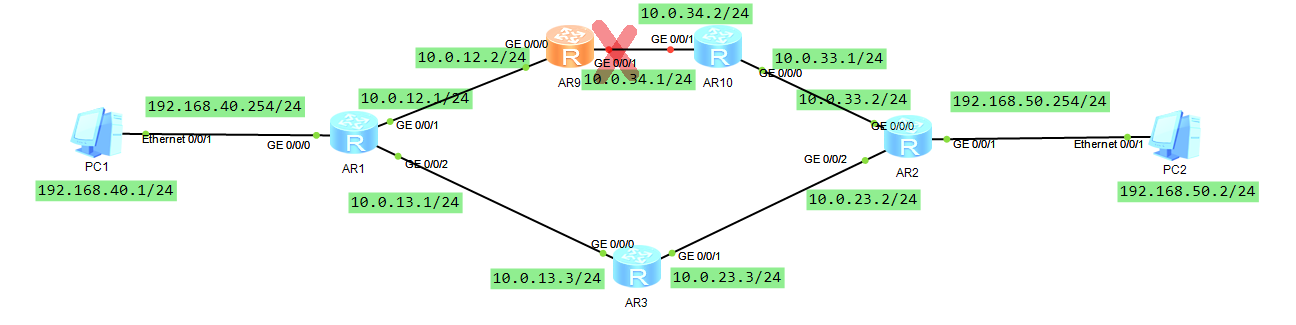
实现目的:
1.默认情况,PC1和PC2之间的通信使用AR1-AR9-AR10-AR2链路通信(主链路),当AR1-AR9-AR10-AR2链路中任何一点的链路断开后,路由会以毫秒级速度切换到AR1-AR3-AR2(备链路),实现网络的连通性。
2.当主链路恢复后,路由又切回到主线路。
实验前的配置基础:
1.配置PC和路由器端口IP;
2.添加静态路由,实现PC1到PC2网络可达。
3.然后创建BFD,绑定到路由上。
开启BFD [AR1]bfd [AR1-bfd]q 配置BFD的源地址,目的地址 [AR1]bfd abc bind peer-ip 10.0.33.2 source-ip 10.0.12.2 auto 绑定到主路由上,当BFD检测失败后,会把这个路由给删掉,然后ip route-static 192.168.50.0 255.255.255.0 10.0.13.3 preference 70这条浮动路由会生效。 [AR1]ip route-static 192.168.50.0 255.255.255.0 10.0.12.2 track bfd-session abc
AR2路由器上的配置同上。
实现技术:使用BFD(双向转发检测)技术,说的直白点,就是在末端路由器上开启BFD,两端都要开启,设置BFD,将BFD绑定到静态路由,每100毫秒(时间可以自定义)发送一个BFD检测包,当链路断开后,BFD检测状态从UP变为DOWN,路由快速收敛,备份路由(浮动路由)成为主路由。
路由器和PC配置如下:
AR1配置:
[AR1]display current-configuration [V200R003C00] # sysname AR1 # snmp-agent local-engineid 800007DB03000000000000 snmp-agent # clock timezone China-Standard-Time minus 08:00:00 # portal local-server load flash:/portalpage.zip # drop illegal-mac alarm # wlan ac-global carrier id other ac id 0 # set cpu-usage threshold 80 restore 75 # bfd # aaa authentication-scheme default authorization-scheme default accounting-scheme default domain default domain default_admin local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$ local-user admin service-type http # firewall zone Local priority 15 # interface GigabitEthernet0/0/0 ip address 192.168.40.254 255.255.255.0 # interface GigabitEthernet0/0/1 ip address 10.0.12.1 255.255.255.0 # interface GigabitEthernet0/0/2 ip address 10.0.13.1 255.255.255.0 # interface NULL0 # bfd aa bind peer-ip 10.0.12.2 source-ip 10.0.12.1 auto min-tx-interval 100 min-rx-interval 100 commit # bfd abc bind peer-ip 10.0.33.2 source-ip 10.0.12.1 auto min-tx-interval 100 min-rx-interval 100 commit # ip route-static 10.0.33.0 255.255.255.0 10.0.12.2 ip route-static 10.0.34.0 255.255.255.0 10.0.12.2 ip route-static 192.168.50.0 255.255.255.0 10.0.13.3 preference 70 ip route-static 192.168.50.0 255.255.255.0 10.0.12.2 track bfd-session abc # user-interface con 0 authentication-mode password user-interface vty 0 4 user-interface vty 16 20 # wlan ac # return
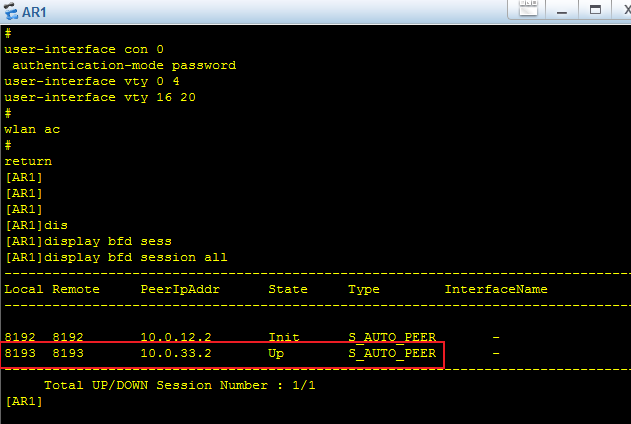
AR1上查看bfd的状态:
AR9配置:
[AR9]display current-configuration [V200R003C00] # sysname AR9 # snmp-agent local-engineid 800007DB03000000000000 snmp-agent # clock timezone China-Standard-Time minus 08:00:00 # portal local-server load portalpage.zip # drop illegal-mac alarm # set cpu-usage threshold 80 restore 75 # aaa authentication-scheme default authorization-scheme default accounting-scheme default domain default domain default_admin local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$ local-user admin service-type http # firewall zone Local priority 15 # interface GigabitEthernet0/0/0 ip address 10.0.12.2 255.255.255.0 # interface GigabitEthernet0/0/1 ip address 10.0.34.1 255.255.255.0 # interface GigabitEthernet0/0/2 # interface NULL0 # ip route-static 10.0.33.0 255.255.255.0 10.0.34.2 ip route-static 192.168.40.0 255.255.255.0 10.0.12.1 ip route-static 192.168.50.0 255.255.255.0 10.0.34.2 # user-interface con 0 authentication-mode password user-interface vty 0 4 user-interface vty 16 20 # wlan ac # return
AR10配置:
[AR10]display current-configuration [V200R003C00] # sysname AR10 # snmp-agent local-engineid 800007DB03000000000000 snmp-agent # clock timezone China-Standard-Time minus 08:00:00 # portal local-server load portalpage.zip # drop illegal-mac alarm # set cpu-usage threshold 80 restore 75 # aaa authentication-scheme default authorization-scheme default accounting-scheme default domain default domain default_admin local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$ local-user admin service-type http # firewall zone Local priority 15 # interface GigabitEthernet0/0/0 ip address 10.0.33.1 255.255.255.0 # interface GigabitEthernet0/0/1 ip address 10.0.34.2 255.255.255.0 # interface GigabitEthernet0/0/2 # interface NULL0 # ip route-static 10.0.12.0 255.255.255.0 10.0.34.1 ip route-static 192.168.40.0 255.255.255.0 10.0.34.1 ip route-static 192.168.50.0 255.255.255.0 10.0.33.2 # user-interface con 0 authentication-mode password user-interface vty 0 4 user-interface vty 16 20 # wlan ac # return
AR2配置:
[AR2]display current-configuration [V200R003C00] # sysname AR2 # snmp-agent local-engineid 800007DB03000000000000 snmp-agent # clock timezone China-Standard-Time minus 08:00:00 # portal local-server load flash:/portalpage.zip # drop illegal-mac alarm # wlan ac-global carrier id other ac id 0 # set cpu-usage threshold 80 restore 75 # bfd # aaa authentication-scheme default authorization-scheme default accounting-scheme default domain default domain default_admin local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$ local-user admin service-type http # firewall zone Local priority 15 # interface GigabitEthernet0/0/0 ip address 10.0.33.2 255.255.255.0 # interface GigabitEthernet0/0/1 ip address 192.168.50.254 255.255.255.0 # interface GigabitEthernet0/0/2 ip address 10.0.23.2 255.255.255.0 # interface NULL0 # bfd ar2-ar1 bind peer-ip 10.0.12.1 source-ip 10.0.12.2 discriminator local 1 discriminator remote 2 min-rx-interval 100 commit # bfd bb bind peer-ip 10.0.12.1 source-ip 10.0.12.2 auto min-tx-interval 100 min-rx-interval 100 commit # bfd def bind peer-ip 10.0.12.1 source-ip 10.0.33.2 auto min-tx-interval 100 min-rx-interval 100 commit # ip route-static 10.0.12.0 255.255.255.0 10.0.33.1 ip route-static 10.0.34.0 255.255.255.0 10.0.33.1 ip route-static 192.168.40.0 255.255.255.0 10.0.23.3 preference 70 ip route-static 192.168.40.0 255.255.255.0 10.0.33.1 track bfd-session def # user-interface con 0 authentication-mode password user-interface vty 0 4 user-interface vty 16 20 # wlan ac # return
在AR2上查看bfd状态:

AR3配置:
[AR3]display current-configuration [V200R003C00] # sysname AR3 # snmp-agent local-engineid 800007DB03000000000000 snmp-agent # clock timezone China-Standard-Time minus 08:00:00 # portal local-server load flash:/portalpage.zip # drop illegal-mac alarm # wlan ac-global carrier id other ac id 0 # set cpu-usage threshold 80 restore 75 # aaa authentication-scheme default authorization-scheme default accounting-scheme default domain default domain default_admin local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$ local-user admin service-type http # firewall zone Local priority 15 # interface GigabitEthernet0/0/0 ip address 10.0.13.3 255.255.255.0 # interface GigabitEthernet0/0/1 ip address 10.0.23.3 255.255.255.0 # interface GigabitEthernet0/0/2 # interface NULL0 # ip route-static 10.0.40.0 255.255.255.0 10.0.13.1 ip route-static 10.0.50.0 255.255.255.0 10.0.23.2 ip route-static 192.168.40.0 255.255.255.0 10.0.13.1 ip route-static 192.168.50.0 255.255.255.0 10.0.23.2 # user-interface con 0 authentication-mode password user-interface vty 0 4 user-interface vty 16 20 # wlan ac # return
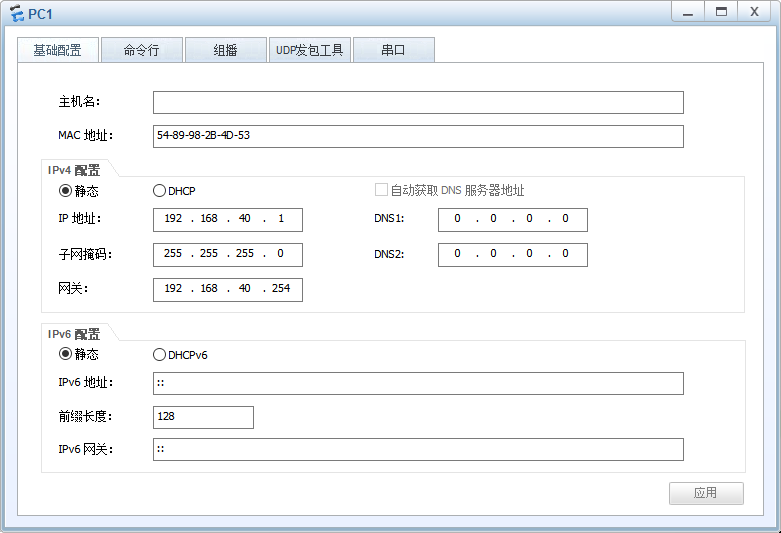
PC1配置:
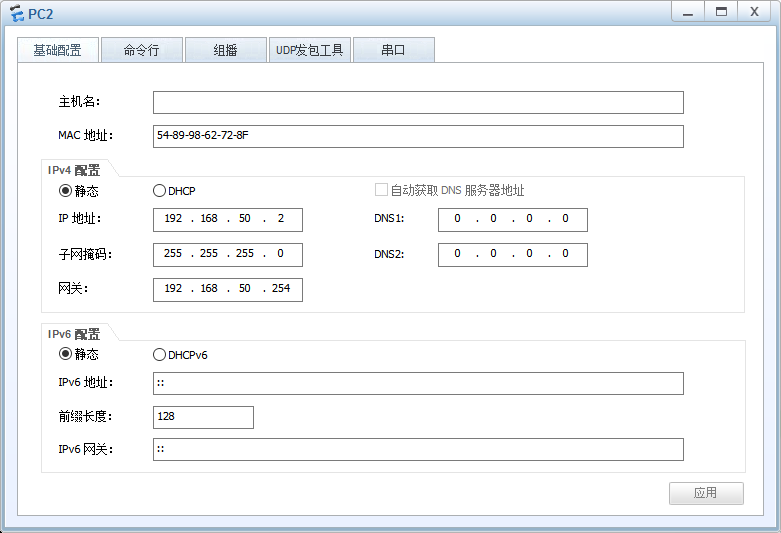
PC2配置:
验证:
默认路由跟踪:

把AR9的ge0/0/1关闭调后,路由跟踪: