DHCP中继
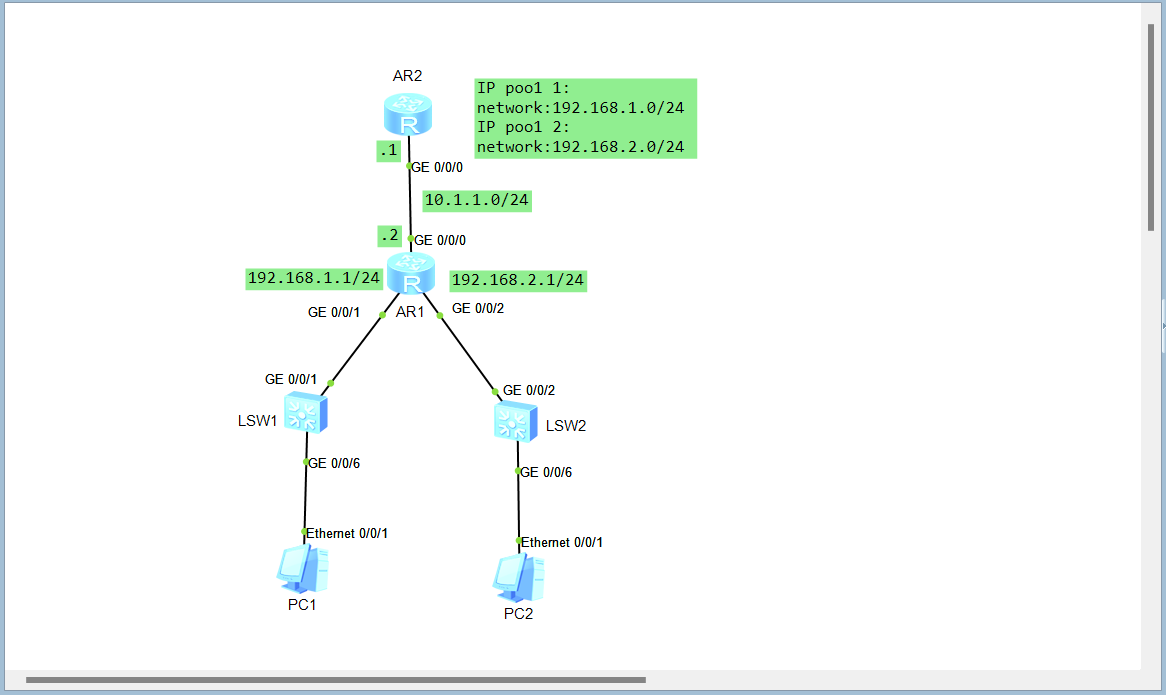
拓扑
使得PC1,PC2通过AR2获取地址
配置
AR2
#
dhcp enable
#
ip pool 1
network 192.168.1.0 mask 255.255.255.0
#
ip pool 2
network 192.168.2.0 mask 255.255.255.0
#
interface GigabitEthernet0/0/0
ip address 10.1.1.1 255.255.255.0
dhcp select global
#
ip route-static 192.168.1.0 255.255.255.0 10.1.1.2
ip route-static 192.168.2.0 255.255.255.0 10.1.1.2
AR1
#
dhcp enable
#
interface GigabitEthernet0/0/0
ip address 10.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 192.168.1.1 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.1.1
#
interface GigabitEthernet0/0/2
ip address 192.168.2.1 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.1.1
抓包验证
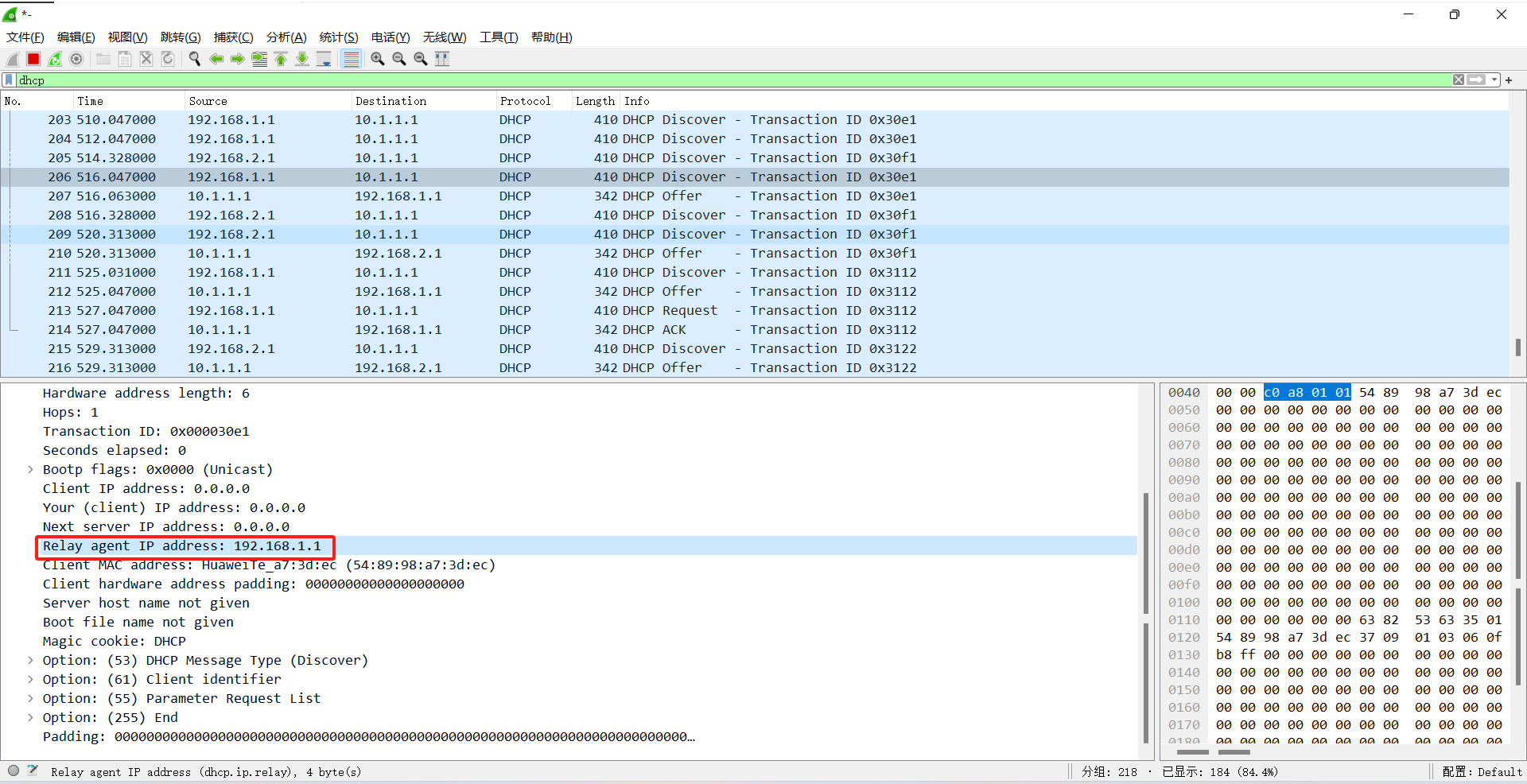
PC1,PC2开启自动获取地址,在AR1的GE0/0/0接口抓包

AR2通过中继过来的DISCOVERY报文中的中继代理地址来判断分配哪个地址池的地址给客户端
查看PC1和PC2 IP地址
PC1
PC>ipconfig
Link local IPv6 address...........: fe80::5689:98ff:fea7:3dec
IPv6 address......................: :: / 128
IPv6 gateway......................: ::
IPv4 address......................: 192.168.1.254
Subnet mask.......................: 255.255.255.0
Gateway...........................: 0.0.0.0
Physical address..................: 54-89-98-A7-3D-EC
DNS server........................:
PC2
PC>ipconfig
Link local IPv6 address...........: fe80::5689:98ff:fe5a:413e
IPv6 address......................: :: / 128
IPv6 gateway......................: ::
IPv4 address......................: 192.168.2.254
Subnet mask.......................: 255.255.255.0
Gateway...........................: 0.0.0.0
Physical address..................: 54-89-98-5A-41-3E
DNS server........................:
DHCP 攻击和防御模拟
DHCP 恶意服务器模拟
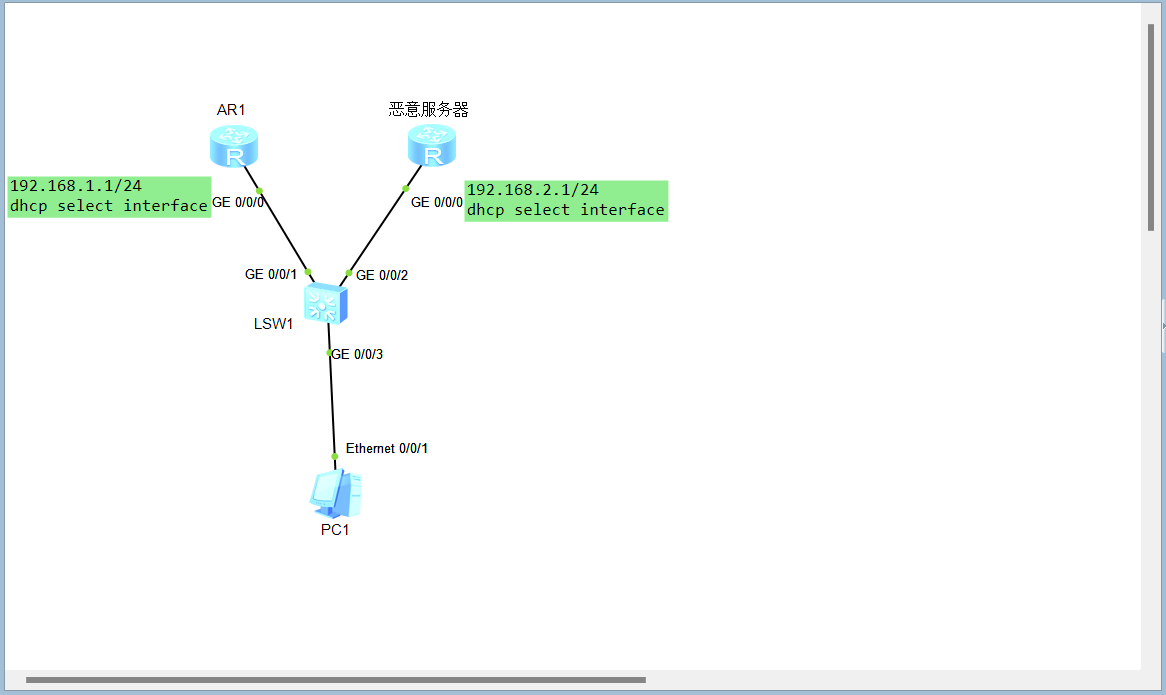
拓扑
配置
AR2
#
dhcp enable
#
interface GigabitEthernet0/0/0
ip address 192.168.2.1 255.255.255.0
dhcp select interface
AR1
#
dhcp enable
#
interface GigabitEthernet0/0/0
ip address 192.168.1.1 255.255.255.0
dhcp select interface
模拟攻击
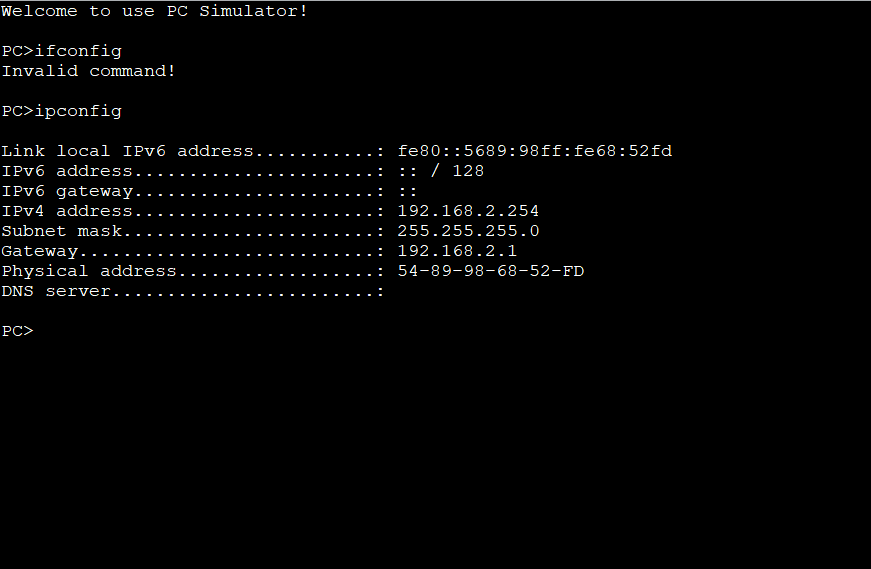
PC1开启自动获取地址,有百分之50的概率获取到恶意服务器的地址
DHCP Snooping 修复
LSW1配置DHCP Snooping,将非法服务器的接口设置为不信任端口,正常服务器设置为信任端口
[LSW1]dhcp enable
[LSW1]dhcp snooping enable
[LSW1]port-group group-member gi 0/0/1 to gi 0/0/3
[LSW1-port-group]dhcp snooping enable
[LSW1-port-group]q
[LSW1]inte gi 0/0/1
[LSW1-GigabitEthernet0/0/1]dhcp snooping trusted
PC1重新获取地址
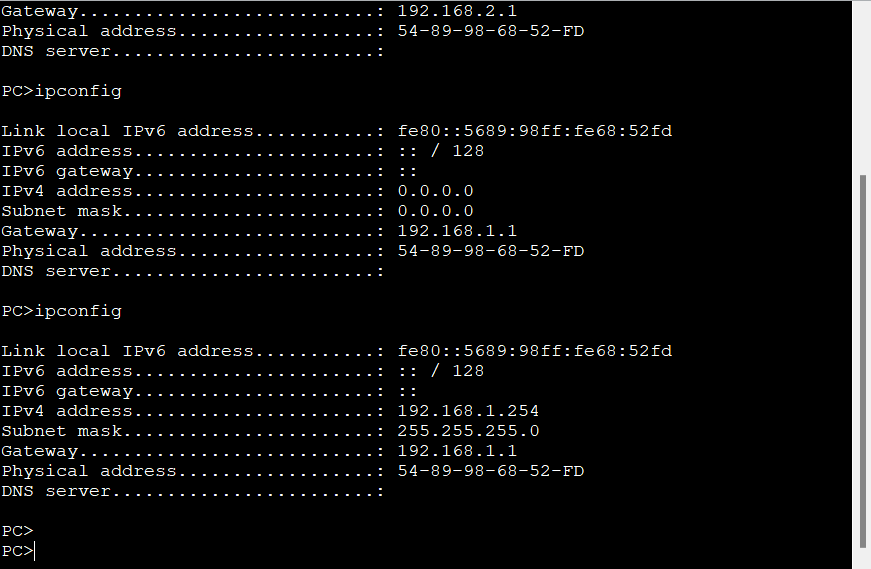
在恶意服务器的GE0/0/0接口抓包,没有收到来自PC的DISCOVERY
饿死攻击
拓扑
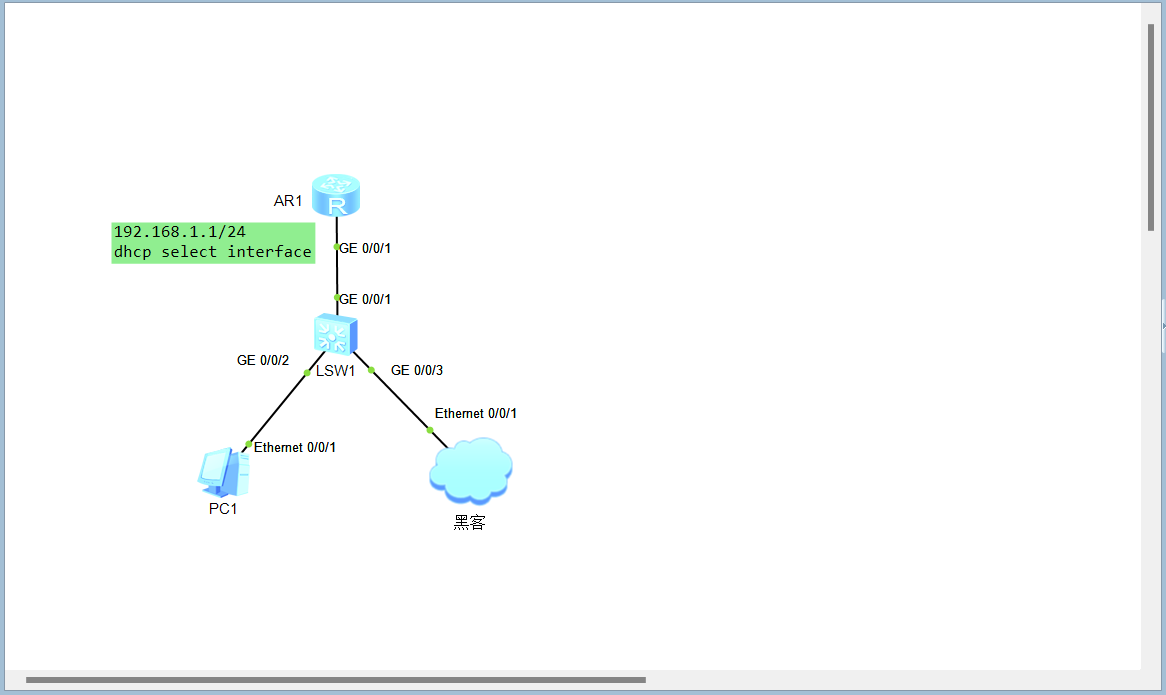
配置
AR1
#
dhcp enable
#
interface GigabitEthernet0/0/1
---- More ----
ip address 192.168.1.1 255.255.255.0
dhcp select interface
攻击模拟
使用kali的yersinia工具模拟
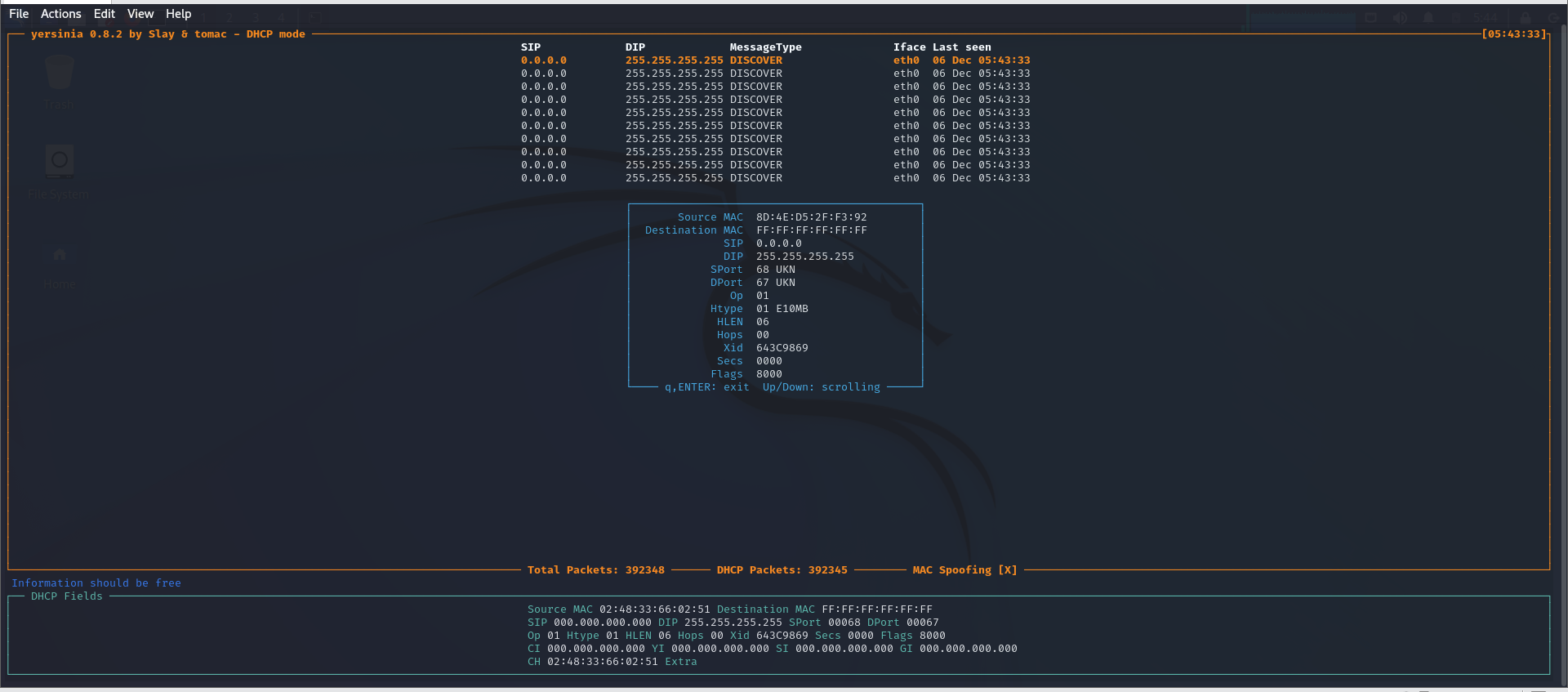
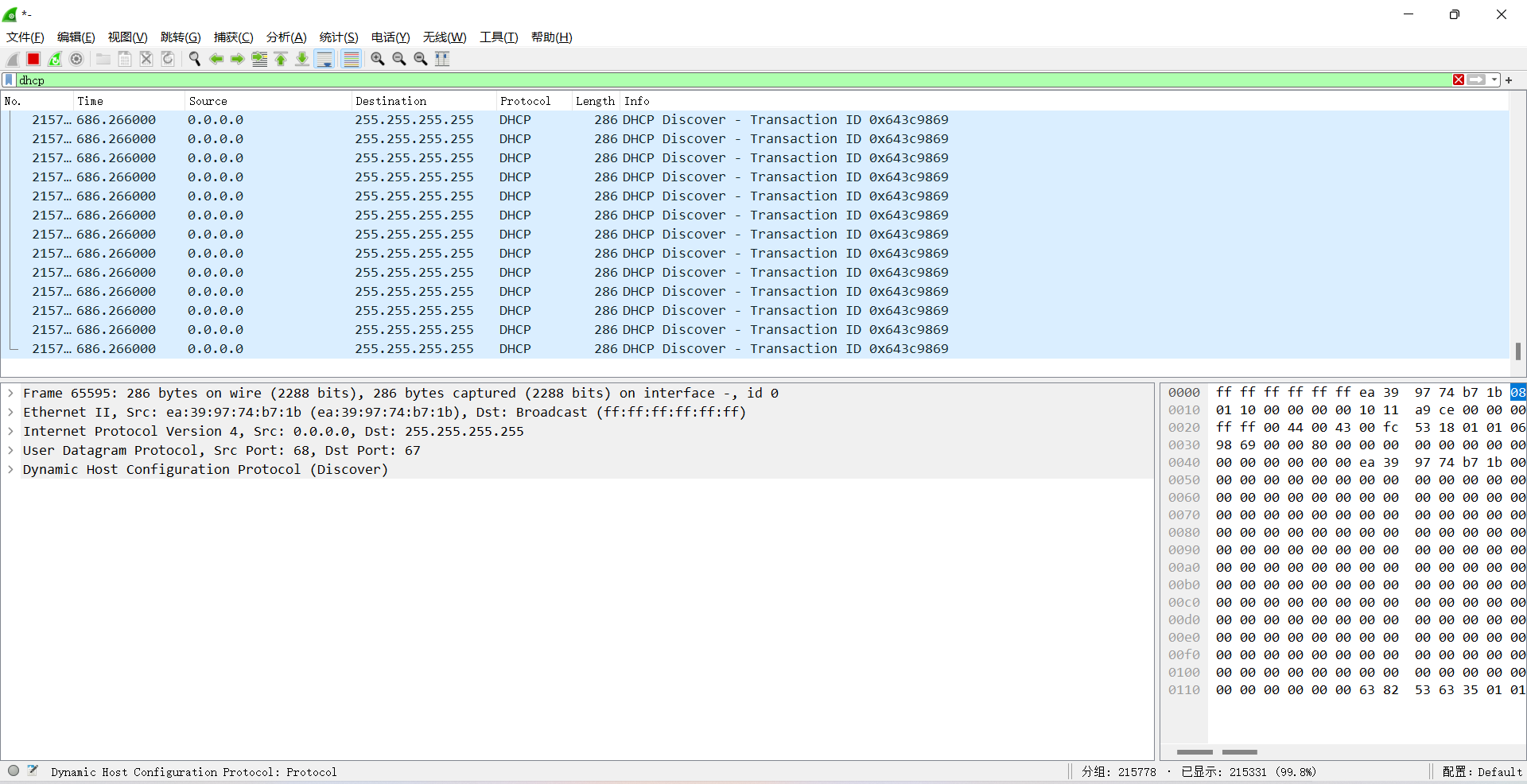
查看DHCP的地址池分配情况,所有地址都在使用中,此时PC1无法动态获取到地址
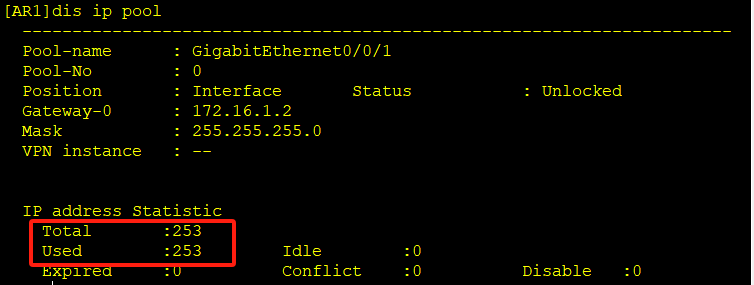
防御配置(端口安全)
配置LSW1的GE0/0/3接口可以学习的MAC地址做限制
LSW1
[LSW1-GigabitEthernet0/0/3]port-security enable
[LSW1-GigabitEthernet0/0/3]port-security max-mac-num 1
[LSW1-GigabitEthernet0/0/3]port-security protect-action shutdown
KALI再次模拟攻击,LSW3的GE0/0/3接口被关闭

DHCP中间人攻击
拓扑
配置如同上
攻击模拟
KALI开启Ettercap嗅探

开启KALI转发

进行中间人欺骗
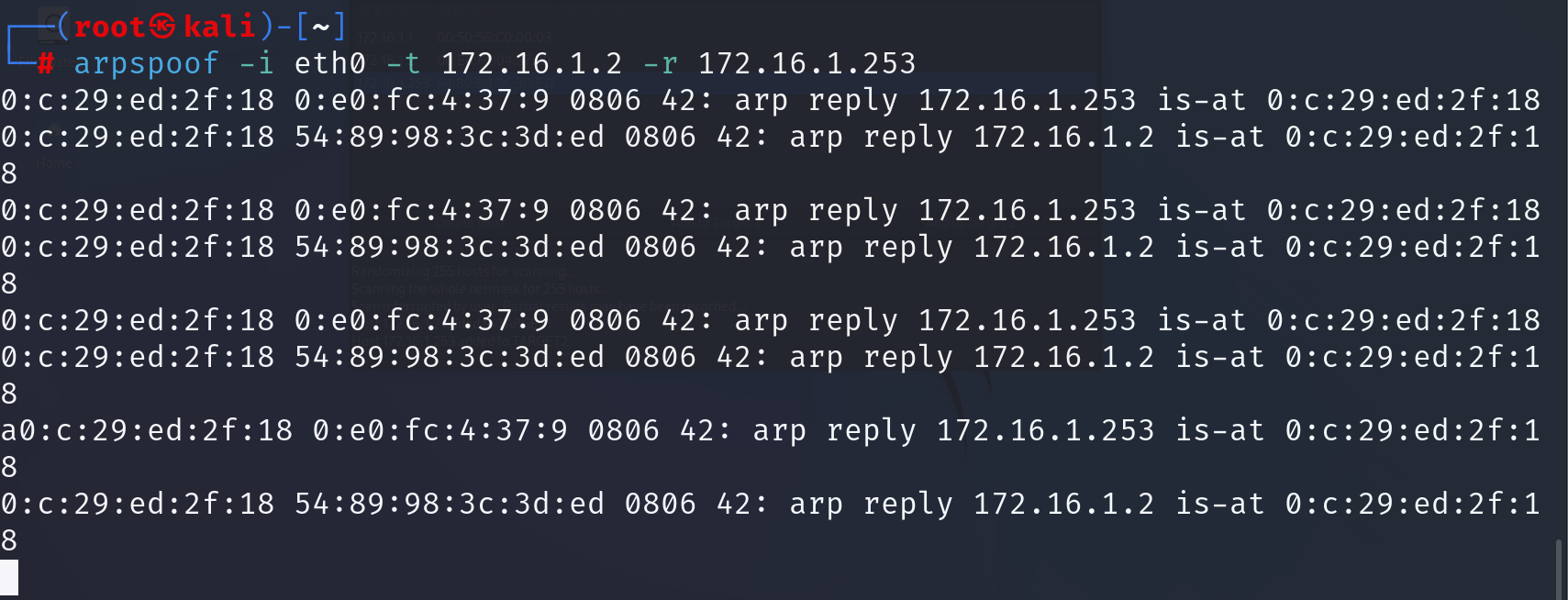
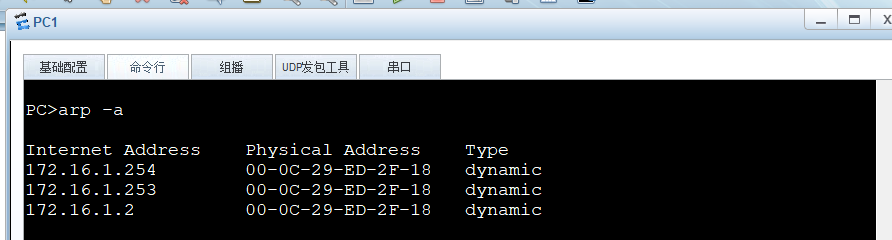
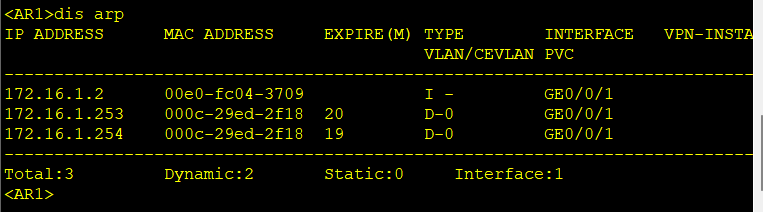
观察PC和路由器的ARP表,都已将互相的MAC地址记录为黑客的地址
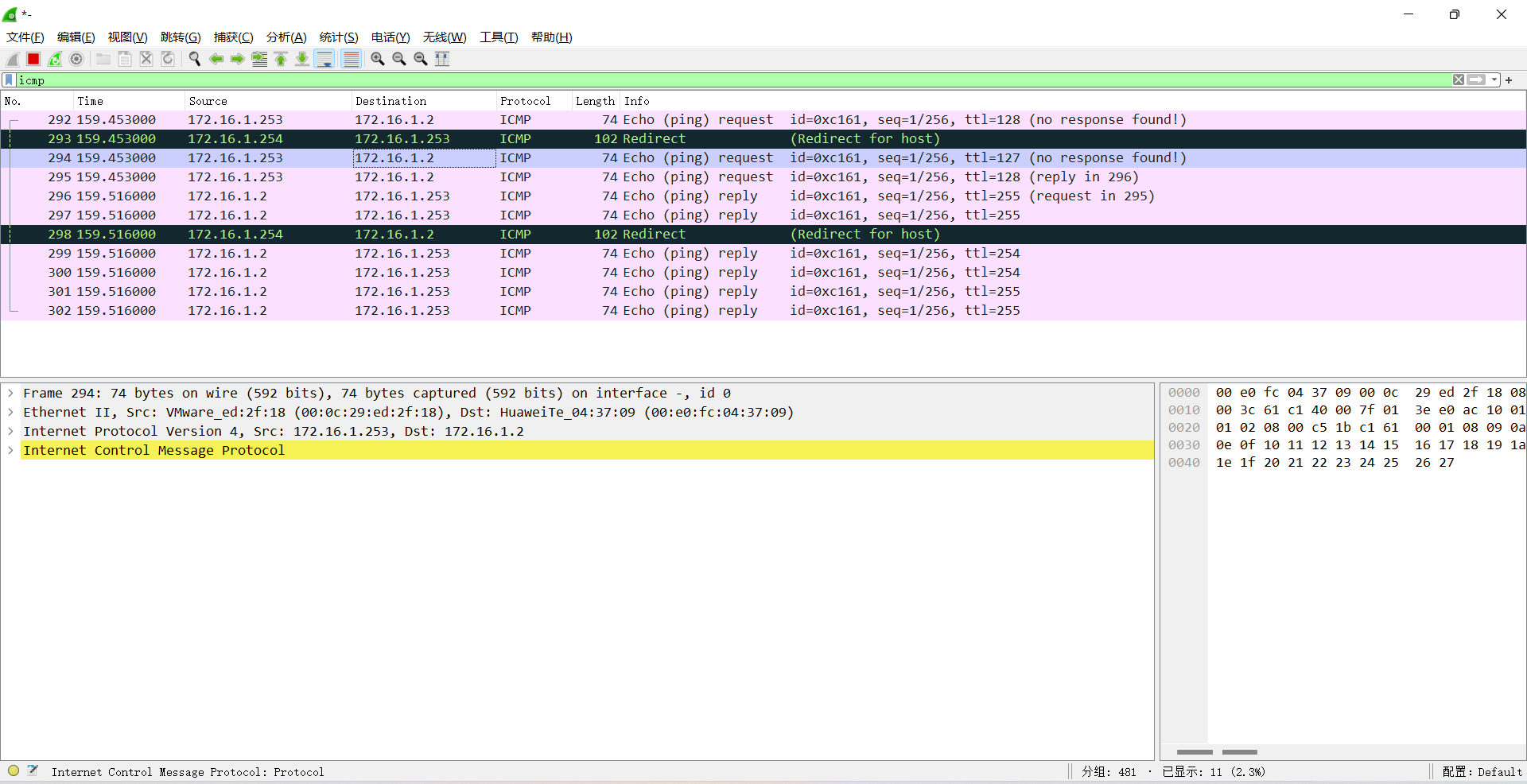
在LSW1的GE0/0/3接口抓包,发现PC1和AR1之间的流量已经被截获
防御中间人攻击(DAI)
LSW1开启DHCP Snooping,使用DHCP Snooping生成的表格做ARP防护
[LSW1]dhcp snooping enable
[LSW1]inte gi 0/0/1
[LSW1-GigabitEthernet0/0/1]dhcp snooping enable
[LSW1-GigabitEthernet0/0/1]dhcp snooping trusted
[LSW1]port-group group-member gi 0/0/2 to gi 0/0/3
[LSW1-port-group]dhcp snooping enable
[LSW1-port-group]port-security enable
[LSW1-port-group]arp anti-attack check user-bind enable
黑客和PC1重新获取地址,查看LSW1记录了IP和MAC的绑定关系
[LSW1]display dhcp snooping user-bind all
DHCP Dynamic Bind-table:
Flags:O - outer vlan ,I - inner vlan ,P - map vlan
IP Address MAC Address VSI/VLAN(O/I/P) Interface Lease
--------------------------------------------------------------------------------
172.16.1.253 5489-983c-3ded 1 /-- /-- GE0/0/2 2023.12.07-22:52
172.16.1.254 000c-29ed-2f18 1 /-- /-- GE0/0/3 2023.12.07-22:53
--------------------------------------------------------------------------------
print count: 2 total count: 2
再次黑客模拟中间人攻击
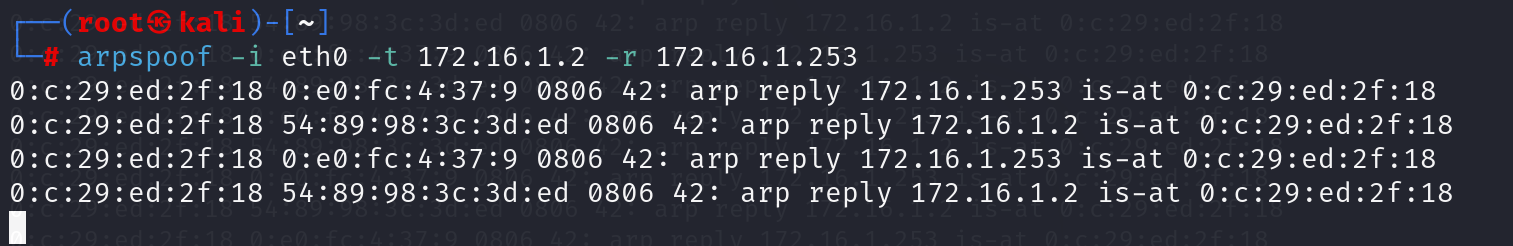
查看PC1和AR1的arp表,并没有被影响(ensp中模拟不出效果,知道防御成功就好)