[SCTF2019]Who is he
打开文件夹发现是个unity程序,先运行下看
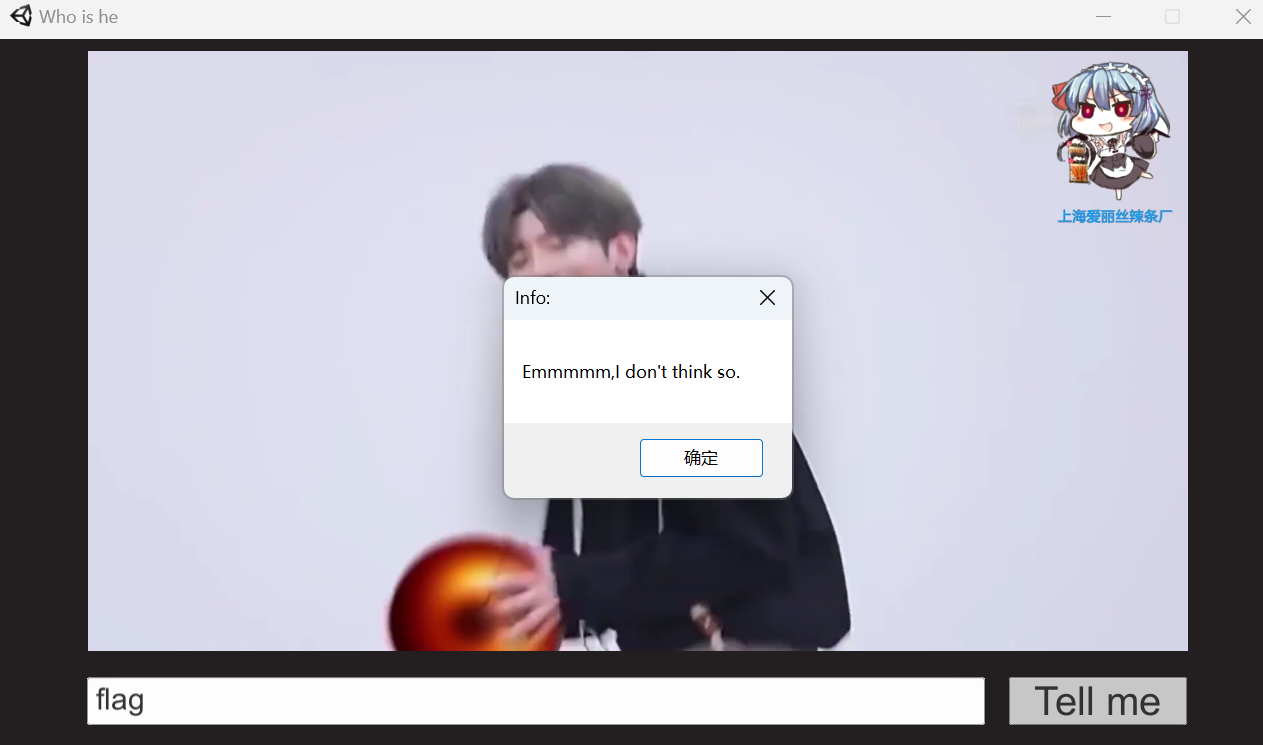
推测正确的输入为flag,所以此时用dnspy继续进行分析
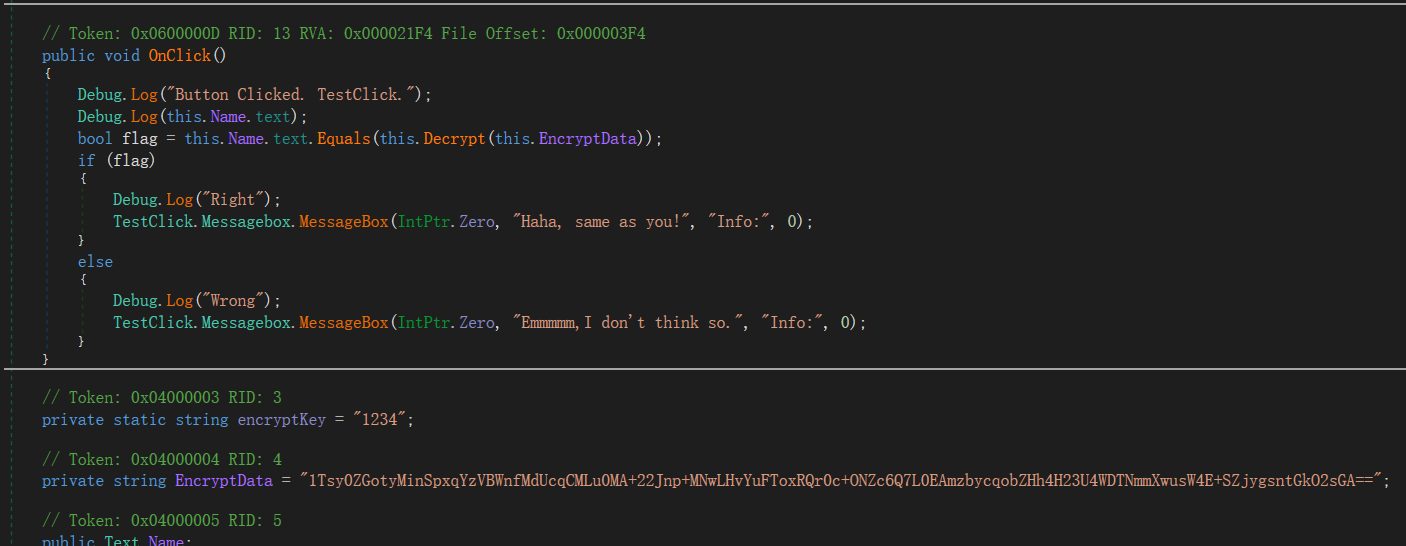

发现了关键函数,这个Decrypt()就是得到正确flag的地方,所以我们按照该解密函数的逻辑写出解密脚本:
from pyDes import des,PAD_PKCS5,CBC
import base64
s=base64.b64decode('1Tsy0ZGotyMinSpxqYzVBWnfMdUcqCMLu0MA+22Jnp+MNwLHvYuFToxRQr0c+ONZc6Q7L0EAmzbycqobZHh4H23U4WDTNmmXwusW4E+SZjygsntGkO2sGA==')
# 密钥需要8个字节,且unicode字符串,转成字节数组每个字符后要加\x00
key = b'1\x002\x003\x004\x00'
des_obj=des(key,CBC,key,padmode=PAD_PKCS5)
m=des_obj.decrypt(s)
print(m.decode('UTF-16'))
得到flag,提交后发现失败
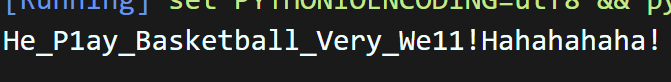
看来这是出题人挖的一个坑,查询资料得知需要使用CE来进行分析
使用CE打开程序,对输入失败时的字符串进行搜索,发现了几个内存地址
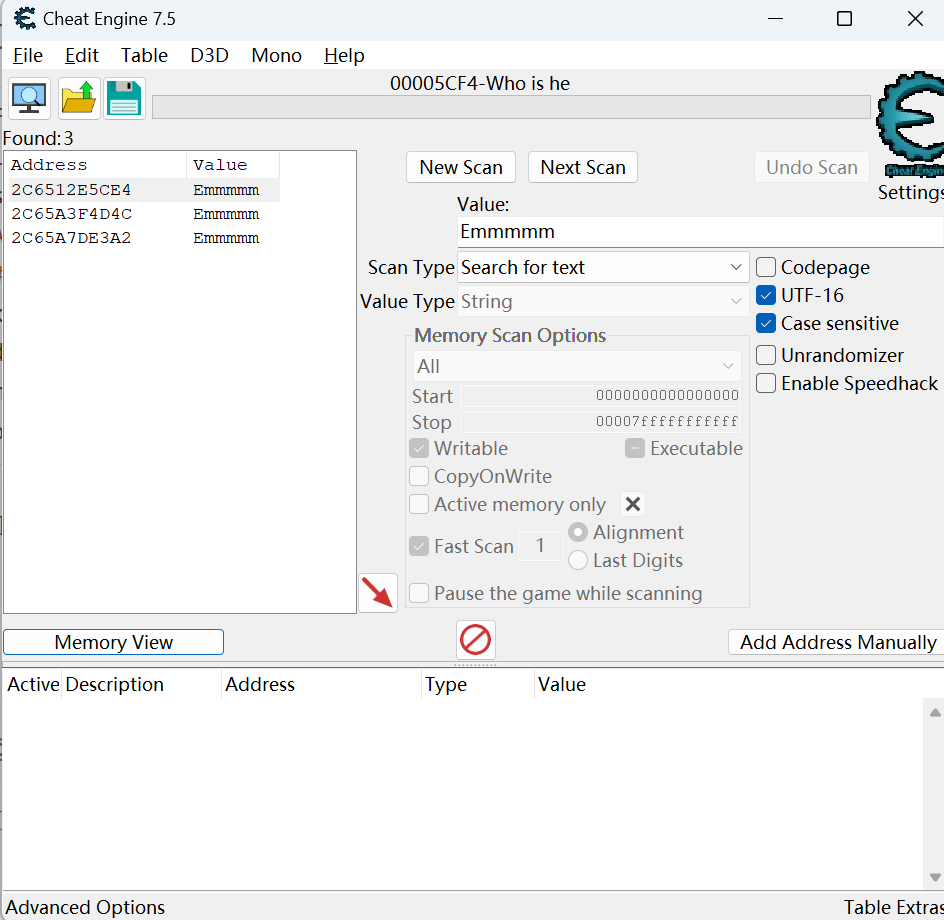
此时我们直接定位到对应的内存,发现了疑似真正的密文和密钥
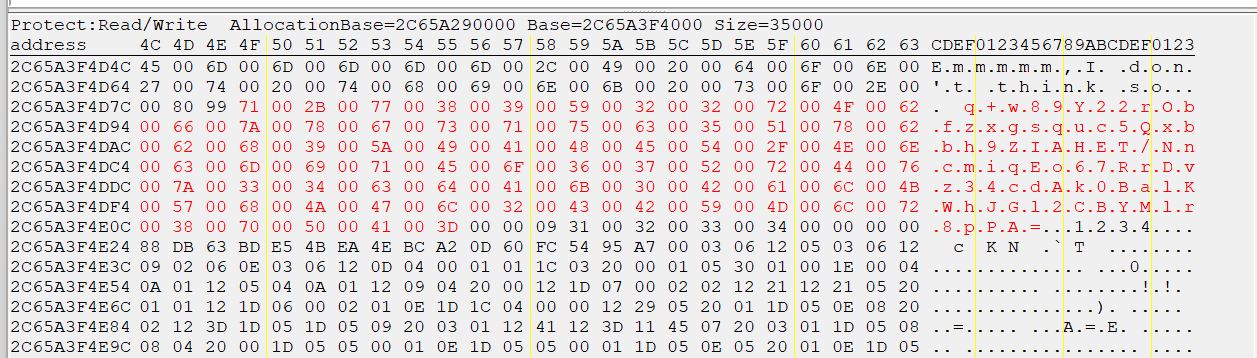
解题脚本如下:
from pyDes import des,PAD_PKCS5,CBC
import base64
miwen_raw = '71 00 2B 00 77 00 38 00 39 00 59 00 32 00 32 00 72 00 4F 00 62 00 66 00 7A 00 78 00 67 00 73 00 71 00 75 00 63 00 35 00 51 00 78 00 62 00 62 00 68 00 39 00 5A 00 49 00 41 00 48 00 45 00 54 00 2F 00 4E 00 6E 00 63 00 6D 00 69 00 71 00 45 00 6F 00 36 00 37 00 52 00 72 00 44 00 76 00 7A 00 33 00 34 00 63 00 64 00 41 00 6B 00 30 00 42 00 61 00 6C 00 4B 00 57 00 68 00 4A 00 47 00 6C 00 32 00 43 00 42 00 59 00 4D 00 6C 00 72 00 38 00 70 00 50 00 41 00 3D'
mi_list = miwen_raw.split(' ')
miwen = ''
for i in range(len(mi_list)):
if int(('0x'+mi_list[i]),16) != 0:
miwen += chr(int(('0x'+mi_list[i]),16))
s=base64.b64decode(miwen)
# 密钥需要8个字节,且unicode字符串,转成字节数组每个字符后要加\x00
key = b'1\x002\x003\x004\x00'
des_obj=des(key,CBC,key,padmode=PAD_PKCS5)
m=des_obj.decrypt(s)
print(m.decode('UTF-16'))
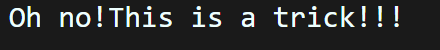
根据提示可以得知这仍然不是真正的flag,因此查看最后一个内存地址
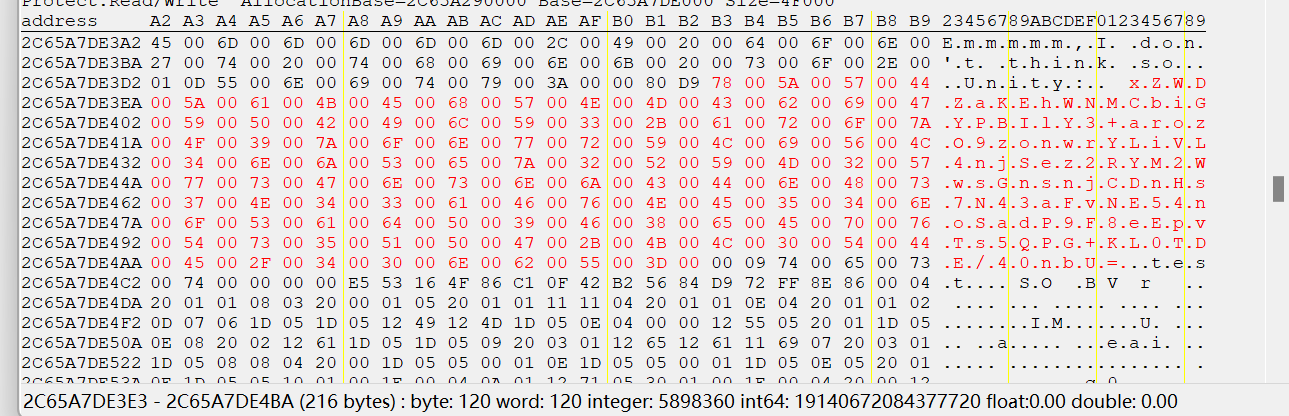
此时密文以及密钥都发生了变化,编写解题脚本如下:
from pyDes import des,PAD_PKCS5,CBC
import base64
miwen_raw = '78 00 5A 00 57 00 44 00 5A 00 61 00 4B 00 45 00 68 00 57 00 4E 00 4D 00 43 00 62 00 69 00 47 00 59 00 50 00 42 00 49 00 6C 00 59 00 33 00 2B 00 61 00 72 00 6F 00 7A 00 4F 00 39 00 7A 00 6F 00 6E 00 77 00 72 00 59 00 4C 00 69 00 56 00 4C 00 34 00 6E 00 6A 00 53 00 65 00 7A 00 32 00 52 00 59 00 4D 00 32 00 57 00 77 00 73 00 47 00 6E 00 73 00 6E 00 6A 00 43 00 44 00 6E 00 48 00 73 00 37 00 4E 00 34 00 33 00 61 00 46 00 76 00 4E 00 45 00 35 00 34 00 6E 00 6F 00 53 00 61 00 64 00 50 00 39 00 46 00 38 00 65 00 45 00 70 00 76 00 54 00 73 00 35 00 51 00 50 00 47 00 2B 00 4B 00 4C 00 30 00 54 00 44 00 45 00 2F 00 34 00 30 00 6E 00 62 00 55 00 3D'
mi_list = miwen_raw.split(' ')
miwen = ''
for i in range(len(mi_list)):
if int(('0x'+mi_list[i]),16) != 0:
miwen += chr(int(('0x'+mi_list[i]),16))
s=base64.b64decode(miwen)
# 密钥需要8个字节,且unicode字符串,转成字节数组每个字符后要加\x00
key = b't\x00e\x00s\x00t\x00'
des_obj=des(key,CBC,key,padmode=PAD_PKCS5)
m=des_obj.decrypt(s)
print(m.decode('UTF-16'))
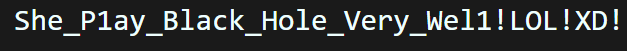
将最后的flag提交发现成功,因此本题的flag为:
flag{She_P1ay_Black_Hole_Very_Wel1!LOL!XD!}