签发用户证书
创建私钥
# (umask 077; openssl genrsa -out user1.key 2048)创建CSR文件
下面的脚本展示了如何生成 PKI 私钥和 CSR。 设置 CSR 的 CN 和 O 属性很重要。CN 是用户名,O 是该用户归属的组。# openssl req -new -key user1.key -out user1.csr -subj "/CN=user1/O=developers"获取CSR文件base64编码
# cat user1.csr | base64 | tr -d "\n"LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ2FqQ0NBVklDQVFBd0pURU9NQXdHQTFVRUF3d0ZkWE5sY2pFeEV6QVJCZ05WQkFvTUNtUmxkbVZzYjNCbApjbk13Z2dFaU1BMEdDU3FHU0liM0RRRUJBUVVBQTRJQkR3QXdnZ0VLQW9JQkFRQzNGZkdGRm9hWnRxVFVnQUxiCmdZSjJBNU9ncmRHczJhK0FHWTl6NzNRcU1lczg2dUg5dForcTJiSk44TXZRYXlPUk9IVnJBQ3J2STBJQkxoK3IKbENESllRVms3YytkL0JaTWhDa3M2em5RU0ZMQndzdGJNRkIySVY5OXdXNzUwUlVMcnRYREUzTk8vRzdnWmpxaQpjWFdheERJYmw1Vjk4ZS92M2NGWk9aOXc5MnRSeDZJNUJQWUEwSlFiYTQ2QkllOTBFdmYzL1VMamJSS1lXTm1OCkZudnYwOXlqR21pU2M5OEpDRGtHTXptY0NRWjd5U1lRdzdFK3JVRVdjblM5clNQaURyMGJ0eWVhQU9YVjNxNkIKdHpmbW15T2NTWjVMKzVsV1NCTllyY2Q4TTVudXp1R204UjBqV3E1UWlDRlpmN3YzVzFDeVpGR0grYk5WUDkxYQpnTUx2QWdNQkFBR2dBREFOQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBYlMrbkJlaWVFK2o1bmF6YnNyWDZYVXpzCjMvZkpCOTN0MjVxcWE4bk94bWIyeUFMQjFkb090R1pndUt1Wi8zbE1DZk9Yd1RWTGN6WjVEbjJoY05Qa0ErbmsKUjF2bzNqZ0VuVGQ3ZTdaS1FhQkg2Z092Z2xPM01oWVhiK0xSUGFDUVJwRGs2NEdCL1dFYkpQK1RodzhSZVJheApmS3dlS3BDcXc5cDkySm9LQXRHYVgzVEdqR2ZJSHduNjhvcngxTzRQc0NkSnV6NElRNHpyLytJZkY0bE8welN6CjFCQjdGakhmemVmZ1B2M25pQjRDL2U0VDZTU21WbkEwaE4rYWZYd3FKbEtYV0pmeGJaaS9EQWN4SFQ1WXU3SC8KT0RwMlI5clR2bUJudHJVOFZJcHVlZkUvOFhCbWV4b01UelpwRFBmK1hQa0h3eXhSbDhwTFkzWVZ4NnU3NXc9PQotLS0tLUVORCBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0Kuser1-csr.yaml
apiVersion: certificates.k8s.io/v1
kind: CertificateSigningRequest
metadata:
name: user1
namespace: demoapp
spec:
request: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ2FqQ0NBVklDQVFBd0pURU9NQXdHQTFVRUF3d0ZkWE5sY2pFeEV6QVJCZ05WQkFvTUNtUmxkbVZzYjNCbApjbk13Z2dFaU1BMEdDU3FHU0liM0RRRUJBUVVBQTRJQkR3QXdnZ0VLQW9JQkFRQzNGZkdGRm9hWnRxVFVnQUxiCmdZSjJBNU9ncmRHczJhK0FHWTl6NzNRcU1lczg2dUg5dForcTJiSk44TXZRYXlPUk9IVnJBQ3J2STBJQkxoK3IKbENESllRVms3YytkL0JaTWhDa3M2em5RU0ZMQndzdGJNRkIySVY5OXdXNzUwUlVMcnRYREUzTk8vRzdnWmpxaQpjWFdheERJYmw1Vjk4ZS92M2NGWk9aOXc5MnRSeDZJNUJQWUEwSlFiYTQ2QkllOTBFdmYzL1VMamJSS1lXTm1OCkZudnYwOXlqR21pU2M5OEpDRGtHTXptY0NRWjd5U1lRdzdFK3JVRVdjblM5clNQaURyMGJ0eWVhQU9YVjNxNkIKdHpmbW15T2NTWjVMKzVsV1NCTllyY2Q4TTVudXp1R204UjBqV3E1UWlDRlpmN3YzVzFDeVpGR0grYk5WUDkxYQpnTUx2QWdNQkFBR2dBREFOQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBYlMrbkJlaWVFK2o1bmF6YnNyWDZYVXpzCjMvZkpCOTN0MjVxcWE4bk94bWIyeUFMQjFkb090R1pndUt1Wi8zbE1DZk9Yd1RWTGN6WjVEbjJoY05Qa0ErbmsKUjF2bzNqZ0VuVGQ3ZTdaS1FhQkg2Z092Z2xPM01oWVhiK0xSUGFDUVJwRGs2NEdCL1dFYkpQK1RodzhSZVJheApmS3dlS3BDcXc5cDkySm9LQXRHYVgzVEdqR2ZJSHduNjhvcngxTzRQc0NkSnV6NElRNHpyLytJZkY0bE8welN6CjFCQjdGakhmemVmZ1B2M25pQjRDL2U0VDZTU21WbkEwaE4rYWZYd3FKbEtYV0pmeGJaaS9EQWN4SFQ1WXU3SC8KT0RwMlI5clR2bUJudHJVOFZJcHVlZkUvOFhCbWV4b01UelpwRFBmK1hQa0h3eXhSbDhwTFkzWVZ4NnU3NXc9PQotLS0tLUVORCBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0K
signerName: kubernetes.io/kube-apiserver-client
expirationSeconds: 8640000 # 100天
usages:
- client auth创建csr资源
# kubectl apply -f user1-csr.yamlcertificatesigningrequest.certificates.k8s.io/user1 created查看CSR
# kubectl get csr -n demoappNAME AGE SIGNERNAME REQUESTOR REQUESTEDDURATION CONDITION
user1 63s kubernetes.io/kube-apiserver-client admin 100d Pending批准 CSR
# kubectl certificate approve user1 -n demoappcertificatesigningrequest.certificates.k8s.io/user1 approved查看CSR状态
# kubectl get csr -n demoappNAME AGE SIGNERNAME REQUESTOR REQUESTEDDURATION CONDITION
user1 2m9s kubernetes.io/kube-apiserver-client admin 100d Approved,Issued获取证书
# kubectl get csr user1 -o jsonpath='{.status.certificate}'| base64 -d > user1.crt验证证书
# openssl x509 -in user1.crt -text -nooutCertificate:
Data:
Version: 3 (0x2)
Serial Number:
af:3b:4a:8c:e1:69:51:12:64:15:69:7a:a9:bd:b0:8d
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CN, ST = HangZhou, L = XS, O = k8s, OU = System, CN = kubernetes
Validity
Not Before: Aug 4 07:05:54 2023 GMT
Not After : Nov 12 07:05:54 2023 GMT
Subject: O = developers, CN = user1
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:b7:15:f1:85:16:86:99:b6:a4:d4:80:02:db:81:
82:76:03:93:a0:ad:d1:ac:d9:af:80:19:8f:73:ef:
74:2a:31:eb:3c:ea:e1:fd:b5:9f:aa:d9:b2:4d:f0:
cb:d0:6b:23:91:38:75:6b:00:2a:ef:23:42:01:2e:
1f:ab:94:20:c9:61:05:64:ed:cf:9d:fc:16:4c:84:
29:2c:eb:39:d0:48:52:c1:c2:cb:5b:30:50:76:21:
5f:7d:c1:6e:f9:d1:15:0b:ae:d5:c3:13:73:4e:fc:
6e:e0:66:3a:a2:71:75:9a:c4:32:1b:97:95:7d:f1:
ef:ef:dd:c1:59:39:9f:70:f7:6b:51:c7:a2:39:04:
f6:00:d0:94:1b:6b:8e:81:21:ef:74:12:f7:f7:fd:
42:e3:6d:12:98:58:d9:8d:16:7b:ef:d3:dc:a3:1a:
68:92:73:df:09:08:39:06:33:39:9c:09:06:7b:c9:
26:10:c3:b1:3e:ad:41:16:72:74:bd:ad:23:e2:0e:
bd:1b:b7:27:9a:00:e5:d5:de:ae:81:b7:37:e6:9b:
23:9c:49:9e:4b:fb:99:56:48:13:58:ad:c7:7c:33:
99:ee:ce:e1:a6:f1:1d:23:5a:ae:50:88:21:59:7f:
bb:f7:5b:50:b2:64:51:87:f9:b3:55:3f:dd:5a:80:
c2:ef
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Extended Key Usage:
TLS Web Client Authentication
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 Authority Key Identifier:
90:4F:95:52:FF:B2:B1:F7:04:60:1B:D8:21:EA:8F:F6:E6:39:CD:2B
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
36:53:c9:fa:ad:06:0a:65:fd:c8:17:6a:f9:f3:ca:c5:a5:7e:
d9:e1:5c:8d:60:5d:e9:47:ce:f7:fd:68:2f:66:10:79:74:68:
5f:e6:07:52:01:71:49:d8:5c:28:f7:e2:0c:1b:32:f3:f9:fa:
d4:8a:e0:95:cd:f6:7d:4d:9b:a1:f3:da:fd:76:51:f5:15:25:
2d:68:bd:3c:c2:fc:67:03:c6:db:b5:13:3b:6b:a2:56:7b:c8:
85:eb:da:37:99:a3:10:5f:7e:10:7d:74:e7:6a:b9:c0:ca:fa:
49:8a:d6:24:c9:1f:21:2d:f7:f9:c3:ca:9d:e5:0e:d7:08:bf:
d8:83:08:b8:b9:fd:97:cc:47:13:e2:ab:27:94:2d:2b:a5:61:
bf:7c:cd:de:eb:80:e0:a3:9e:90:4e:c1:67:ee:41:c7:a9:b6:
64:19:97:b2:c5:c7:71:fb:aa:b6:75:ba:a6:22:16:76:9b:74:
64:1b:e0:a4:cb:bd:9e:c8:f7:44:c1:e0:28:90:79:64:d1:21:
8c:d6:51:4a:9f:ad:49:d6:5b:4c:e5:ad:71:cf:6b:83:1e:ad:
d4:93:35:d2:2e:67:e4:c8:d2:38:81:9f:01:2a:bb:c3:62:01:
c4:1f:8c:78:bc:63:e5:4f:4d:f9:2d:2e:33:b2:7c:d5:89:00:
cc:6d:63:85创建用户
demoapp-ns.yaml
apiVersion: v1
kind: Namespace
metadata:
name: demoappserviceaccount-user1.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: user1
namespace: demoapp创建user1资源
# kubectl apply -f demoapp-ns.yaml -f serviceaccount-user1.yamlnamespace/demoapp created
serviceaccount/user1 created查看user1资源
# kubectl get serviceaccount -n demoappNAME SECRETS AGE
default 0 54s
user1 0 54s创建role
user1-role.yaml
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: demoapp
name: user1-role
rules:
- apiGroups: ["*"] # "" 表示核心群组
resources: ["pods", "services", "pods/log"]
verbs: ["get", "watch", "list"]创建role资源
# kubectl apply -f user1-role.yamlrole.rbac.authorization.k8s.io/user1-role created查看role资源
# kubectl get role -n demoappNAME CREATED AT
user1-role 2023-08-04T07:34:14Z查看role规则
# kubectl describe role user1-role -n demoappName: user1-role
Labels: <none>
Annotations: <none>
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
pods.*/log [] [] [get watch list]
pods.* [] [] [get watch list]
services.* [] [] [get watch list]角色绑定
role-bind-user1.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: role-bing-user1
namespace: demoapp
subjects:
- kind: ServiceAccount
name: user1
namespace: demoapp
roleRef:
kind: Role
name: user1-role
apiGroup: rbac.authorization.k8s.io创建rolebinging资源
# kubectl apply -f role-bind-user1.yamlrolebinding.rbac.authorization.k8s.io/role-bing-user1 created查看RoleBinding资源
# kubectl get rolebinding -n demoappNAME ROLE AGE
role-bing-user1 Role/user1-role 82s查看RoleBinding规则
# kubectl describe rolebinding/role-bing-user1 -n demoappName: role-bing-user1
Labels: <none>
Annotations: <none>
Role:
Kind: Role
Name: user1-role
Subjects:
Kind Name Namespace
---- ---- ---------
ServiceAccount user1 为user1手动创建长期 API 令牌
user1-secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: user1-secret
namespace: demoapp
annotations:
kubernetes.io/service-account.name: user1
type: kubernetes.io/service-account-token创建secret资源
# kubectl apply -f user1-secret.yamlsecret/user1-secret created查看token
# kubectl get secret user1-secret -n demoapp -o jsonpath={".data.token"} | base64 -deyJhbGciOiJSUzI1NiIsImtpZCI6IklkYWRmQU53aV8yYlU4amdheGY0aXhseVNDMDhOZFg3SElVdjNFbHowaFEifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZW1vYXBwIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6InVzZXIxLXNlY3JldCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJ1c2VyMSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjY2ZDgwMjQxLTM0MzEtNDIzNS1hNjE4LTRhYjM4MWNkZjE2NCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZW1vYXBwOnVzZXIxIn0.e_afkGL9vVAcsHnMF4SzN00iqHCMy6iHJkwRmthz9q6YC0zCGs6ltmvhmy5GqS7yTSIYy_RROVT12PTaq2WqIgoZV-ZT14oDQbc9gs9l9ssssyRtXyj9lglb4SADBxYv5cxBIFW-BodpsnG8J8j-QqbmCUViXe5EJky5pi4xVmS7ezzRmdcYUfjE0Xzq6c3gib4nU9KutvgqOG8zve35cRQ4Ca6jedFj23Yb9n7q_x8Ozpt9JfU9XopinjqS8M4uSHYy7BmTY9UgZnEA6xUOmG-TIAJZyEeBLaGHiBS7Lo2aA0uU_zj224efU7QoliyL8nBBLYynvLEtRRnV1g5QTg创建kubeconfig
添加集群信息
# kubectl config set-cluster developer --embed-certs=true --certificate-authority=/etc/kubernetes/ssl/ca.pem --server="https://127.0.0.1:6443" --kubeconfig=$HOME/.kube/kube-user1.configCluster "developer" set.添加用户信息
# kubectl config set-credentials user1 --embed-certs=true --client-certificate=user1.crt --client-key=user1.key --token=eyJhbGciOiJSUzI1NiIsImtpZCI6IklkYWRmQU53aV8yYlU4amdheGY0aXhseVNDMDhOZFg3SElVdjNFbHowaFEifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZW1vYXBwIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6InVzZXIxLXNlY3JldCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJ1c2VyMSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjY2ZDgwMjQxLTM0MzEtNDIzNS1hNjE4LTRhYjM4MWNkZjE2NCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZW1vYXBwOnVzZXIxIn0.e_afkGL9vVAcsHnMF4SzN00iqHCMy6iHJkwRmthz9q6YC0zCGs6ltmvhmy5GqS7yTSIYy_RROVT12PTaq2WqIgoZV-ZT14oDQbc9gs9l9ssssyRtXyj9lglb4SADBxYv5cxBIFW-BodpsnG8J8j-QqbmCUViXe5EJky5pi4xVmS7ezzRmdcYUfjE0Xzq6c3gib4nU9KutvgqOG8zve35cRQ4Ca6jedFj23Yb9n7q_x8Ozpt9JfU9XopinjqS8M4uSHYy7BmTY9UgZnEA6xUOmG-TIAJZyEeBLaGHiBS7Lo2aA0uU_zj224efU7QoliyL8nBBLYynvLEtRRnV1g5QTg --kubeconfig=$HOME/.kube/kube-user1.configUser "user1" set.添加上下文信息
# kubectl config set-context user1 --cluster=developer --namespace=demoapp --user=user1 --kubeconfig=$HOME/.kube/kube-user1.configContext "user1" created.查看当前上下文
# kubectl config get-contexts --kubeconfig=$HOME/.kube/kube-user1.configCURRENT NAME CLUSTER AUTHINFO NAMESPACE
user1 developer user1 demoapp切换当前上下文
# kubectl config use-context user1 --kubeconfig=$HOME/.kube/kube-user1.configSwitched to context "user1".查看kubeconfig文件
# kubectl config view --kubeconfig=$HOME/.kube/kube-user1.configapiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://127.0.0.1:6443
name: developer
contexts:
- context:
cluster: developer
namespace: demoapp
user: user1
name: user1
current-context: user1
kind: Config
preferences: {}
users:
- name: user1
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
token: REDACTED登录dashboard
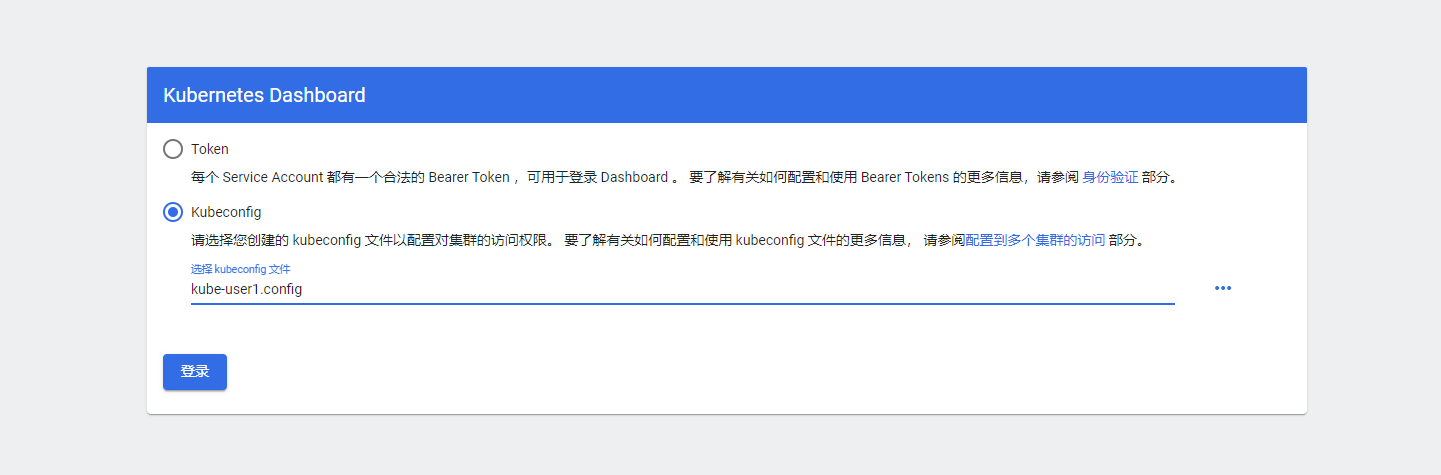

验证权限
验证deployments权限

添加deployment权限
user1-role.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: demoapp
name: user1-role
rules:
- apiGroups: ["*"] # "" 表示核心群组
resources: ["pods", "services", "pods/log","deployments"] # deployments
verbs: ["get", "watch", "list"]更新权限
# kubectl apply -f user1-role.yamlrole.rbac.authorization.k8s.io/user1-role configured再次验证deployments权限
