防火墙区域划分与NAT
任务目的
理解防火墙区域划分方式与流量过滤规则,掌握防火墙安全策略与NAT配置过程
任务设备、设施
Win10、ENSP、VMware、win7、typora
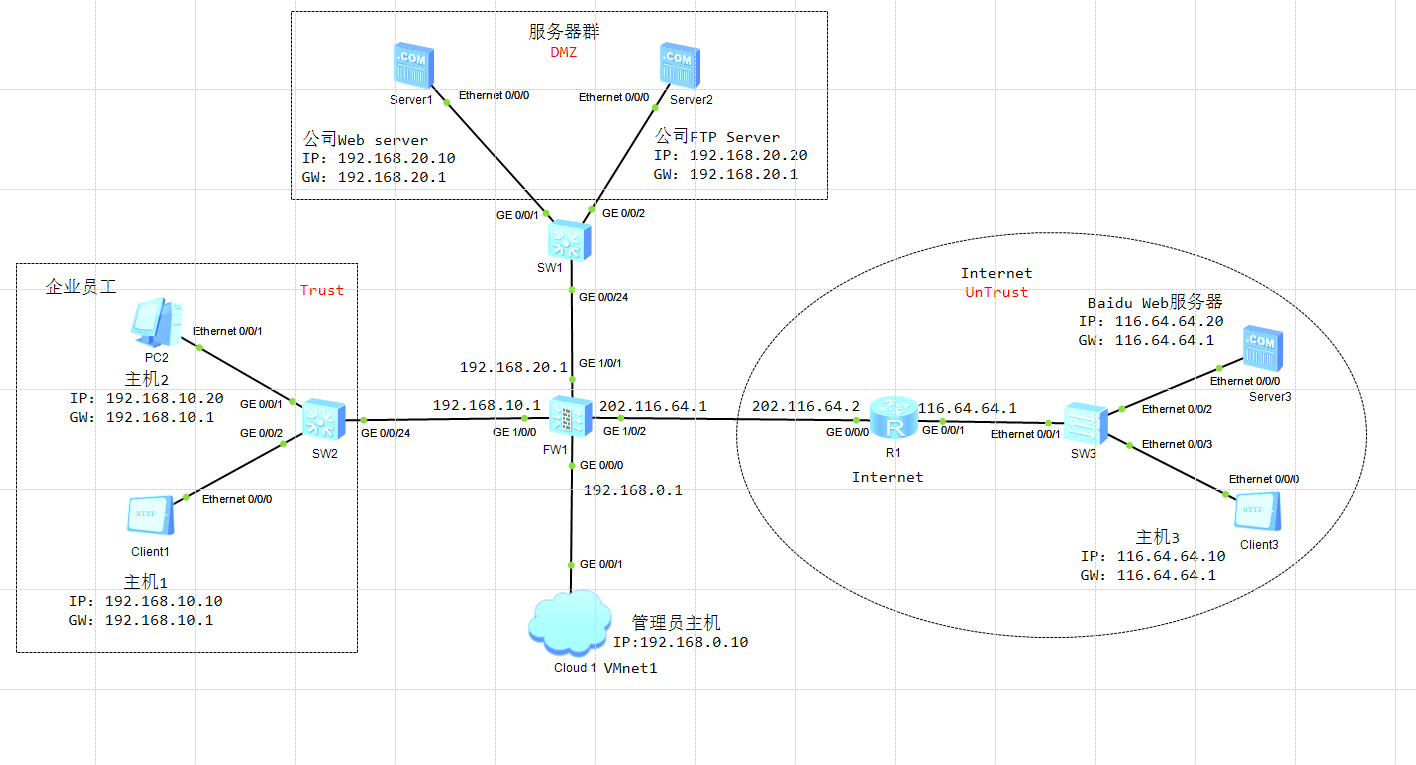
环境拓扑图
配置过程
基本配置
R1
<Huawei>
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]un in en
Info: Information center is disabled.
[Huawei]sys R1
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]ip add 202.116.64.2 24
[R1-GigabitEthernet0/0/0]q
[R1]int g0/0/1
[R1-GigabitEthernet0/0/1]ip add 116.64.64.1 24
[R1-GigabitEthernet0/0/1]q
[R1]
FW1
Username:admin //用户名admin
Password: //密码Admin@123
The password needs to be changed. Change now? [Y/N]: y //需要修改密码
Please enter old password: //输入初始密码
Please enter new password: //输入新密码 可设置为P@ssw0rd
Please confirm new password: //确认新密码
Info: Your password has been changed. Save the change to survive a reboot.
*************************************************************************
* Copyright (C) 2014-2018 Huawei Technologies Co., Ltd. *
* All rights reserved. *
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
*************************************************************************
<USG6000V1>sys
Enter system view, return user view with Ctrl+Z.
[USG6000V1]sys FW1
[FW1]int g0/0/0
[FW1-GigabitEthernet0/0/0]ip add 192.168.0.1 24
[FW1-GigabitEthernet0/0/0]q
[FW1]int g1/0/0
[FW1-GigabitEthernet1/0/0]ip add 192.168.10.1 24
[FW1-GigabitEthernet1/0/0]q
[FW1]int g1/0/1
[FW1-GigabitEthernet1/0/1]ip add 192.168.20.1 24
[FW1-GigabitEthernet1/0/1]q
[FW1]int g1/0/2
[FW1-GigabitEthernet1/0/2]ip add 202.116.64.1 24
[FW1-GigabitEthernet1/0/2]q
[FW1]undo info-center enable
Info: Saving log files...
Info: Information center is disabled.
[FW1]ip route-static 0.0.0.0 0.0.0.0 202.116.64.2
[FW1]
创建区域
[FW1]firewall zone trust
[FW1-zone-trust]add interface g1/0/0
[FW1-zone-trust]q
[FW1]firewall zone dmz
[FW1-zone-dmz]add interface g1/0/1
[FW1-zone-dmz]q
[FW1]firewall zone untrust
[FW1-zone-untrust]add in
[FW1-zone-untrust]add interface g1/0/2
[FW1-zone-untrust]q
[FW1]
配置安全策略,定义区域间互访规则
公司员工访问公网Web服务
[FW1]security-policy
[FW1-policy-security]rule name trust_untrust_web
[FW1-policy-security-rule-trust_untrust_web]source-zone trust
[FW1-policy-security-rule-trust_untrust_web]destination-zone untrust
[FW1-policy-security-rule-trust_untrust_web]source-address 192.168.10.0 24
[FW1-policy-security-rule-trust_untrust_web]service protocol tcp destination-por
t 80
[FW1-policy-security-rule-trust_untrust_web]action permit
[FW1-policy-security-rule-trust_untrust_web]q
[FW1-policy-security]q
[FW1]
公司员工访问dmz Web服务
[FW1]security-policy
[FW1-policy-security]rule name trust_dmz_web
[FW1-policy-security-rule-trust_dmz_web]source-zone trust
[FW1-policy-security-rule-trust_dmz_web]destination-zone dmz
[FW1-policy-security-rule-trust_dmz_web]source-address 192.168.10.0 24
[FW1-policy-security-rule-trust_dmz_web]service protocol tcp destination-port 80
[FW1-policy-security-rule-trust_dmz_web]action permit
[FW1-policy-security-rule-trust_dmz_web]q
[FW1-policy-security]
外网用户访问fmz Ftp服务
[FW1]security-policy
[FW1-policy-security]rule name trust_dmz_ftp
[FW1-policy-security-rule-trust_dmz_ftp]source-zone trust
[FW1-policy-security-rule-trust_dmz_ftp]destination-zone dmz
[FW1-policy-security-rule-trust_dmz_ftp]source-address 192.168.10.0 24
[FW1-policy-security-rule-trust_dmz_ftp]service protocol tcp destination-port 21
[FW1-policy-security-rule-trust_dmz_ftp]action permit
[FW1-policy-security-rule-trust_dmz_ftp]q
外网用户访问dmz Web服务
[FW1]security-policy
[FW1-policy-security]rule name untrust_dmz_web
[FW1-policy-security-rule-untrust_dmz_web]source-zone untrust
[FW1-policy-security-rule-untrust_dmz_web]destination-zone dmz
[FW1-policy-security-rule-untrust_dmz_web]destination-address 192.168.20.10 32
[FW1-policy-security-rule-untrust_dmz_web]service protocol tcp destination-port
80
[FW1-policy-security-rule-untrust_dmz_web]action permit
[FW1-policy-security-rule-untrust_dmz_web]q
[FW1-policy-security]q
[FW1]
外网用户访问dmz Ftp服务
[FW1]security-policy
[FW1-policy-security]rule name untrust_dmz_ftp
[FW1-policy-security-rule-untrust_dmz_ftp]source-zone untrust
[FW1-policy-security-rule-untrust_dmz_ftp]destination-zone dmz
[FW1-policy-security-rule-untrust_dmz_ftp]destination-address 192.168.20.20 32
[FW1-policy-security-rule-untrust_dmz_ftp]service protocol tcp destination-port
21
[FW1-policy-security-rule-untrust_dmz_ftp]action permit
[FW1-policy-security-rule-untrust_dmz_ftp]q
[FW1-policy-security]q
[FW1]
配置Easy-IP
公司员工可以访问公网
[FW1]nat-policy
[FW1-policy-nat]rule name trust_internet
[FW1-policy-nat-rule-trust_internet]source-zone trust
[FW1-policy-nat-rule-trust_internet]destination-zone untrust
[FW1-policy-nat-rule-trust_internet]source-address 192.168.10.0 24
[FW1-policy-nat-rule-trust_internet]action source-nat easy-ip
[FW1-policy-nat-rule-trust_internet]q
[FW1-policy-nat]
公司员工可以访问dmz区域服务器群
[FW1-policy-nat]rule name trust_dmz
[FW1-policy-nat-rule-trust_dmz]source-zone trust
[FW1-policy-nat-rule-trust_dmz]destination-zone dmz
[FW1-policy-nat-rule-trust_dmz]source-address 192.168.10.0 24
[FW1-policy-nat-rule-trust_dmz]action source-nat easy-ip
[FW1-policy-nat-rule-trust_dmz]q
[FW1-policy-nat]
配置NAT server 发布DMZ区域web站点和ftp站点
[FW1]nat server company_web_server protocol tcp global 202.116.64.1 www inside 1
92.168.20.10 www
[FW1]nat server company_ftp_server protocol tcp global 202.116.64.1 ftp inside 1
92.168.20.20 ftp
[FW1]
任务验证
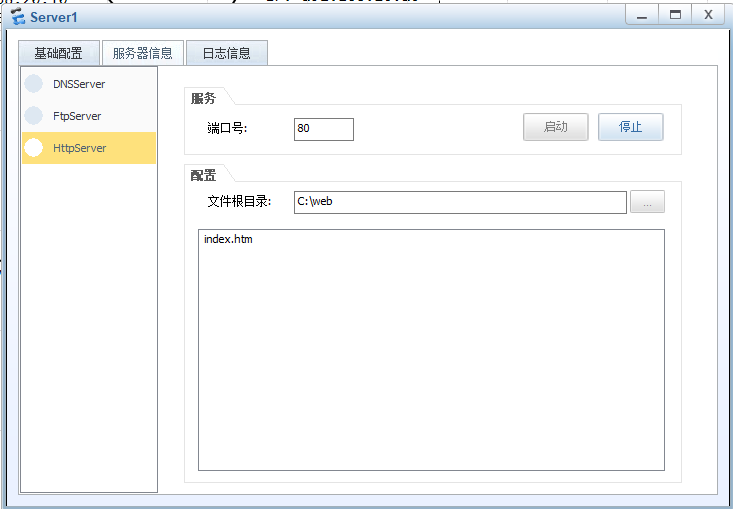
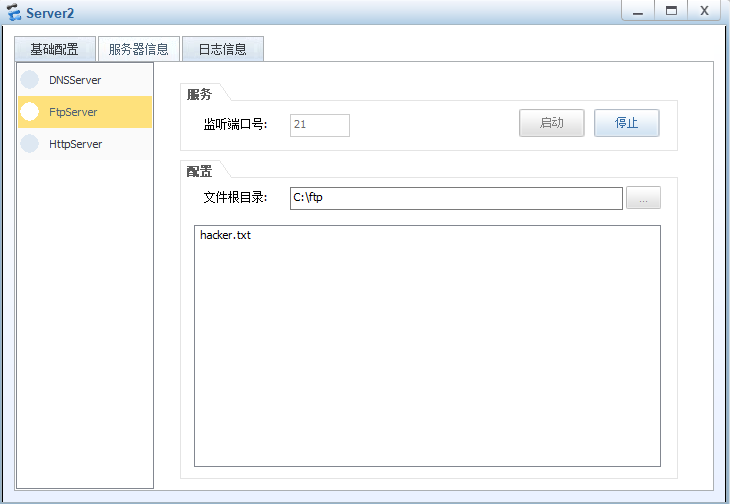
在server1发布web站点,ftp站点
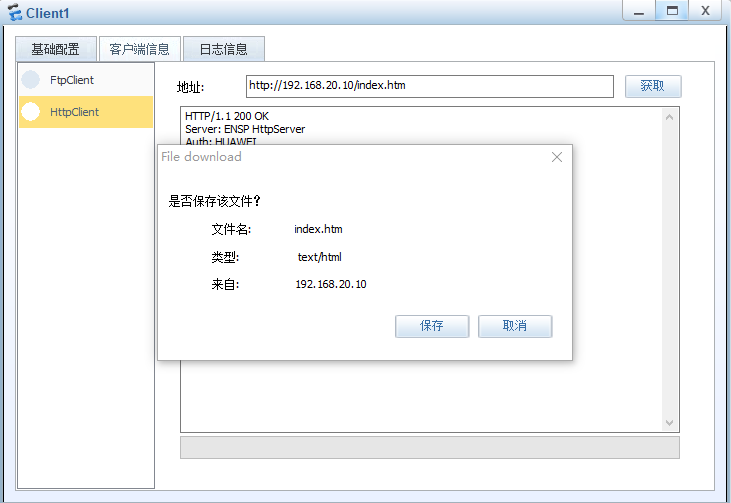
主机1可以访问公司web server和ftp server
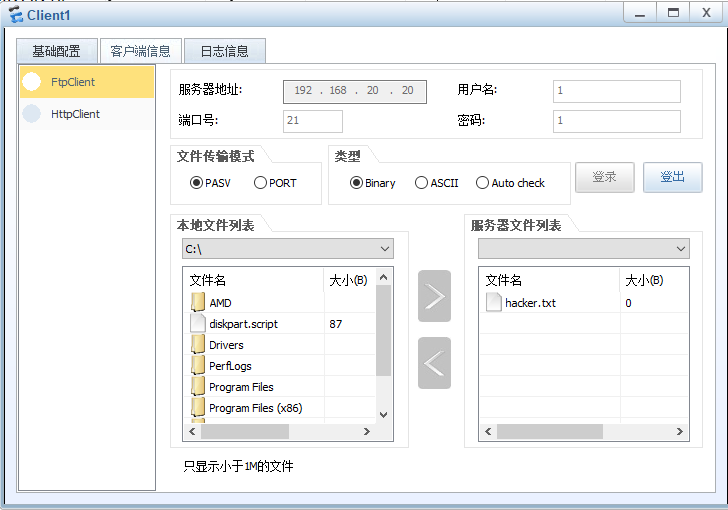
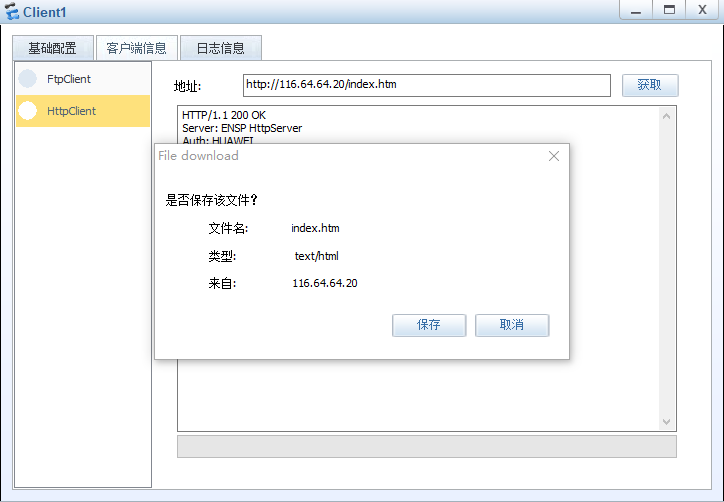
主机1可以访问baidu web服务器
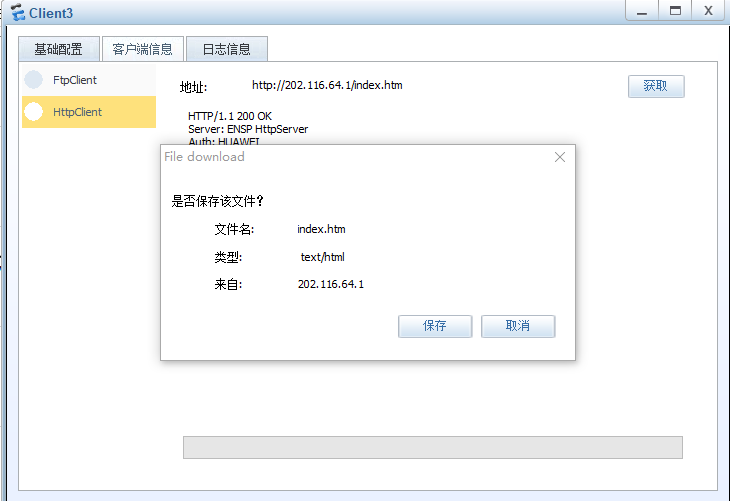
主机3可以访问公司web server和ftpserver

入侵实战(任务扩展)
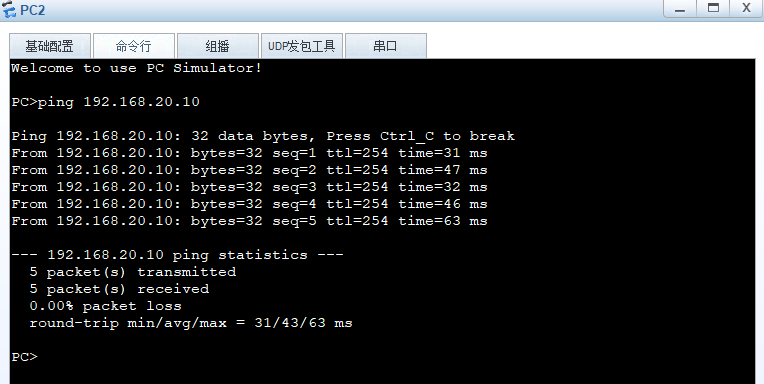
企业员工要ping通服务器群
[FW1]security-policy
[FW1-policy-security]rule name trust_dmz_icmp
[FW1-policy-security-rule-trust_dmz_icmp]source-zone trust
[FW1-policy-security-rule-trust_dmz_icmp]destination-zone dmz
[FW1-policy-security-rule-trust_dmz_icmp]source-address 192.168.10.0 24
[FW1-policy-security-rule-trust_dmz_icmp]service icmp
[FW1-policy-security-rule-trust_dmz_icmp]action permit
[FW1-policy-security-rule-trust_dmz_icmp]q
[FW1-policy-security]
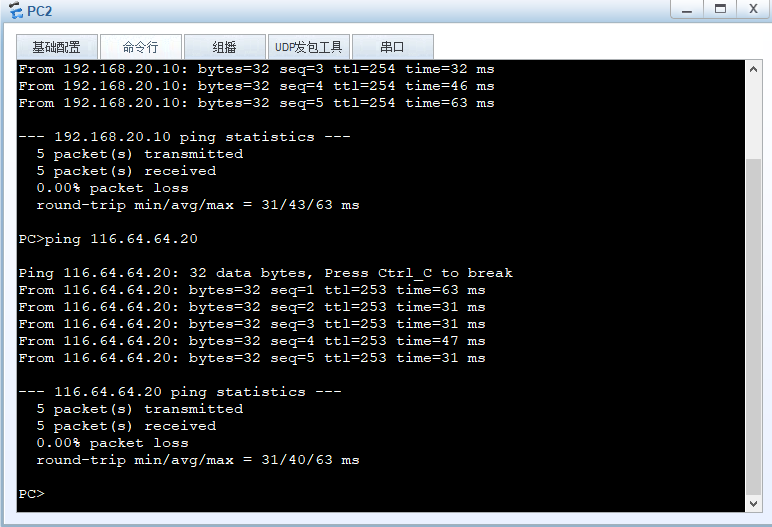
企业员工要ping通Internet
[FW1]security-policy
[FW1-policy-security]rule name trust_untrust_icmp
[FW1-policy-security-rule-trust_untrust_icmp]source-zone trust
[FW1-policy-security-rule-trust_untrust_icmp]destination-zone untrust
[FW1-policy-security-rule-trust_untrust_icmp]source-address 192.168.10.0 24
[FW1-policy-security-rule-trust_untrust_icmp]service icmp
[FW1-policy-security-rule-trust_untrust_icmp]action permit
[FW1-policy-security-rule-trust_untrust_icmp]q
[FW1-policy-security]
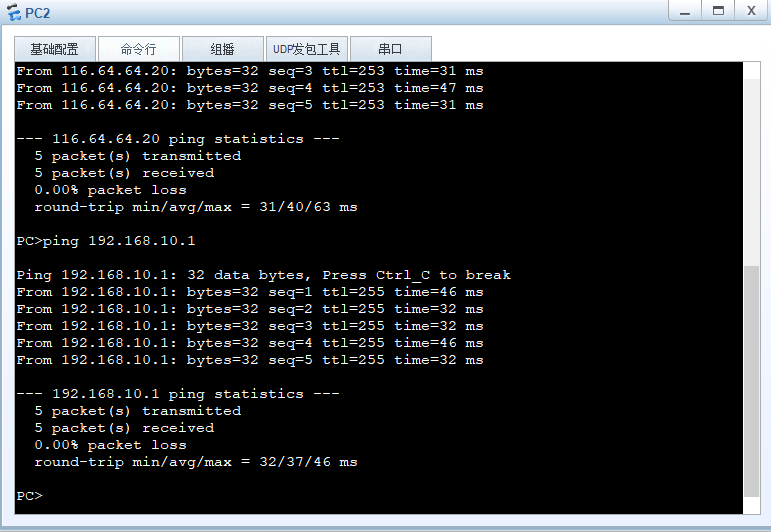
企业员工要ping通防火墙
[FW1]int g1/0/0
[FW1-GigabitEthernet1/0/0]serv
[FW1-GigabitEthernet1/0/0]service-mana
[FW1-GigabitEthernet1/0/0]service-manage ping permit
[FW1-GigabitEthernet1/0/0]q
[FW1]
任务总结
对于防火墙来说原则上默认禁止所有区域访问。假如配置安全策略,如允许Trust区域访问UnTrust区域,UnTrust区域默认不允许访问Trust区域,则:
- Trust区域主机可以主动向UnTrust区域主机发起连接,UnTrust返回的应答报文也能正常
- UnTrust区域主机不能主动向Trust区域主机发起连接,但是可以被动响应Trust区域主机发起的连接
补充
如何删除NAT Server
[FW1]undo nat server name [nat server名字]
[FW1]undo nat server ID 0
第一个基于名字的删除
第二个是基于ID号删除
在系统视图 使用dis this 然后翻到最后,可以看到name及ID号