We will use the OpenSSL (https://www.openssl.org/source/) tool to generate self-signed certificates. A certificate authority (CA) is responsible for storing, signing, and issuing digital certificates. This means we will first generate a private key and a self-signed certificate for the certificate authority:
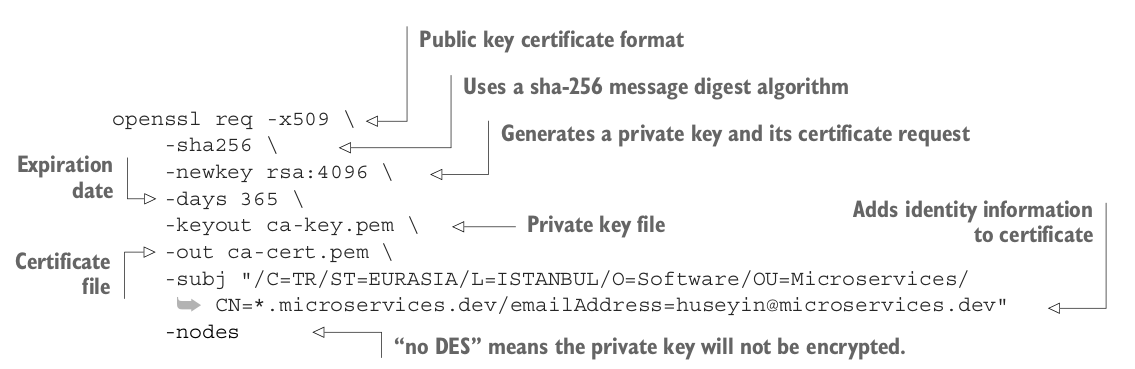
The -subj parameter contains identity information about the certificate:
/C is used for country.
/ST is the state information.
/L states city information.
/O means organization.
/OU is for the organization unit to explain which department.
/CN is used for the domain name, the short version of common name.
/emailAddress is used for an email address to contact the certificate owner.
You can verify the generated self-certificate for the CA with the following command:
openssl x509 -in ca-cert.pem -noout -text
Once you verify it, we can proceed with the private key and certificate signing request:
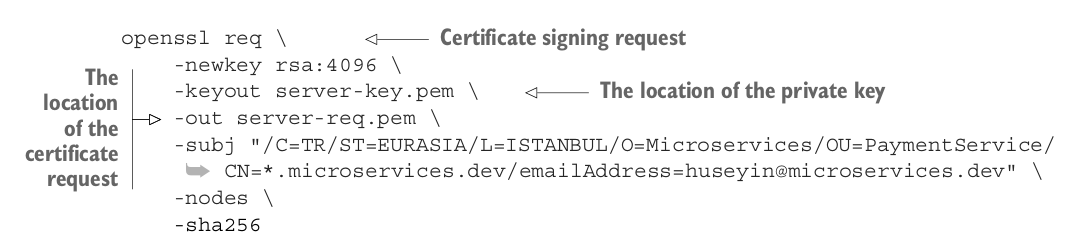
Then we will use CA’s private key to sign the request:
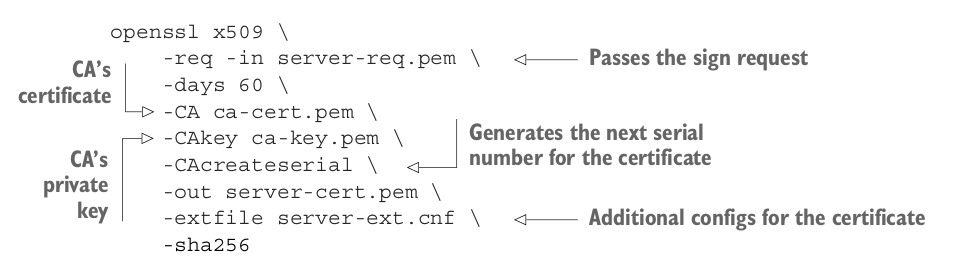
An example configuration for ext file option is as follows:
subjectAltName=DNS:*.microservices.dev,DNS:*.microservices.dev,IP:0.0.0.0
Now you can verify the server’s self-signed certificate:
openssl x509 -in server-cert.pem -noout -text
For mTLS communication, we need to generate a certificate signing request for the client side, so let’s generate a private key and this self-signed certificate:
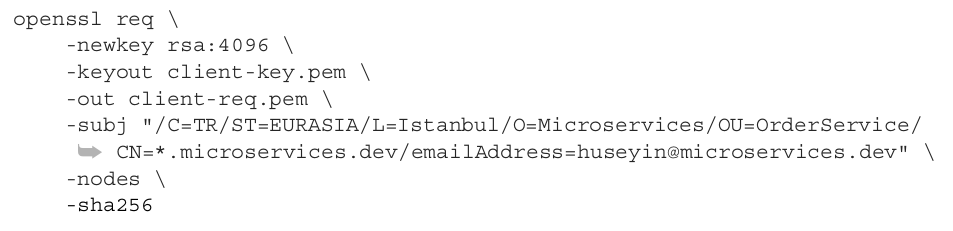
Now, let’s sign it using the CA’s private key:
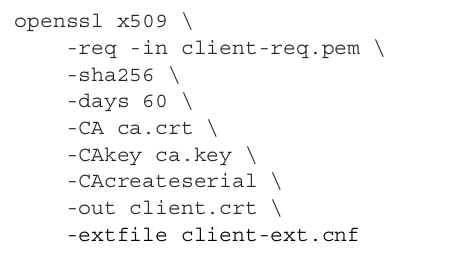
Finally, you can verify the client certificate with the following command:
openssl x509 -in client-cert.pem -noout -text
- Certificate Generation OpenSSLcertificate generation openssl self-signed certificate openssl signed generation text-generation-webui next-generation empowering generation difformer diffusion error generation kustomize manifest oobabooga-text-generation-webui any-to-any generation composable any font generation diff-font diffusion