Nginx config generator All In One
NGINXConfig, Nginx 配置配置高性能、安全、稳定的 Nginx 服务器的最简单方法。
https://github.com/digitalocean/nginxconfig.io
https://www.digitalocean.com/community/tools/nginx?global.app.lang=zhCN
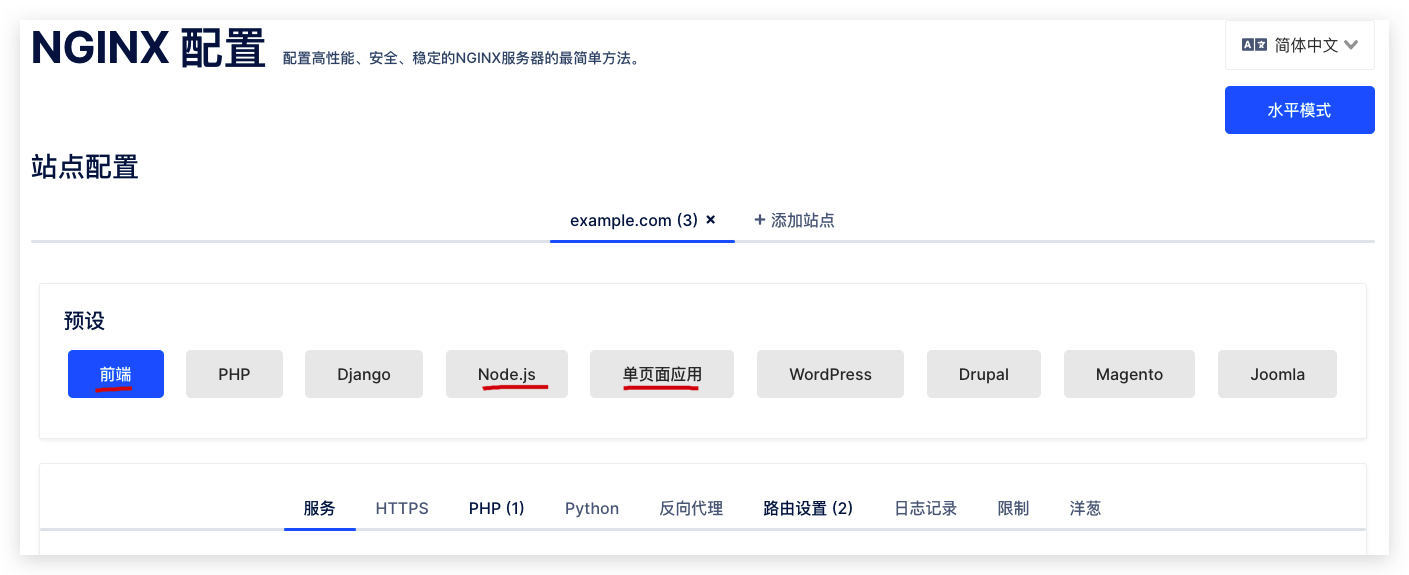
demos
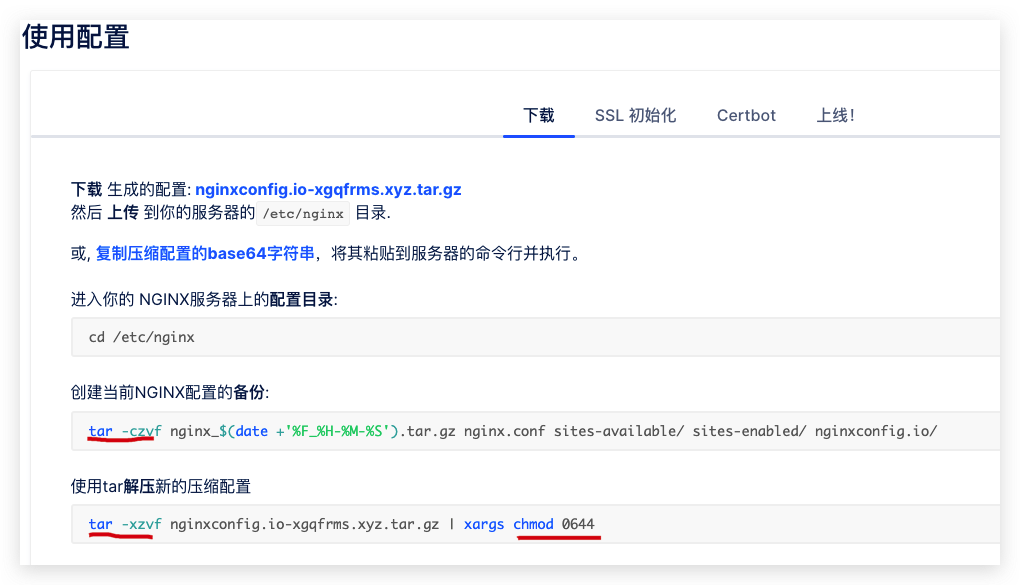
tar
chmod
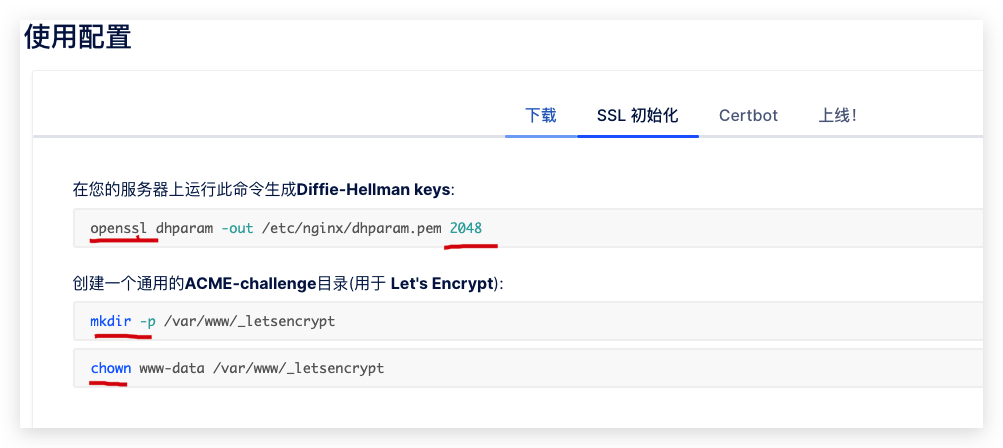
openssl
chown
sed
tee
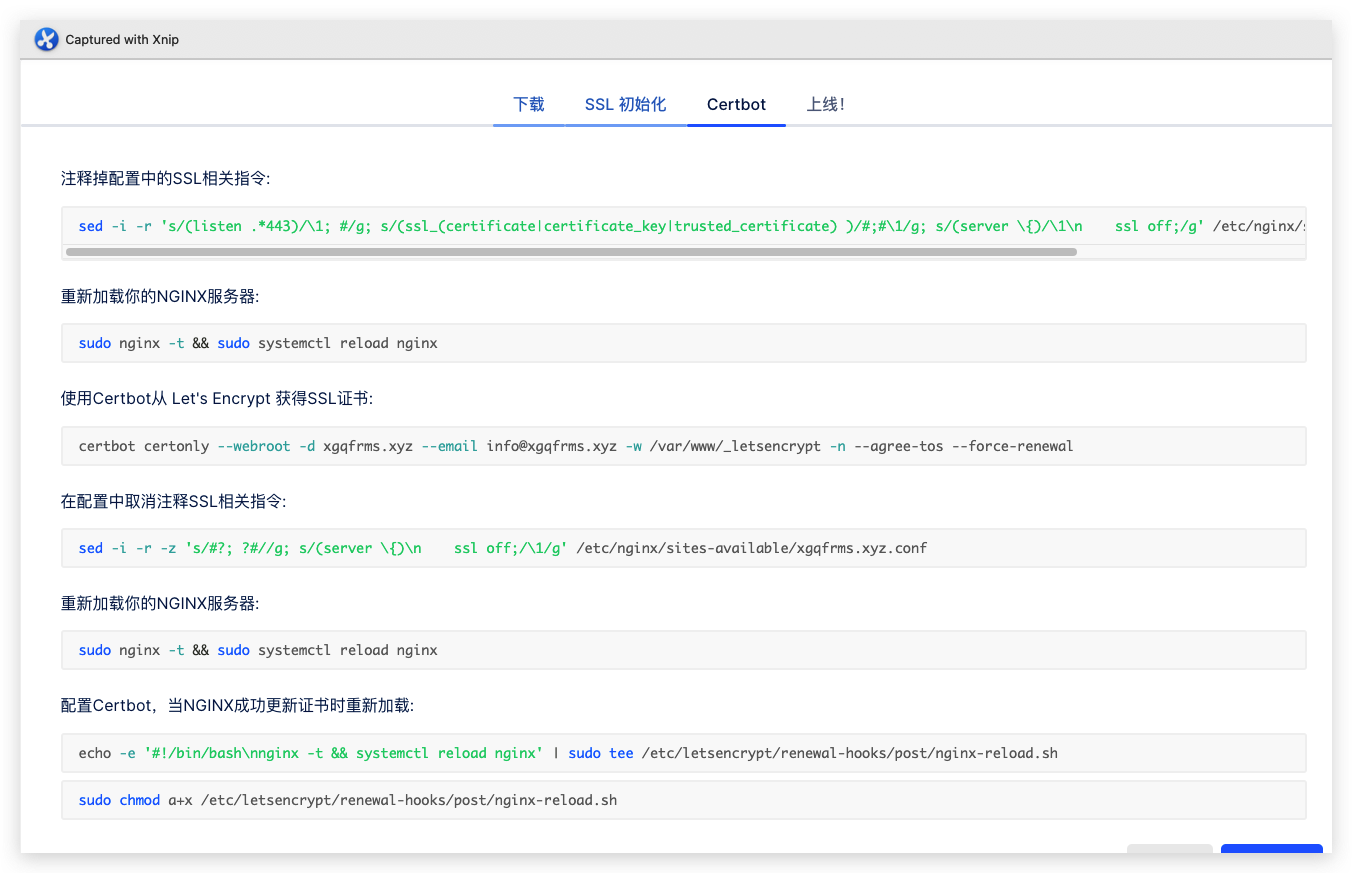
systemctl
/etc/nginx/nginx.conf
# Generated by nginxconfig.io
# See nginxconfig.txt for the configuration share link
user www-data;
pid /run/nginx.pid;
worker_processes auto;
worker_rlimit_nofile 65535;
# Load modules
include /etc/nginx/modules-enabled/*.conf;
events {
multi_accept on;
worker_connections 65535;
}
http {
charset utf-8;
sendfile on;
tcp_nopush on;
tcp_nodelay on;
server_tokens off;
log_not_found off;
types_hash_max_size 2048;
types_hash_bucket_size 64;
client_max_body_size 16M;
# MIME
include mime.types;
default_type application/octet-stream;
# Logging
access_log off;
error_log /dev/null;
# SSL
ssl_session_timeout 1d;
ssl_session_cache shared:SSL:10m;
ssl_session_tickets off;
# Diffie-Hellman parameter for DHE ciphersuites
ssl_dhparam /etc/nginx/dhparam.pem;
# Mozilla Intermediate configuration
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384;
# OCSP Stapling
ssl_stapling on;
ssl_stapling_verify on;
resolver 1.1.1.1 1.0.0.1 8.8.8.8 8.8.4.4 208.67.222.222 208.67.220.220 valid=60s;
resolver_timeout 2s;
# Load configs
include /etc/nginx/conf.d/*.conf;
include /etc/nginx/sites-enabled/*;
}
/etc/nginx/sites-available/xgqfrms.xyz.conf
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name xgqfrms.xyz;
set $base /var/www/xgqfrms.xyz;
root $base/public;
# SSL
ssl_certificate /etc/letsencrypt/live/xgqfrms.xyz/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/xgqfrms.xyz/privkey.pem;
ssl_trusted_certificate /etc/letsencrypt/live/xgqfrms.xyz/chain.pem;
# security
include nginxconfig.io/security.conf;
# logging
access_log /var/log/nginx/access.log combined buffer=512k flush=1m;
error_log /var/log/nginx/error.log warn;
# index.php
index index.php;
# index.php fallback
location / {
try_files $uri $uri/ /index.php?$query_string;
}
# additional config
include nginxconfig.io/general.conf;
# handle .php
location ~ \.php$ {
fastcgi_pass unix:/var/run/php/php-fpm.sock;
include nginxconfig.io/php_fastcgi.conf;
}
}
# subdomains redirect
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name *.xgqfrms.xyz;
# SSL
ssl_certificate /etc/letsencrypt/live/xgqfrms.xyz/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/xgqfrms.xyz/privkey.pem;
ssl_trusted_certificate /etc/letsencrypt/live/xgqfrms.xyz/chain.pem;
return 301 https://xgqfrms.xyz$request_uri;
}
# HTTP redirect
server {
listen 80;
listen [::]:80;
server_name .xgqfrms.xyz;
include nginxconfig.io/letsencrypt.conf;
location / {
return 301 https://xgqfrms.xyz$request_uri;
}
}
(? 反爬虫测试!打击盗版⚠️)如果你看到这个信息, 说明这是一篇剽窃的文章,请访问 https://www.cnblogs.com/xgqfrms/ 查看原创文章!
refs
©xgqfrms 2012-2021
www.cnblogs.com/xgqfrms 发布文章使用:只允许注册用户才可以访问!
原创文章,版权所有©️xgqfrms, 禁止转载 ?️,侵权必究⚠️!