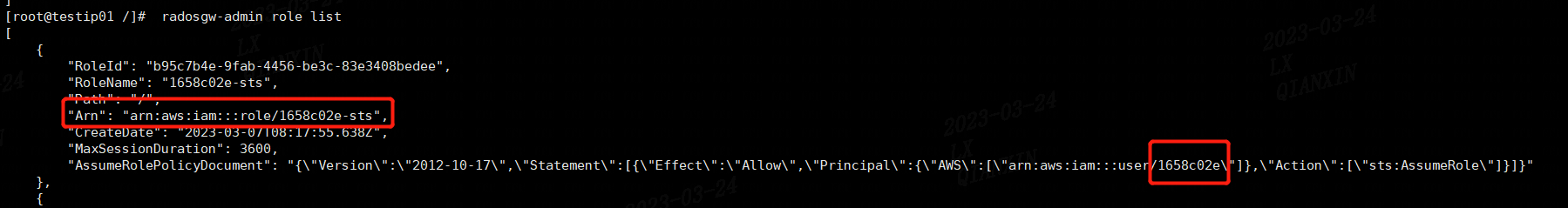
python脚本运行结果:
增加内容:提供临时下载地址方式

import boto3 from botocore.client import Config s3_endpoint = "https://lxtest.t.lanxin.cn:11443" s3_acces_key = "10b7da8c-5ca0-4f0d-97e5-3def3c6ea596" s3_secret_key = "1658c02e-4c6c-460e-88c8-8285c304524e" s3_sign_vers = "s3v4" region="default" #"s3"(SignV2) or "s3v4"(SignV4) s3 = boto3.client('s3', region_name=region,endpoint_url = s3_endpoint, aws_access_key_id = s3_acces_key, aws_secret_access_key = s3_secret_key, config=Config(signature_version=s3_sign_vers)) bucket_name = "lanxin" object_name = "coredns2.yaml" expire_time = 3600 #wpsfile/snapshot.3.6.0-pla-web.yaml url = s3.generate_presigned_url( ClientMethod='get_object', Params={ 'Bucket': bucket_name, 'Key': object_name }, ExpiresIn=expire_time ) print(url) #https://zzepc.net:11443/lanxin/56d89868-f0d4-45ce-9940-cef9d1e3d6b6.doc?X-Amz-Algorithm=AWS4-HMAC-SHA256\u0026X-Amz-Credential=919bdedb-1737-4018-aa6a-2be463c383b0%2F20221125%2Fdefault%2Fs3%2Faws4_request\u0026X-Amz-Date=20221125T010724Z\u0026X-Amz-Expires=3600\u0026X-Amz-SignedHeaders=host\u0026X-Amz-Signature=9a803dcd12d9efd44e5622fe223dc2e9919e006ed730062c3eb52834dd8fc065 #https://zzepc.net:11443/lanxin/c09c0455-b54a-4bd8-8c5b-6a06f6f0c692.xlsx?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=919bdedb-1737-4018-aa6a-2be463c383b0%2F20221125%2Fdefault%2Fs3%2Faws4_request&X-Amz-Date=20221125T010248Z&X-Amz-Expires=3600&X-Amz-SignedHeaders=host&X-Amz-Signature=008c01f9b261658c503a2e9ce402e3d9da29e0257d9a76f23504b3fce0a4226f
参考官网:https://docs.ceph.com/en/latest/radosgw/STS/
说明:此文档初衷是为了跟研发证明,ceph服务没有异常,临时了解的内容
