1、Dashboard
1.1、安装
请参考7、Dashboard部署:https://www.cnblogs.com/ygbh/p/17221496.html
1.2、确认dashboard正常访问
1.2.1、查询布署到哪个节点上
master1 ~]# kubectl get pods -n kubernetes-dashboard -o wide NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES dashboard-metrics-scraper-64bcc67c9c-zbx6r 1/1 Running 0 12d 10.244.4.29 node2 <none> <none> kubernetes-dashboard-5c8bd6b59-dwp5t 1/1 Running 0 13d 10.244.4.8 node2 <none> <none> master1 ~]# kubectl get svc -n kubernetes-dashboard -o wide NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR dashboard-metrics-scraper NodePort 10.102.192.36 <none> 8000:30001/TCP 13d k8s-app=dashboard-metrics-scraper kubernetes-dashboard NodePort 10.98.68.75 <none> 443:30443/TCP 13d k8s-app=kubernetes-dashboard
1.2.2、使用浏览器访问是否正常
1.3、认证解析
1.3.1、认证方法类型
对于dashboard来说,他的认证方法主要有两种:令牌认证和文件认证。由于涉及面比较多,我们通过两节的内容来进行讲解,在这里我们用令牌的方式来学习完整的服务认证流程。 令牌认证 - 基于认证用户的唯一令牌来进行认证,有默认的超时机制,一会儿就失效了 文件认证 - 基于账号的token信息,创建kubeconfig文件,实现长久的认证方式。
1.3.2、dashboard创建sa绑定的流程
根据我们之前对serviceaccount的工作流程的学习,对于dashboard的配置也应该遵循相应的操作流程: 1、创建专用的serviceaccount 2、创建对应的权限角色 3、将serviceaccount和权限角色进行关联绑定
2、Dashboard令牌认证-实践
2.1、认证授权方法
2.1.1、方法1:命令的方式-创建sa并且绑定集群角色
# 创建sa和绑定集群角色 kubectl create serviceaccount dashboard-admin -n kubernetes-dashboard kubectl create clusterrolebinding dashboard-admin --clusterrole=cluster-admin --serviceaccount=kubernetes-dashboard:dashboard-admin # 使用 --dry-run=client -o yaml 可以打印出yaml,方便使用yaml创建。 参数详解: --clusterrole=集群角色名称 --serviceaccount=命名空间:serviceaccountname 由于我们这里配置的是全局用户,所有命名空间是kubernetes-dashboard dashboard需要操作各种资源的所有权限,所以我们需要和cluster-admin的clusterrole进行绑定 #关联token,新版本有一些不会自动关联 kubectl apply -f - <<EOF apiVersion: v1 kind: Secret metadata: name: dashboard-admin-secret namespace: kubernetes-dashboard annotations: kubernetes.io/service-account.name: dashboard-admin type: kubernetes.io/service-account-token EOF
2.1.2、方法2:yaml的方式-创建sa并且绑定集群角色
kubectl apply -f - <<EOF apiVersion: v1 kind: ServiceAccount metadata: name: dashboard-admin namespace: kubernetes-dashboard --- apiVersion: v1 kind: Secret metadata: name: dashboard-admin-secret namespace: kubernetes-dashboard annotations: kubernetes.io/service-account.name: dashboard-admin type: kubernetes.io/service-account-token --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: creationTimestamp: null name: dashboard-admin roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: dashboard-admin namespace: kubernetes-dashboard EOF
2.2、获取token
2.2.1、查询secret
master1 ~]# kubectl -n kubernetes-dashboard get secrets NAME TYPE DATA AGE dashboard-admin-secret kubernetes.io/service-account-token 3 10m # 这个是我们创建关联的secret token kubernetes-dashboard-certs Opaque 0 13d kubernetes-dashboard-csrf Opaque 1 13d kubernetes-dashboard-key-holder Opaque 2 13d
2.2.2、获取token
# 方法1-推荐-但需要base64解码 kubectl -n kubernetes-dashboard get secrets dashboard-admin-secret -o go-template --template='{{.data.token}}' | base64 -d # 方法2 kubectl -n kubernetes-dashboard describe secrets dashboard-admin-secret | grep token | awk '{print $2}'
2.2.4、复制token到dashboard登陆
2.2.5、登陆成功界面
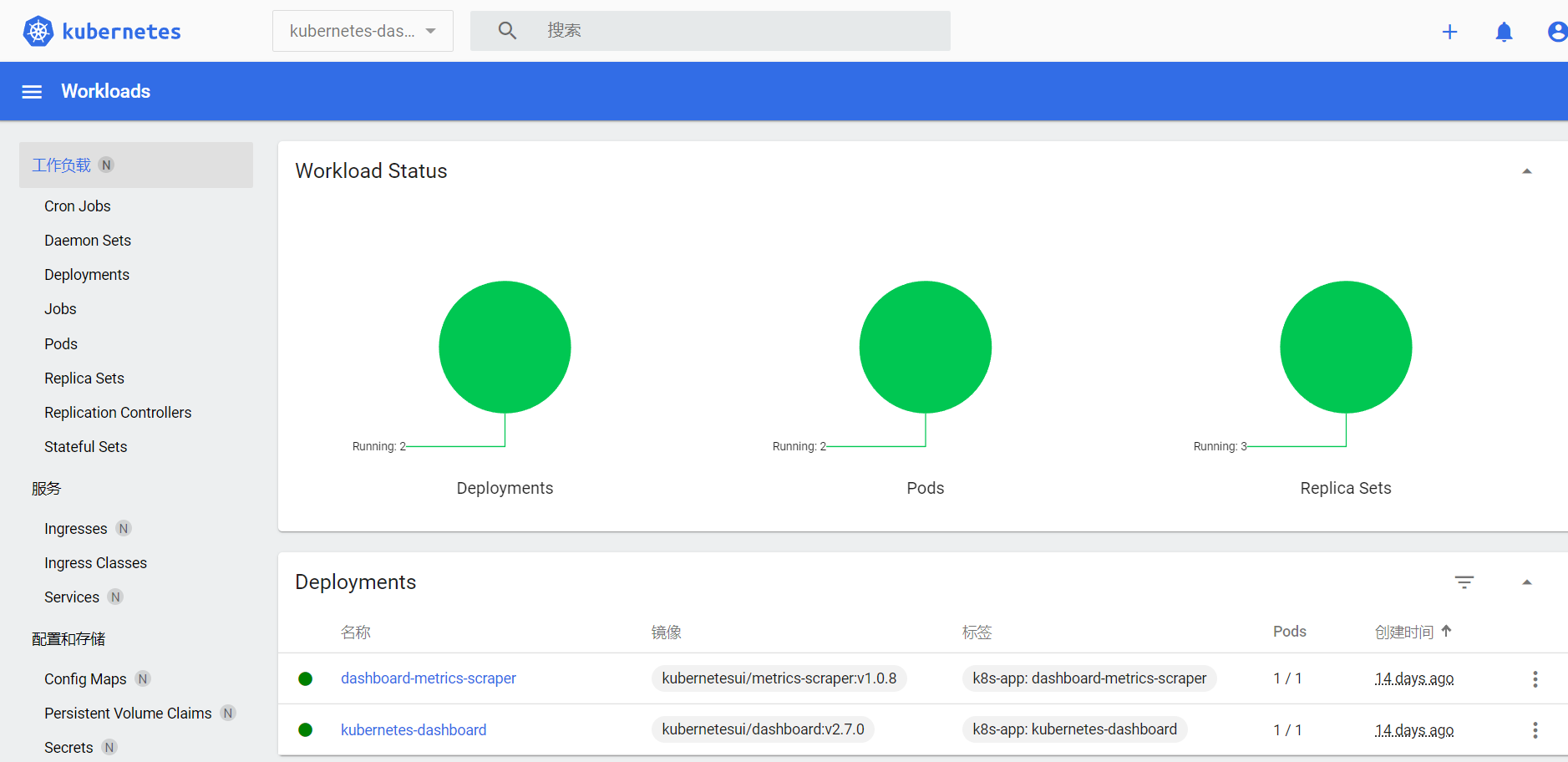
2.2.6、dashboard-admin用户是可以看到全部的命名空间
此权限太大,下一小节介绍,限定命令空间,访问

2.3、创建用户-限定命名空间使用
2.3.1、使用命令方法-创建用户并且绑定
kubectl create serviceaccount def-ns-admin -n default kubectl create rolebinding def-ns-admin --clusterrole=admin --serviceaccount=default:def-ns-admin kubectl apply -f - <<EOF apiVersion: v1 kind: Secret metadata: name: def-ns-admin-secret namespace: default annotations: kubernetes.io/service-account.name: def-ns-admin type: kubernetes.io/service-account-token EOF
# 注意:如果要使用yaml的话,请使用--dry-run=client -o yaml生成后,再拼接
2.3.2、获取token进行登陆
kubectl describe secrets def-ns-admin-secret | grep token | awk '{print $2}'
2.3.3、登陆后的效果
当前的dashboard,仅仅能管理default命名空间下的资源

2、Dashboard-Kubeconfig文件认证-实践
2.1、通用认证-拥有所有权限
2.1.1、当前sa的帐号
# sa:dashboard-admin 所有权限 master1 ~]# kubectl -n kubernetes-dashboard get sa dashboard-admin NAME SECRETS AGE dashboard-admin 0 93m # sa:def-ns-admin 只有default命名空间的权限 master1 ~]# kubectl get sa def-ns-admin NAME SECRETS AGE def-ns-admin 0 66m
2.1.2、设置集群生成配置文件
# 设置集群:即在基于当前kubernetes集群,生成只有公钥证书的配置文件,方便加入用户 kubectl config set-cluster kubernetes --certificate-authority=/etc/kubernetes/pki/ca.crt --server=https://vip.k8test.com:6443 --embed-certs=true --kubeconfig=/root/kubeadm.conf # 查看当前的配置 master1 ~]# kubectl config view --kubeconfig=/root/kubeadm.conf apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://vip.k8test.com:6443 name: kubernetes contexts: null current-context: "" kind: Config preferences: {} users: null
2.1.3、配置用户
# 1、获取dashboard-admin的secret ]# kubectl -n kubernetes-dashboard get secrets | grep admin dashboard-admin-secret kubernetes.io/service-account-token 3 102m # 2、获取dashboard-admin-secret的token KUBEADMIN_TOKEN=$(kubectl -n kubernetes-dashboard get secrets dashboard-admin-secret -o jsonpath='{.data.token}' | base64 -d) # 3、设置用户信息 kubectl config set-credentials dashboard-admin --token=$KUBEADMIN_TOKEN --kubeconfig=/root/kubeadm.conf ]# kubectl config view --kubeconfig=/root/kubeadm.conf apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://vip.k8test.com:6443 name: kubernetes contexts: null current-context: "" kind: Config preferences: {} users: - name: dashboard-admin # 这个就是增加完成的用户 user: token: REDACTED
2.1.4、配置上下文
]# kubectl config set-context dashboard-admin@kubernetes --cluster=kubernetes --user=dashboard-admin --kubeconfig=/root/kubeadm.conf ]# kubectl config view --kubeconfig=/root/kubeadm.conf apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://vip.k8test.com:6443 name: kubernetes contexts: - context: cluster: kubernetes user: dashboard-admin name: dashboard-admin@kubernetes current-context: "" kind: Config preferences: {} users: - name: dashboard-admin user: token: REDACTED
2.1.5、切换用户
]# kubectl config use-context dashboard-admin@kubernetes --kubeconfig=/root/kubeadm.conf ]# kubectl config view --kubeconfig=/root/kubeadm.conf apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://vip.k8test.com:6443 name: kubernetes contexts: - context: cluster: kubernetes user: dashboard-admin name: dashboard-admin@kubernetes current-context: dashboard-admin@kubernetes kind: Config preferences: {} users: - name: dashboard-admin user: token: REDACTED
2.1.6、确认命令行下可以正常使用
]# kubectl get sa --kubeconfig=/root/kubeadm.conf NAME SECRETS AGE admin 0 28h def-ns-admin 0 101m default 0 14d
2.1.7、使用新建的kubeconfig文件-登陆Dashboard
复制文件kubeadm.conf到电脑桌面,使用Kubeconfig方式登陆
2.1.8、登陆成功
拥有所有命名空间的权限

2.2、单用户认证-只有default命令空间权限
2.2.1、当前sa的帐号
# sa:dashboard-admin 所有权限
master1 ~]# kubectl -n kubernetes-dashboard get sa dashboard-admin
NAME SECRETS AGE
dashboard-admin 0 93m
# sa:def-ns-admin 只有default命令空间权限
master1 ~]# kubectl get sa def-ns-admin
NAME SECRETS AGE
def-ns-admin 0 66m
2.2.2、设置集群生成配置文件
]# kubectl config set-cluster kubernetes --certificate-authority=/etc/kubernetes/pki/ca.crt --server=https://vip.k8test.com:6443 --embed-certs=true --kubeconfig=/root/def-ns-admin.conf ]# kubectl config view --kubeconfig=/root/def-ns-admin.conf apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://vip.k8test.com:6443 name: kubernetes contexts: null current-context: "" kind: Config preferences: {} users: null
2.2.3、配置用户
]# DEF_NS_ADMIN_TOKEN=$(kubectl get secrets def-ns-admin-secret -o jsonpath={.data.token} | base64 -d)
]# kubectl config set-credentials def-ns-admin --token=$DEF_NS_ADMIN_TOKEN --kubeconfig=/root/def-ns-admin.conf
]# kubectl config view --kubeconfig=/root/def-ns-admin.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://vip.k8test.com:6443
name: kubernetes
contexts: null
current-context: ""
kind: Config
preferences: {}
users:
- name: def-ns-admin
user:
token: REDACTED
2.2.4、配置上下文
]# kubectl config set-context def-ns-admin@kubernetes --cluster=kubernetes --user=def-ns-admin --kubeconfig=/root/def-ns-admin.conf ]# kubectl config view --kubeconfig=/root/def-ns-admin.conf apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://vip.k8test.com:6443 name: kubernetes contexts: - context: cluster: kubernetes user: def-ns-admin name: def-ns-admin@kubernetes current-context: "" kind: Config preferences: {} users: - name: def-ns-admin user: token: REDACTED
2.2.5、切换用户
]# kubectl config use-context def-ns-admin@kubernetes --kubeconfig=/root/def-ns-admin.conf ]# kubectl config view --kubeconfig=/root/def-ns-admin.conf apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://vip.k8test.com:6443 name: kubernetes contexts: - context: cluster: kubernetes user: def-ns-admin name: def-ns-admin@kubernetes current-context: def-ns-admin@kubernetes kind: Config preferences: {} users: - name: def-ns-admin user: token: REDACTED
2.1.6、确认命令行下可以正常使用
]# kubectl get sa --kubeconfig=/root/def-ns-admin.conf NAME SECRETS AGE admin 0 30h def-ns-admin 0 3h31m default 0 14d
2.1.7、使用新建的kubeconfig文件-登陆Dashboard

2.1.8、登陆成功
只有default命名空间权限

3、Dashboard进阶之Octant
3.1、Octant
3.1.1、简介
我们在搭建K8S环境的时候,涉及到一个私有容器仓库Harbor,Harbor是VMware开源的一个私有容器
镜像仓库,对于k8s默认的可视化界面dashboard虽然功能很好,但是在有些场景中,它并不太美观和便捷。
VMware为此开源了一个Octant工具,它看来它更像一个Dashboard的代替品,不仅仅外观漂亮了很多,而
且功能也丰富了很多,尤其是便捷性。
3.1.2、官网地址
官方代码:https://octant.dev/ github:https://github.com/vmware-tanzu/octant 最新版本:v0.25.0 (20220224)
3.2、环境搭建
3.2.1、安装下载软件
]# rpm -ivh https://github.com/vmware-archive/octant/releases/download/v0.25.1/octant_0.25.1_Linux-64bit.rpm
3.2.2、检查是否安装成功
]# octant version Version: 0.25.1 Git commit: f16cbb951905f1f8549469dfc116ca16cf679d46 Built: 2022-02-24T23:02:15Z
3.2.3、octant help
]# octant --help octant is a dashboard for high bandwidth cluster analysis operations Usage: octant [flags] octant [command] Available Commands: completion generate the autocompletion script for the specified shell help Help about any command version Show version Flags: --context string initial context --disable-cluster-overview disable cluster overview --enable-feature-applications enable applications feature --kubeconfig string absolute path to kubeConfig file -n, --namespace string initial namespace --namespace-list strings a list of namespaces to use on start --plugin-path string plugin path -v, --verbose turn on debug logging --client-max-recv-msg-size int client max receiver message size (default 16777216) --accepted-hosts string accepted hosts list [DEV] --client-qps float32 maximum QPS for client [DEV] (default 200) --client-burst int maximum burst for client throttle [DEV] (default 400) --disable-open-browser disable automatic launching of the browser [DEV] --disable-origin-check disable cross origin resource check -c, --enable-opencensus enable open census [DEV] --klog-verbosity int klog verbosity level [DEV] --listener-addr string listener address for the octant frontend [DEV] --local-content string local content path [DEV] --proxy-frontend string url to send frontend request to [DEV] --ui-url string dashboard url [DEV] --browser-path string the browser path to open the browser on --memstats string log memory usage to this file --meminterval string interval to poll memory usage (requires --memstats), valid time units are "ns", "us" (or "µs"), "ms", "s", "m", "h". (default "100ms") -h, --help help for octant
3.2.4、octant启动
octant --kubeconfig=/etc/kubernetes/admin.conf --listener-addr=0.0.0.0:8000 --ui-url=octant.example.com \
--namespace-list default,kube-flannel,kube-node-lease,kube-public,kube-system,kubernetes-dashboard
3.2.5、配置hosts
vi /c/Windows/System32/drivers/etc/hosts 192.168.10.26 octant.example.com
3.2.6、访问查看
