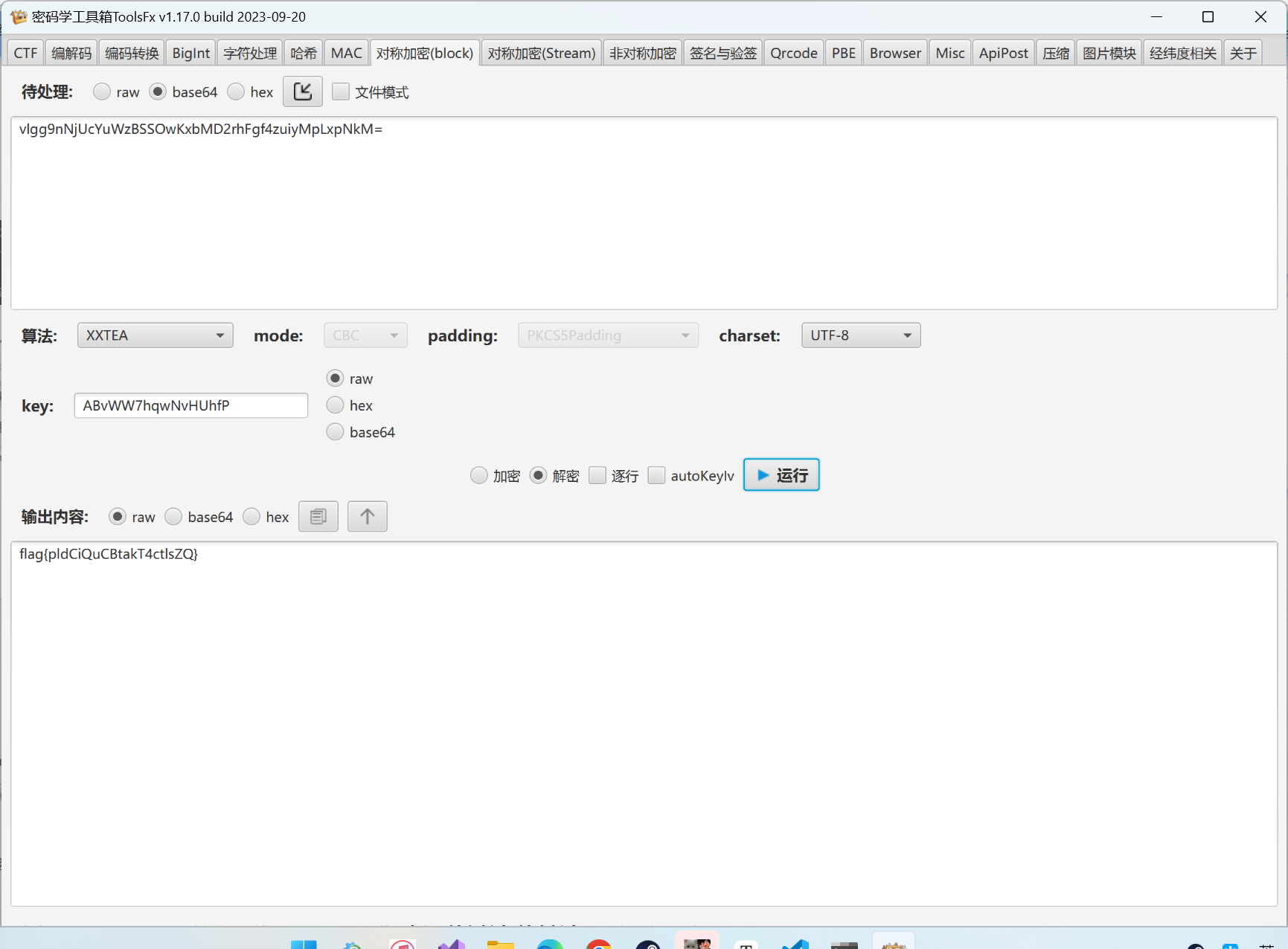
Tea总结(例题形式)
[GDOUCTF 2023]Tea
老规矩,pe查壳,无壳64位,拖进IDA中
在Function模块中没有找到main函数,看看String里面有没有
发现了fake_flag,点进去看看
发现sub,跟进
看到以下内容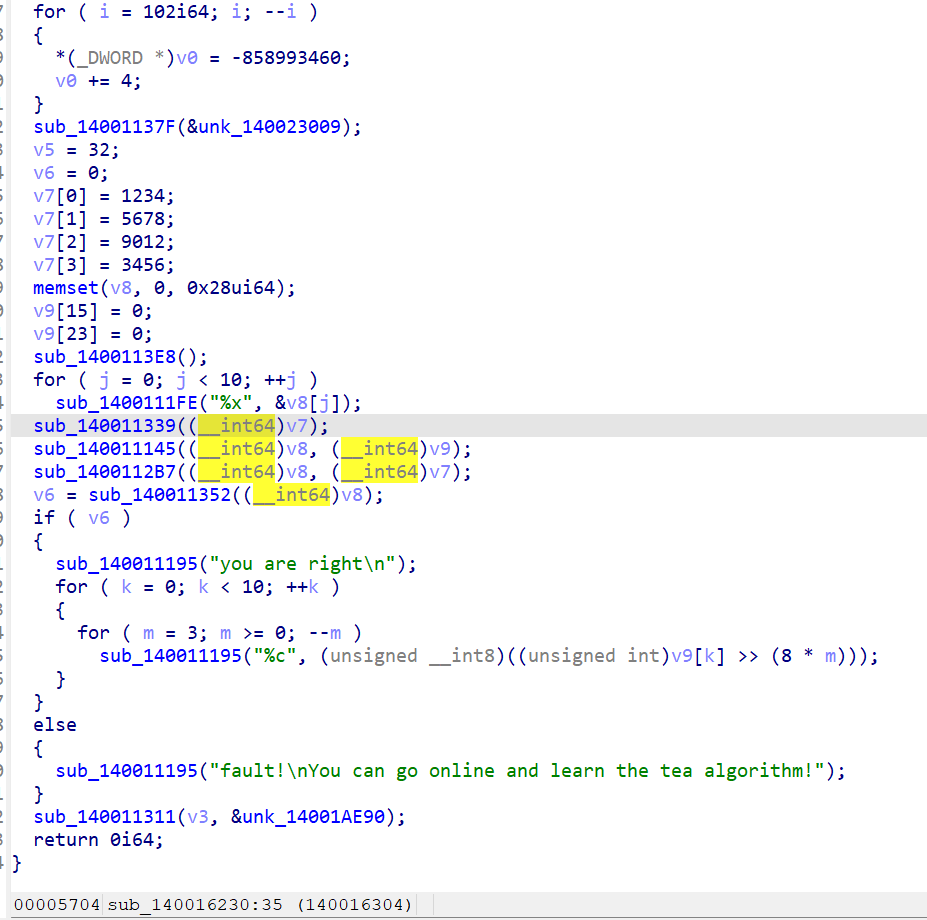
发现sub_140011339中的sub_1400117D0有有用内容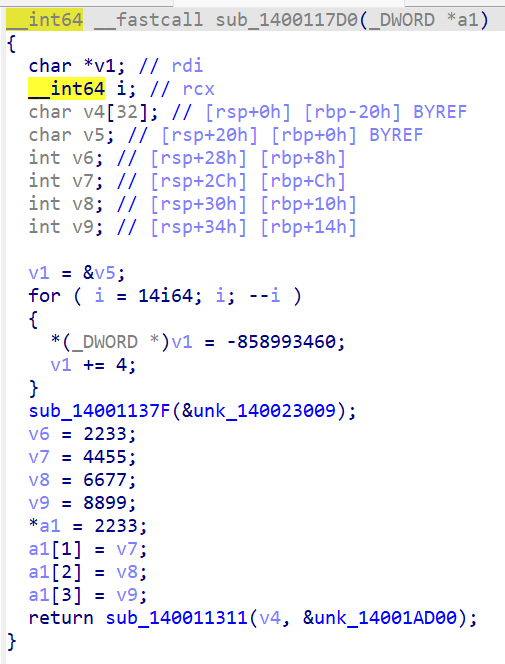
那么key的值就是key[]=
再跟进到sub_1400112B7下的sub_140011900函数,看到了tea加密
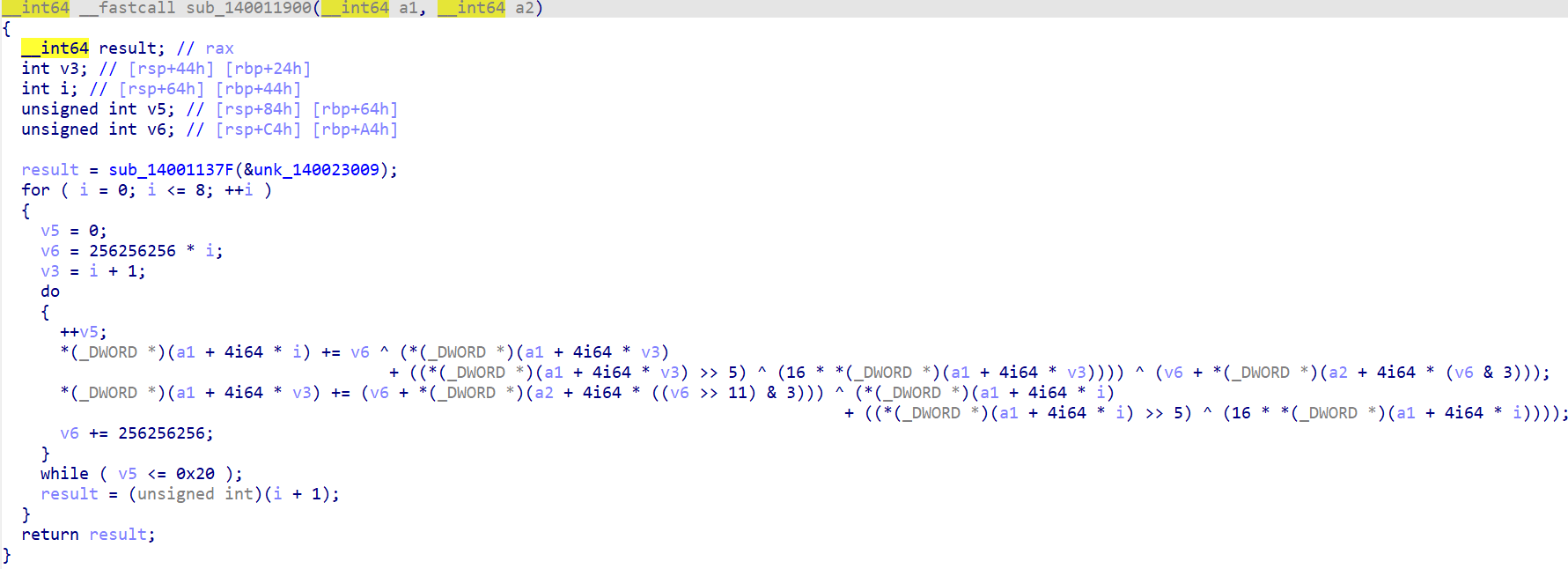
又跟进到sub_140011352下的sub_140011B60函数,得到加密后的数据
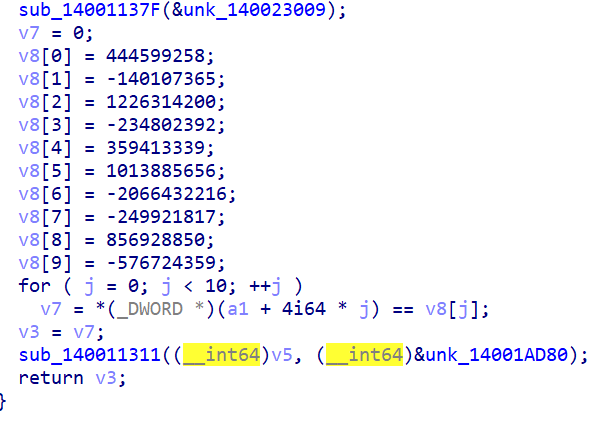
那么就可以开始编写脚本了
#include <stdio.h>
int main()
{
int key[] = { 2233, 4455, 6677, 8899 };
unsigned int result[10];
result[0] = 0x1A800BDA;
result[1] = 0xF7A6219B;
result[2] = 0x491811D8;
result[3] = 0xF2013328;
result[4] = 0x156C365B;
result[5] = 0x3C6EAAD8;
result[6] = 0x84D4BF28;
result[7] = 0xF11A7EE7;
result[8] = 0x3313B252;
result[9] = 0xDD9FE279;
int dalte = 0xF462900;
int i = 0;
int wheel;
int sum = 0;
// 逆算法
for (i = 8; i >= 0; i--)
{
// 轮数
wheel = 33;
sum = dalte * (i + wheel);
while (wheel--)
{
sum -= dalte;
result[i + 1] -= (sum + key[(sum >> 11) & 3]) ^ (result[i] + ((result[i] >> 5) ^ (16 * result[i])));
result[i] -= sum ^ (result[i + 1] + ((result[i + 1] >> 5) ^ (16 * result[i + 1]))) ^ (sum + key[sum & 3]);
}
}
for (i = 0; i <= 9; i++)
{
printf("%x", result[i]);
}
return 0;
}
运行结果为
一眼为16进制,转换一下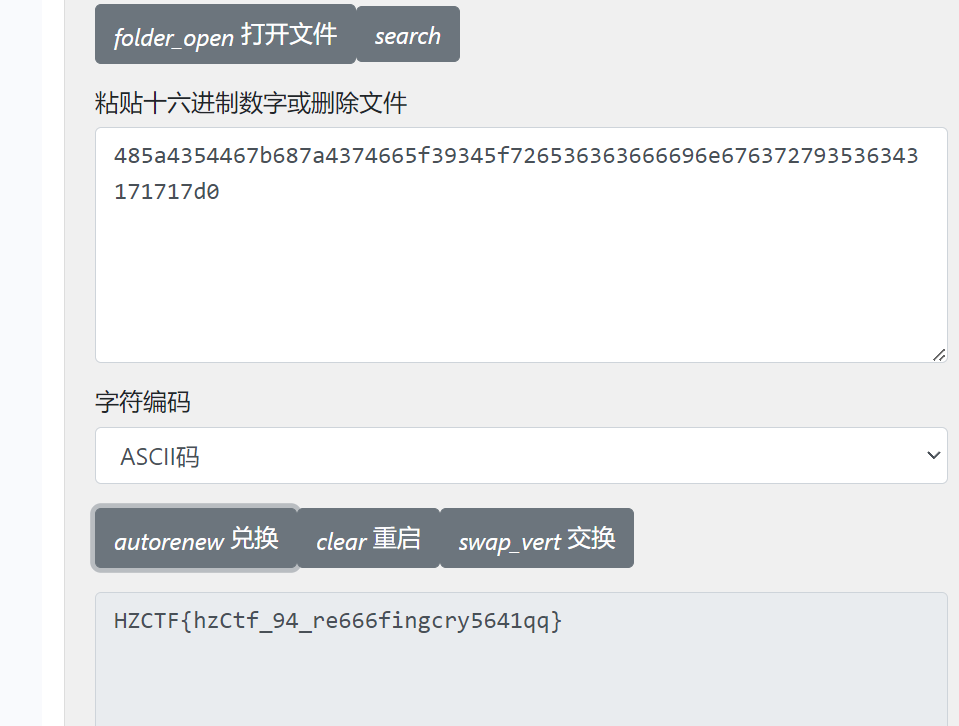
[HGAME 2023 week1]a_cup_of_tea.exe
老规矩,pe查壳,无壳64位,拖进IDA中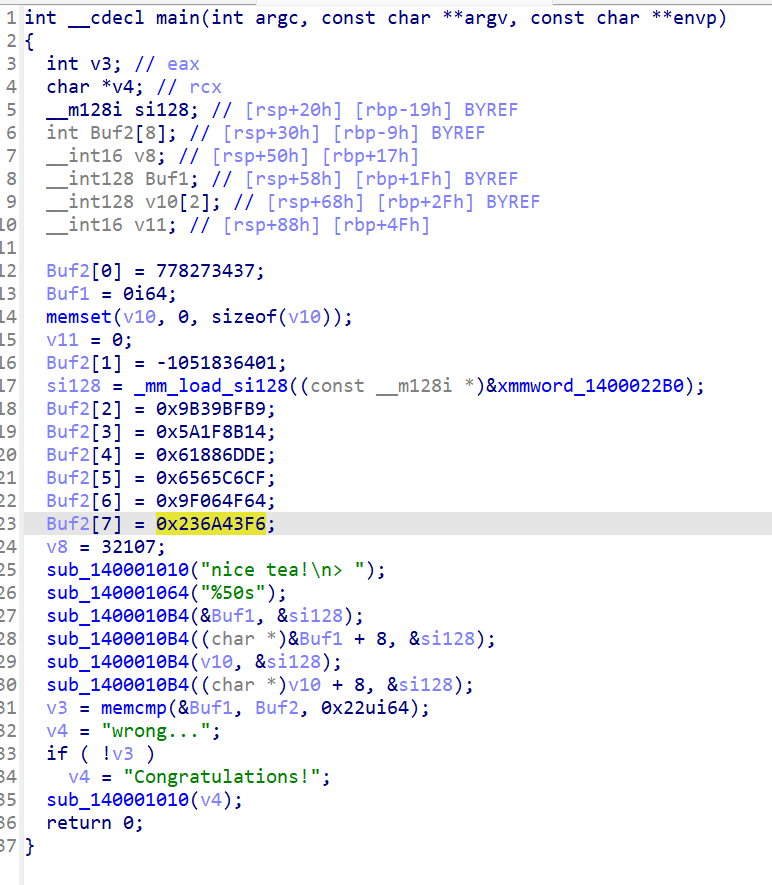
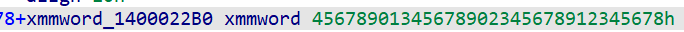
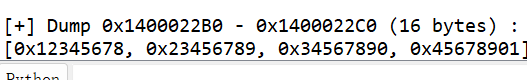
一来就看到了result,点进sub_1400010B4看到了tea模块
key值在这里面
拿到一串16进制数,闫师傅直接上手操作,ddddddd
解密为
得到key为[0x12345678, 0x23456789, 0x34567890, 0x45678901]
编写脚本
#include<stdio.h>
void decrypt(unsigned int* a1, long long* a2)
{
int v2; // ebx
long long v3; // r11d
int v4; // edi
int v5; // esi
int v6; // ebp
unsigned int v7; // r9d
int v8; // rdx
unsigned int v9; // r10d
v2 = *a2;
v3 = 0;
v4 = a2[1];
v5 = a2[2];
v6 = a2[3];
v7 = *a1;
v8 = 32;//wheel
v9 = a1[1];
v3 = -(1412567261 * 32);
do
{
v9 -= (v3 + v7) ^ (v5 + 16 * v7) ^ (v6 + (v7 >> 5));
v7 -= (v3 + v9) ^ (v2 + 16 * v9) ^ (v4 + (v9 >> 5));
v3 += 1412567261;
--v8;
} while (v8);
*a1 = v7;
a1[1] = v9;
}
int main()
{
long long key[4] = { 0x12345678,0x23456789,0x34567890,0x45678901 };
unsigned int Buf2[8] = { 0 };
Buf2[0] = 0x2E63829D;
Buf2[1] = 0xC14E400F;
Buf2[2] = 0x9B39BFB9;
Buf2[3] = 0x5A1F8B14;
Buf2[4] = 0x61886DDE;
Buf2[5] = 0x6565C6CF;
Buf2[6] = 0x9F064F64;
Buf2[7] = 0x236A43F6;
for (int i = 0; i < 8; i += 2)
{
decrypt(Buf2 + i, key);
}
char* p = (char*)Buf2;
for (int j = 0; j < 8 * 4; j++)
{
printf("%c", *(p + j));
}
}
[MoeCTF 2022]ezTea
做完以后发现这个题才是最好入手的TEA题
下载下来后有两个东西,一个pdf一个C源码,打开来看看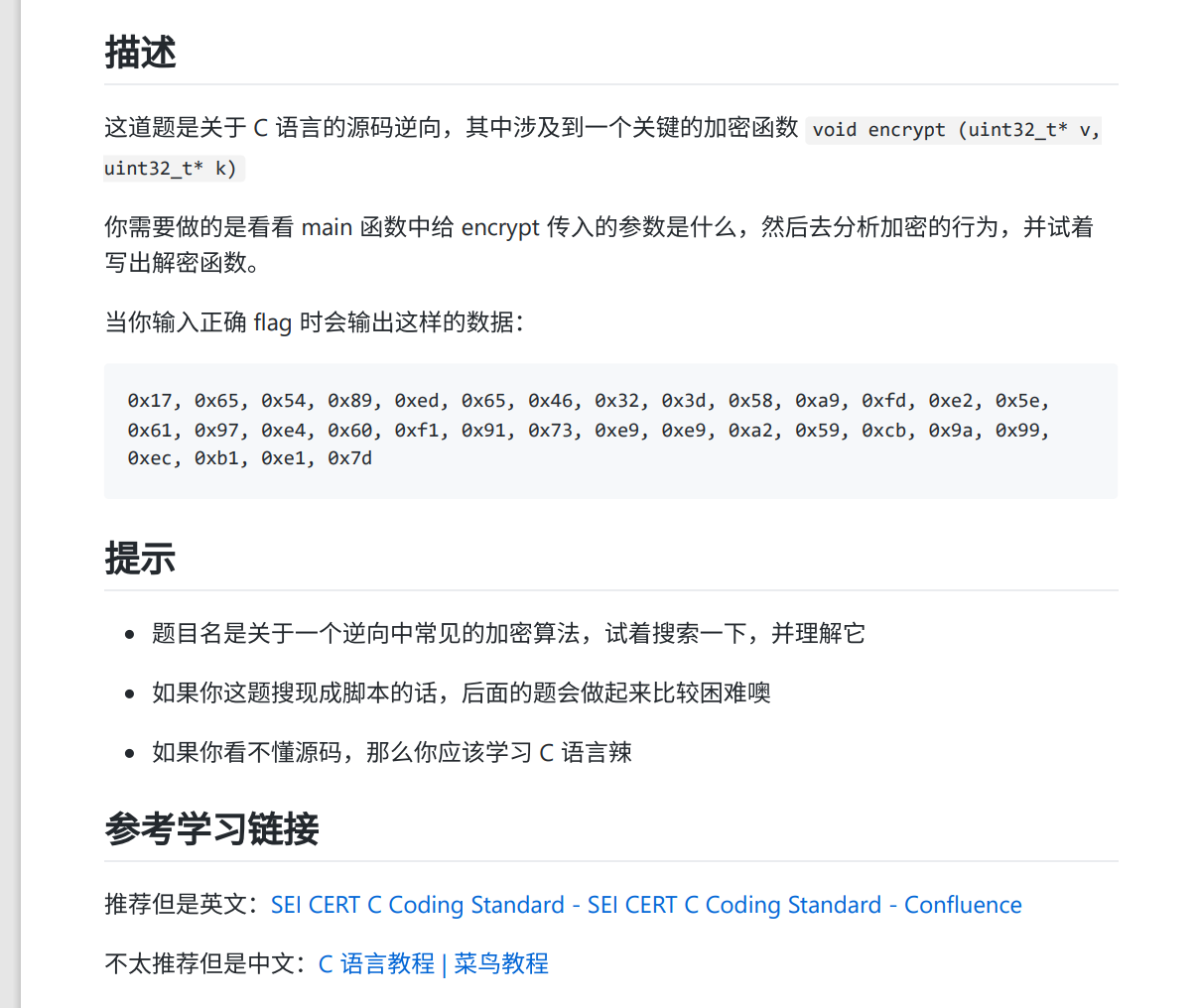
这里我们得知它的result为【0x17, 0x65, 0x54, 0x89, 0xed, 0x65, 0x46, 0x32, 0x3d, 0x58, 0xa9, 0xfd, 0xe2, 0x5e, 0x61, 0x97, 0xe4, 0x60, 0xf1, 0x91, 0x73, 0xe9, 0xe9, 0xa2, 0x59, 0xcb, 0x9a, 0x99, 0xec, 0xb1, 0xe1, 0x7d】再来看看C源码
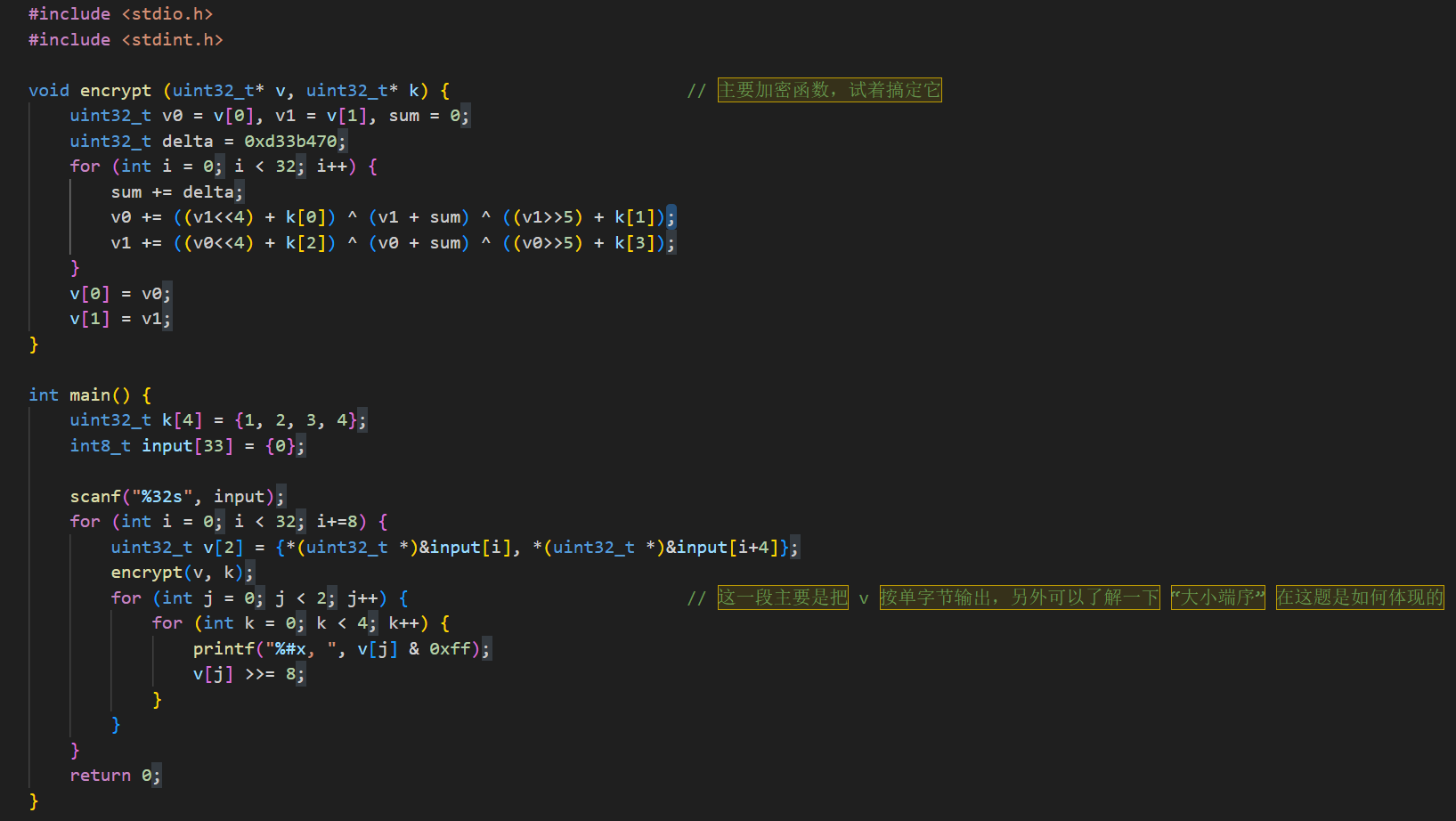
看到了tea模块和key值
那我们就开始编写脚本
#include<stdio.h>
#include <stdint.h>
void decrypt(uint32_t* v, uint32_t* k)
{
uint32_t delta = 0xd33b470;
uint32_t v0 = v[0], v1 = v[1], sum = delta * 32;
for (int i = 0; i < 32; i++)
{
v1 -= ((v0 << 4) + k[2]) ^ (v0 + sum) ^ ((v0 >> 5) + k[3]);
v0 -= ((v1 << 4) + k[0]) ^ (v1 + sum) ^ ((v1 >> 5) + k[1]);
sum -= delta;
}
v[0] = v0;
v[1] = v1;
}
int main()
{
uint32_t k[4] = { 1, 2, 3, 4 };
int8_t input[33] =
{
0x17, 0x65, 0x54, 0x89, 0xed, 0x65, 0x46, 0x32, 0x3d, 0x58, 0xa9, 0xfd, 0xe2, 0x5e,
0x61, 0x97, 0xe4, 0x60, 0xf1, 0x91, 0x73, 0xe9, 0xe9, 0xa2, 0x59, 0xcb, 0x9a, 0x99,
0xec, 0xb1, 0xe1, 0x7d
};
for (int i = 0; i < 32; i += 8)
{
uint32_t v[2] = { *(uint32_t*)&input[i], *(uint32_t*)&input[i + 4] };
decrypt(v, k);
for (int j = 0; j < 2; j++)
{
for (int k = 0; k < 4; k++)
{
printf("%c", v[j] & 0xff);
v[j] >>= 8;
}
}
}
return 0;
}
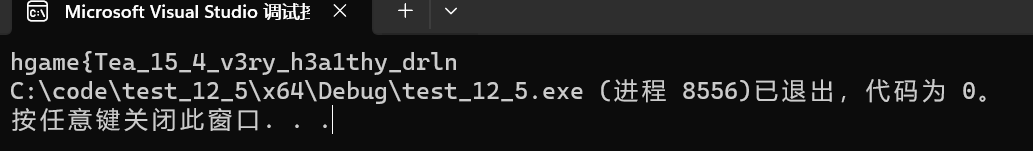
运行得到
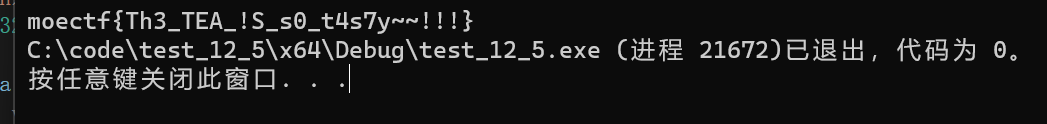
这道题应该放在最前面做才对,因为基础。
[FSCTF 2023]Tea_apk
一道java逆向tea
用jadx打开,看到以下内容

但感觉不像平常的TEA加密,无从下手。网上看了看wp发现这个是XXTEA加密,震惊!
用工具可以直接解开