justpaint
1、题目信息
FLAG被我弄丢了>_<不过,JBN应该记得,或许你能从他那得到一些线索。
附件是压缩包有密码。。
2、解题方法
暴力破解压缩包,测试长度为6,选择所有数字

得到密码后解压
train.py
import torch
import torch.nn as nn
import numpy as np
import matplotlib.pyplot as plt
from PIL import Image
import cv2
class JBN(nn.Module):
def __init__(self):
super(JBN, self).__init__()
self.main = nn.Sequential(
nn.Linear(100, 256),
nn.ReLU(),
nn.Linear(256, 512),
nn.ReLU(),
nn.Linear(512, 452 * 280),
nn.Tanh()
)
def forward(self, x):
img = self.main(x)
img = img.view(-1, 452, 280)
return img
def watch_flag(img):
flag = cv2.imread('./data/data/flag.png')
gray_image = cv2.cvtColor(flag, cv2.COLOR_BGR2GRAY)
flag_tensor = torch.from_numpy(np.array(gray_image))
flag_tensor = flag_tensor.unsqueeze(0).transpose(1, 2)
img_tensor = img
flag_tensor = flag_tensor.unsqueeze(0)
img_tensor = img_tensor.unsqueeze(0)
loss_fn = torch.nn.MSELoss()
loss = loss_fn(flag_tensor.float(), img_tensor)
return loss
jbn = JBN()
g_optimizer = torch.optim.Adam(jbn.parameters(), lr=0.001)
min_loss = float('inf')
for epoch in range(10):
random_noise = torch.randn(1, 100)
jbn_img = jbn(random_noise)
g_optimizer.zero_grad()
g_loss = watch_flag(jbn_img)
g_loss.backward()
g_optimizer.step()
with torch.no_grad():
if g_loss < min_loss:
min_loss = g_loss
torch.save(jbn.state_dict(), 'jbn.pth')还有一个jbn.pth
懒得看了,直接交给GPT看看能不能解
import torch
import torch.nn as nn
import numpy as np
import matplotlib.pyplot as plt
from PIL import Image
import cv2
class JBN(nn.Module):
def __init__(self):
super(JBN, self).__init__()
self.main = nn.Sequential(
nn.Linear(100, 256),
nn.ReLU(),
nn.Linear(256, 512),
nn.ReLU(),
nn.Linear(512, 452 * 280),
nn.Tanh()
)
def forward(self, x):
img = self.main(x)
img = img.view(-1, 452, 280)
return img
jbn = JBN()
jbn.load_state_dict(torch.load('jbn.pth'))
random_noise = torch.randn(1, 100)
jbn_img = jbn(random_noise)
jbn_img = jbn_img.squeeze().detach().numpy()
jbn_img = (jbn_img + 1) / 2 # 将图像像素值范围从[-1, 1]转换为[0, 1]
jbn_img = (jbn_img * 255).astype(np.uint8) # 将图像像素值转换为[0, 255]的整数
jbn_img = cv2.resize(jbn_img, (280, 452)) # 调整图像大小为452x280
flag_image = Image.fromarray(jbn_img)
flag_image.save('flag.png')得到flag图片,需要翻转一下,放到PS里垂直翻转画布即可

NoPasswd
1、题目信息
小C收到了一个加密的word文档,但是苦于没有密码,你能帮他解开吗?

2、解题方法
有个加密文档,所以要破解密码,010打开分析一下
拉到尾部范围内也是有很多字符串信息,其中有一段十六进制,但这些都解不出来没啥用,仔细往上看可以发现一些宏的现象。

所以我们可以用oletools提取出vba脚本。
oletools是一个python工具包,用于分析Microsoft OLE2文件,如Microsoft Office文档或Outlook消息,主要用于恶意软件分析、取证和调试。
其中的 olevba 用来从文件中提取和分析VBA宏代码,示例:
# 扫描单个文件
olevba file.doc
# 扫描单个文件 只显示VBA代码,不分析
olevba file.doc -c
# 扫描单个文件 显示解码之后的混淆字符串
olevba file.doc --decode
# 扫描单个文件 显示经过字符串反混淆之后的VBA宏代码
olevba file.doc --reveal了解之后我们提取一下
olevba attachment.doc得到
Sub XOREncryptFile()
Dim numbers(8) As Integer
numbers(0) = 19
numbers(1) = 71
numbers(2) = 122
numbers(3) = 99
numbers(4) = 65
numbers(5) = 111
numbers(6) = 43
numbers(7) = 67
Dim CurrentDirectory As String
CurrentDirectory = ".\"
If Dir(CurrentDirectory & "abc") = "" Then
Exit Sub
End If
Dim FileNumber As Integer
FileNumber = FreeFile
Open CurrentDirectory & "abc" For Binary Access Read Write As #FileNumber
Dim FileContent As String
FileContent = Input$(LOF(FileNumber), #FileNumber)
Close #FileNumber
Dim EncryptedContent As String
For i = 1 To Len(FileContent)
EncryptedContent = EncryptedContent & Chr(Asc(Mid(FileContent, i, 1)) Xor numbers((i - 1) Mod 8))
Next i
FileNumber = FreeFile
Open CurrentDirectory & "enc" For Binary Access Write As #FileNumber
Put #FileNumber, , EncryptedContent
Close #FileNumber
End Sub仔细分析发现是xor,而被xor的字符串感觉像是文档最下面的那一串十六进制,总觉得这串肯定有用

于是我们去解一下看看,注意这里我们通过vba脚本可以得到“13477a63416f2b43”这个就是异或的key

然后得到密码去打开文档得到信息
UEsDBBQACQAIAFZ/RVfYoRV90yAAAJUhAAAEAAAAZmxhZy5wbme1Wvc3HM4Wl0TiKwUJUUIiBRuiR7DKCtFWWdFZLVr0tnpPEZ1NdLFL9LJ6t1jRIgiy+tqou4LVgtVZz/edV/6Ad979Yc7cmTtn5jMz98znzkzUS4jKjat3rlJRUd0AqyrqUFFRA87zcn9dOU9HznLkqajuU4EV5fX8EOtIaRgBfSs80BWZr0pnan6h9SIu6lHhYNFLCI/n8g/a21BcXjwizfRt3btiWo0NJZbRDC7VBdyXvDPUQuvSQaSzzJ3pOJ7nJ1Dav6j+LfcZzq6ZUf1HTMVVIf+te/w/K2cfBP+V/6KmzaToDzn007C+g7VnQitSUc2xcAH+Wff15uWBQi3y1v6f1IweOTKoc21SQkm8sGHCDsrPfSYCcdgFWQoxUlG5vyWGAfZwGwS58qez77CRQc37goeP8mZktSN9hvpfzz5ldnGdnV307N+QkWkM2ljZfxTa2ufh8VGiQHPfvZYAXFEuE8w327IcUexWdLtbZ4yzsNv+XVmKnwEFlrMU8jNLkuH+pjf0J84EHfxl5EOuGyRcy/7ifKToO1za9dNy+9pa9dcvlmS3+QWVB4Gg/IbQCfKfQGXG1Ic0pMDaBEZbgszdQmxgU3YGe87qKg0azRlzxbbcRTwfPwH1dzNfxquPG0smH7K3hvCXDLYkR+YcfDLn4IVq25B399Q4O4qLm+qQJ8fQNhux1mBupPm40t6ekkXDaNZ0d8E0aIWwObv9+mgHNOLpbvXKzk2LPIXfuNkdFYDzOT38xZKnuNAkFLq839VgLWgfcqzI2RMqal/BsEsKulbHyAIY/LYg/we48m0cIys0tVqdvO86Epnj6vkBraStIRQ6M71nWCMM8aL8aaSggSMvIMb8BxNyex7PHps1dCafuf5kqei1kpG9QN4WmBpfoBXsLbBGmxSdihtlGKq3E1gmbc1uxZ9y0MRSBIxO/B5TDWRtLPsLyOWs6sTH2KH3ZKVN+HlO4VaDoXIZkytDau9logwWBcRTi9b4BjzvVn3Lqyq9roDR5W36aI0V1K6udoiTiTP8ZJvVlXwFbFi1uBPgfd9hfPKDa52syYx7L1+881HHl1n9zCweq9i0Ze0WnTL0TYWhUi8JxdbtWlxPObnQ5I/xSnh9nDHez4UX1fU1PvrL174QHyvUTiB598EtZVypOaLa70956BrB8Q16xmAQ2lyLUzGkNHt0y2I/O8c6mpUT5K/leUcZeCSUDotNm4Jb7lVwt08FXYNbzKV6e0jueHIIHzW82iJ43CQFcBp/O7wXDFeEO1td2yN2yR9+wO46yHYRawbSgLr3Ly16v6Y2/T5jzpKKsL9mr3fcUbt+O9Ntgg6rJlL+M48tj0QSDGyV+ha6aTsSaVfA/lv02buQDAy0AQmnDW8d9AX1fIKEJXZfiqBUxaPkSQFOljRZiMpU6SRimPOaT6qADexdtxD1R2//xu1/DurlFgESxOfvj8bwJzBigrXwLX2Vsh3cgPikbyrxOTWlglfMLVRUsHzRBP2Wtq42lQRRtiQlgZiWTw2JFhRPPD67Xw3yfdWwfDlKXznYcFi91lMHM/19R1+wfDojvvWTSNqblEW1hO0y8OGPaXyieKe++cZdmNOsERegZRxVBu/bevnJuC9xYuDxW39XNHbBeRz2obT6XtPBmSijkJvb7VP7a5JqeG/yt8oZc2Z00btrSKFPFTN4zI1pkgLOFzxsNfKMQ/rcD43IcE/TG7oT3n39SMSybm8NGKIaFHGGzqgDTjTapHq//Rtu5eHfcEue8HoUVWw5ys5iCp2PjWb2eNYt0xGR8CQFWD6ezvkpx/iNGehw5vWM9/kiLnfN+Fw311W+6Y385QUwU3tf9lBulp/e2VPZLDjAhpqUePIYfHsjMVXLpEEsc1pARYUFeotdTT1VnFGnbtsl9kv0PXBc5AhYWaVaTRrYri10OLkmFq9jl+f0aFBTwmZ3xT6R2f8UUjxucRVPUaPZ6LvQ55G7c9Rvu4hGjdoiqo3mhtve1DswoMu1zYdg7BjjbM1VxpT55QqeuK3+RDGsmyfGo/fJ6i0P4pLkqx23Cws9U0Glx7AkxB9S4Pbrh73Ps9YSGaH0qtJ7zZKmCeaGNlhhcGuVc1jTr5jSWwzrIdOfF39xcWs8vi0s4njVGNbxC2G8mvJQvD2W33M1wGlYKttOltdnwmfbuQ4z6DmmLq6cRNb5/Yp/FppV7ZrGvaVBXEcU/BaXA8NGk2easf7gj9bohDxDeqDt1tfCUATB0Q898yhNBKhdkQtlCBHsjQrH1GjQ7eIR3qaifWhF024fyvyO29qW9dDVk6KqW+3iwPbFwB9rhyItvVGn76f2bJuN5bGsXot4dbtEC+PXA7t99OmTzNx0eyI1uhqQ0WNI7qwNZyCbqrL565dIaodWk9QTKeHTgHSpKnH/6CMPH7QlqH7g6MePkKmyd47BRY+QDe6DcaJknALEmMOdlMX2GnalYPVUB5fAWJ2m2RbE4bIQwdBLeyq+xJHa2XABoDk3CaEXPGO+H+I8rVB9OgkjtOG5AH7BcJcFSQ2Y1Y6YVqGDWNwUWvv6HrkYNHuGL0hZNJQX2ODlAZBs6yefyHC5AdI58Cxatw64B26Dze+mubaW9jSChUNC0PNBq4kSsh5O7xGkIDOWZ1oXhz97efRZzXGRh2IG1pmWjSb0X6lBWAHfwwubCyoBgOtTCE/TzLAbksZXGPArXxdnFbrgCcQXiyNUgwmM4mmHmUes47vws9xXsfbbmByx8rNged+RHydVOIA+PCp+JVuGycdLC66tOVz4FrEQIYPgnxaAUaCoxPtqjw1BMXeMPrW6DLHO3NTeDnzuIocpKDozhDLtFKohc4n0A+Uc11Ze1Jh3T6isn+ysTxq+Vtx/9qjq5CAnZzWlZiTuHQbkaGfRIySmC6oMUKD3zsCcqDQZsOmxjdS96PYt2Tls+yxIEs5BZRBCLYbbyq8QkxaRjFg5evEGlS+6Zpy3cHhPpdBcokS68U92tM54Yr9y2wCwZzFq8g2jLUMVkk6DIqB60vgo+jHEE1qGWQkWzbFMrxLGLMmFfNLn2eTtjmkmEQO31DxvzqHYc+9eHrBAjRy8x04/HtzZVj2NXXRPwOI9g+2jaX9m4b4yHQT1gpyKHwio+L9j8gwoWTbVELL9IAAL5yCeORK40Myv9eHYqcS7snbso7Xe+4crypCB16NO3WA2NsF4vK18Fk5a80pSjcMcdKkh0XDnCyktUqr5ja4BjZL2y0zDR21bfhq5nwbfNL48tS7AGuZk8UBPiSX3PUvCnfEehYq6hu8eTNUwrBtjQ7AFBOxPnjs2k78RBNgr8S/YhhyLYI37QKLwNx/XkwtVhw0MW9aHwydDVz2BbO2JjLYpO7JxDh6+zqop5JMUrIav7fMtpbEwJ0X4foQr57ScDteV3/MA9aMDPvuCpxmsZtqap33crElR1UeRwTYonvF0iP1T+hsqgj+azKXG5OJ+VB9SWyPnAksw+lEjvkLo6RiXVtdyclxI501KfpaCES/u/aC2xJ0nQyXierRg4a2GupsRb2iQFcdRmPv5CspjCMMhdkuIcU/k3NPjgNyJJSW3OdZu2taTzF3U1+LlLN2MfsVPWDK4i7F/b0ZnA6DSaPKsXevB1E5ZoayEIhNAiBwojoP3OgeoV/Sou68OGYFGRtZVdrQlhMguTVbjRX+vP4Pzcwf8TGZYqIXPZP3rNsdObrtHP9yclzo5k8K23TCEnmeXNMzpwt7gpeLTTgryMM55iD9OoIIqfkBAXrQm+8Byfv0vdX/cwD3crdTLrYO7mTnhNv4ZUdlXfou9ezmdb07hDXFkjyMFVOyUTiXIzbc+Ht14kLorWmidfsxGUibs86jnN7R3iahzBl6+07ssmvnTkEFOysICaopp0m2pu4fooZe9wFXID9WCLVnBdp1kCqQ/PK+1afIraN4S0KxxlfPnO+pxzSj1ajXSCg+N2wwADJecEqlR+oyjv6yc/hSMRIr2eh7HfLu63mQJjlkyPOIrCTURhAvizPptd6oFm40zPOP7f4p/SdNaqa91QdK+32VUapvBHvio8czLpSLey2hVIVVCK9/i2oDcZHEwjWR0jRebMkyh2lBF/cKEWIPc+c6IKx3Nw7C5HGq4QWHKYig7yXE420jZDvUHG5zVR9qpxWHT+iGXXwH2/CNPfJlZBRmdZJ7M7TOajq5uwl8vVK2LbBcicl0bjaa+16tgu/FOcCm5Q6QeRr2yMUPHjd/gnDag/hrr6+RFHQTkL33oFQNT43ytSUd5o+DlLPUMVHRVOYtY27TGm9GVTQALYqEk6uETQJKtzkMv8A9hF89BD7bhK0nglqoF6sAhmPyQVU4ZI8WzF0fADh2SaaQlT/H3hrYIvQz2yXPPExibW6X0a6X0vXkniW9JxZfX6a37DAJ+8shvrRpY/iwaLkqUmb8YpP2ScNk4WC9FHfdb9/PMzPA69hly0GHjeF3XIahn7FWnDPuM6TaL8/FHVEB6ELX6IUGdJYedR52dnTP7oV085fnOscJRlMmQlNxnbFZ0rlHpLHPdbvCnAQlGzsRt974S3ZAfT8CPBfbVOS0cFKq6tMovqY/Z0WueIaZMbbPD0RiwhhjIWH/mXndS3op2aH5S5GAJhCpTtbrq6416FI8aqT6g7El3QMXxfLUQKdNZjSB9GFZtWmDuNiT2afVsjw5Lo5K6xqI92uLct5kz4Oser85jjCOnckUBpmQg3D5lM4zqAfdQuGeCQJo0a2lOyv2w0J07cplXBRf4X3jF7/0J+JW71mIYV6NypyfBh0NiRKZj9Ms92SXqay+sg5mGKoecMGG5iibx+dNJftzvmsYpcqYZuW9NH17kbHKOIWQlxYuiOLOWDhp5VwOAkjNa4r+JAcHx6PkNIz2AeD0qj875Uepg4TAl0vDhG5N8BzTom0B5w/F4xHLHA6dZ14WmU9ITOVFTQdfGo6XO33z94qPeuOBTFewi7C5sjgAv3odjPbn3MP3jyh45XyoEarsC1TxmoL4Lgz5LkmqjLecOb3uf/f5Ifiboe7fslCezILBnP3DPk3Iiz1hBiXsWohfy6meuossCPz5XMSIR8RGpWWrKPhBVjXraF3iLiT3CPjPPnm7hAZIw8BHx3fMmk6PplO0GdnbcE65bfGGtxWv3i5eqtl6rFPmHYwKelV4g4PdD4HyNefVWke63eiq9cVa7YvaNiy8qMB33v66GhqsgLeqo0zK/1bgZ+7NROU7nkvCXVjkLB/S7jSa4XSB8iRFII/9WJBeA4/KvbWJMR75YVImqIykfVW+Pilklhun/7b0M4s9FDZjwbby5KLMmIkcMeXPp5PA9sz/mhN3uxP5E4xvwiy3Ce6aXlvAWbygYdUHM54qjG1gzgQkzC5qalwZmh+72VyQ3VQzlh2dzv8RdqUHajrIh+dw+KH5MzuMDs8WJr4g+jE9gBK1y3yhJnmqVLf6SgpCkmXaXKAg+jDaF+ppFDJTurMIAJDDKZTa9g1f9dl1y3Ntd+MBvvvF2hYl1Q+bDjI8SXu04ou6mTnlMKSeHkOUuElHpdO6cvW6XYgGUjGZ2Ql5ZiymM7s8xUN/LAD2xtTI7uaCif5EbgOgyrrNbru98k8BYQHupRgOFzP4oo8WbUbhff7mXtqddOfirg1A746kvItIx8NJIPXVjP5DctyHx9aisAujTeE5bdh1NBka36ku9fJAmtTYB3ilokTWiYkZcZaaX/5j/IZdW2WY4v3pi+GAfeZ46gXFcfKL2RAq9sbwYkyd7TmzvMBbc65OoX+1y47iGf9IkZYgpGlcRL/jVYxmSyFjvEjLYSxvo7xjcw2135kSZhNBwh76MaG/z6IaXUKtCGqNqDAaqnUCvnvfSdiYzlvWjdjdrfFsO+TSZEpg+Tc2ocAHI5a6Hmp3jKMDd9hI1s0WcSjcoiV/kHMD0MZR9ceTuUGa990GF4Vijilm7E6KoNVtSfZrVEZYj8DiKY412t3hHwE1XMbQbjFYbWfepXTfHqR6ZjPkQkmy/RnEBgvA8HxLwq2gHjdGvZfBZpoGzhtufFSRmsR97bGXbMamS2jzfLJon5Y5jExkFeUL56uPUB81N35zDWCdSZ4VaR3HqW2pCGmNqxEd7qs1xEUiEMPRCNpQni80jmUspVMUsCJaDOWtYisYTU91QmjNcdZrPXUCjanQgx89uuyjumNL6q5oeQlYTsoP73VJFExvaPL3ldTs6GlbIfNfrQkAsxaBDyX1Jd8mWkh+6iPC6bF6hATF2XLvYLQYef2taQ0+Thlgu//gUP8rX8am82eQ2SQo4D8JlK82ItmP9c9ccYHNCwPmcgSEJ4Hze9G2eKVMYse0aJz798P3p9BplIPCk6KourMMB4X1iGiWkMy0rjCCGaYdPbXfyzWh1LqvrePmedIcyjCjx2gZ+15OLXLSaTV7kFWuFp7oCtsnikSLNrnpC+Xa1wBQzM6bUr5n5rn4nOuh25g/jupdq5ewbrCb8UbQ5r42BtuB7lbhLHD2OT25IrR9/JFfcZakv3lMsRG8Mpn5e89z8as/b4GTDedVlUzpTt0uGB4CoBS41EusuVB+8XPow+Zs0ARAEzltLp1JeGeYLUwacToqi94lhBEl1nvbl0aIH3AANyM+PG1EaEyp9j82qu97Ca6Sk99J92S5wcJO+JO0SarxAGiTiCyNBOcwUj8LSk05mWtmN/NB6C60ZGRuCzRTIYPTgVcKCTm3NaFy2Bh1+PyVlz6wtuNF7ppNiFSc0cJzoHaSLNh8vYWoEV4xoQpyjSR3iZZxEowmz8WkXWMdYhLALNgrVsqptks7R6zHyOzUZUdk2msC4sUgdu95ycMkfaXSCn3eV28oNmJflAfw6zjS48+Qp5DHQslrt69Cb/dSB1M2nm6zO5iDVxegRDYjz9Qor5Z/YEN34BiFHnG1/r7AvzGoRFrW98Va2Z1D8qCW/YhAiId74+TmrXCHhvd7r03vPl5AtZWJm7QTtceYy7opViZAqLvfk1KeNFIdXLhmI1aNw+fOJDabpvEyq6gcDABz153N8na+/9/ZD4E3B+p0VeoWDho0+qWjO5EV/NYjftixM+/UTACVX/iN2KWevcPnThsrdhnPGXjZLCDtnc6EjNuPcv2KxROQ2USguKzW5TUgOU5Q2UPTAI0hT+3BWP+RansaMYdLZ4PL6Sjxzc7ip4PLGyudtt1OflqY7r/vhG5y8twK8fyZzBwfdFpMeJjhLFXwmJV9V0mrgdFRIqctIHUoIdFveGpJuugPi2x0OnCtqHtoJTd5Sxj6Lu80Z3IfG9s1y8tnnACFXjw5NTtW9yn5GdxTMxmcVl+doI4azfKdFnf/K3jGeTu+mz7nsnf7zfWQRswocGvSaDCoGRekagEXaXA4qbtzs3nokK2OK9ZNxja9xVouRxgXLnoemPAaEvvfl9OkLq7kGE2n3yLfHblqjyy8b9Ic2HczuOHpXuAwCBdNdnjMpQRM+/6rsp72NP9yj+UUpY4FvPWKPxRQWcyoIDcuRA4dH4t/JcwGiD58882TcR35wu2Pue6BBFfs69PFhEdstS0VMtLGnggS6sGe5yVFiKuQalC2Oh0xBjuyuazdfIxynDIS9JaG3HF0o8IyzTa0HztNU7BY6Bs9SbrTleTcQf6vs9DwTKU9l87abdIwY1JP4NlCEJHfuIShjYbs8rnl0noTvM8iGYi2kr4SIK1npEsSYm6312UVsZMIJPl3uakEoT9oUj4FZQzYu/jUTeVc78COW61IRof5vQvCSnYGb3DOXnyzODwvq8cGcXmgIrVEBhly/jNp0IKkgQnyHmuIPsgjDrPd1/6SZS9WZWPnlpg2LPUMnBFz0RFK5v3zG+wgdqjeQ1hfSnLfU8MM7W/DNzQHzhT6LvjUHCbwE/5xCUcVc9HKV9+G4P+nbcgllfEnodHmqYyGiRERJcVpESVk3qpP/PcJSc/xiTch7VojBDvc7fJcimPWUwPWm3A3g2/4YUwTUAsWNdjW6El805PPF488DdVjfAmk2cSyXTvLkrUTLgQ7yQIT6B6YQdIWgBxTRvuW3qCi/g2/+XRJF9PUNNzwftYoH3PKS1uOCpWaCjvMtqqfIlForsAvqaoa6yuUY6c+g0lqpO3/x0OcUstAEr5oJNoLpZDltP2oajBF3mUIq881vGpdxmQpmqLffodczGZZUrR4qESD9gvq4oqvyQcrX67FiBnW7ztj+Am9OBt3PbdLQsI6ynUfoklaIhJnozM+4DNSUrqRt70wX5jFNjtLpbSP2C2Q4Yxsak32Y4v60aSRFuyEi/LqTugp4pywAz47TDn4TxXz4QzH0hswebOY8hk3QNqgJvdGjRk9ZdD8G0oV+XZnl+HJbbrtzPpBvtL7RviKg6rjyw0APaDsFfnsvNLL79GZGNSFfJoRVd+cFdBu+EiYZjtIpSTy4/zoZmh4Hci1EOW1gQNMC4fPvrS+AInv3Hzy7FAzSnXYPHla2kxZFElxi3w42HzYiodLbvdXHklYjEXV4X4PTGvkJcY8VdC69gzpcbjSELjFuRH7JRnKoR5azq/HkfkHW37c7ztUcwZPoNlUNmAZ2z1OG8mYkdWreB1Tbkzz0F4Pd2DFkgvoDGJKk4qQGF9Z2EAY/bG/nAp/6FccL1ZWAE0ZbC+9KY0pJCxzQp4P3gdlcnQt+BbvrV1SId74wnpj85QHaOFISHe03GkwnhWs2iTGKvwCaV94GFHqzklGkp5M2xtR+Omdj2e9jj+zebzQujHjTCJlArehcOOWKdKXGLw/Httm0+VboQhIZMX9f+1T3ikb2xM0lWP9lB1Po4XQ/0rnW0l0cn3D1wUIpozqEiBKLWmR0GVPez7cvYdve3Xz4YOSPuyDOI4fvtj0w3GvalZktWkaz65TH11wN1vH7uyRSEQoUvz7ELD7GawJUuzD6ZzXfcyP4rHXpC3sB7atpCR86+MH2h0+DeAid98ZSgm2AnhnemGRmSxyWG/ToRq0Oj6X0XcQf/fjaE6jOnN7KpUYoKJuweLAEAnl8RvwZ/21KSDBMIRe9yG03vveUzTz+Jl0CY8jJhUKhZ508IXp+je+JimmSTnO9UQPplQ4JpQvMdoUTc6AaeDTbdnS1IsoI2MiLlw+5V+lY2MuxOtPuWJbzfQKc8Lhae7QfDPl+wzRrsC/OPdDELZRzhRujMcQg3iEMbDcREhnUiRPhZdeFXlqQ8X4R4GYX2l+/svv9zi8TfdoC1Acbxju32ZGFOhY4B5N0m16elumjyWpv3fa96mXOpcaF8d36ZHqPLBdnLY20A7/mxUOzbpkWLp263SixEJ2YC8SA0mW7CULpcYNgIuPMlKkBRIiQYJJiunTc0zdP8ZaZli5oIrK+mlua/BuoLZzzWFFSFUIdXXPx/LQztWJ43HM5c/+slzTxklgvwKzgkCNpzq1QNUJ4EjURX1xH+by4qfZyrZ//iiuCKxnGleNc1Who4MMF0HNNrjCNWtAJpd+d4SJADWh2W7pRUuX2O2teiXPSFLPMwrtPPsrcuZdBpDZppdtWA4JjEHm2/KyXYecBjUBi0rrixn1xiwrMMP1Fg7v1oxswdNao1RNdk/v1IzHB7L9pkGK7N/mrobsyZa29KJ62iQCWic310Kp5szPJHn0qM7e4iZx19WS0Swm+azgEuj62d9AaBQ1UcwnOKne6fFTNRTbwYZKwST1rwfarglOaiWGbbkHusf1U1VILR0dGuP6krpu/fb5WcZhxuFiQF+kPghzeHFTVSIb8/dYwpLzWywMgNyj7mYFqlC150zvjDYbSDHql33ElXuulHRF1NE1xKx09Hu5JiBKAnLdYtX0w1FGFKHStpSEGG9rU6Q9s3Dnf0eA23n7CpzHKb5RJW0awy4EmS+pRD7D84gpaO3Tdu33vBSwTdMvQ6m6E0pGHlms5PKiXFu4y86BzvfH6I3X0IhTPfF0lnjk8JH6I0/1wWHjLOtCDgwtw8fAenth1Fpnx+BY6XRczLGuiD/OK23lUzENmmKDUBhU0rB3QG9LRqf+qbd8PnBBJWY99vUlGFiZ1idvR3O0TRTydixiw39PsqProiroGADdZWjj99cDyyQnCkONWQUDZ8bLJJutP60FdCR6y4FpsefpNiJML/mvk61lgfrgPVAvgb6M546kmprhGxse+XZ2lnfxV3Vbr/VCt1Hk+8wi4r5c5J/GmPrrvERmzC7fipA02XVmRk+b/mxgc2sTxbCqDTu7r/VBhsnIQBHL8ObwEsZBqWbLgkkq/ftrwHsvHl/pqPaVnmRtSEna0bBGD2BUV/SDAnPxkGPeoWHXiVm556YQPbw4wtQFmpbWkg3VkXxX3wG93+SCr11Vu8M889BxHndTHkPwm+a+J3RoxwD4djSunZzMZXVkzhHBkF7FAvIab+W8HF5XFikGB2Y+GnDXKsgZFyi+uoqF3V1HGAoYQP1mgkibgZPKFLFKbzXrQACKcaUAINL2SnH9TN6Nn2BTGVGn64DuJXua44cuWNfKaOXALdcJ5MYVJjwm4eEh/GkTJDT1usxjp7LyN9dMgYL+HGpQxLH5XAi5HgOTO7p5GuABVk6z5+zyqVlpjC9o27KvO9tOGx6RxLdZPqmO3ObEzZ/XrwafP6Q1zkIC9UzOmBRwQOzQEOMX7LtUxeCgZKhTyAKY+Oe9OxUUQKMA7iRj8Jr/3i+8D24+OFyohqR2YTZBcA6YjC3KUUhdCmZDvqeC8F0bR/I63ujh05Fsuvv9c3jjFkJxdim9drhkp+1x5TgcH3SaXc4cO1HkyhnquX4G0feVTj0098WtJ2lY8MzeL2rgbI0IQNLD8RGBzDZ0ba7scz6mFtApRJyx1ukZImjmUGbyAXTRluDzg1uPFKrTXS0v1L1HEkVmm785QOwEAB23AC8+Flb30D1mAibpUVBde/v0X4NX3d6Ca+tmL/7J/mfslq6/HjdzmEkmkbnz8bWKMnsRvvmTFeuFfBsI8gdLQbMHIeyvmnizXExjnclgHzItg9/u30781NIgh7ZJsVXX/Zfvm1qKvbjVwoLCBvOonR5PcFBW4vtk+l8E4t/29IK695tvYTcd/mbpvSGYaWi5SN8o4D6Vf+Vfhz/vRAxYHlKUWMSoEVW6vdHBFiO6nYCx+ieZUQG4GNhLI/u+OZG8qfUpTkwUNd57+IP1l7LxK9W95/rKy7NJ/NHl52MX/l3Iop8mOozaHNz/7WwUrQRTLFV69+wdQSwECPwAUAAkACABWf0VX2KEVfdMgAACVIQAACAAkAAAAAAAAACAAAAAAAAAAZmxhZy5wbmcKACAAAAAAAAEAGAB4FtrCYffZARc9ZA1i99kBhPTMwmH32QFQSwUGAAAAAAEAAQBaAAAA+SAAAAAA百度一下可以知道这是一串zip的base64形式,我们转成zip保存,但发现有密码。。。010看一波

我们发现第A列下第二行处04这个地方文件名长度有问题,我们给它改回去改成08

但还是需要密码,我们用伪加密解看看

成功解决,解压后是一张图片内容就是flag
![]()
SecretZip
1、题目信息
Do you know the classic encryption method for zip?

2、解题方法
明文攻击,尝试后发现所给的key文件就是经过压缩的secret key.zip的前半段,于是直接拿来用
.\bkcrack -C purezip.zip -c "secret key.zip" -p key -o 0 >1.log得到密钥e63af7cc 55ef839d dc10b922,直接解压
.\bkcrack -C purezip.zip -c "secret key.zip" -k e63af7cc 55ef839d dc10b922 -d 1.zip注意此时的zip是压缩之后的,需要解压一下,然后cyberchef里面使用raw inflate解一下
压缩包注释提示password is two bytes
直接zip2john和hashcat进行爆破,得到密码为$HEX[9c07]
随便写个脚本解压,然后里面给了一串密钥,结合zpaq文件尾的提示,一眼丁真直接爆
.\bkcrack -k e48d3828 5b7223cc 71851fb0 -r 3 ?b得到密码
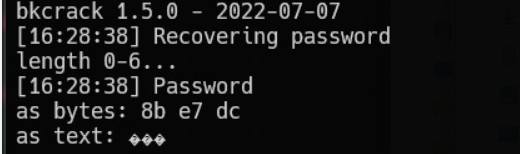
MD5再用bandizip解开zpaq压缩包即可。
justlisten
1、题目信息
听听这是什么

2、解题方法
我们先扫一下hint.png
明显是汉信码,但在线工具扫不出来,然后发现还有一个可以扫“中国编码APP”下载一下APP扫就行了

得到密码“0urS3cret”我们利用ourSecret来解bmp文件,导入文件,输入密码得到txt文件。
这里为什么用这个工具,因为密码的提示以及文件的名字就可以想到。

打开txt得到
abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890_}{-?!像是某种表。。先不管它了看看WAV吧
音频的话试了好多发现使用Sonic Visualiser可以,下载官网:https://www.sonicvisualiser.org/
打开一看就是十进制,右上方是设置。

我们需要提取十进制数据,左上角导出图片然后写脚本读像素
from PIL import Image
img = Image.open('1.png')
flag = []
for x in range(58,6561,17):
for y in range(868):
col = img.getpixel((x,y))[0]
if(col >= 210):
flag.append(y)
break
flgg = []
for i in flag:
if(i < 250):
print(0,end='')
elif(i < 280):
print(1,end='')
elif(i < 320):
print(2,end='')
elif(i < 350):
print(3,end='')
elif(i < 390):
print(4,end='')
elif(i < 430):
print(5,end='')
elif(i < 470):
print(6,end='')
elif(i < 520):
print(7,end='')
elif(i < 580):
print(8,end='')
else:
print(9,end='')然后得到十进制数据
0900030907000309100003100007100307100022277031005192203203432284426284735274836292742424842463147282734424837362942334460720080624061811100213180401000920140308111000181321001411220513021020010006211814083733362813100301092108201804080511070022131021010910032111041881000051310002215140514150005142926442845316448075218191108130662196162281413321042462081305141712001952141367676763根据我们第一步解出来的txt文件中的表猜测可能是每两位int一下后再去表里找相应的字符,如果超出范围就舍去。
table = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890_}{-?!"
a = "0900030907000309100003100007100307100022277031005192203203432284426284735274836292742424842463147282734424837362942334460720080624061811100213180401000920140308111000181321001411220513021020010006211814083733362813100301092108201804080511070022131021010910032111041881000051310002215140514150005142926442845316448075218191108130662196162281413321042462081305141712001952141367676763"
for i in range(len(a)//2):
try:
ii = a[2*i:2*i+2]
print(table[int(ii)],end='')
except:
continue但只得到了右半边的flag
![]()
脑洞一下,删掉第一个0再转一下,得到了另一半flag,为什么这么干呢?我们可以分析下第一次得到的结果“{Q2qSvkE?vqwPHvey_informat1on!!!}”,明显我们可以发现前面的“Q2qSvkE?vqwPHvey”肯定不全是flag,一般我们得到的flag都是有一定意义的(大部分形式上都可以翻译出来)为什么得到的不全是flag呢?因为我们刚才也说了两位一组超出范围就舍去所以肯定有出入。因此我们可以通过控制十进制前面数字的增减来查看情况,经检验发现把开头0删去可以得到flag前缀“DASCTF{”,那么也就是说这样做是正确的。

经过上面两次结果我们可以拼接出flag大概形式
DASCTF{Wh1stling_t0_ConGkQUuEZPubvPK Q2qSvkE?vqwPHvey_informat1on!!!}我们再根据意义来分析一下最终可得正确flag
DASCTF{Wh1stling_t0_Convey_informat1on!!!}