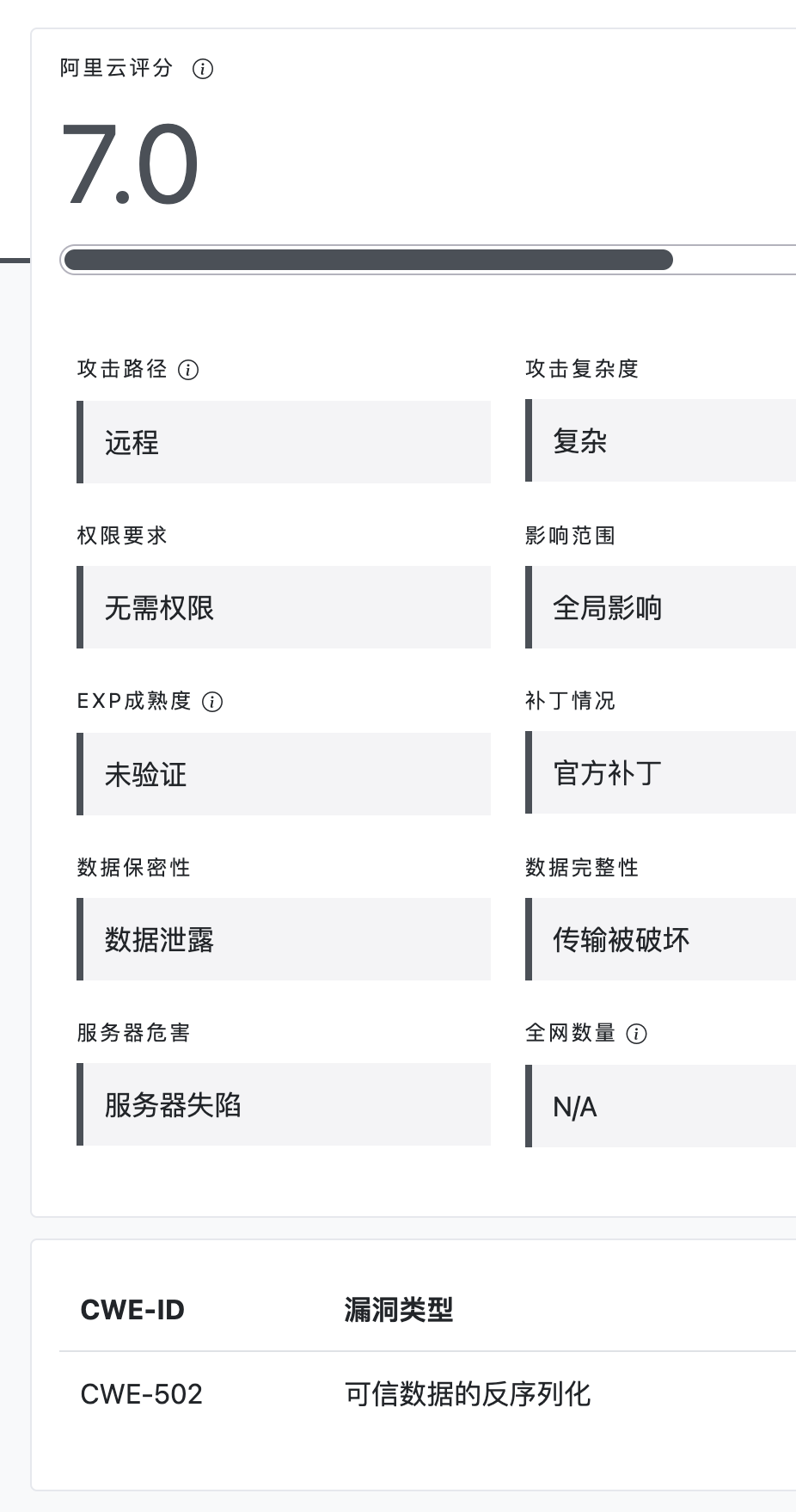
CVE编号
利用情况
补丁情况
披露时间
漏洞描述
解决建议
2、版本低于2.4.17的用户应升级到2.4.17
3、使用3.0.0至3.0.9版本的用户应升级至3.0.10
受影响软件情况
| # | 类型 | 厂商 | 产品 | 版本 | 影响面 | ||||
| 1 | |||||||||
|---|---|---|---|---|---|---|---|---|---|
| 运行在以下环境 | |||||||||
| 应用 | vmware | spring_advanced_message_queuing_protocol | * | From (including) 1.0.0 |
Up to (excluding) 2.4.16 |
||||
| 运行在以下环境 | |||||||||
| 应用 | vmware | spring_advanced_message_queuing_protocol | * | From (including) 3.0.0 |
Up to (excluding) 3.0.9 |
||||
https://avd.aliyun.com/detail/CVE-2023-34050?spm=0.2020520154.sas.102.6852YQ8IYQ8IkD&lang=zh
CVE-2023-34050 Spring AMQP Deserialization Vulnerability
Description
In 2016, allowed list patterns for deserializable class names were added to Spring AMQP, allowing users to lock down deserialization of data in messages from untrusted sources; however by default, when no allowed list was provided, all classes could be deserialized.
Specifically, and application is vulnerable if
- the SimpleMessageConverter or SerializerMessageConverter is used
- the user does not configure allowed list patterns
- untrusted message originators gain permissions to write messages to the RabbitMQ broker to send malicious content
Affected Spring Products and Versions
- Spring AMQP
- 1.0.0 to 2.4.16
- 3.0.0 to 3.0.9
Mitigation
- Do not allow untrusted sources to access the RabbitMQ server
- Users with versions less that 2.4.17 should upgrade to 2.4.17
- Users using versions 3.0.0 to 3.0.9 should upgrade to 3.0.10
Spring Boot dependency management will pull in the corrected versions, starting with Boot versions 2.7.17, 3.0.12, 3.1.5, and 3.2.0.
Allowed class name patterns are now required.
However, users who wish to revert to the previous behavior of trusting all, can set a global environment property or system property; refer to the Java Deserialization documentation section
Credit
This vulnerability was responsibly reported by L0ne1y.
https://spring.io/security/cve-2023-34050/
- Deserialization Vulnerability Spring 34050 2023deserialization vulnerability spring 34050 34050 deserialization deserialization webassembly polymorphic blazor binaryformatter deserialization serialization vulnerabilities deserialization insufficient python deserialization objects json vulnerability java deserialization openweathermap objects apache_parsing_vulnerability