概述
虽然现在由SDN参与的园区网方案大行其道,但仍然有大量的企业还在使用传统的网络架构,华为有一套非常的经典的传统园区网解决方案,几乎适合大多数园区,做为一个有追求的网络工程师,此等经典案例,不可不学!
PS:此实验仅是简化版本,去除了NAT、堆叠、策略路由
拓扑&思路
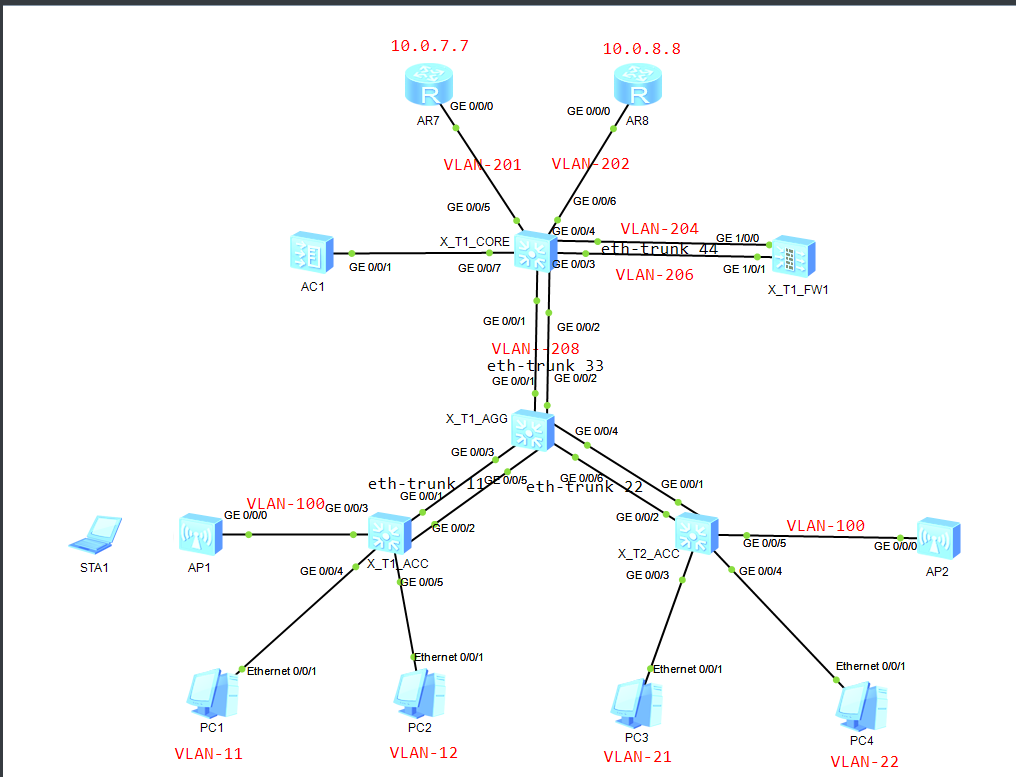
PS: 此套拓扑当前没有堆叠,按理说应该要有堆叠的,但因ENSP无法模拟堆叠,所以在这里就没有将堆叠体现出来。
介绍
- 实验最终的目的是:有线vlan11可以访问外网、有线和无线用户可以互访
- 公司内部的业务分为有线和无线,有线vlan11、12、21、22、无线的管理vlan100、无线业务vlan31
- 有线的网关集中在汇聚AGG上
- 无线采用集中式转发,由管理vlan100通过capwap隧道运载到AC上,再由AC通过VLAN31交给在核心的无线网关
- 有线的网关在汇聚上,但DHCP在核心上,通过vlan208互联,也就是说vlan208是整个有线的聚合
- vlan208、vlan31、以及与虚拟防火墙连接的vlan206,都放置到了虚拟网络VN上
- 防火墙上通过虚拟防火墙与之对接
- 核心上不仅有有线的地址池、也有无线的地址池,都绑定在了一个VN上
- 最终结果做完之后就是有线和无线都可以相互连通
- 有线或无线下的主机都可以通过防火墙连接外网
本实验有一个特别需要注意的地方,那就是实验步骤的第九步,涉及到虚拟防火墙计算5类的LSA的,需要在OSPF进程里面特别敲一个命令(vpn-instance-capability simple),具体情况请直接查看实验步骤当中的第九步!
本实验的难点就在于核心交换机与虚拟防火墙之间的VLAN接口,OSPF连接上,关键配置写在下一小节了!
另外所有的DHCP地址池都放在了核心上,而且所有的地址都绑定了VN,注意绑定的方法
关键配置
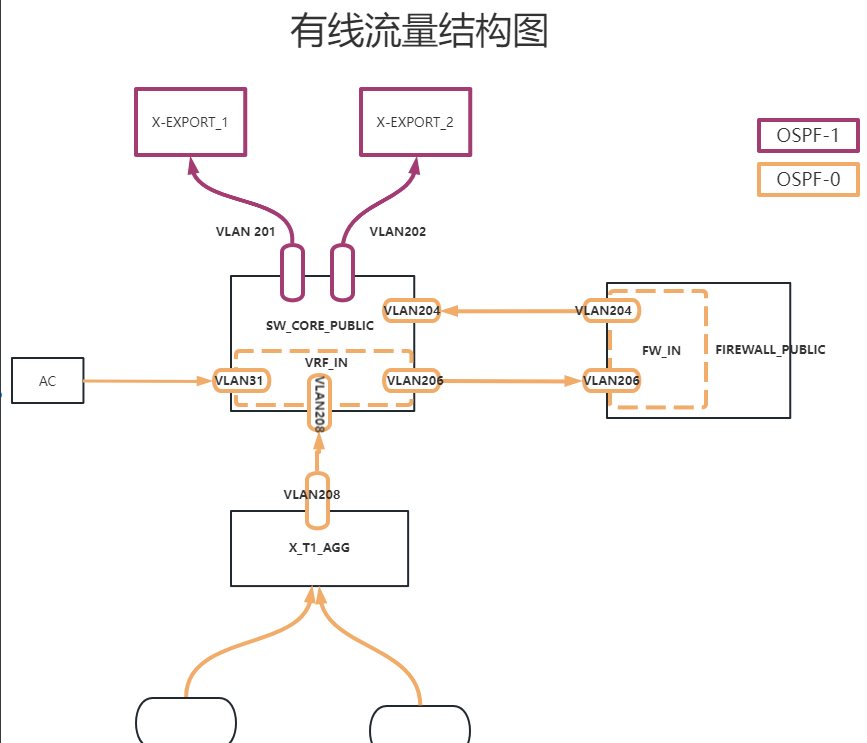
# CORE关键VLAN配置
# CORE
ip vpn-instance IN
# 无线网关
int vlan 31
ip binding vpn-instance IN
# 有线下一跳
int vlan 208
ip binding vpn-instance IN
# 与防火墙连接VN
int vlan 206
ip binding vpn-instance IN
# CORE只有vlan 204不在IN,而是根实例
# CORE关键OSPF配置
ospf 1 vpn-instance IN
a 1 # 对接防火墙
network vlanfif 31
network vlanfif 208
network vlanfif 206
ospf 2
a 0 # 对接外部网络
network vlanfif 201
network vlanfif 202
a 1 # 对接防火墙
network vlanfif 204
# 防火墙关键OSPF配置
ospf 1 vpn-instance IN # 对接核心交换机
a 1
network vlanfif 206
network vlanfif 204
实验步骤
1. 先把链路聚合做好
# X_T1_ACC
sys
sysn X_T1_ACC
vlan batch 100 11 12
int eth-trunk 11
mode lacp-sta
port link-type trunk
port trunk allow vlan 100 11 12
trunkport g0/0/1
trunkport g0/0/2
quit
# X_T2_ACC
sys
sysn X_T2_ACC
vlan batch 100 21 22
int eth-trunk 22
mode lacp-sta
port link-type trunk
port trunk allow vlan 100 21 22
trunkport g0/0/1
trunkport g0/0/2
quit
# X_T1_AGG
sys
sysn X_T1_AGG
vlan batch 100 11 12 21 22 208
int eth-trunk 11
mode lacp-sta
port link-type trunk
port trunk allow vlan 100 11 12
trunkport g0/0/3
trunkport g0/0/5
quit
int eth-trunk 22
mode lacp-sta
port link-type trunk
port trunk allow vlan 100 21 22
trunkport g0/0/4
trunkport g0/0/6
quit
int eth-trunk 33
mode lacp-sta
port link-type trunk
port trunk allow vlan 100 208
trunkport g0/0/1
trunkport g0/0/2
quit
# X_T1_CORE
sys
sysn X_T1_CORE
vlan batch 100 208 206 204 201 202
int eth-trunk 33
mode lacp-sta
port link-type trunk
port trunk allow vlan 100 208
trunkport g0/0/1
trunkport g0/0/2
quit
int eth-trunk 44
mode lacp-sta
port link-type trunk
port trunk allow vlan 204 206
trunkport g0/0/3
trunkport g0/0/4
quit
# X_T1_FW1
sysn X_T1_FW1
vlan batch 204 206
int eth-trunk 44
portsw
mode lacp-sta
port link-type trunk
port trunk allow vlan 204 206
trunkport g1/0/0
trunkport g1/0/1
quit
# 校验命令
dis eth-trunk 33
dis interface eth-trunk 44
2. 让两台无线AP获取管理地址
PS:我们使用集中式转发
# X_T1_ACC
int g0/0/3
port link-type access
port de vlan 100
# X_T2_ACC
int g0/0/5
port link-type access
port de vlan 100
# AC1
sys
sysn AC1
vlan 100
dhcp enable
int g0/0/1
port link-type trunk
port trunk allow vlan 100
int vlan 100
# 无线的管理网段
ip add 10.1.100.254 24
dhcp select interface
# X_T1_CORE
int g0/0/7
port link-type trunk
port trunk allow vlan 100
# 校验一下,去两台AP看是否获取到了IP地址
dis ip int bri
3. 有线网关放在汇聚
我们将有线的网关放到汇聚之后,还要配置OSPF,有与核心相连的接口,以及四个网关都宣告进入OSPF进程1当中区域1当中,为什么是区域1呢?根据题目需求,我们这里就该配置成区域1
# X_T1_AGG
int vlan 11
ip add 192.168.11.254 24
int vlan 12
ip add 192.168.12.254 24
int vlan 21
ip add 192.168.21.254 24
int vlan 22
ip add 192.168.22.254 24
int vlan 208
ip add 192.168.208.254 24
ospf 1
a 1
network 192.168.208.254 0.0.0.0
network 192.168.11.254 0.0.0.0
network 192.168.12.254 0.0.0.0
network 192.168.21.254 0.0.0.0
network 192.168.22.254 0.0.0.0
network 192.168.208.254 0.0.0.0
quit
4. 有线流量引导到核心VN
- 在核心上先创建VN,然后把208放到VN当中
- 在VN当中支行OSPF进程1,区域1,把汇聚当中的四个VLAN的流量接引过来
# X_T1_CORE
ip vpn-instance IN
route-dist 1:1
int vlan 208
ip binding vpn-instance IN
ip add 192.168.208.1 24
ospf 1 vpn-instance IN
a 1
network 192.168.208.1 0.0.0.0
quit
# 在核心上校验一下
[X_T1_CORE]dis ospf peer brief
OSPF Process 1 with Router ID 192.168.208.1
Peer Statistic Information
----------------------------------------------------------------------------
Area Id Interface Neighbor id State
0.0.0.1 Vlanif208 192.168.11.254 Full
----------------------------------------------------------------------------
[X_T1_CORE]dis ip rou
[X_T1_CORE]dis ip routing-table vpn
[X_T1_CORE]dis ip routing-table vpn-instance IN
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Routing Tables: IN
Destinations : 6 Routes : 6
Destination/Mask Proto Pre Cost Flags NextHop Interface
192.168.11.0/24 OSPF 10 2 D 192.168.208.254 Vlanif208
192.168.12.0/24 OSPF 10 2 D 192.168.208.254 Vlanif208
192.168.21.0/24 OSPF 10 2 D 192.168.208.254 Vlanif208
192.168.22.0/24 OSPF 10 2 D 192.168.208.254 Vlanif208
192.168.208.0/24 Direct 0 0 D 192.168.208.1 Vlanif208
192.168.208.1/32 Direct 0 0 D 127.0.0.1 Vlanif208
5. 有线流量再引导到虚拟防火墙上
- 我们已经在核心上配置了VN,我们接下来要在防火墙上创建虚拟防火墙,核心上的VN与虚拟防火墙之前通过vlan 206连接,也要运行OSPF进程1区域1,把流量顺利的引导到防火墙上。
- 流量到了虚拟防火墙之后,还要再流出到核心的根实例上,流出时的vlan通过vlan204对接
- 也就是将vlan206放到trunk区域当中,把vlan204放到untrust当中,这两个接口都要放到虚拟防火墙当中
# X_T1_FW1
vlan batch 204 206
# 必须先创建接口,才能把接口加入到虚拟防火墙当中
int vlan 204
quit
int vlan 206
quit
vsys enable
vsys name IN
ass vlan 206
ass vlan 204
quit
switch vsyn IN
sys
int vlan 204
ip add 10.0.204.254 24
service-manage ping permit
int vlan 206
ip add 10.0.206.254 24
service-manage ping permit
firewall zone trust
add interface vlan 206
firewall zone untrust
add interface vlan 204
quit
quit
quit
ospf 1 vpn-instance IN
a 1
network 10.0.206.254 0.0.0.0
network 10.0.204.254 0.0.0.0
# X_T1_CORE
int vlan 206
ip binding vpn-instance IN
ip add 10.0.206.1 24
ospf 1 vpn-instance IN
a 1
network 10.0.206.1 0.0.0.0
quit
# 校验一上,防火墙上当前已经获取了有线的网段
[X_T1_FW1]dis ip routing-table vpn-instance IN protocol ospf
2023-06-30 19:24:39.210
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
IN routing table : OSPF
Destinations : 5 Routes : 5
OSPF routing table status : <Active>
Destinations : 5 Routes : 5
Destination/Mask Proto Pre Cost Flags NextHop Interface
192.168.11.0/24 OSPF 10 3 D 10.0.206.1 Vlanif206
192.168.12.0/24 OSPF 10 3 D 10.0.206.1 Vlanif206
192.168.21.0/24 OSPF 10 3 D 10.0.206.1 Vlanif206
192.168.22.0/24 OSPF 10 3 D 10.0.206.1 Vlanif206
192.168.208.0/24 OSPF 10 2 D 10.0.206.1 Vlanif206
OSPF routing table status : <Inactive>
Destinations : 0 Routes : 0
6. 从虚拟防火墙上引导到核心根实例
# X_T1_CORE
# 注意,根实例接口不加入任何VN
int vlan 204
ip add 10.0.204.1 24
# 在根实例上,我们通过OSPF进程2区域1与虚拟防火墙对接
ospf 2
a 1
network 10.0.204.1 0.0.0.0
quit
# 校验,X_T1_CORE已经获取了有线的业务网段信息
[X_T1_CORE]dis ip routing-table protocol ospf
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Public routing table : OSPF
Destinations : 6 Routes : 6
OSPF routing table status : <Active>
Destinations : 6 Routes : 6
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.0.206.0/24 OSPF 10 2 D 10.0.204.254 Vlanif204
192.168.11.0/24 OSPF 10 4 D 10.0.204.254 Vlanif204
192.168.12.0/24 OSPF 10 4 D 10.0.204.254 Vlanif204
192.168.21.0/24 OSPF 10 4 D 10.0.204.254 Vlanif204
192.168.22.0/24 OSPF 10 4 D 10.0.204.254 Vlanif204
192.168.208.0/24 OSPF 10 3 D 10.0.204.254 Vlanif204
OSPF routing table status : <Inactive>
Destinations : 0 Routes : 0
7. 通过区域0与外部网络对接
# X_T1_CORE
vlan batch 201 202
int vlan 201
ip add 10.0.201.1 24
int vlan 202
ip add 10.0.202.1 24
int g0/0/5
port link-type access
port de vlan 201
int g0/0/6
port link-type access
port de vlan 202
# 通过OSPF进程2,区域0来对接
ospf 2
a 0
network 10.0.201.1 0.0.0.0
network 10.0.202.1 0.0.0.0
quit
# AR7
sys
sysn AR7
int l0
ip add 10.0.7.7 32
int g0/0/0
ip add 10.0.201.254 24
ospf 2
a 0
network 10.0.201.254 0.0.0.0
network 10.0.7.7 0.0.0.0
quit
# AR8
sys
sysn AR8
int l0
ip add 10.0.8.8 32
int g0/0/0
ip add 10.0.202.254 24
ospf 2
a 0
network 10.0.202.254 0.0.0.0
network 10.0.8.8 0.0.0.0
quit
# 校验一下,AR7和AR8都顺利获取了有线业务的网段
<AR8>dis ip routing-table protocol ospf
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Public routing table : OSPF
Destinations : 9 Routes : 9
OSPF routing table status : <Active>
Destinations : 9 Routes : 9
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.0.7.7/32 OSPF 10 2 D 10.0.202.1 GigabitEthernet
0/0/0
10.0.201.0/24 OSPF 10 2 D 10.0.202.1 GigabitEthernet
0/0/0
10.0.204.0/24 OSPF 10 2 D 10.0.202.1 GigabitEthernet
0/0/0
10.0.206.0/24 OSPF 10 3 D 10.0.202.1 GigabitEthernet
0/0/0
192.168.11.0/24 OSPF 10 5 D 10.0.202.1 GigabitEthernet
0/0/0
192.168.12.0/24 OSPF 10 5 D 10.0.202.1 GigabitEthernet
0/0/0
192.168.21.0/24 OSPF 10 5 D 10.0.202.1 GigabitEthernet
0/0/0
192.168.22.0/24 OSPF 10 5 D 10.0.202.1 GigabitEthernet
0/0/0
192.168.208.0/24 OSPF 10 4 D 10.0.202.1 GigabitEthernet
0/0/0
OSPF routing table status : <Inactive>
Destinations : 0 Routes : 0
<AR7>dis ip routing-table protocol ospf
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Public routing table : OSPF
Destinations : 9 Routes : 9
OSPF routing table status : <Active>
Destinations : 9 Routes : 9
Destination/Mask Proto Pre Cost Flags NextHop Interface
10.0.8.8/32 OSPF 10 2 D 10.0.201.1 GigabitEthernet
0/0/0
10.0.202.0/24 OSPF 10 2 D 10.0.201.1 GigabitEthernet
0/0/0
10.0.204.0/24 OSPF 10 2 D 10.0.201.1 GigabitEthernet
0/0/0
10.0.206.0/24 OSPF 10 3 D 10.0.201.1 GigabitEthernet
0/0/0
192.168.11.0/24 OSPF 10 5 D 10.0.201.1 GigabitEthernet
0/0/0
192.168.12.0/24 OSPF 10 5 D 10.0.201.1 GigabitEthernet
0/0/0
192.168.21.0/24 OSPF 10 5 D 10.0.201.1 GigabitEthernet
0/0/0
192.168.22.0/24 OSPF 10 5 D 10.0.201.1 GigabitEthernet
0/0/0
192.168.208.0/24 OSPF 10 4 D 10.0.201.1 GigabitEthernet
0/0/0
OSPF routing table status : <Inactive>
Destinations : 0 Routes : 0
<AR7>
8. 有线dhcp设置
有线的网关的汇聚上,但是根据题目要求我们需要把地址池放在核心上
# X_T1_AGG
interface Vlanif11
dhcp select relay
dhcp relay server-ip 192.168.208.1
interface Vlanif12
dhcp select relay
dhcp relay server-ip 192.168.208.1
interface Vlanif21
dhcp select relay
dhcp relay server-ip 192.168.208.1
interface Vlanif22
dhcp select relay
dhcp relay server-ip 192.168.208.1
# X_T1_CORE
dhcp enable
ip pool vlan11
# 注意这一步, 要将地址池绑定到对应的VN当中,否则地址池不生效的!
**vpn-instance IN**
network 192.168.11.0 mask 24
gateway 192.168.11.254
ip pool vlan12
vpn-instance IN
network 192.168.12.0 mask 24
gateway 192.168.12.254
ip pool vlan21
vpn-instance IN
network 192.168.21.0 mask 24
gateway 192.168.21.254
ip pool vlan22
vpn-instance IN
network 192.168.22.0 mask 24
gateway 192.168.22.254
[X_T1_CORE-ip-pool-vlan22]int vlan 208
[X_T1_CORE-Vlanif208]dhcp select global
# x_t1_acc
interface GigabitEthernet0/0/4
port link-type access
port default vlan 11
interface GigabitEthernet0/0/5
port link-type access
port default vlan 12
# x_t2_acc
interface GigabitEthernet0/0/3
port link-type access
port default vlan 21
interface GigabitEthernet0/0/4
port link-type access
port default vlan 22
PS:保证所有的PC都能获取到IP地址
9. 让所有PC能上网(坑点!)
第一步:在两台外网路由器的OSPF区域0当中下发默认路由
# 两台外网路由器
ospf 2
a 0
default-route-adver always
第二步:防火墙要放行从trust到untrust
[X_T1_FW1]switch vsys IN
<X_T1_FW1-IN>sys
[X_T1_FW1-IN]security-policy
[X_T1_FW1-IN-policy-security]dis th
security-policy
rule name test-1
source-zone trust
destination-zone untrust
source-address 192.168.11.0 mask 255.255.255.0
source-address 1
第三步:发现虚拟防火墙上和核心上的实例没有外网路由,但是AGG设备却有路由,非常奇怪!(坑点!)
OSPF当中有一个知识点,设备通过非骨干区域接收到外部路由(比如五类)时,原因是非骨干传出出去的五类DN不为1 ,当有设备接收到这条DN不为1的五类路由时,是不会计算路由器的。但在我们当前这个有虚拟VN参与的环境,虚拟系统(虚拟防火墙和核心上的IN实例)接收到外部路由,无论是DN是否为1,都不会计算路由(但会继续传递),这是防环的措施。所以最终虚拟防火墙和核心的VN上都没有外部路由,但最终传递到AGG设备,AGG设备是实体,所以AGG会计算出来!
# 虚拟防火墙上当中写一条命令,让它计算
ospf 1
vpn-instance-capability simple
# CORE的IN实例当中写一条命令,让它计算
ospf 1
vpn-instance-capability simple
第四步:校验
# 校验
PC>ipconfig
Link local IPv6 address...........: fe80::5689:98ff:fe7f:5953
IPv6 address......................: :: / 128
IPv6 gateway......................: ::
IPv4 address......................: 192.168.11.253
Subnet mask.......................: 255.255.255.0
Gateway...........................: 192.168.11.254
Physical address..................: 54-89-98-7F-59-53
DNS server........................:
PC>ping 10.0.7.7
Ping 10.0.7.7: 32 data bytes, Press Ctrl_C to break
From 10.0.7.7: bytes=32 seq=1 ttl=251 time=110 ms
From 10.0.7.7: bytes=32 seq=2 ttl=251 time=125 ms
From 10.0.7.7: bytes=32 seq=3 ttl=251 time=109 ms
From 10.0.7.7: bytes=32 seq=4 ttl=251 time=109 ms
From 10.0.7.7: bytes=32 seq=5 ttl=251 time=125 ms
--- 10.0.7.7 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 109/115/125 ms
10. AC下发配置
无线通过隧道模式转发的,AP通过VLAN100进行封装,发送到AC上,然后AC再通过VLAN31再扔到核心设备上的无线网关上,也就是说无线用户的网关要放到核心上。
这个无线是给内部用户用的,所以也要跟企业内部的有线用户一个实例
# CORE
# vlan31是无线的业务VLAN
vlan 31
int vlan 31
ip binding vpn-instance IN
ip add 10.0.31.254 24
dhcp select global
ip pool vlan31
vpn-instance IN
network 10.0.31.0 mask 24
gateway 10.0.31.254
int g0/0/7
port trunk allow vlan 31
quit
## OSPF1-区域1也加上这个网段
## 这样有线和无线就通了
ospf 1
a 1
network 10.0.31.0 0.0.0.255
quit
# AC
vlan 31
int g0/0/1
port trunk allow vlan 31
quit
# AC的无线配置
vlan 31
quit
int vlan 31
ip add 10.0.31.1 24
quit
capwap source interface Vlanif 31
wlan
regulatory-domain-profile name default
country-code cn
quit
ap-group name test_group
# 这一步必须手动,敲Y
regulatory-domain-profile default
quit
ap auth-mode mac-auth
ap-id 1 ap-mac 00e0-fc98-29b0
ap-name AP1
# 这一步必须手动,敲Y
ap-group test_group
quit
ap-id 2 ap-mac 00e0-fc48-3be0
ap-name AP2
# 这一步必须手动,敲Y
ap-group test_group
quit
wlan
security-profile name wlan_sec_profile
security wpa-wpa2 psk pass-phrase a1234567 aes
quit
ssid-profile name ssid_profile
ssid HCIE
quit
vap-profile name wlan-net
forward-mode tunnel
service-vlan vlan-id 31
security-profile wlan_sec_profile
ssid-profile ssid_profile
ap-group name test_group
vap-profile wlan-net wlan 1 radio all
最终结果
有线无线之间全部通畅!!!
STA>ipconfig
Link local IPv6 address...........: ::
IPv6 address......................: :: / 128
IPv6 gateway......................: ::
IPv4 address......................: 10.0.31.252
Subnet mask.......................: 255.255.255.0
Gateway...........................: 10.0.31.254
Physical address..................: 54-89-98-B6-4D-47
DNS server........................:
STA>ping 192.168.11.253
Ping 192.168.11.253: 32 data bytes, Press Ctrl_C to break
From 192.168.11.253: bytes=32 seq=1 ttl=126 time=250 ms
From 192.168.11.253: bytes=32 seq=2 ttl=126 time=281 ms
From 192.168.11.253: bytes=32 seq=3 ttl=126 time=281 ms
From 192.168.11.253: bytes=32 seq=4 ttl=126 time=266 ms
From 192.168.11.253: bytes=32 seq=5 ttl=126 time=234 ms
PC>ipconfig
Link local IPv6 address...........: fe80::5689:98ff:fe7f:5953
IPv6 address......................: :: / 128
IPv6 gateway......................: ::
IPv4 address......................: 192.168.11.253
Subnet mask.......................: 255.255.255.0
Gateway...........................: 192.168.11.254
Physical address..................: 54-89-98-7F-59-53
DNS server........................:
PC>ping 10.0.31.252
Ping 10.0.31.252: 32 data bytes, Press Ctrl_C to break
From 10.0.31.252: bytes=32 seq=1 ttl=126 time=235 ms
From 10.0.31.252: bytes=32 seq=2 ttl=126 time=265 ms
From 10.0.31.252: bytes=32 seq=3 ttl=126 time=235 ms
From 10.0.31.252: bytes=32 seq=4 ttl=126 time=281 ms