一、虚拟机的安装使用
-
文档步骤安装,过程中未出现问题
-
使用虚拟机打开镜像
- 问题:无网络
- 解决:
- 打开虚拟机设置
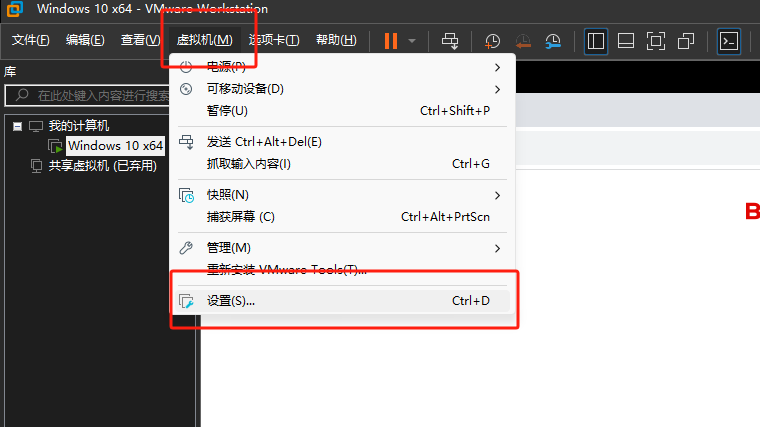
- 网络适配器:网络连接选择“NAT 模式”
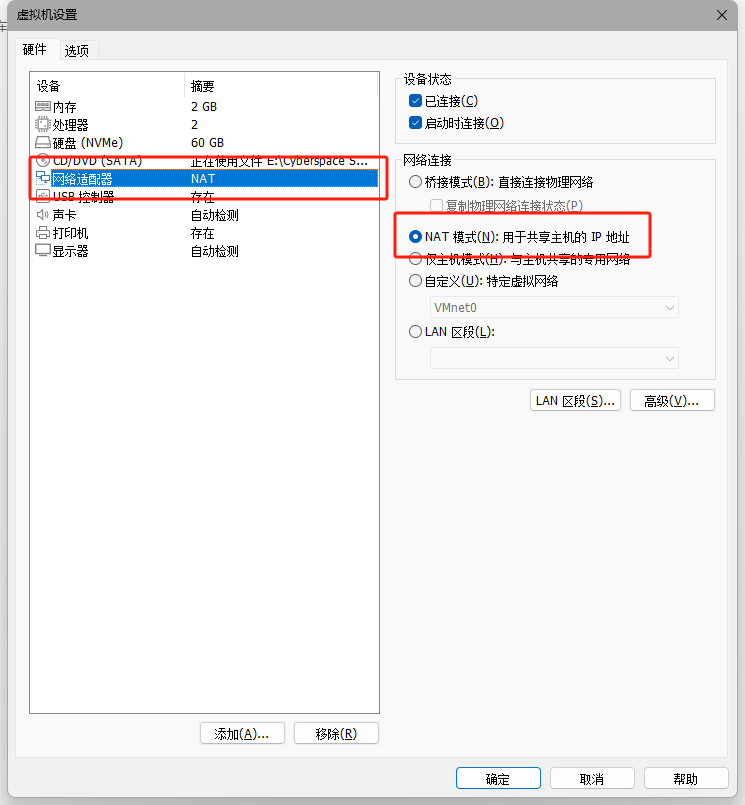
- 打开虚拟机设置
二、工具的安装
Python, Java
- 镜像中已安装,验证环境配置成功
- python
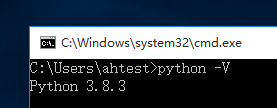
- java
- python
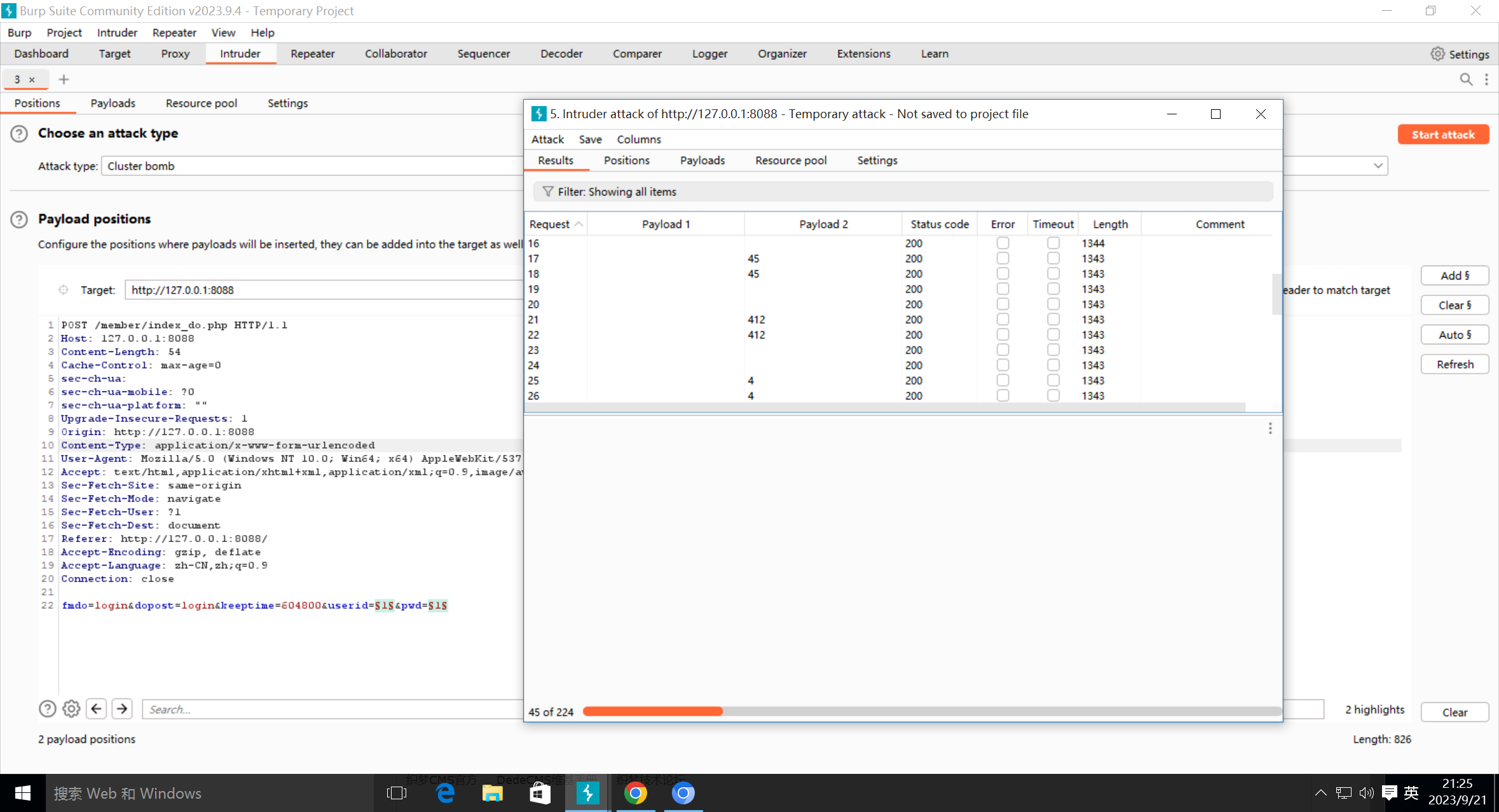
SQLmap
- 按文档安装,并验证安装成功
Nmap
- 按文档安装,并验证安装成功
-
终端中验证
-
图形化界面

-
Burp Suite
- 按文档安装,并验证安装成功
AWVS
- 按照文档描述来验证安装
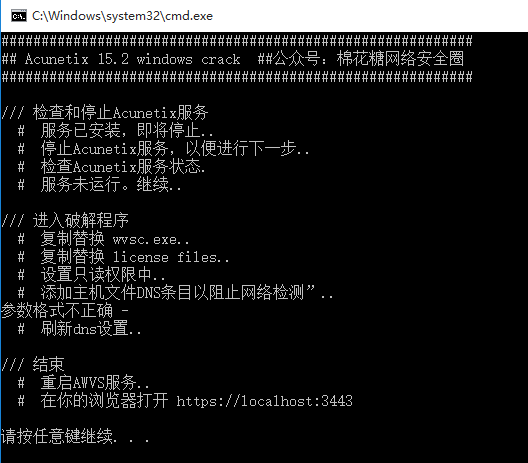
- 按照步骤更改文件内容时突然报错
- 问题:无权限修改
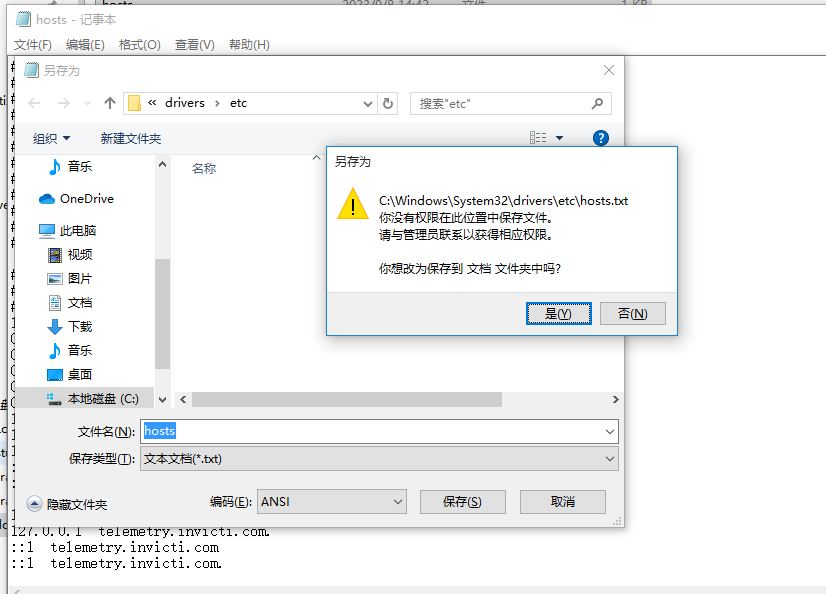
- 解决:
- 本地安全策略->本地策略->安全选项->用户管理控制(如图)->禁用后重启
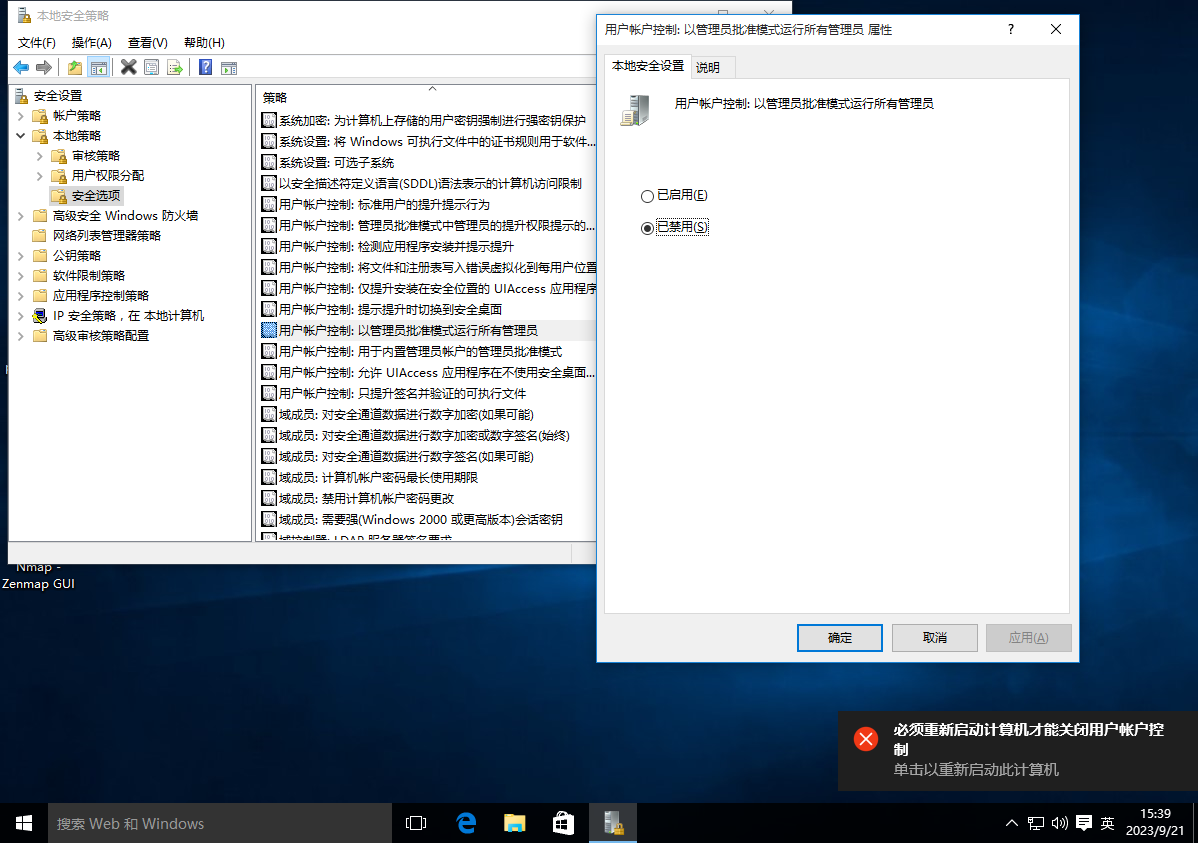
(希望不要留下坑...)
- 本地安全策略->本地策略->安全选项->用户管理控制(如图)->禁用后重启
- 问题:无权限修改
- 登录localhost:3443
账号:awvs@awvs.lan 密码:Awvs@awvs.lan
三、工具的使用
Nmap
-
扫描本机信息
C:\Users\ahtest>ipconfig Windows IP 配置 ... IPv4 地址 . . . . . . . . . . . . : 192.168.152.128 ------------------------------------------------------- C:\Users\ahtest>nmap -O 192.168.152.128 Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-21 16:29 ?D1ú±ê×?ê±?? Nmap scan report for 192.168.152.128 Host is up (0.0037s latency). Not shown: 997 closed tcp ports (reset) PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds Device type: general purpose Running: Microsoft Windows 10 OS CPE: cpe:/o:microsoft:windows_10 OS details: Microsoft Windows 10 10586 - 14393 Network Distance: 0 hops OS detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 2.44 seconds扫得本机运行系统为win10,以及得知一些开放的端口
-
扫描靶机
C:\Users\ahtest>nmap -A 127.0.0.1 Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-21 16:57 ?D1ú±ê×?ê±?? Nmap scan report for localhost (127.0.0.1) Host is up (0.0019s latency). Not shown: 998 closed tcp ports (reset) PORT STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC |_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug) |_ms-sql-info: ERROR: Script execution failed (use -d to debug) 445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP) |_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug) |_ms-sql-info: ERROR: Script execution failed (use -d to debug) Device type: general purpose Running: Microsoft Windows 10 OS CPE: cpe:/o:microsoft:windows_10:1511 OS details: Microsoft Windows 10 1511 Network Distance: 0 hops Service Info: Host: DESKTOP-LQVIT68; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-time: | date: 2023-09-21T08:57:41 |_ start_date: 2023-09-21T07:42:40 |_ms-sql-info: ERROR: Script execution failed (use -d to debug) | smb2-security-mode: | 3:1:1: |_ Message signing enabled but not required |_smb-os-discovery: ERROR: Script execution failed (use -d to debug) OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 43.71 seconds发现没找到靶机处在的端口
8088,于是指定端口扫描C:\Users\ahtest>nmap -p8088 --script http-title 127.0.0.1 ... PORT STATE SERVICE 8088/tcp closed radan-http ...居然没有开?
捣鼓一两个小时,最后咨询老师得知问题所在:没开phpstudy,打开之后重新扫描C:\Users\ahtest>nmap -p8088 --script http-title 127.0.0.1 ... PORT STATE SERVICE 8088/tcp open radan-http |_http-title: \xE6\x88\x91\xE7\x9A\x84\xE7\xBD\x91\xE7\xAB\x99 ...
AWVS
-
扫描漏洞
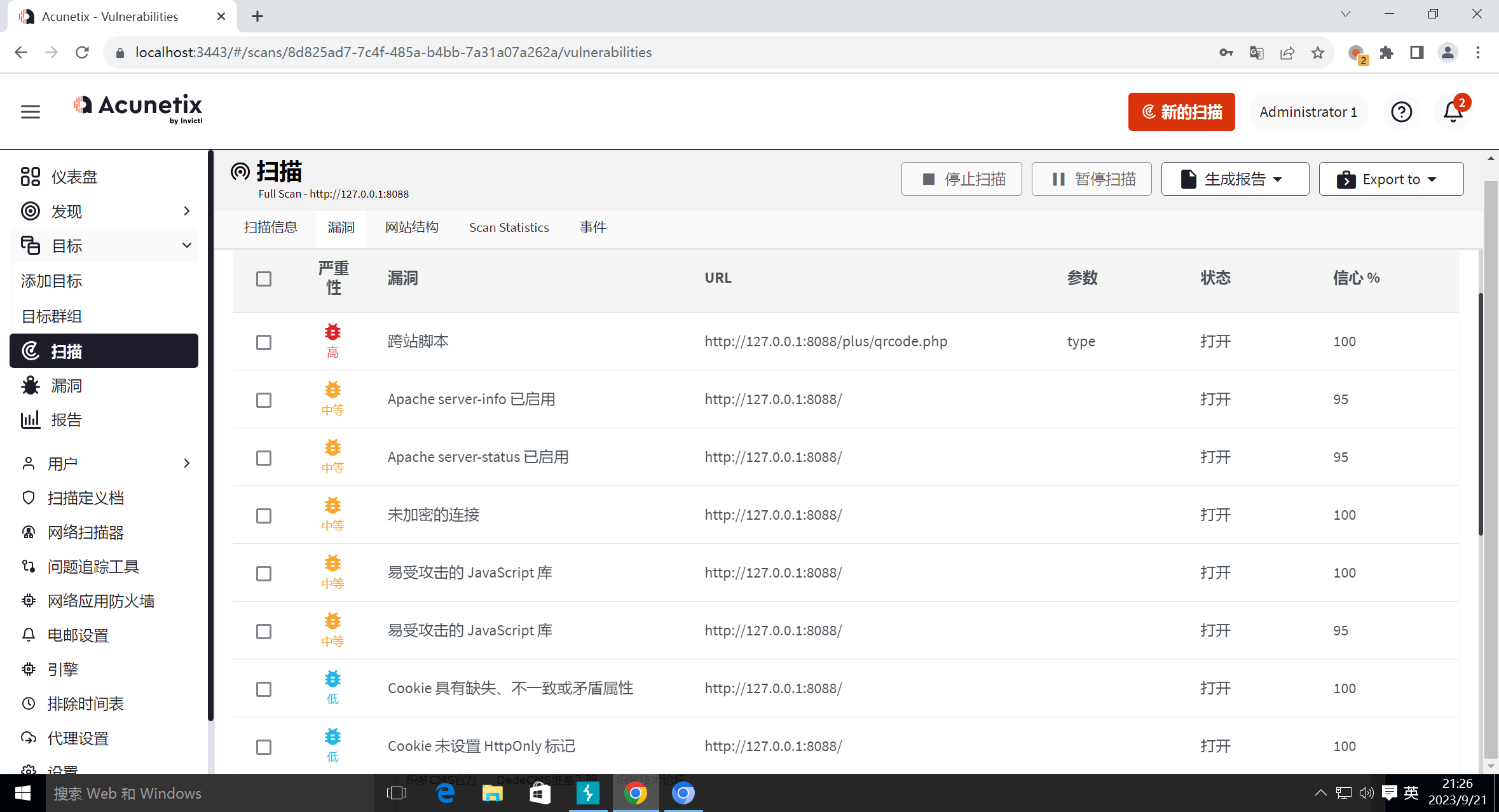
-
待解决:
- 复现漏洞发觉过程
- 如何利用漏洞
BurpSuite
-
截包

-
发包
-
爆破