1.UPX
010修改特征码后 脱壳
2.分析
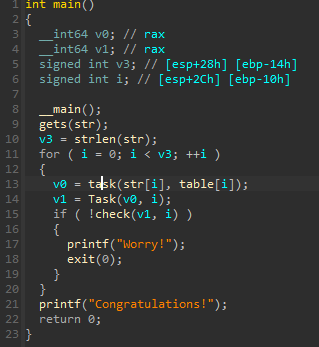
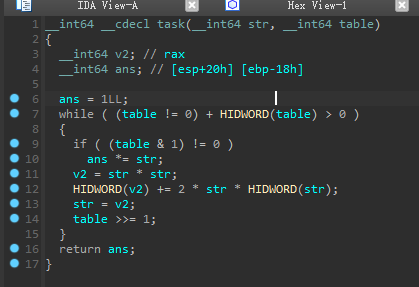
ida python导出数据和后 写脚本爆破即可
注意 task()中的HIDWORD在我们写脚本是没意义的,它只是手动修改防止溢出而已
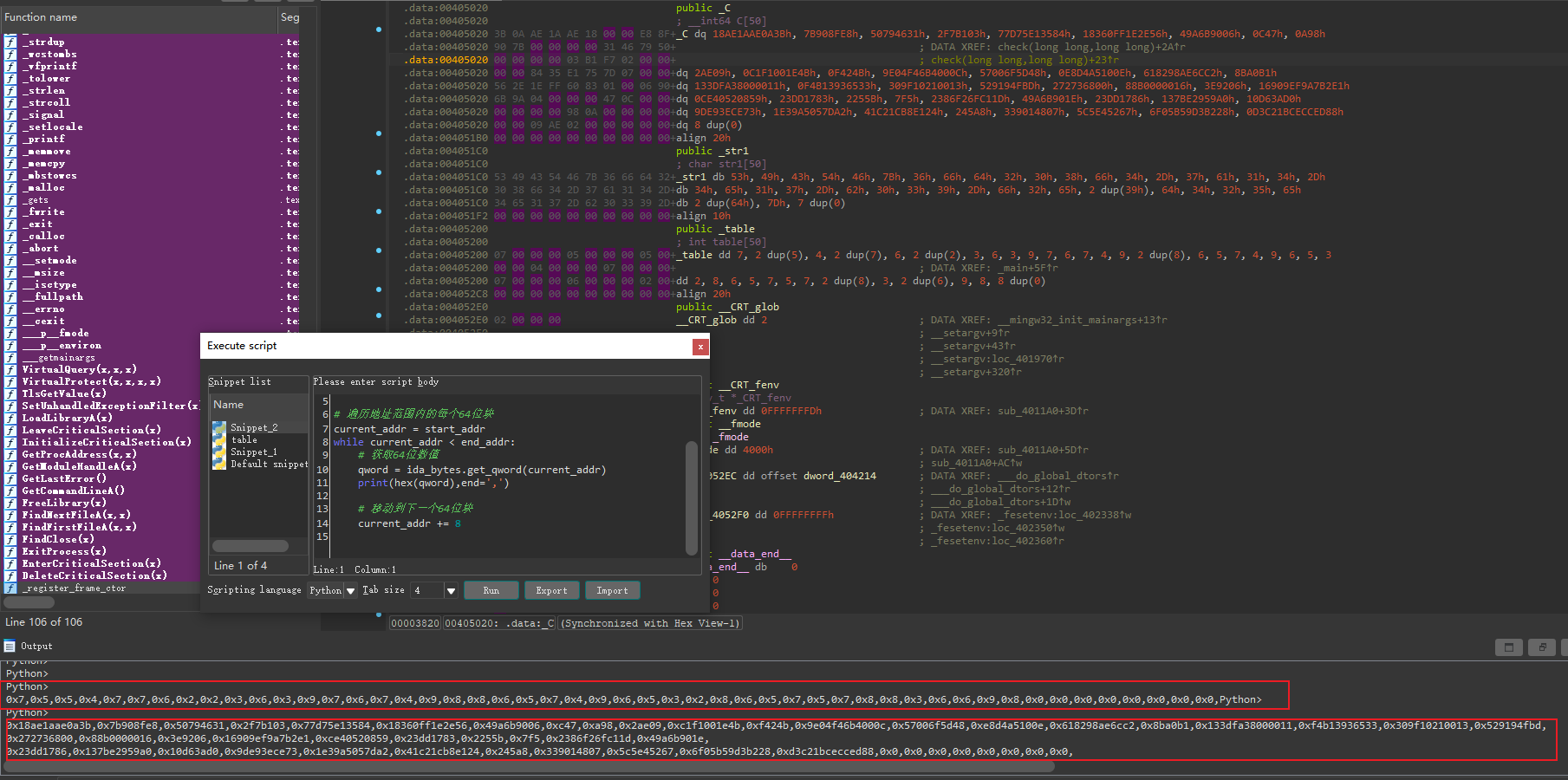
导出C数据脚本
import ida_bytes start_addr = 0x405020 end_addr = 0x4051B0 # 遍历地址范围内的每个64位块 current_addr = start_addr while current_addr < end_addr: # 获取64位数值 qword = ida_bytes.get_qword(current_addr) print(hex(qword),end=',') # 移动到下一个64位块 current_addr += 8table
import ida_bytes start_addr = 0x405200 end_addr = 0x4052c8 # 遍历地址范围内的每个64位块 current_addr = start_addr while current_addr < end_addr: # 获取64位数值 qword = ida_bytes.get_byte(current_addr) print(hex(qword),end=',') # 移动到下一个64位块 current_addr += 4
3.exp
def task(a, b): ans = 1 while b: if b & 1: ans *= a a *= a b >>= 1 return ans def main(): C = [0x18ae1aae0a3b,0x7b908fe8,0x50794631,0x2f7b103,0x77d75e13584,0x18360ff1e2e56,0x49a6b9006,0xc47,0xa98,0x2ae09,0xc1f1001e4b,0xf424b,0x9e04f46b4000c,0x57006f5d48,0xe8d4a5100e,0x618298ae6cc2,0x8ba0b1,0x133dfa38000011,0xf4b13936533,0x309f10210013,0x529194fbd,0x272736800,0x88b0000016,0x3e9206,0x16909ef9a7b2e1,0xce40520859,0x23dd1783,0x2255b,0x7f5,0x2386f26fc11d,0x49a6b901e,0x23dd1786,0x137be2959a0,0x10d63ad0,0x9de93ece73,0x1e39a5057da2,0x41c21cb8e124,0x245a8,0x339014807,0x5c5e45267,0x6f05b59d3b228,0xd3c21bcecced88,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0,] table = [0x7,0x5,0x5,0x4,0x7,0x7,0x6,0x2,0x2,0x3,0x6,0x3,0x9,0x7,0x6,0x7,0x4,0x9,0x8,0x8,0x6,0x5,0x7,0x4,0x9,0x6,0x5,0x3,0x2,0x8,0x6,0x5,0x7,0x5,0x7,0x8,0x8,0x3,0x6,0x6,0x9,0x8,0x0,0x0,0x0,0x0,0x0,0x0,0x0,0x0 ] for i in range(50): for str in range(127): v0 = task(str, table[i]) v1 = v0 ^ i if v1 == C[i]: print(chr(str), end='') main()