Reverse
ldd
UPX魔改修复段 UPX0, UPX1
花指令修复
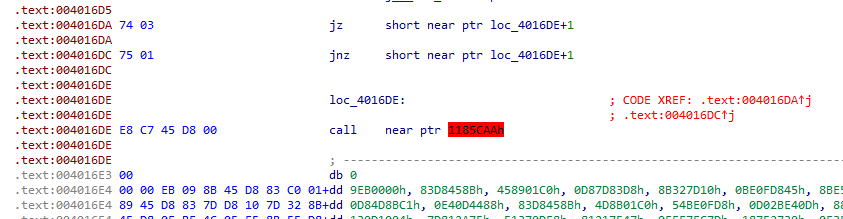
u掉 call ,然后E8这个指令nop掉。下一行按 c。main处按p 即可恢复代码。
int __cdecl main_0(int argc, const char **argv, const char **envp)
{
FILE *v3; // eax
char v5; // [esp+0h] [ebp-F8h]
char v6; // [esp+0h] [ebp-F8h]
int i; // [esp+D0h] [ebp-28h]
char Buffer[24]; // [esp+DCh] [ebp-1Ch] BYREF
strcpy(Buffer, "DASCTF{????????}");
sub_40107D("Please input your answer:\n", v5);
v3 = _acrt_iob_func(0);
fgets(Buffer, 17, v3);
for ( i = 0; i < 16; ++i )
{
Buffer[i] ^= Buffer[i + 1];
Buffer[i] -= i + 1;
}
if ( *(_DWORD *)Buffer == 0x130D1004
&& *(_DWORD *)&Buffer[4] == 0x4751370D
&& *(_DWORD *)&Buffer[8] == 0x2730FEF7
&& *(_DWORD *)&Buffer[12] == 0x6D0AFAF3 )
{
sub_40107D("WoW, you are get the true flag!", v6);
}
else
{
sub_40107D("errorrrr!", v6);
}
return 0;
}
z3 解方程.
from natsort import natsorted
from z3 import *
s = [BitVec('s1_%d' % i, 8) for i in range(17)]
enc = [0x04,0x10,0x0d,0x13,0x0d,0x37,0x51,0x47,0xf7,0xfe,0x30,0x27,0xf3,0xfa,0x0a,0x6d]
s[16] = 0
solver = Solver()
for i in range(16):
s[i] ^= s[i + 1]
s[i] -= i + 1
for i in range(16):
solver.add(s[i] == enc[i])
print(solver.check())
res = solver.model()
lst = natsorted([(k, res[k]) for k in res], lambda x: str(x[0]))
for k, v in lst:
print(chr(v.as_long()), end='')
luoing

.text:0019602B 0E8 55 push ebp
.text:0019602C 0EC E8 00 00 00 00 call $+5
.text:0019602C
.text:00196031
.text:00196031 loc_196031: ; DATA XREF: sub_196010+23↓o
.text:00196031 0F0 5D pop ebp
.text:00196032 0EC 48 dec eax
.text:00196033 0EC 83 C5 08 add ebp, (offset loc_196039 - offset loc_196031)
.text:00196036 0EC 55 push ebp
.text:00196037 0F0 C3 retn
.text:00196037
.text:00196037 sub_196010 endp ; sp-analysis failed
.text:00196037
.text:00196037 ; ---------------------------------------------------------------------------
.text:00196038 E8 db 0E8h
.text:00196039 ; ---------------------------------------------------------------------------
.text:00196039
.text:00196039 loc_196039: # 上面全是垃圾代码 ; DATA XREF: sub_196010+23↑o
.text:00196039 5D pop ebp
这些都是垃圾代码。nop掉。 下面代码按u。main 处 u, p
web
百分富翁
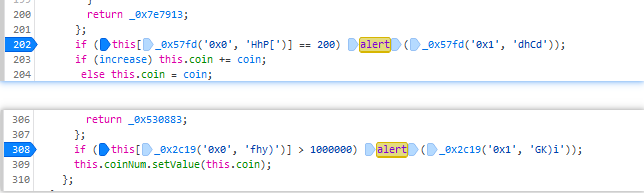
Firefox格式化js代码后。
在对应的alert处修改判断值,即可弹出flag1,flag2.
Crypto
classical && coding
https://www.yii666.com/blog/5791.html?version=2.5.50000.153&platform=win
照着做。
From HTML Entity
From Charcode base 10
Brainfuck
Morse
词频。
Misc
m00n
- 解压 m00n.zip 4位密码:
m00n - 将m00n.jpg 另存为 png, 补全 flag 文件的png头和尾部。另存为 flag.png
- fff.txt 零宽隐写得到
开头两个字母大写,其余小写 moon.jpg右击属性得到 outguess的消息 。
fff.txt用sublime或者 vscode 全选能看到morse码。解出CORRECT_MORSE
outguess -k "Correct_Morse" -r m00n.jpg -t 1.txt` 得到 `1sb_SecRet
cloacked-pixel解密 得到 flag