边缘
目标:先把四台接入交换同、两台EXPORT、一台AC彻底配置完成。
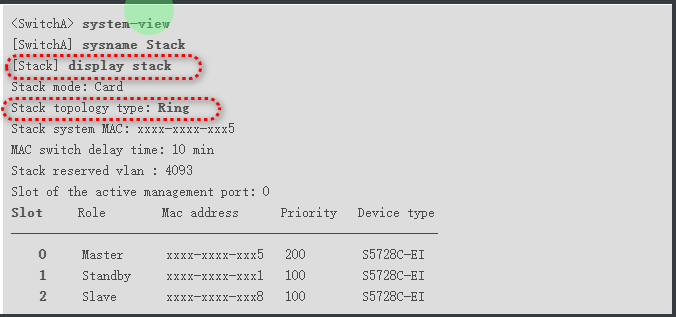
ACC堆叠
# MASTER
## 先给主设备命个名
## 这样在备设备上配置成功之后也会使用这个名字
## 从而间接的判断出堆叠是否成功
sysname X_T2_ACC1
stack slot 0 priority 200
stack slot 0 renumber 0
interface stack-port 0/1
port interface xg 0/0/1 enable
shutdown int xg0/0/1
interface stack-port 0/2
port int xg0/0/2 en
shutdown int xg0/0/2
run save force
# slave
## 默认优先级就是100,所以这一条可以默认不写
# stack slot 0 priority 100
stack slot 0 renumber 1
interface stack-port 0/1
port int xg0/0/2 en
interface stack-port 0/2
port int xg0/0/1 en
run save force
reboot
PS:在备设备重启的过程当中(大概持续一到两分种),去主设备把逻辑接口给UP了!
# MASTER
interface stack-port 0/1
undo shutdown int xg0/0/1
interface stack-port 0/2
undo shutdodown int xg0/0/2
-
验证
ACC配置
- 四台ACC的的任务非常简单(把这四个任务做完,ACC再无配置了)
- 连接AP
- 对于无线仅需要透传一个VLAN-100
- 对于有线直接把dot1x打开
- 链路捆绑
# X_T1_ACC1
sys
sysn X_T1_ACC1
vlan 100
int g0/0/22
p l a
p d v 100
# 链路捆绑相关配置
int eth-trunk 2
mode lacp
p l t
p t a v 100
trunkp g0/0/23
trunkp g0/0/24
# 准入相关配置
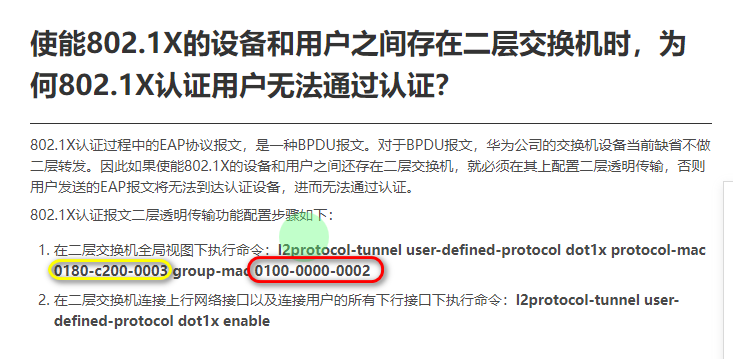
l2protocol-tunnel user-defined-protocol DOT1X protocol-mac 0180-c200-0003 group-mac 0100-0ccd-0002
int eth-trunk 2
l2protocol-tunnel user-defined-protocol DOT1X enable
int range g0/0/1 to g0/0/20
l2protocol-tunnel user-defined-protocol DOT1X enable
- PS:
- l2protocol-tunnel user-defined-protocol命令用来自定义二层透明传输协议的特征信息
- user-defined-protocol 后面的DOT1X是自己起的名字
# X_T1_ACC2
sys
sysn X_T1_ACC2
vlan 100
# 链路捆绑相关配置
int eth-trunk 3
mode lacp
p l t
p t a v 100
trunkp g0/0/23
trunkp g0/0/24
# 准入相关配置
l2protocol-tunnel user-defined-protocol DOT1X protocol-mac 0180-c200-0003 group-mac 0100-0ccd-0002
int eth-trunk 3
l2protocol-tunnel user-defined-protocol DOT1X enable
int range g0/0/1 to g0/0/20
l2protocol-tunnel user-defined-protocol DOT1X enable
# X_T2_ACC1
sys
sysn X_T2_ACC1
vlan 100
# 链路捆绑相关配置
int eth-trunk 2
mode lacp
p l t
p t a v 100
trunkp g0/0/23
trunkp g0/0/24
# 准入相关配置
l2protocol-tunnel user-defined-protocol DOT1X protocol-mac 0180-c200-0003 group-mac 0100-0ccd-0002
int eth-trunk 2
l2protocol-tunnel user-defined-protocol DOT1X enable
int range g0/0/1 to g0/0/20
l2protocol-tunnel user-defined-protocol DOT1X enable
# X_T2_ACC2
sys
sysn X_T2_ACC2
vlan 100
int g0/0/22
p l a
p d v 100
# 链路捆绑相关配置
int eth-trunk 3
mode lacp
p l t
p t a v 100
trunkp g0/0/23
trunkp g0/0/24
# 准入相关配置
l2protocol-tunnel user-defined-protocol DOT1X protocol-mac 0180-c200-0003 group-mac 0100-0ccd-0002
int eth-trunk 3
l2protocol-tunnel user-defined-protocol DOT1X enable
int range g0/0/1 to g0/0/20
l2protocol-tunnel user-defined-protocol DOT1X enable
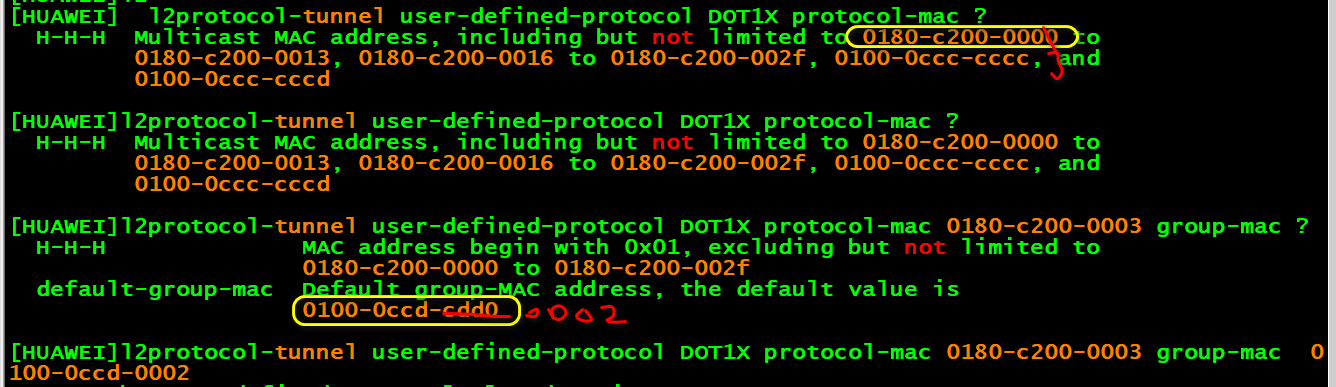
- protocol-mac 0180-c200-0003 二层透明传输协议报文的组播目的MAC地址。
- group-mac 0100-0ccd-0002 二层协议报文的目的MAC地址被替换后的组播MAC地址,如果这个地方不写,那就使用默认的,二层协议报文的目的MAC地址被替换为缺省的组播MAC地址0100-0ccd-cdd0。
- 合起来的意思是上面的意思是将 EAP协议原本的组播目的MAC地址 0180-c200-0003替换成0180-c200-0003 这个组播MAC
- l2protocol-tunnel user-defined-protocol 这里是定义要透传的报文的协议特征,这里是涉及802.1x认证的 eap协议。原本目的组播mac的报文是要上送CPU处理的,经过替换目的组播mac就不会上送了,达到直接转发(透明传输)功能,当然出接口还是会替换回来的,要不然下个设备不认识这个报文了。(来自网友的回答)
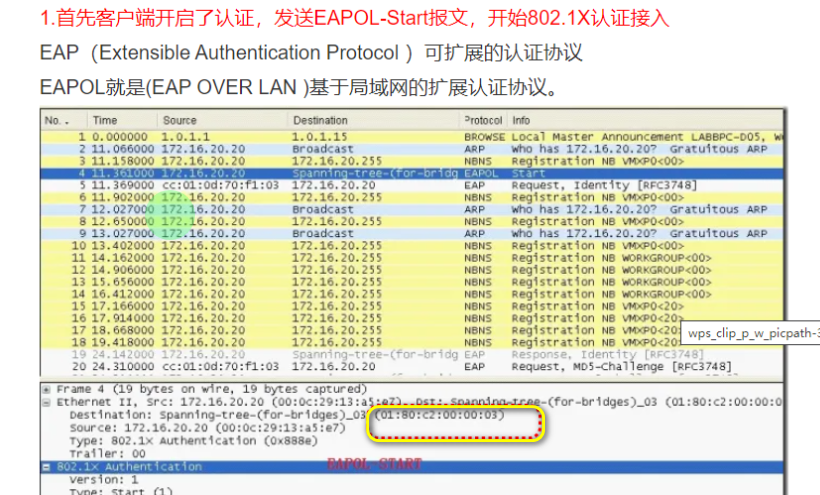
https://support.huawei.com/enterprise/zh/doc/EDOC1100301638/5b1ae9a9
EXPORT-1
- EXPORT-1的配置也很简单:
- 环回+三个接口的IP地址
- OSPF进程1区域0的配置
- OSPF下发静态路由
sys
sysn X_T1_Export1
vlan 201
int l0
ip add 10.1.0.1 32
int g0/0/0
ip add 10.255.1.1 24
int g0/0/2
ip add 10.255.2.1 24
int vlan 201
ip add 10.1.200.1 30
int g5/0/1
p l a
p d v 201
ospf 1 router-id 10.1.0.1
ar 0
net 10.1.0.1 0.0.0.0
net 10.1.200.1 0.0.0.0
default-route-advertise
ip route-static 0.0.0.0 0 10.255.1.254
ip route-static 0.0.0.0 0 10.255.2.254
EXPORT-2
EXPORT-1的配置也很简单:
- 环回+三个接口的IP地址
- OSPF进程1区域0的配置
- OSPF下发静态路由
- NAT一个接口纯NAT、另一个接口是基于地址池的NAT
- 还有一个端口映射
sys
sysn X_T1_Export2
vlan 202
int l0
ip add 10.1.0.2 32
acl 2000
rule permit
int g0/0/0
ip add 10.255.3.1 24
nat outbound 2000
nat address-group 1 10.255.4.2 10.255.4.100
int g0/0/2
ip add 10.255.4.1 24
nat outbound 2000 address-group 1
nat server protocol tcp global current-interface 8081 inside 10.1.60.101 80
int vlan 202
ip add 10.1.200.5 30
int g5/0/1
p l a
p d v 202
ospf 1 router-id 10.1.0.2
a 0
net 10.1.0.2 0.0.0.0
net 10.1.200.5 0.0.0.0
default-route-advertise
ip route-static 0.0.0.0 0 10.255.3.254
ip route-static 0.0.0.0 0 10.255.4.254
AC
AC上的配置也并不多:
- 环回接口(10.1.0.11)、vlan100配置IP、开启接口dhcp
- vlan203就配置一个IP地址10.1.200.10即可
- 所有的无线都从这过,所以51-55,101到105都得创建并且与核心对接的trunk接口也得放行
- 最后就是WLAN的配置,注意先不认证,获取到MAC之后再改成mac认证,而且还要使用VLAN池
AP_dhcp
# AC
sys
sysn X_T1_AC1
vlan b 203 100
vlan batch 51 to 55
vlan batch 101 to 105
dhcp enable
int l0
ip add 10.1.0.11 32
int g0/0/1
p l t
p t a v 203 100 51 to 55 101 to 105
interface Vlanif100
dhcp select interface
ip address 10.1.100.254 255.255.255.0
int vlan 203
ip add 10.1.200.10 30
AP上线
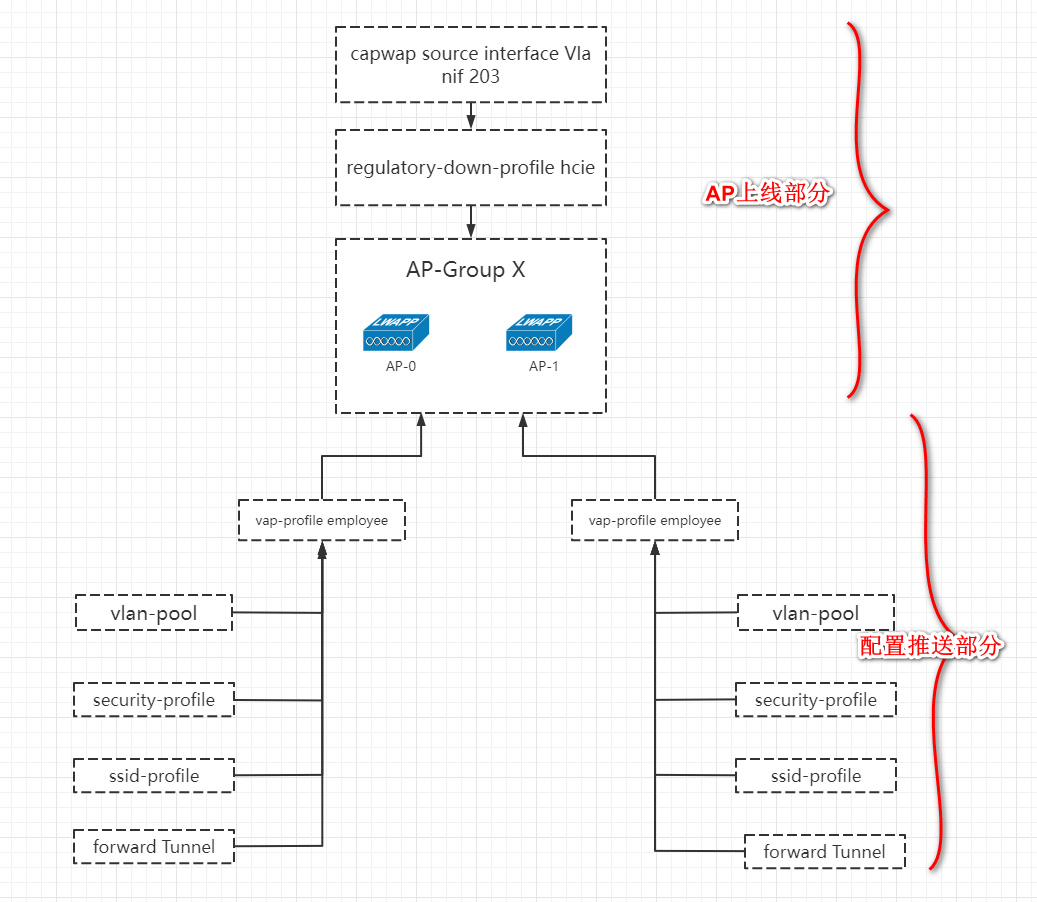
# WLAN整体配置
## 首先声明隧道的目标VLAN-IP
capwap source interface Vlanif 203
wlan
## 先创建域管理模板,hcie模板
regulatory-domain-profile name hcie
country-code cn
quit
## 创建ap组,声明使default域管理模板
ap-group name X
regulatory hcie
y
quit
## 考试时先让P上线,所以直接采用不认证,否则自己也拿不到AP的MAC
ap auth-mode no-auth
## 将两台AP添加到AP组
## 这是预配
ap-id 0 ap-mac 00e0-fcf6-6f80
ap-name X_T1_AP1
ap-group X
quit
ap-id 1 ap-mac 00e0-fc7e-4d20
ap-name X_T2_AP1
ap-group X
这一步完成之后,两台AP就会正常上线:
<X_T1_AC1>dis ap all
Info: This operation may take a few seconds. Please wait for a moment.done.
Total AP information:
nor : normal [2]
--------------------------------------------------------------------------------
-----------
ID MAC Name Group IP Type State STA Uptime
--------------------------------------------------------------------------------
-----------
0 00e0-fcf6-6f80 X_T1_AP1 X 10.1.100.219 AP2050DN nor 0 34S
1 00e0-fc7e-4d20 X_T2_AP1 X 10.1.100.71 AP2050DN nor 0 28S
--------------------------------------------------------------------------------
配置推送
# 先做出两个vlan池,内部和外部,尽量保持IP地址不改变
# 注意这是vlan池,不是地址池
vlan pool interior_vlan_pool
vlan 51 to 55
ass hash
vlan pool without_vlan_pool
vlan 101 to 105
ass hash
wlan
## 创建empoyee的安全模板
security-profile name employee
security wpa-wpa2 psk pass-phrase Huawei@123 aes
quit
## 创建SSID模板
ssid-profile name employee
ssid employee
quit
## VAP的配置文件
vap-profile name Employee
forward-mode tunnel
service-vlan vlan-pool interior_vlan_pool
security-profile employee
ssid-profile employee
quit
## 将vap模板在AP组里面应用到射频
ap-group name X
vap-profile Employee wlan 1 radio all
wlan
## 创建empoyee的安全模板
security-profile name guest
security wpa-wpa2 psk pass-phrase Huawei@123 aes
quit
## 创建SSID模板
ssid-profile name guest
ssid guest
quit
## VAP的配置文件
vap-profile name guest
forward-mode tunnel
service-vlan vlan-pool without_vlan_pool
security-profile guest
ssid-profile guest
quit
## 将vap模板在AP组里面应用到射频
ap-group name X
vap-profile guest wlan 2 radio all
T1_AGG1
链路捆绑
# X_T1_AGG1
int eth-trunk 1
mode lacp
p l t
port t al vlan 100 208
trunkport g0/0/11
trunkport g0/0/12
trunkport g0/0/13
trunkport g0/0/14
int eth-trunk 2
mode lacp
port link-type hybrid
port hybrid tagged vlan 100
port hybrid untagged vlan 11 to 15 21 to 25
trunkp g0/0/23
trunkp g0/0/24
int eth-trunk 3
mode lacp
port hybrid tagged vlan 100
port hybrid untagged vlan 11 to 15 21 to 25
trunkp g0/0/21
trunkp g0/0/22
vlan地址和dhcp
# X_T1_AGG1 全局配置
sys
sysn X_T1_AGG1
vlan batch 100 208 11 to 15 21 to 25
dhcp enable
# X_T1_AGG1 环回和互联接口
int l0
ip add 10.1.0.6 32
int vlan 208
ip add 10.1.200.30 30
# X_T1_AGG1 业务接口
# purchase 采购部相关vlan接口
int vlan 11
ip add 10.1.11.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 12
ip add 10.1.12.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 13
ip add 10.1.13.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 14
ip add 10.1.14.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 15
ip add 10.1.15.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.29
# market 市场部相关vlan接口
int vlan 21
ip add 10.1.21.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 22
ip add 10.1.22.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 23
ip add 10.1.23.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 24
ip add 10.1.24.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 25
ip add 10.1.25.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.29
OSPF
ospf 2 router-id 10.1.0.6
a 1
network 10.1.200.30 0.0.0.0
network 10.1.11.254 0.0.0.0
network 10.1.12.254 0.0.0.0
network 10.1.13.254 0.0.0.0
network 10.1.14.254 0.0.0.0
network 10.1.15.254 0.0.0.0
network 10.1.21.254 0.0.0.0
network 10.1.22.254 0.0.0.0
network 10.1.23.254 0.0.0.0
network 10.1.24.254 0.0.0.0
network 10.1.25.254 0.0.0.0
AAA和准入
# 第一步:在X_T1_AGG1上定义Radius-server
radius-server template Employee
radius-server shared-key cipher Huawei@123
radius-server authentication 10.1.60.2 1012
radius-server accounting 10.1.60.2 1813
radius-server authorization 10.1.60.2 shared-key cipher Huawei@123
# 第二步:定义AAA并指向到Radius
aaa
authentication-scheme Employee
authentication-mode radius
accounting-scheme Employee
accounting-mode radius
# 由于radius的授权与认证是一体的,所以下面这两行可以不敲
# authorization-scheme Employee
# authorization-mode none
# 第三步:将AAA与radius放到一个新创建的域模板当中
aaa
domain Employee
authentication-scheme Employee
accounting-scheme Employee
authorization-scheme Employee
radius-server Employee
# 第四步:准入的配置
## 定义MAC认证的模板
mac-access-profile name Employ
## 定义DOT1X认证的模板
dot1x-access-profile name Employ
## 定义authtication模板,将准入的模板关联到域模板当中
authentication-profile name Employ
mac-access-profile name Employ
dot1x-access-profile name Employ
# 使能MAC旁路认证功能。缺省情况下,未使能MAC旁路认证功能。
authtication dot1x-mac-bypass
authtication mode multi-authen max-user 500 # 允许多少人来认证
# 配置用户的默认域或强制域,缺省情况下
# 认证模板中未配置用户的默认域或强制域,用户默认使用全局默认域“default”。
access-domain employee force
# 第五步:汇聚接口和接入接入调用域模板
# 当你在接口上调用时,它会要求接口类型必须是Hybrid
int eth-trunk 2
authtication-profile Employee
int eth-trunk 3
authtication-profile Employee
T1_AGG2
链路捆绑
# X_T1_AGG2
int eth-trunk 1
mode lacp
p l t
port t al vlan 100 209
trunkport g0/0/15
trunkport g0/0/16
trunkport g0/0/17
trunkport g0/0/18
int eth-trunk 2
mode lacp
port hybrid tagged vlan 100
port hybrid untagged vlan 31 to 35 41 to 45
trunkp g0/0/23
trunkp g0/0/24
int eth-trunk 3
mode lacp
port hybrid tagged vlan 100
port hybrid untagged vlan 31 to 35 41 to 45
trunkp g0/0/21
trunkp g0/0/22
vlan地址和dhcp
# X_T2_AGG1 全局配置
sys
sysn X_T2_AGG1
dhcp enable
vlan batch 100 209 31 to 35 41 to 45
# X_T2_AGG1,环回接口和互联接口
int l0
ip add 10.1.0.7 32
int vlan 209
ip add 10.1.200.34 30
# 业务接口
## finance 财务部相关vlan接口
int vlan 31
ip add 10.1.31.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 32
ip add 10.1.32.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 33
ip add 10.1.33.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 34
ip add 10.1.34.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 35
ip add 10.1.35.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.33
# hr 人力部相关vlan接口
int vlan 41
ip add 10.1.41.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 42
ip add 10.1.42.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 43
ip add 10.1.43.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 44
ip add 10.1.44.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 45
ip add 10.1.45.254 24
dhcp select relay
dhcp relay server-ip 10.1.200.33
OSFP
ospf 2 router-id 10.1.0.7
a 1
network 10.1.200.34 0.0.0.0
network 10.1.31.254 0.0.0.0
network 10.1.32.254 0.0.0.0
network 10.1.33.254 0.0.0.0
network 10.1.34.254 0.0.0.0
network 10.1.35.254 0.0.0.0
network 10.1.41.254 0.0.0.0
network 10.1.42.254 0.0.0.0
network 10.1.43.254 0.0.0.0
network 10.1.44.254 0.0.0.0
network 10.1.45.254 0.0.0.0
AAA和准入
# 第一步:在X_T1_AGG1上定义Radius-server
radius-server template Employee
radius-server shared-key cipher Huawei@123
radius-server authentication 10.1.60.2 1812
radius-server accounting 10.1.60.2 1813
radius-server authorization 10.1.60.2 shared-key cipher Huawei@123
# 第二步:定义AAA并指向到Radius
authentication-scheme Employee
authentication-mode radius
accounting-scheme Employee
accounting-mode radius
# 由于radius的授权与认证是一体的,所以下面这两行可以不敲
# authorization-scheme Employee
# authorization-mode none
# 第三步:将AAA与radius放到一个新创建的域模板当中
aaa
domain Employee
authentication-scheme Employee
accounting-scheme Employee
authorization-scheme Employee
radius-server Employee
# 第四步:准入的配置
## 定义MAC认证的模板
mac-access-profile name Employ
## 定义DOT1X认证的模板
dot1x-access-profile name Employ
## 定义authtication模板,将准入的模板关联到域模板当中
authentication-prifile name Employ
mac-access-profile name Employ
dot1x-access-profile name Employ
# 使能MAC旁路认证功能。缺省情况下,未使能MAC旁路认证功能。
authtication dot1x-mac-bypass
authtication mode multi-authen max-user 500 # 允许多少人来认证
# 配置用户的默认域或强制域,缺省情况下
# 认证模板中未配置用户的默认域或强制域,用户默认使用全局默认域“default”。
access-domain employee force
# 第五步:汇聚接口和接入接入调用域模板
# 当你在接口上调用时,它会要求接口类型必须是Hybrid
int eth-trunk 2
authtication-profile Employee
int eth-trunk 3
authtication-profile Employee
防火墙
物理接口配置
# FW
sys
sysn X_T1_FW1
vlan batch 204 to 207
int l0
ip add 10.1.0.8 32
int l1
ip add 10.1.0.9 32
int g1/0/2
portsw
p l t
p t al vlan 206 207
undo p t al vlan 1
int g1/0/1
undo shut
portsw
p l t
p t al vlan 204 205
undo p t al vlan 1
VN、接口
# FW防火墙
int vlan 204
quit
int vlan 205
quit
int vlan 206
quit
int vlan 207
quit
vsys enable
vsys name Employee
ass vlan 206
ass vlan 204
vsys name Guest
ass vlan 207
ass vlan 205
swi vsys Employee
sys
int vlan 206
ip add 10.1.200.22 30
service ping permit
int vlan 204
ip add 10.1.200.14 30
service ping permit
firewall zone trust
add int vlan 206
firewall zone untrust
add int vlan 204
quit
quit
quit
swi vsys Guest
sys
int vlan 207
ip add 10.1.200.26 30
service ping permit
int vlan 205
ip add 10.1.200.18 30
service ping permit
firewall zone trust
add int vlan 207
firewall zone untrust
add int vlan 205
OSPF
# Employee-OSPF2-A1
ospf 2 router-id 10.1.0.8 vpn-instance Employee
vpn-instance-cap simple
a 1
network 10.1.200.22 0.0.0.0
network 10.1.200.14 0.0.0.0
# Employee-OSPF2-A2
ospf 3 router-id 10.1.0.9 vpn-instance Guest
vpn-instance-cap simple
a 2
network 10.1.200.26 0.0.0.0
network 10.1.200.18 0.0.0.0
安全策略
Guest操作汇总
- 一个地址组所有:外部无线
- 一个对象组:3389
- 四条策略
[X_T1_FW1-Guest-policy-security]dis th
2023-07-18 08:03:51.510
#
security-policy
rule name permit_ospf
source-zone local
source-zone trust
source-zone untrust
destination-zone local
destination-zone trust
destination-zone untrust
service ospf
action permit
rule name permit_60.99_trust_untrust
source-zone trust
destination-zone untrust
destination-address 10.1.60.99 mask 255.255.255.255
service Guest_Server
action permit
rule name deny_60.0_trust_untrust
source-zone trust
destination-zone untrust
source-address address-set without_wireless
destination-address 10.1.60.0 0.0.0.255
action deny
rule name to_internet
source-zone trust
destination-zone untrust
source-address address-set without_wireless
action permit

Guest当中只有五条策略,其中ospf就占了两条,还有三条,分别是:
- 允许guest组访问60.99+端口绕行的(trust-untrust)
- 拒绝所有访问60网段的(trust-untrust)
- 上网的(trust-untrust)
Employee操作汇总
-
三个地址组:采购、市场、内部无线
-
三个对象组:Guest_Server、port_map_80、server_60.100
default packet-filter intrazone enable
rule name permit_ospf_in
source-zone trust
source-zone untrust
destination-zone local
service ospf
action permit
rule name permit_ospf_out
source-zone local
destination-zone trust
destination-zone untrust
service ospf
action permit
rule name permit_untrust_to_trust60.101
source-zone untrust
destination-zone trust
destination-address 10.1.60.101 mask 255.255.255.255
service http
action permit
rule name permit_trust_trust60.100
source-zone trust
destination-zone trust
source-address address-set wlan
destination-address 10.1.60.100 mask 255.255.255.255
action permit
rule name permit_untrust_trust60.99
source-zone untrust
destination-zone trust
source-address address-set guest
destination-address 10.1.60.99 mask 255.255.255.255
service Guest_Service
action permit
rule name permit_inner_to_internet
source-zone trust
destination-zone untrust
source-address address-set caigoushichang
source-address address-set wlan
action permit
(双)组
# 在employee虚拟防火墙当中的地址组
## purshase
ip address-set purshase type group
add 10.1.11.0 mask 24
add 10.1.12.0 mask 24
add 10.1.13.0 mask 24
add 10.1.14.0 mask 24
add 10.1.15.0 mask 24
## market
ip address-set market type group
add 10.1.21.0 mask 24
add 10.1.22.0 mask 24
add 10.1.23.0 mask 24
add 10.1.24.0 mask 24
add 10.1.25.0 mask 24
## employee_wireless
ip address-set employee_wireless type group
add 10.1.51.0 mask 24
add 10.1.52.0 mask 24
add 10.1.53.0 mask 24
add 10.1.54.0 mask 24
add 10.1.55.0 mask 24
## guest_wireless
ip address-set guest_wireless type group
add 10.1.101.0 mask 24
add 10.1.102.0 mask 24
add 10.1.103.0 mask 24
add 10.1.104.0 mask 24
add 10.1.105.0 mask 24
## 针对60.101,端口映射用的
ip address-set host60.101 type group
address 10.1.60.101 mask 32
## 针对60.100的
ip address-set host60.100 type group
address 10.1.60.100 mask 32
## 针对60.99绕行的,被多次调用,两台虚防火墙都要创建
ip address-set host60.99 type group
address 10.1.60.99 mask 32
## Guest_Service 代表3389,需求要求,必须创建
ip service-set Guest_Server type object
service 0 protocol tcp destination-port 3389
# 在guest虚拟防火墙当中的地址组
## guest_wireless
ip address-set guest_wireless type group
add 10.1.101.0 mask 24
add 10.1.102.0 mask 24
add 10.1.103.0 mask 24
add 10.1.104.0 mask 24
add 10.1.105.0 mask 24
## 同样针对60.99绕行的,被多次调用,两台虚防火墙都要创建
ip address-set host60.99 type group
address 0 10.1.60.99 mask 32
## 两台虚拟防火墙当中都要创建
ip service-set Guest_Service type object
server protocol tcp 3389
(双)OSPF放行
# 根实例全局敲
firewall packet-filter basic-protocol enable
switch vsys Employee
sys
security-policy
rule name ospf_in
source-zone trust
source-zone untrust
destination-zone local
service ospf
action permit
rule name ospf_out
source-zone local
destination-zone trust
destination-zone untrust
service ospf
action permit
switch vsys Guest
sys
security-policy
rule name ospf_in
source-zone trust
source-zone untrust
destination-zone local
service ospf
action permit
rule name ospf_out
source-zone local
destination-zone trust
destination-zone untrust
service ospf
action permit
(双)101 映射
switch vsys Employee
securiyt-policy
rule name permit_untrust_to_trust60.101
source-zone untrust
destination-zone trust
destination-address address-set host60.101
service http
action permit
有Employee当中放行了untrust到trust方向的策略,得去guest虚拟防火墙当中把101和105这五个网段到60网段全部拒绝,如下所示:
switch vsys guest
sys
security-policy
rule name deny_trust_untrust60.0
source zone trust
destination zone untrust
destination-address 10.1.60.0 mask 255.255.255.0
action deny
(单E)60.100
需求:内部无线仅可以访问服务器网段的10.1.60.100主机
PS:10.1.200.2是虚拟防火墙Employee的vlan206的接口IP
# 在employee虚拟防火墙打开同zone控制功能,默认已经打开
switch vsys epmloyee
security-policy
default packet-filter intrazone enable
# 由于我们上面已经定义好了employee_wireless的地址组,所以这里直接调用
switch vsys epmloyee
security-policy
rule name intrazone_employee_wireless_to_serverhost
source-zone trust
source-address address-set employee_wireless
destination-zone untrust
destination-address address-set host60.100
action permit
验证方法:
- 使用内部无线的终端ping 10.1.60.100看一下是否能ping通
- 同时,去防火墙上是否生成了会话,如果生成会话,那说明流量从防火墙走了(dis firewall session table)
- 再同时,去看策略是否被命中(dis security-policy rule all)
(双)60.99+端口绕行
需求:外部无线用户仅可以访问服务器网段中10.1.60.99的HTTP(3389端口)服务(服务名为Gueest-Server)
PS:从Guest绕到CORE,然后再从CORE绕到Employee的untrust当中
# 先在虚拟防火墙Guest操作,然后再去employee操作
# 先前我们已经做好了地址组和服务组了,这里面直接进行调用
switch vsys Guest
security-policy
rule name trust_to_untrust_60.99_permit
source-zone trust
souce-address set guest_wireless
destination untrust
destination-address address-set host60.99
service Guest_Server
action permit
switch vsys Employee
security-policy
rule name untrust_to_trust_60.99_permit
source-zone untrust
souce-address set guest_wireless
destination trust
destination-address 10.1.60.99 0.0.0.0
service Guest_Server
action permit
(双)60.99直通(无策略)
外部无线用户访问Guest_Server服务听流量需要直接在Geust和Emple之间转发;
- Guest与EMP两个虚拟系统的虚拟接口属于untrust区域,IP分别j10.1.200.254与10.1.200.253
- 仅当外部无线用户访问10.1.60.99时,流量直接在虚拟系统之间转发
- 没有安全策略
switch vsysn Guest
interface vlanif 2
ip add 10.1.200.254 30
firewall zone untrust
add interface vlanif 2
ip route-static vpn-instance Guest 10.1.60.99 255.255.255.255 vpn-instance Employee
# 先把虚拟接口和路由设置好,接口加入到安全区域
switch vsys Employee
interface vlanif 1
ip add 10.1.200.253 30
firewall zone untrust
add interface vlanif 1
ip route-static vpn-instance Employee 10.1.101.0 255.255.255.0 vpn-instance Guest
ip route-static vpn-instance Employee 10.1.102.0 255.255.255.0 vpn-instance Guest
ip route-static vpn-instance Employee 10.1.103.0 255.255.255.0 vpn-instance Guest
ip route-static vpn-instance Employee 10.1.104.0 255.255.255.0 vpn-instance Guest
ip route-static vpn-instance Employee 10.1.105.0 255.255.255.0 vpn-instance Guest
校验一下:
通过在Guest虚拟防火墙看会话,用主机进行测试一下,就会发现没做策略之前是绕行从核心的guest到guest,而现在是从guest直接到employess。
(双)上网
# employee当中三个部门上网:purshase、market、employee_wireless
switch vsys employee
sys
security-policy
rule name employee_to_internet
source zone trust
source-address set purshase market employee_wireless
destination zone untrust
action permit
# guest当中的所有网段都要上网:guest_wireless
switch vsys guest
sys
security-policy
rule name guest_to_internet
source zone trust
source-address set guest_wireless
destination zone untrust
action permit
核心
全局VN
ip vpn-instance Employee
route-dist 65001:1
quit
ip vpn-instance Guest
route-dist 65001:2
quit
vlan_所有地址池
所有业务的地址池11-15、21-15、31-35、41-45、51-55、101-105
接下来的操作可以通过VIM来操作,比较快捷,将purchase替换成为market、11替换成21、12替换成22、13替换23、14替换24、15替换成24
:%s@^\s\+@@g
:%s@\<purchase\>@market@g
:%s@\<11\>@21@g
:%s@\<12\>@22@g
:%s@\<13\>@23@g
:%s@\<14\>@24@g
:%s@\<15\>@25@g
:w! >> test10.tt
# 采购部相关地址池
ip pool wired_purchase1
vpn-instance Employee
gateway-list 10.1.11.254
network 10.1.11.0 mask 255.255.255.0
ip pool wired_purchase2
vpn-instance Employee
gateway-list 10.1.12.254
network 10.1.12.0 mask 255.255.255.0
ip pool wired_purchase3
vpn-instance Employee
gateway-list 10.1.13.254
network 10.1.13.0 mask 255.255.255.0
ip pool wired_purchase4
vpn-instance Employee
gateway-list 10.1.14.254
network 10.1.14.0 mask 255.255.255.0
ip pool wired_purchase5
vpn-instance Employee
gateway-list 10.1.15.254
network 10.1.15.0 mask 255.255.255.0
# 市场部
ip pool wired_market1
vpn-instance Employee
gateway-list 10.1.21.254
network 10.1.21.0 mask 255.255.255.0
ip pool wired_market2
vpn-instance Employee
gateway-list 10.1.22.254
network 10.1.22.0 mask 255.255.255.0
ip pool wired_market3
vpn-instance Employee
gateway-list 10.1.23.254
network 10.1.23.0 mask 255.255.255.0
ip pool wired_market4
vpn-instance Employee
gateway-list 10.1.24.254
network 10.1.24.0 mask 255.255.255.0
ip pool wired_market5
vpn-instance Employee
gateway-list 10.1.25.254
network 10.1.25.0 mask 255.255.255.0
# 财务部
ip pool wired_finace1
vpn-instance Employee
gateway-list 10.1.31.254
network 10.1.31.0 mask 255.255.255.0
ip pool wired_finace2
vpn-instance Employee
gateway-list 10.1.32.254
network 10.1.32.0 mask 255.255.255.0
ip pool wired_finace3
vpn-instance Employee
gateway-list 10.1.33.254
network 10.1.33.0 mask 255.255.255.0
ip pool wired_finace4
vpn-instance Employee
gateway-list 10.1.34.254
network 10.1.34.0 mask 255.255.255.0
ip pool wired_finace5
vpn-instance Employee
gateway-list 10.1.35.254
network 10.1.35.0 mask 255.255.255.0
# Hr部
ip pool wired_hr1
vpn-instance Employee
gateway-list 10.1.41.254
network 10.1.41.0 mask 255.255.255.0
ip pool wired_hr2
vpn-instance Employee
gateway-list 10.1.42.254
network 10.1.42.0 mask 255.255.255.0
ip pool wired_hr3
vpn-instance Employee
gateway-list 10.1.43.254
network 10.1.43.0 mask 255.255.255.0
ip pool wired_hr4
vpn-instance Employee
gateway-list 10.1.44.254
network 10.1.44.0 mask 255.255.255.0
ip pool wired_hr5
vpn-instance Employee
gateway-list 10.1.45.254
network 10.1.45.0 mask 255.255.255.0
# 内部无线
ip pool employee_wireless1
vpn-instance Employee
gateway-list 10.1.51.254
network 10.1.51.0 mask 255.255.255.0
ip pool employee_wireless2
vpn-instance Employee
gateway-list 10.1.52.254
network 10.1.52.0 mask 255.255.255.0
ip pool employee_wireless3
vpn-instance Employee
gateway-list 10.1.53.254
network 10.1.53.0 mask 255.255.255.0
ip pool employee_wireless4
vpn-instance Employee
gateway-list 10.1.54.254
network 10.1.54.0 mask 255.255.255.0
ip pool employee_wireless5
vpn-instance Employee
gateway-list 10.1.55.254
network 10.1.55.0 mask 255.255.255.0
# 外部无线
ip pool guest_wireless1
vpn-instance Guest
gateway-list 10.1.101.254
network 10.1.101.0 mask 255.255.255.0
ip pool guest_wireless2
vpn-instance Guest
gateway-list 10.1.102.254
network 10.1.102.0 mask 255.255.255.0
ip pool guest_wireless3
vpn-instance Guest
gateway-list 10.1.103.254
network 10.1.103.0 mask 255.255.255.0
ip pool guest_wireless4
vpn-instance Guest
gateway-list 10.1.104.254
network 10.1.104.0 mask 255.255.255.0
ip pool guest_wireless5
vpn-instance Guest
gateway-list 10.1.105.254
network 10.1.105.0 mask 255.255.255.0
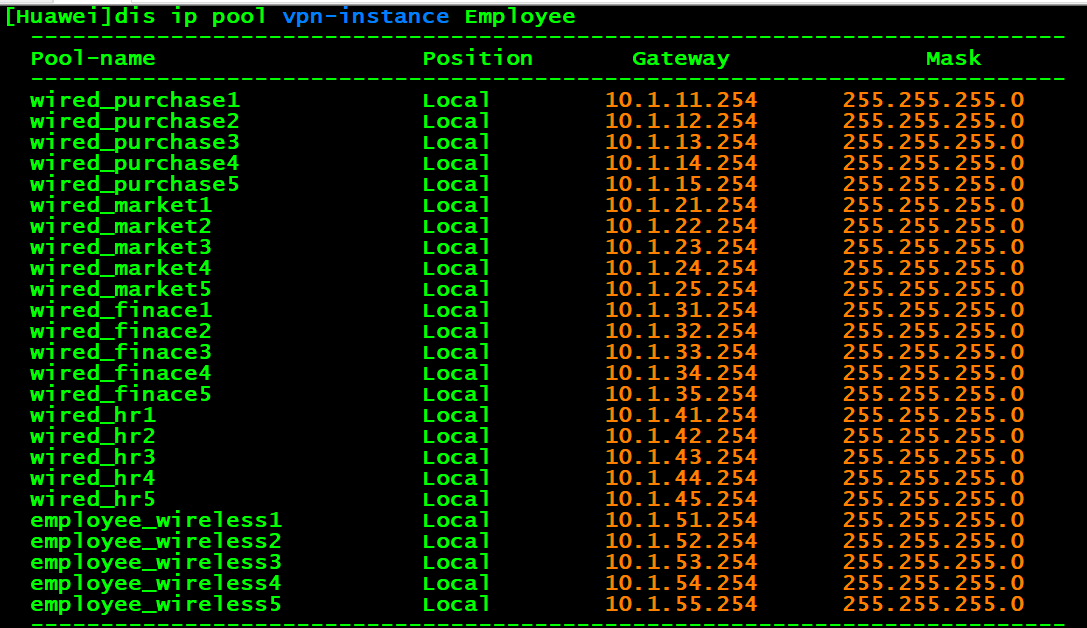
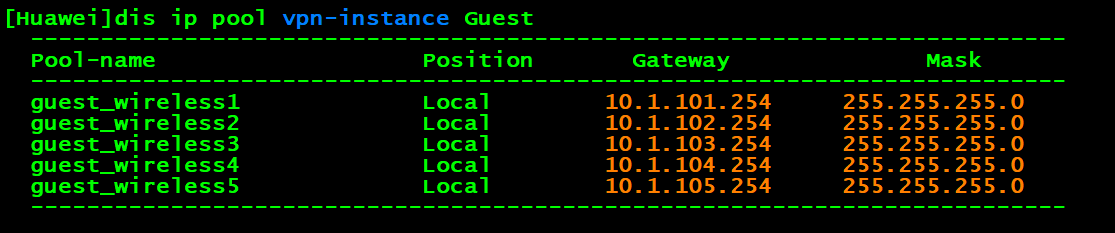
# 校验
dis ip pool vpn-instance Employee
dis ip pool vpn-instance Guest
接口_链路捆绑
# x_t1_core
int eth-trunk 2
mode lacp
p l t
port t al vlan 100 208
trunkport g0/0/11
trunkport g0/0/12
trunkport g0/0/13
trunkport g0/0/14
int eth-trunk 3
mode lacp
p l t
port t al vlan 100 209
trunkport g0/0/15
trunkport g0/0/16
trunkport g0/0/17
trunkport g0/0/18
接口_物理接口
# 与export对接
int g0/0/1
p l a
p d v 201
int g0/0/2
p l a
p d v 202
# 与AC对接
int g0/0/3
p l t
p t a vlan 100 203 51 to 55 101 to 105
int vlan 203
ip add 10.1.200.9 30
# 与防火墙对接
int g0/0/5
p l t
p t al vlan 206 207
undo p t al vlan 1
int g0/0/4
p l t
p t al vlan 204 205
undo p t al vlan 1
# 与服务器网段对接
int g0/0/6
port link-ty t
port t all vlan 60
接口_互联接口
# 全局配置
# CORE
sys
sysn X_T1_CORE1
# 先把所有的VLAN准备好
vlan batch 100 208 209 60 201 202 203 204 to 207 51 to 55 101 to 105
# 核心VN,先创建出来
ip vpn-instance Employee
route-dist 65001:1
ip vpn-instance Guest
route-dist 65001:2
# 全局dhcp打开,所有的vlan都要在这些获取IP地址
dhcp enable
# # 三个环回接口,用于OSPF-router-id
int l0
ip add 10.1.0.3 32
int l1
ip add 10.1.0.4 32
int l2
ip add 10.1.0.5 32
# 有线互联接口
## 208和209与汇聚的互联接口,不需要dhcp
int vlan 208
ip bind vpn Employee
ip add 10.1.200.29 30
int vlan 209
ip bind vpn Employee
ip add 10.1.200.33 30
## 与export的互联接口
int vlan 201
ip add 10.1.200.2 30
int vlan 202
ip add 10.1.200.6 30
## 与防火墙的互联接口
int vlan 204
ip add 10.1.200.13 30
int vlan 205
ip add 10.1.200.17 30
int vlan 206
ip bind vpn Employee
ip add 10.1.200.21 30
int vlan 207
ip bind vpn Guest
ip add 10.1.200.25 30
接口_11个vlan业务网关
- 51-55,101和105、60的网关
# 服务器网段全是静态,也不需要DHCP
int vlan 60
ip bind vpn Employee
ip add 10.1.60.254 24
# employee_wireless
int vlan 51
ip bind vpn Employee
ip add 10.1.51.254 24
dhcp select global
int vlan 52
ip bind vpn Employee
ip add 10.1.52.254 24
dhcp select global
int vlan 53
ip bind vpn Employee
ip add 10.1.53.254 24
dhcp select global
int vlan 54
ip bind vpn Employee
ip add 10.1.54.254 24
dhcp select global
int vlan 55
ip bind vpn Employee
ip add 10.1.56.254 24
dhcp select global
# without_wireless
int vlan 101
ip bind vpn Guest
ip add 10.1.101.254 24
dhcp select global
int vlan 102
ip bind vpn Guest
ip add 10.1.102.254 24
dhcp select global
int vlan 103
ip bind vpn Guest
ip add 10.1.103.254 24
dhcp select global
int vlan 104
ip bind vpn Guest
ip add 10.1.104.254 24
dhcp select global
int vlan 105
ip bind vpn Guest
ip add 10.1.105.254 24
dhcp select global
路由_OSPF
# public-ospf-1
ospf 1 router-id 10.1.0.3
ar 0
network 10.1.200.2 0.0.0.0
network 10.1.200.6 0.0.0.0
ar 1
network 10.1.200.13 0.0.0.0
ar 2
network 10.1.200.17 0.0.0.0
# Employee-OSPF2-A1
ospf 2 router-id 10.1.0.2 vpn-instance Employee
vpn-instance-cap simple
a 1
# 与FW的employee相连
network 10.1.200.21 0.0.0.0
# 所有内部无线
network 10.1.51.254 0.0.0.0
network 10.1.52.254 0.0.0.0
network 10.1.53.254 0.0.0.0
network 10.1.54.254 0.0.0.0
network 10.1.55.254 0.0.0.0
# 服务器网段
network 10.1.60.254 0.0.0.0
# 有线网段
network 10.1.200.29 0.0.0.0
network 10.1.200.33 0.0.0.0
# Employee-OSPF2-A2
ospf 3 router-id 10.1.0.3 vpn-instance Guest
vpn-instance-cap simple
a 2
# 与虚拟防火墙Guest相连
network 10.1.200.25 0.0.0.0
# 所有外部无线
network 10.1.101.254 0.0.0.0
network 10.1.102.254 0.0.0.0
network 10.1.103.254 0.0.0.0
network 10.1.104.254 0.0.0.0
network 10.1.105.254 0.0.0.0
路由_路由过滤
# CORE
# 把所有的内部路由匹配上,在Guest所在OSPF进程一,区域2当中调用
ip ip-prefix employee_route deny 10.1.11.0 24
ip ip-prefix employee_route deny 10.1.12.0 24
ip ip-prefix employee_route deny 10.1.13.0 24
ip ip-prefix employee_route deny 10.1.14.0 24
ip ip-prefix employee_route deny 10.1.15.0 24
ip ip-prefix employee_route deny 10.1.21.0 24
ip ip-prefix employee_route deny 10.1.22.0 24
ip ip-prefix employee_route deny 10.1.23.0 24
ip ip-prefix employee_route deny 10.1.24.0 24
ip ip-prefix employee_route deny 10.1.25.0 24
ip ip-prefix employee_route deny 10.1.31.0 24
ip ip-prefix employee_route deny 10.1.32.0 24
ip ip-prefix employee_route deny 10.1.33.0 24
ip ip-prefix employee_route deny 10.1.34.0 24
ip ip-prefix employee_route deny 10.1.35.0 24
ip ip-prefix employee_route deny 10.1.41.0 24
ip ip-prefix employee_route deny 10.1.42.0 24
ip ip-prefix employee_route deny 10.1.43.0 24
ip ip-prefix employee_route deny 10.1.44.0 24
ip ip-prefix employee_route deny 10.1.45.0 24
ip ip-prefix employee_route deny 10.1.51.0 24
ip ip-prefix employee_route deny 10.1.52.0 24
ip ip-prefix employee_route deny 10.1.53.0 24
ip ip-prefix employee_route deny 10.1.54.0 24
ip ip-prefix employee_route deny 10.1.55.0 24
ip ip-prefix employee_route deny 10.1.60.0 24
ip ip-prefix employee_route deny 10.1.200.28 30
ip ip-prefix employee_route deny 10.1.200.32 30
ip ip-prefix employee_route permit 0.0.0.0 0 less 32
ospf 1
a 2
# 这个地方最容易出错,名字不检测,瞎写也能写好,所以最好复制
filter ip-prefix employee_route import
ip ip-prefix guest_route deny 10.1.101.0 24
ip ip-prefix guest-route deny 10.1.102.0 24
ip ip-prefix guest_route deny 10.1.103.0 24
ip ip-prefix guest_route deny 10.1.104.0 24
ip ip-prefix guest_route deny 10.1.105.0 24
ip ip-prefix guest_route permi 0.0.0.0 0 less 32
ospf 1
a 1
filter ip-prefix guest_route import
路由_重定向
# 默认内部无线与服务器直接在CORE同VN路由转发
# 想要实现路由的过滤必须进行路由重定向
## CORE
acl number 300
rule 5 permit ip souce 10.1.51.0 0.0.0.255 destination 10.1.60.0 0.0.0.255
rule 5 permit ip souce 10.1.52.0 0.0.0.255 destination 10.1.60.0 0.0.0.255
rule 5 permit ip souce 10.1.53.0 0.0.0.255 destination 10.1.60.0 0.0.0.255
rule 5 permit ip souce 10.1.54.0 0.0.0.255 destination 10.1.60.0 0.0.0.255
rule 5 permit ip souce 10.1.55.0 0.0.0.255 destination 10.1.60.0 0.0.0.255
interface vlanif 51
# ENSP敲不上的
traffic-redirect inbound acl 3000 vpn-instance Employee ip-nexthop 10.1.200.22
interface vlanif 52
traffic-redirect inbound acl 3000 vpn-instance Employee ip-nexthop 10.1.200.22
interface vlanif 53
traffic-redirect inbound acl 3000 vpn-instance Employee ip-nexthop 10.1.200.22
interface vlanif 54
traffic-redirect inbound acl 3000 vpn-instance Employee ip-nexthop 10.1.200.22
阶段测试
- 在AGG上使用dis eth-trunk 1/2/3分别来看上下游的链路聚合是否建立成功
- 在核心上测试去往防火墙四个接口、去往下游209和208是否通畅
- 在核心上测试去往export的所有接口,看是否通畅
ping -c 3 -vpn-instance Employee 10.1.200.30
ping -c 3 -vpn-instance Employee 10.1.200.34
ping -c 3 -vpn-instance Employee 10.1.200.22
ping -c 3 -vpn-instance Guest 10.1.200.26
ping -c 3 10.1.200.14
ping -c 3 10.1.200.18
ping -c 3 10.1.200.1
ping -c 3 10.1.200.5
批量
- 30个IP-POOL都在核心上,要加入到VPN实例当中;
- 前10个VLAN-IF在汇聚上,后10个VLAN-IF在另一台汇聚上;
vlanif
int vlan 11
ip add 10.1.11.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 12
ip add 10.1.12.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 13
ip add 10.1.13.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 14
ip add 10.1.14.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 15
ip add 10.1.15.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 21
ip add 10.1.21.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 22
ip add 10.1.22.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 23
ip add 10.1.23.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 24
ip add 10.1.24.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.29
int vlan 25
ip add 10.1.25.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.29
## X-T2-AGG1
int vlan 31
ip add 10.1.31.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 32
ip add 10.1.32.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 33
ip add 10.1.33.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 34
ip add 10.1.34.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 35
ip add 10.1.35.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 41
ip add 10.1.41.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 42
ip add 10.1.42.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 43
ip add 10.1.43.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 44
ip add 10.1.44.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.33
int vlan 45
ip add 10.1.45.254 255.255.255.0
dhcp select relay
dhcp relay server-ip 10.1.200.33
# CORE
int vlan 51
ip bind vpn-instance Employee
ip add 10.1.51.254 255.255.255.0
dhcp select global
int vlan 52
ip bind vpn-instance Employee
ip add 10.1.52.254 255.255.255.0
dhcp select global
int vlan 53
ip bind vpn-instance Employee
ip add 10.1.53.254 255.255.255.0
dhcp select global
int vlan 54
ip bind vpn-instance Employee
ip add 10.1.54.254 255.255.255.0
dhcp select global
int vlan 55
ip bind vpn-instance Employee
ip add 10.1.55.254 255.255.255.0
dhcp select global
# CORE
int vlan 101
ip bind vpn-instance Guest
ip add 10.1.101.254 255.255.255.0
dhcp select global
int vlan 102
ip bind vpn-instance Guest
ip add 10.1.102.254 255.255.255.0
dhcp select global
int vlan 103
ip bind vpn-instance Guest
ip add 10.1.103.254 255.255.255.0
dhcp select global
int vlan 104
ip bind vpn-instance Guest
ip add 10.1.104.254 255.255.255.0
dhcp select global
int vlan 105
ip bind vpn-instance Guest
ip add 10.1.105.254 255.255.255.0
dhcp select global
pool
ip pool purchase_1
vpn-instance Employee
gateway-list 10.1.11.254
network 10.1.11.0 mask 255.255.255.0
ip pool purchase_2
vpn-instance Employee
gateway-list 10.1.12.254
network 10.1.12.0 mask 255.255.255.0
ip pool purchase_3
vpn-instance Employee
gateway-list 10.1.13.254
network 10.1.13.0 mask 255.255.255.0
ip pool purchase_4
vpn-instance Employee
gateway-list 10.1.14.254
network 10.1.14.0 mask 255.255.255.0
ip pool purchase_5
vpn-instance Employee
gateway-list 10.1.15.254
network 10.1.15.0 mask 255.255.255.0
ip pool market_1
vpn-instance Employee
gateway-list 10.1.21.254
network 10.1.21.0 mask 255.255.255.0
ip pool market_2
vpn-instance Employee
gateway-list 10.1.22.254
network 10.1.22.0 mask 255.255.255.0
ip pool market_3
vpn-instance Employee
gateway-list 10.1.23.254
network 10.1.23.0 mask 255.255.255.0
ip pool market_4
vpn-instance Employee
gateway-list 10.1.24.254
network 10.1.24.0 mask 255.255.255.0
ip pool market_5
vpn-instance Employee
gateway-list 10.1.25.254
network 10.1.25.0 mask 255.255.255.0
ip pool finace_1
vpn-instance Employee
gateway-list 10.1.31.254
network 10.1.31.0 mask 255.255.255.0
ip pool finace_2
vpn-instance Employee
gateway-list 10.1.32.254
network 10.1.32.0 mask 255.255.255.0
ip pool finace_3
vpn-instance Employee
gateway-list 10.1.33.254
network 10.1.33.0 mask 255.255.255.0
ip pool finace_4
vpn-instance Employee
gateway-list 10.1.34.254
network 10.1.34.0 mask 255.255.255.0
ip pool finace_5
vpn-instance Employee
gateway-list 10.1.35.254
network 10.1.35.0 mask 255.255.255.0
ip pool hr_1
vpn-instance Employee
gateway-list 10.1.41.254
network 10.1.41.0 mask 255.255.255.0
ip pool hr_2
vpn-instance Employee
gateway-list 10.1.42.254
network 10.1.42.0 mask 255.255.255.0
ip pool hr_3
vpn-instance Employee
gateway-list 10.1.43.254
network 10.1.43.0 mask 255.255.255.0
ip pool hr_4
vpn-instance Employee
gateway-list 10.1.44.254
network 10.1.44.0 mask 255.255.255.0
ip pool hr_5
vpn-instance Employee
gateway-list 10.1.45.254
network 10.1.45.0 mask 255.255.255.0
ip pool interior_wireless_1
vpn-instance Employee
gateway-list 10.1.51.254
network 10.1.51.0 mask 255.255.255.0
ip pool interior_wireless_2
vpn-instance Employee
gateway-list 10.1.52.254
network 10.1.52.0 mask 255.255.255.0
ip pool interior_wireless_3
vpn-instance Employee
gateway-list 10.1.53.254
network 10.1.53.0 mask 255.255.255.0
ip pool interior_wireless_4
vpn-instance Employee
gateway-list 10.1.54.254
network 10.1.54.0 mask 255.255.255.0
ip pool interior_wireless_5
vpn-instance Employee
gateway-list 10.1.55.254
network 10.1.55.0 mask 255.255.255.0
ip pool without_wireless_1
vpn-instance Guest
gateway-list 10.1.101.254
network 10.1.101.0 mask 255.255.255.0
ip pool without_wireless_2
vpn-instance Guest
gateway-list 10.1.102.254
network 10.1.102.0 mask 255.255.255.0
ip pool without_wireless_3
vpn-instance Guest
gateway-list 10.1.103.254
network 10.1.103.0 mask 255.255.255.0
ip pool without_wireless_4
vpn-instance Guest
gateway-list 10.1.104.254
network 10.1.104.0 mask 255.255.255.0
ip pool without_wireless_5
vpn-instance Guest
gateway-list 10.1.105.254
network 10.1.105.0 mask 255.255.255.0
IP-PREFIX路由过滤
需要匹配所有的内部路由,还需要匹配所有的外部路由;
ACL 路由重定向
匹配五条路由
防火墙地址组
采购、市场、内部无线
易混淆
# 根实例全局
firewall packet-filter basic-protocol enable
switch vsys epmloyee
security-policy
default packet-filter intrazone enable