VRRP+防火墙双机热备实现企业内网访问互联网
实现的目的:
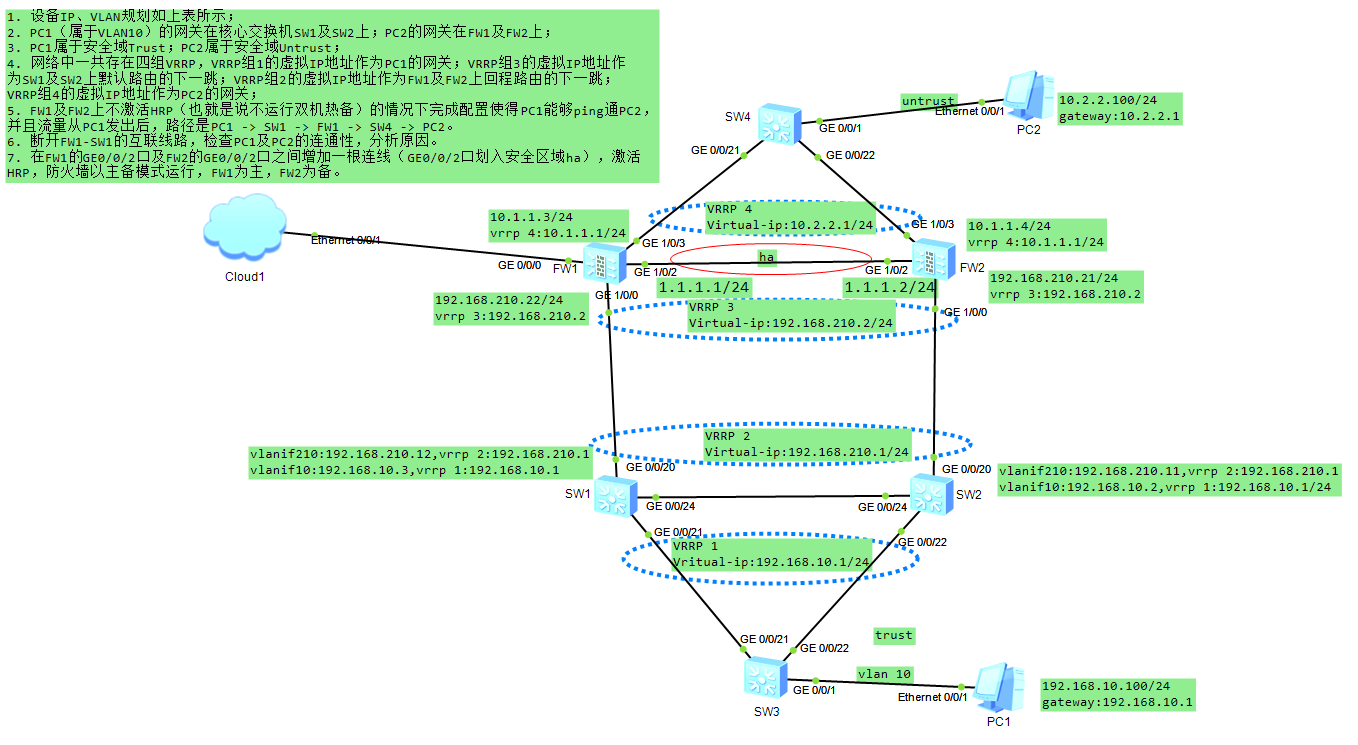
1.配置完成后,SW1、SW2、SW3开启mstp,SW1为根桥、SW2为备根桥,SW3的g0/0/22端口阻塞,且FW1为主防火墙,FW2为热备防火墙,内网用户通过 SW3-->SW1-->FW1-->互联网;
2.防火墙之间使用Ge1/0/2端口互联,此线路为ha线路,作用是防火墙之间的vrrp心跳线。(在路由器或者交换机开启VRRP时,不需要心跳线)
3.当SW1和SW2、SW3之间任何一条线路断掉,都不会影响业务;
4.当FW1和SW1之间的线路断开后,主防火墙变为FW2,vrrp3和vrrp4的虚拟IP切换到FW2。此时,内网用户通过 SW3-->SW1-->FW2-->互联网
注意:
1.心跳线可以使用多条线路做成链路聚合,本实验仅用一条。
2.SW1、SW2、SW3开启mstp,SW1为根桥、SW2为备根桥,此时SW3的g0/0/22端口阻塞。
3.如果防火墙连接的是运行商的路由器,那就需要配置默认路由 ip route-static 0.0.0.0 0 运行商IP。 本实验连接的是交换机,且PC2的网关在防火墙上,所以不用配置。
此实验中SW4为傻瓜交换机。
各设备相关配置
FW1
HRP_M[FW1]display current-configuration 2023-11-02 03:20:37.370 !Software Version V500R005C10SPC300 # sysname FW1 # l2tp domain suffix-separator @ # ipsec sha2 compatible enable # undo telnet server enable undo telnet ipv6 server enable # hrp enable hrp interface GigabitEthernet1/0/2 remote 1.1.1.2 # update schedule location-sdb weekly Sun 01:18 # firewall defend action discard # banner enable # user-manage web-authentication security port 8887 undo privacy-statement english undo privacy-statement chinese page-setting user-manage security version tlsv1.1 tlsv1.2 password-policy level high user-manage single-sign-on ad user-manage single-sign-on tsm user-manage single-sign-on radius user-manage auto-sync online-user # web-manager security version tlsv1.1 tlsv1.2 web-manager enable web-manager security enable # firewall dataplane to manageplane application-apperceive default-action drop # undo ips log merge enable # decoding uri-cache disable # update schedule ips-sdb daily 22:20 update schedule av-sdb daily 22:20 update schedule sa-sdb daily 22:20 update schedule cnc daily 22:20 update schedule file-reputation daily 22:20 # ip vpn-instance default ipv4-family # time-range worktime period-range 08:00:00 to 18:00:00 working-day # ike proposal default encryption-algorithm aes-256 aes-192 aes-128 dh group14 authentication-algorithm sha2-512 sha2-384 sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # aaa authentication-scheme default authentication-scheme admin_local authentication-scheme admin_radius_local authentication-scheme admin_hwtacacs_local authentication-scheme admin_ad_local authentication-scheme admin_ldap_local authentication-scheme admin_radius authentication-scheme admin_hwtacacs authentication-scheme admin_ad authorization-scheme default accounting-scheme default domain default service-type internetaccess ssl-vpn l2tp ike internet-access mode password reference user current-domain manager-user audit-admin password cipher @%@%_+v<>R`ju>#E#pV.\lV:iKJUzD9;OTjWtI#X3<;lOt8ZKJXi@%@% service-type web terminal level 15 manager-user api-admin password cipher @%@%LFWV>4=Ov<o|),I^*Km=~mFo\2Td4**U^R>u3C;GRJ1AmFr~@%@% level 15 manager-user admin password cipher @%@%S"/QP!F#F(PF+T(2idGI)U\b;a>HLA-=a<-ufMU%/[pIU\e)@%@% service-type web terminal level 15 role system-admin role device-admin role device-admin(monitor) role audit-admin bind manager-user audit-admin role audit-admin bind manager-user admin role system-admin # l2tp-group default-lns # interface GigabitEthernet0/0/0 undo shutdown ip binding vpn-instance default ip address 192.168.137.10 255.255.255.0 alias GE0/METH service-manage http permit service-manage https permit service-manage ping permit service-manage ssh permit service-manage snmp permit service-manage telnet permit # interface GigabitEthernet1/0/0 undo shutdown ip address 192.168.210.22 255.255.255.0 vrrp vrid 3 virtual-ip 192.168.210.2 active service-manage ping permit # interface GigabitEthernet1/0/1 undo shutdown # interface GigabitEthernet1/0/2 undo shutdown ip address 1.1.1.1 255.255.255.0 service-manage ping permit # interface GigabitEthernet1/0/3 undo shutdown ip address 10.1.1.3 255.255.255.0 vrrp vrid 4 virtual-ip 10.2.2.1 255.255.255.0 active service-manage ping permit # interface GigabitEthernet1/0/4 undo shutdown # interface GigabitEthernet1/0/5 undo shutdown # interface GigabitEthernet1/0/6 undo shutdown # interface Virtual-if0 # interface NULL0 # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet1/0/0 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/3 # firewall zone dmz set priority 50 # firewall zone name ha id 4 set priority 99 add interface GigabitEthernet1/0/2 # ip route-static 192.168.10.0 255.255.255.0 192.168.210.1 # undo ssh server compatible-ssh1x enable ssh authentication-type default password ssh server cipher aes256_ctr aes128_ctr ssh server hmac sha2_256 sha1 ssh client cipher aes256_ctr aes128_ctr ssh client hmac sha2_256 sha1 # firewall detect ftp # user-interface con 0 authentication-mode aaa user-interface vty 0 4 authentication-mode aaa protocol inbound ssh user-interface vty 16 20 # pki realm default # sa # location # multi-linkif mode proportion-of-weight # right-manager server-group # device-classification device-group pc device-group mobile-terminal device-group undefined-group # user-manage server-sync tsm # security-policy rule name LtoU source-zone local destination-zone trust action permit rule name TtoU source-zone trust destination-zone untrust action permit rule name UtoT source-zone untrust destination-zone trust action permit # auth-policy # traffic-policy # policy-based-route # nat-policy # quota-policy # pcp-policy # dns-transparent-policy # rightm-policy # return
FW2
HRP_S[USG6000V1]display current-configuration 2023-11-02 03:21:27.680 !Software Version V500R005C10SPC300 # sysname USG6000V1 # l2tp domain suffix-separator @ # ipsec sha2 compatible enable # undo telnet server enable undo telnet ipv6 server enable # hrp enable hrp interface GigabitEthernet1/0/2 remote 1.1.1.1 # update schedule location-sdb weekly Sun 05:00 # firewall defend action discard # banner enable # user-manage web-authentication security port 8887 undo privacy-statement english undo privacy-statement chinese page-setting user-manage security version tlsv1.1 tlsv1.2 password-policy level high user-manage single-sign-on ad user-manage single-sign-on tsm user-manage single-sign-on radius user-manage auto-sync online-user # web-manager security version tlsv1.1 tlsv1.2 web-manager enable web-manager security enable # firewall dataplane to manageplane application-apperceive default-action drop # undo ips log merge enable # decoding uri-cache disable # update schedule ips-sdb daily 06:28 update schedule av-sdb daily 06:28 update schedule sa-sdb daily 06:28 update schedule cnc daily 06:28 update schedule file-reputation daily 06:28 # ip vpn-instance default ipv4-family # time-range worktime period-range 08:00:00 to 18:00:00 working-day # ike proposal default encryption-algorithm aes-256 aes-192 aes-128 dh group14 authentication-algorithm sha2-512 sha2-384 sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # aaa authentication-scheme default authentication-scheme admin_local authentication-scheme admin_radius_local authentication-scheme admin_hwtacacs_local authentication-scheme admin_ad_local authentication-scheme admin_ldap_local authentication-scheme admin_radius authentication-scheme admin_hwtacacs authentication-scheme admin_ad authorization-scheme default accounting-scheme default domain default service-type internetaccess ssl-vpn l2tp ike internet-access mode password reference user current-domain manager-user audit-admin password cipher @%@%J(m/~\8jHI;m942F`QO6jKid%U`@E[gP|F4$_O~<&V@PKigj@%@% service-type web terminal level 15 manager-user api-admin password cipher @%@%\W;16h]`:45cE-Pp*I33x+0=ZTfmG}N1=;U>b+BS6~YT+0@x@%@% level 15 manager-user admin password cipher @%@%3]7zF]g%;!xWy>=i|h--HJMQ4#|tCd}fs3`igwLyLK,"JMTH@%@% service-type web terminal level 15 role system-admin role device-admin role device-admin(monitor) role audit-admin bind manager-user audit-admin role audit-admin bind manager-user admin role system-admin # l2tp-group default-lns # interface GigabitEthernet0/0/0 undo shutdown ip binding vpn-instance default ip address 192.168.0.1 255.255.255.0 alias GE0/METH service-manage http permit service-manage https permit service-manage ping permit service-manage ssh permit service-manage snmp permit service-manage telnet permit # interface GigabitEthernet1/0/0 undo shutdown ip address 192.168.210.21 255.255.255.0 vrrp vrid 3 virtual-ip 192.168.210.2 standby service-manage ping permit # interface GigabitEthernet1/0/1 undo shutdown # interface GigabitEthernet1/0/2 undo shutdown ip address 1.1.1.2 255.255.255.0 service-manage ping permit # interface GigabitEthernet1/0/3 undo shutdown ip address 10.1.1.4 255.255.255.0 vrrp vrid 4 virtual-ip 10.2.2.1 255.255.255.0 standby service-manage ping permit # interface GigabitEthernet1/0/4 undo shutdown # interface GigabitEthernet1/0/5 undo shutdown # interface GigabitEthernet1/0/6 undo shutdown # interface Virtual-if0 # interface NULL0 # firewall zone local set priority 100 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/0 add interface GigabitEthernet1/0/0 # firewall zone untrust set priority 5 add interface GigabitEthernet1/0/3 # firewall zone dmz set priority 50 # firewall zone name ha id 4 set priority 99 add interface GigabitEthernet1/0/2 # ip route-static 192.168.10.0 255.255.255.0 192.168.210.1 # undo ssh server compatible-ssh1x enable ssh authentication-type default password ssh server cipher aes256_ctr aes128_ctr ssh server hmac sha2_256 sha1 ssh client cipher aes256_ctr aes128_ctr ssh client hmac sha2_256 sha1 # firewall detect ftp # user-interface con 0 authentication-mode aaa user-interface vty 0 4 authentication-mode aaa protocol inbound ssh user-interface vty 16 20 # pki realm default # sa # location # multi-linkif mode proportion-of-weight # right-manager server-group # device-classification device-group pc device-group mobile-terminal device-group undefined-group # user-manage server-sync tsm # security-policy rule name TtoU source-zone trust destination-zone untrust action permit rule name UtoT source-zone untrust destination-zone trust action permit # auth-policy # traffic-policy # policy-based-route # nat-policy # quota-policy # pcp-policy # dns-transparent-policy # rightm-policy # return
SW1
[SW1]display current-configuration # sysname SW1 # vlan batch 10 210 # stp instance 0 root primary # cluster enable ntdp enable ndp enable # drop illegal-mac alarm # diffserv domain default # drop-profile default # aaa authentication-scheme default authorization-scheme default accounting-scheme default domain default domain default_admin local-user admin password simple admin local-user admin service-type http # interface Vlanif1 # interface Vlanif10 ip address 192.168.10.3 255.255.255.0 vrrp vrid 1 virtual-ip 192.168.10.1 vrrp vrid 1 priority 120 # interface Vlanif210 ip address 192.168.210.12 255.255.255.0 vrrp vrid 2 virtual-ip 192.168.210.1 vrrp vrid 2 priority 120 # interface MEth0/0/1 # interface GigabitEthernet0/0/1 # interface GigabitEthernet0/0/2 # interface GigabitEthernet0/0/3 # interface GigabitEthernet0/0/4 # interface GigabitEthernet0/0/5 # interface GigabitEthernet0/0/6 # interface GigabitEthernet0/0/7 # interface GigabitEthernet0/0/8 # interface GigabitEthernet0/0/9 # interface GigabitEthernet0/0/10 # interface GigabitEthernet0/0/11 # interface GigabitEthernet0/0/12 # interface GigabitEthernet0/0/13 # interface GigabitEthernet0/0/14 # interface GigabitEthernet0/0/15 # interface GigabitEthernet0/0/16 # interface GigabitEthernet0/0/17 # interface GigabitEthernet0/0/18 # interface GigabitEthernet0/0/19 # interface GigabitEthernet0/0/20 port link-type access port default vlan 210 # interface GigabitEthernet0/0/21 port link-type trunk port trunk allow-pass vlan 2 to 4094 # interface GigabitEthernet0/0/22 # interface GigabitEthernet0/0/23 # interface GigabitEthernet0/0/24 port link-type trunk port trunk allow-pass vlan 2 to 4094 # interface NULL0 # ip route-static 0.0.0.0 0.0.0.0 192.168.210.2 # user-interface con 0 user-interface vty 0 4 # port-group link-type # return
SW2
[SW2]display current-configuration # sysname SW2 # vlan batch 10 210 # stp instance 0 root secondary # cluster enable ntdp enable ndp enable # drop illegal-mac alarm # diffserv domain default # drop-profile default # aaa authentication-scheme default authorization-scheme default accounting-scheme default domain default domain default_admin local-user admin password simple admin local-user admin service-type http # interface Vlanif1 # interface Vlanif10 ip address 192.168.10.2 255.255.255.0 vrrp vrid 1 virtual-ip 192.168.10.1 # interface Vlanif210 ip address 192.168.210.11 255.255.255.0 vrrp vrid 2 virtual-ip 192.168.210.1 # interface MEth0/0/1 # interface GigabitEthernet0/0/1 # interface GigabitEthernet0/0/2 # interface GigabitEthernet0/0/3 # interface GigabitEthernet0/0/4 # interface GigabitEthernet0/0/5 # interface GigabitEthernet0/0/6 # interface GigabitEthernet0/0/7 # interface GigabitEthernet0/0/8 # interface GigabitEthernet0/0/9 # interface GigabitEthernet0/0/10 # interface GigabitEthernet0/0/11 # interface GigabitEthernet0/0/12 # interface GigabitEthernet0/0/13 # interface GigabitEthernet0/0/14 # interface GigabitEthernet0/0/15 # interface GigabitEthernet0/0/16 # interface GigabitEthernet0/0/17 # interface GigabitEthernet0/0/18 # interface GigabitEthernet0/0/19 # interface GigabitEthernet0/0/20 port link-type access port default vlan 210 # interface GigabitEthernet0/0/21 # interface GigabitEthernet0/0/22 port link-type trunk port trunk allow-pass vlan 2 to 4094 # interface GigabitEthernet0/0/23 # interface GigabitEthernet0/0/24 port link-type trunk port trunk allow-pass vlan 2 to 4094 # interface NULL0 # ip route-static 0.0.0.0 0.0.0.0 192.168.210.2 # user-interface con 0 user-interface vty 0 4 # return
SW3
[Huawei]display stp brief MSTID Port Role STP State Protection 0 GigabitEthernet0/0/1 DESI FORWARDING NONE 0 GigabitEthernet0/0/21 ROOT FORWARDING NONE 0 GigabitEthernet0/0/22 ALTE DISCARDING NONE [Huawei]display current-configuration # sysname Huawei # vlan batch 10 # cluster enable ntdp enable ndp enable # drop illegal-mac alarm # diffserv domain default # drop-profile default # aaa authentication-scheme default authorization-scheme default accounting-scheme default domain default domain default_admin local-user admin password simple admin local-user admin service-type http # interface Vlanif1 # interface MEth0/0/1 # interface GigabitEthernet0/0/1 port link-type access port default vlan 10 # interface GigabitEthernet0/0/2 # interface GigabitEthernet0/0/3 # interface GigabitEthernet0/0/4 # interface GigabitEthernet0/0/5 # interface GigabitEthernet0/0/6 # interface GigabitEthernet0/0/7 # interface GigabitEthernet0/0/8 # interface GigabitEthernet0/0/9 # interface GigabitEthernet0/0/10 # interface GigabitEthernet0/0/11 # interface GigabitEthernet0/0/12 # interface GigabitEthernet0/0/13 # interface GigabitEthernet0/0/14 # interface GigabitEthernet0/0/15 # interface GigabitEthernet0/0/16 # interface GigabitEthernet0/0/17 # interface GigabitEthernet0/0/18 # interface GigabitEthernet0/0/19 # interface GigabitEthernet0/0/20 # interface GigabitEthernet0/0/21 port link-type trunk port trunk allow-pass vlan 2 to 4094 # interface GigabitEthernet0/0/22 port link-type trunk port trunk allow-pass vlan 2 to 4094 # interface GigabitEthernet0/0/23 # interface GigabitEthernet0/0/24 # interface NULL0 # user-interface con 0 user-interface vty 0 4 # return