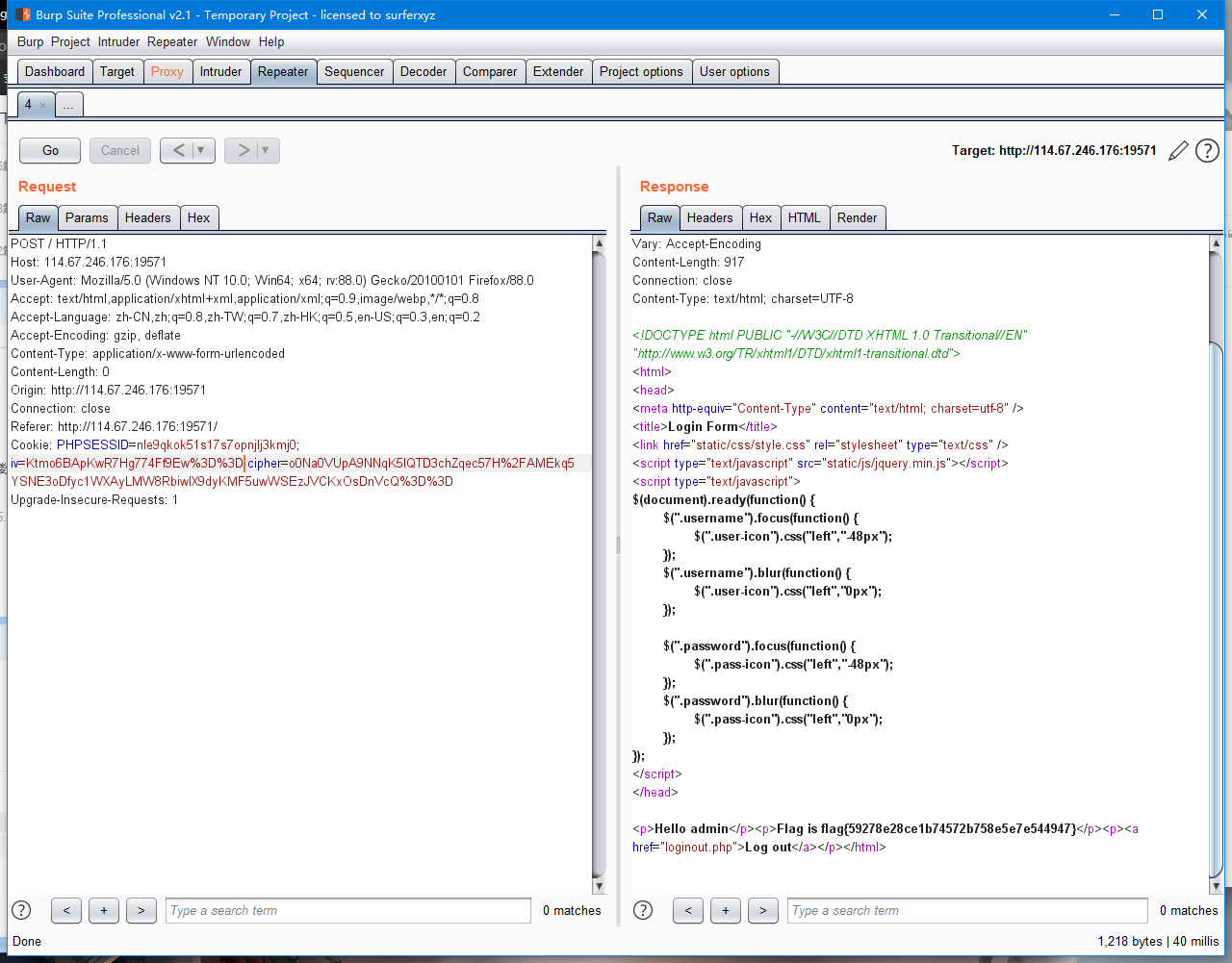
传入cipher::
o0Na0VUpA9NNqK5lQTP3chZqec57H%2FAMEkq5YSNE3oDfyc1WXAyLMW8RbiwIX9dyKMF5uwWSEzJVCKxOsDnVcQ%3D%3D
传入的vi::
L4p%2BUXpwki%2FiUktyYxs7eg%3D%3D
<?php
header("Content-Type: text/html;charset=utf-8");
#计算cipher
/*
明文1:a:2:{s:8:"userna //r
明文2:me";s:5:"admil"; //l字母在第14个字节
明文3:s:8:"password";s
明文4::3:"123";}
*/
$cipher = base64_decode(urldecode('o0Na0VUpA9NNqK5lQTP3chZqec57H%2FAMEkq5YSNE3oDfyc1WXAyLMW8RbiwIX9dyKMF5uwWSEzJVCKxOsDnVcQ%3D%3D'));
$temp = $cipher;
/*
设密文1[13]=A, 解密(密文2)[13]=B, 明文2[13]=C,
将A修改为A ^ C,则:
A ^ B = A ^ C ^ B = B ^ B = 0 = C
*/
// A C X
$cipher[13] = chr(ord($cipher[13]) ^ ord('m') ^ ord('n'));
echo urlencode(base64_encode($cipher));
?>
解的::
o0Na0VUpA9NNqK5lQTD3chZqec57H%2FAMEkq5YSNE3oDfyc1WXAyLMW8RbiwIX9dyKMF5uwWSEzJVCKxOsDnVcQ%3D%3D
传入后报错:
base64_decode('ZGnkgxEqgxOjbjD65j6oCG1lIjtzOjU6ImFkbWluIjtzOjg6InBhc3N3b3JkIjtzOjA6IiI7fQ==') can't unserialize
在处理vi::
<?php
#计算iv
$res = base64_decode('ZGnkgxEqgxOjbjD65j6oCG1lIjtzOjU6ImFkbWluIjtzOjg6InBhc3N3b3JkIjtzOjA6IiI7fQ=='); //这里放burp放回的base64数据
$iv = base64_decode(urldecode('L4p%2BUXpwki%2FiUktyYxs7eg%3D%3D')); //这里放cookie中的iv
$plaintext = 'a:2:{s:8:"userna';
$new_iv = '';
for ($i = 0; $i < 16; $i ++){
$new_iv = $new_iv . chr(ord($iv[$i]) ^ ord($res[$i]) ^ ord($plaintext[$i]));
}
echo urlencode(base64_encode($new_iv));
?>
截取cipher进行异或操作;;因为序列化后可以看到传入的用户名的位置;;进行异或操作之后修改用户名为admin;;之后在提交;通过返回的数据包解密得到序列化后的文件,通过序列化后的文件在对vi进行重新编译;;